-
Products
- Network Security
- Threat Protection
- Secure Access Service Edge (SASE)
- Managed XDR
- Endpoint Security
- Email Security
- Secure Access
-
Gen 7 Firewalls
SonicWall's Gen 7 platform-ready firewalls offer performance with stability and superior threat protection — all at an industry-leading TCO.
Read More
-
Solutions
- Industries
- Use Cases
-
Widgets
-
Content WidgetFederal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
-
Image Widget

-
-
Partners
- SonicWall Partners
- Partner Resources
-
Widgets
-
Content WidgetPartner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
-
Image Widget

-
-
Support
- Support
- Resources
- Capture Labs
-
Widgets
-
Content WidgetSupport Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
-
Image Widget

-
- Company
- Contact Us
Tips to protect against CryptoWall and CryptoLocker



Description
CryptoWall and CryptoLocker are ransomwares which infect a computer usually via email. Once a computer is infected, the malware encrypts certain files stored on the computer. Thereafter, the malware will display a message demanding payment to decrypt the files. Infection usually takes place when a user clicks on an executable file attached to a spam email.
Resolution
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Update: A new variant of the above ransomwares is CryptoWall 3.0. It is similar to CryptoLocker and CryptoWall and uses TOR to fetch the encryption keys.
SonicWall Gateway Anti-Virus and SonicWall IPS provide protection against this threat via the following signatures:
| CryptoWall | CryptoLocker |
GAV: Crypwall.H (Trojan) GAV: Cryptowall.A (Trojan) CryptoWall 3.0 GAV: CryptoWall.B (Trojan) GAV: JSCript.Crypto.RES (Trojan) | GAV: Filecoder.BQ (Trojan)
|
SonicWall Application Control can prevent I2P tunnels on your network via the following signatures:
- 5 Encrypted Key Exchange -- Random Encryption (Skype,UltraSurf,Emule)
- 7 Encrypted Key Exchange -- UDP Random Encryption(UltraSurf)
- 10817 I2P -- HTTP Proxy Access 1 [Reqs SID 5 & 7]
- 10817 I2P -- HTTP Proxy Access 2 [Reqs SID 5 & 7]
- 10817 I2P -- HTTP Proxy Access 3 [Reqs SID 5 & 7]
For more information on the workings of this malware, you can refer to the following SonicAlerts:
- Cryptowall 4.0 emerges with new features (Nov 6, 2015)
- CryptoWall 3.0: Ransomware returns with I2P Network
- Cryptowall Ransomware uses Bitcoin and TOR exclusively (June 27, 2014)
- Cryptolocker Ransomware holds files hostage for cash (Sep 19, 2013)
This article describes tips to follow to be protected against this malware.
 NOTE: These Services are Optional, in order to protect may require additional Purchase and also few services like Botnet and DPI SSL are supported with selected products only.
NOTE: These Services are Optional, in order to protect may require additional Purchase and also few services like Botnet and DPI SSL are supported with selected products only.
Recommend to check your product and its capabilities for further details and purchase options.
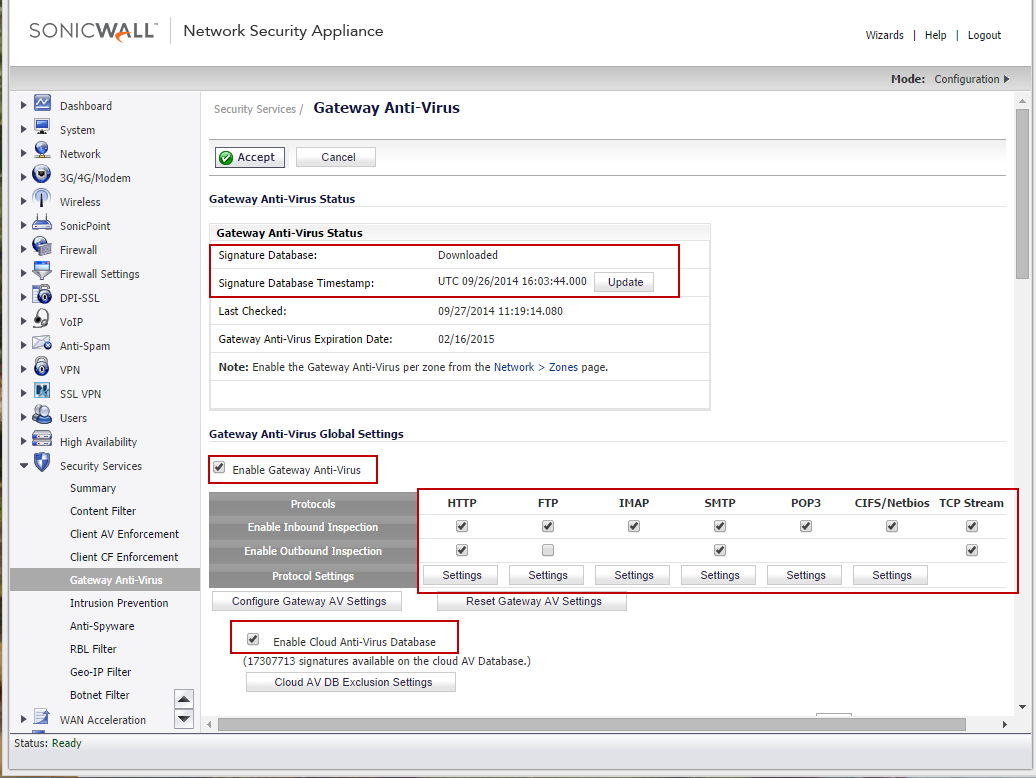
1. Gateway Anti-virus (GAV)
- Make sure GAV is updated with the latest signatures.
- Enable GAV.
- Enable Cloud GAV
- Enable Inbound and Outbound inspection of HTTP, FTP, IMAP, SMTP, POP3, CIFS/Netbios and TCP Stream.
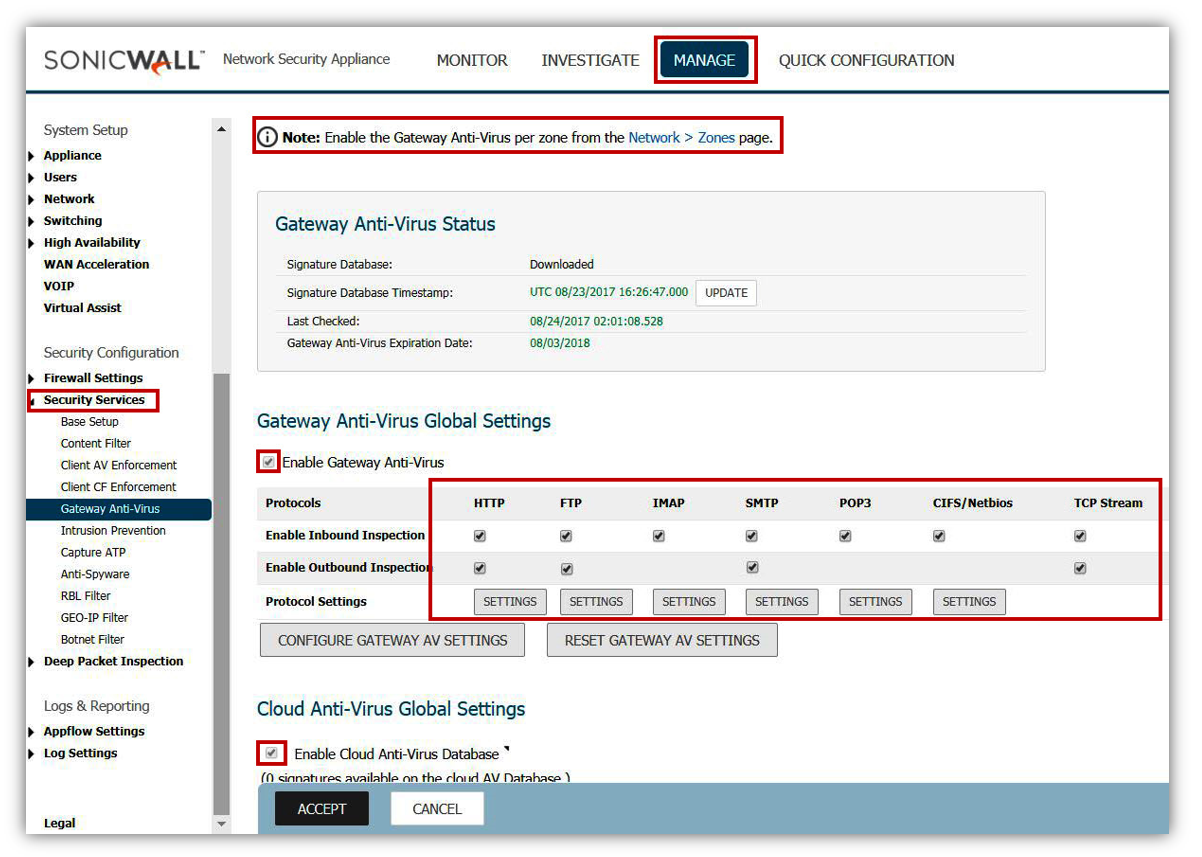
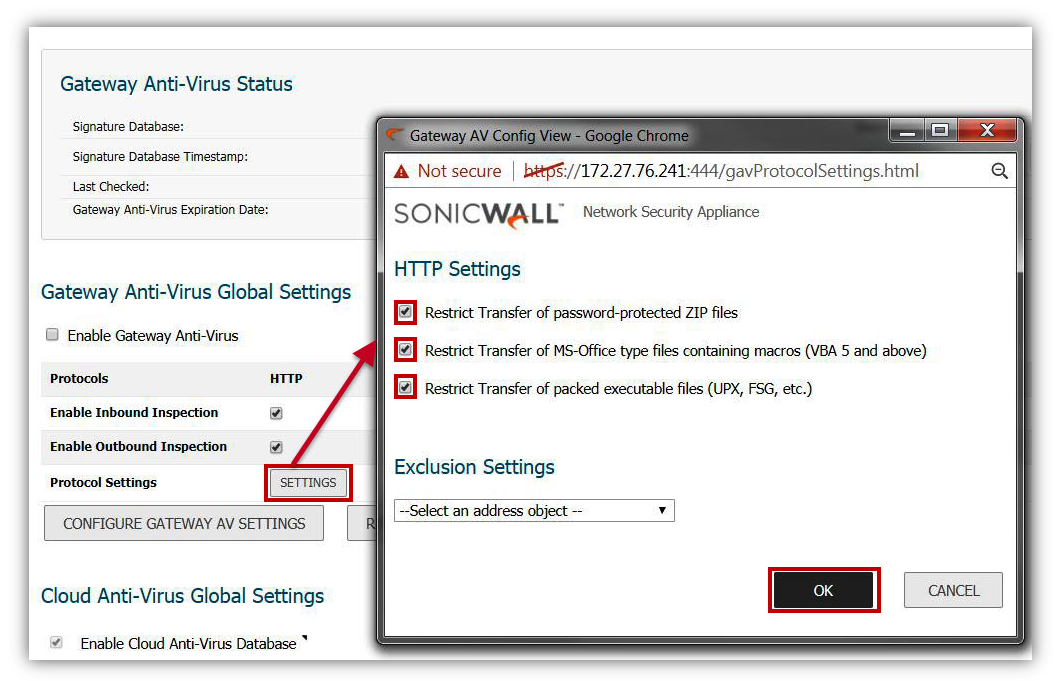
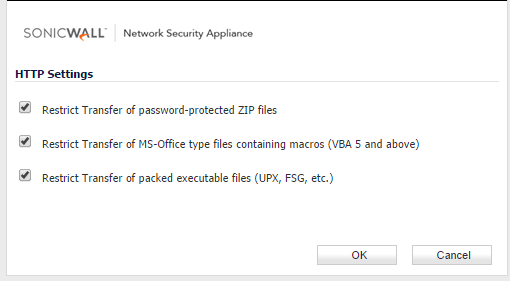
Under the settings of each protocol (HTTP etc), enable the check boxes under
- Restrict Transfer of password-protected ZIP files
- Restrict Transfer of MS-Office type files containing macros (VBA 5 and above)
- Restrict Transfer of packed executable files (UPX, FSG, etc.)
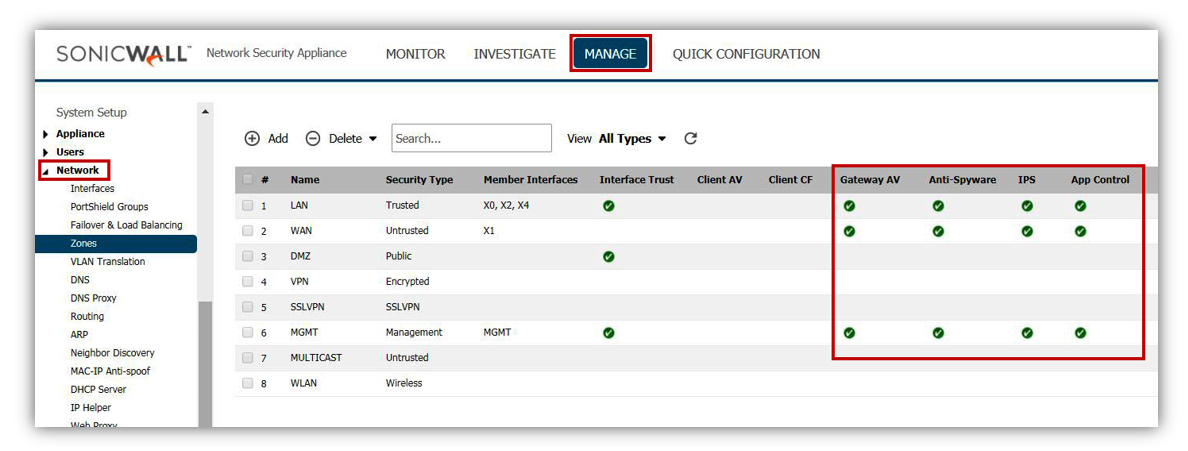
Enable GAV on all internal and external zones under Manage | Network | Zones.
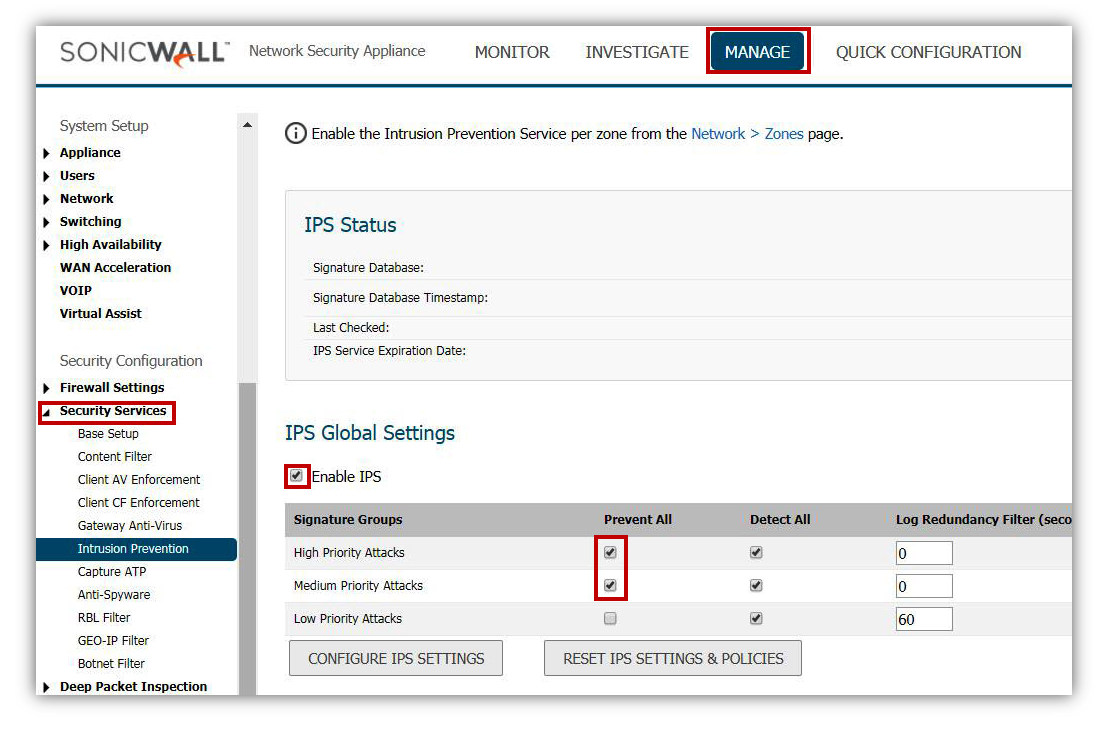
2. Intrusion Prevention Service (IPS)
- Make sure IPS is updated with the latest signatures?
- Enable Prevention of Medium and High Priority Attacks. This will automatically include the signatures for this malware
- Enable IPS on all internal and external zones under Manage | Network | Zones.
3. Botnet Filter
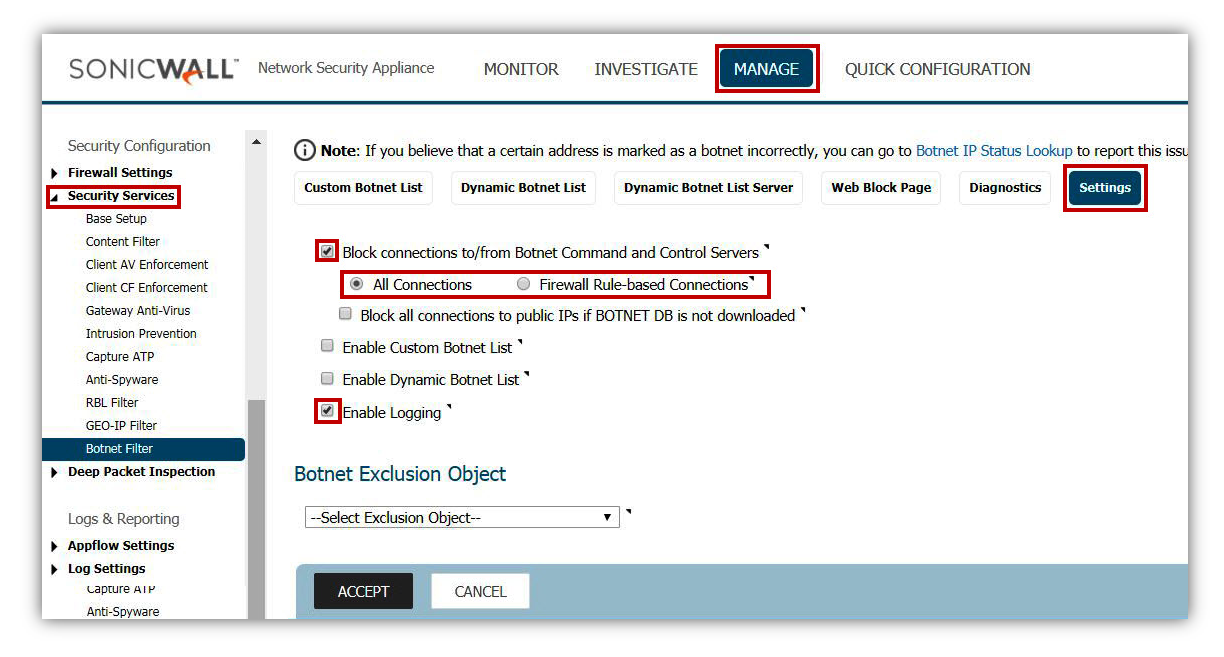
Enabling Botnet Filter will block access to known command and control servers of this malware.
- On the Manage | Security Services | Botnet Filter page, enable the check box, Block connections to/from Botnet Command and Control Servers.
- Enable the check box Enable Logging.
4. Content Filter Service (CFS)
Enable CFS and configure to block sites in the “Malware” and “Hacking/Proxy Avoidance Systems”
5. App Control Advanced
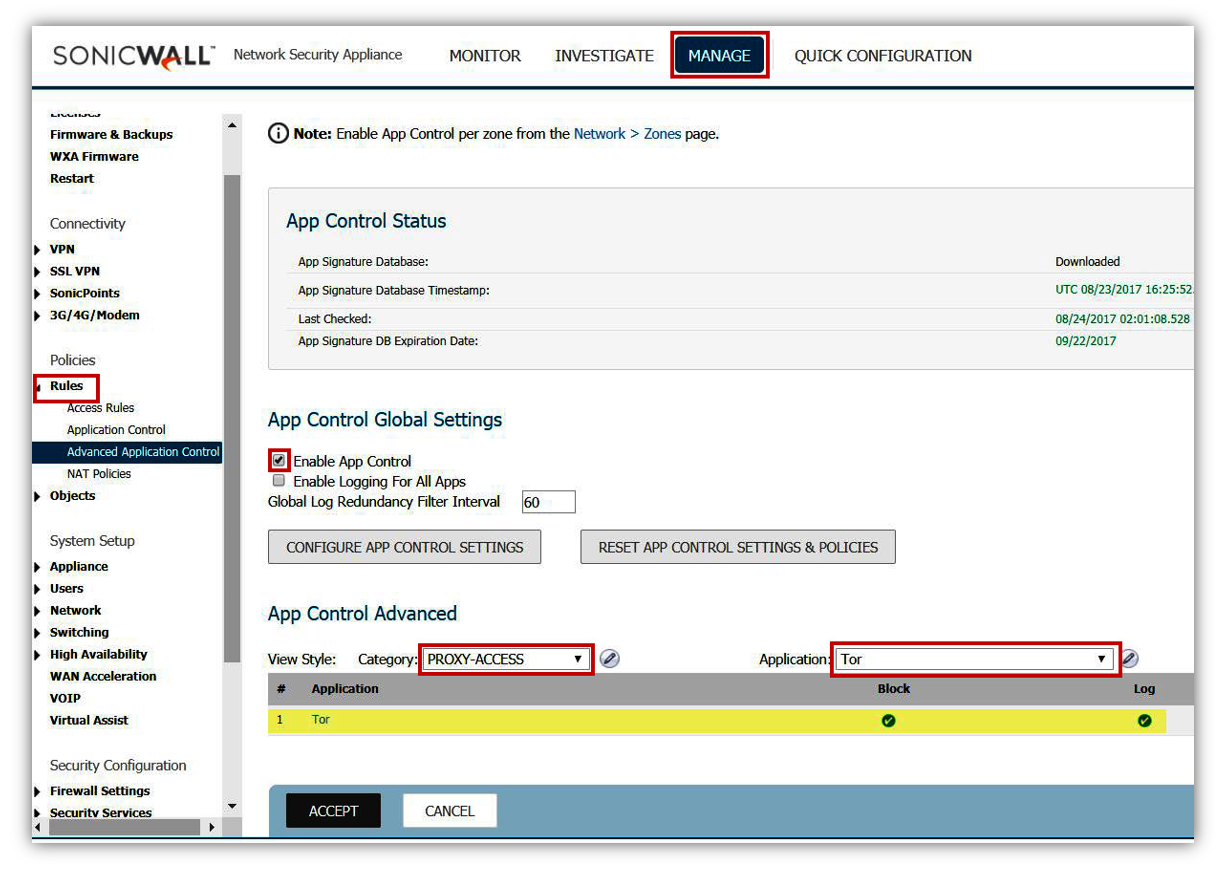
CryptoWall is known to use TOR to obtain the encryption keys used for encrypting files. Therefore, use App Control Advanced to block TOR. By enabling the signatures for TOR, CryptoWall will not be able to obtain the keys needed to encrypt files thus mitigating further damage to the infected host computer.
- On the Manage | Rules | Advanced Application Control page, select Category as PROXY-ACCESS
- Set Application to TOR.
- Click on Configure under Application with TOR selected.
- Set Block and Log to Enable.
- Click on OK to save.
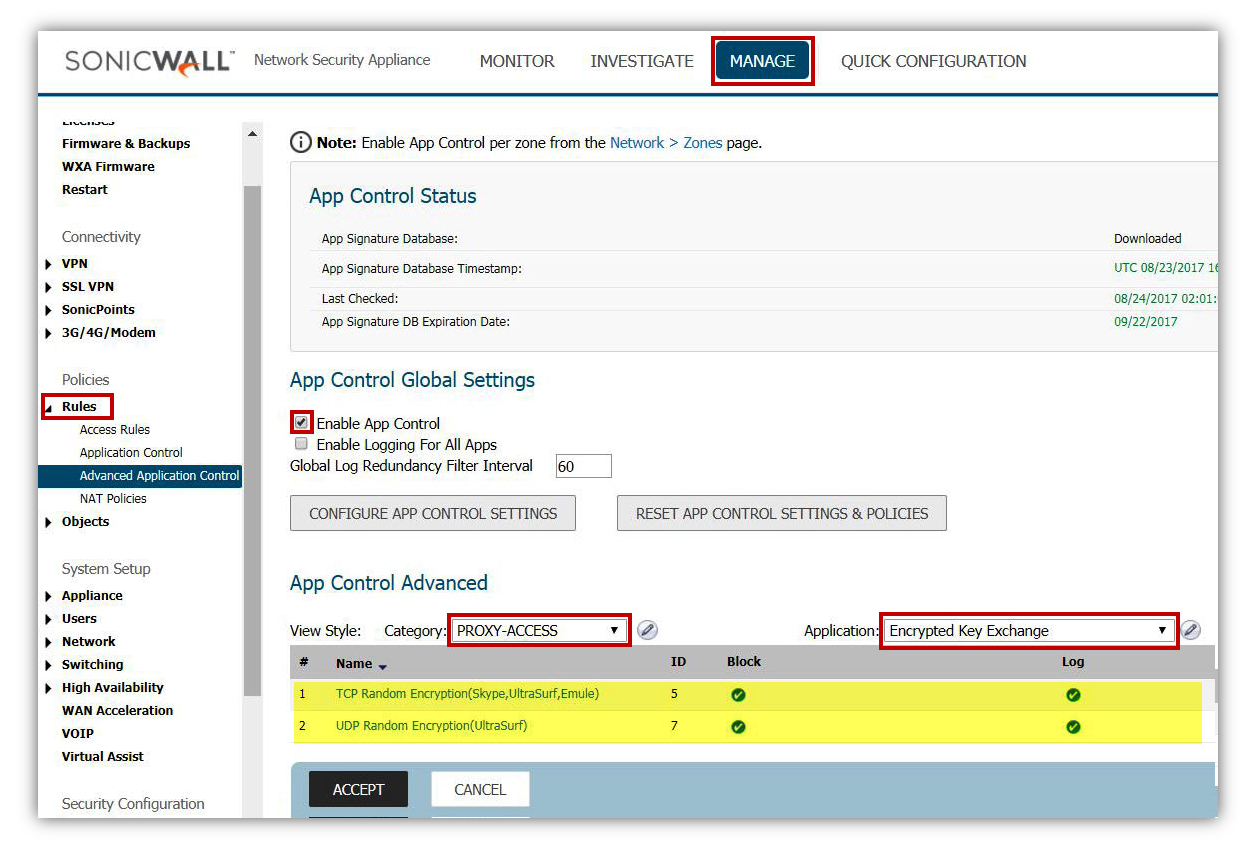
Tor will use Encrypted key exchange application,in order to block that:
- On the Manage | Rules | Advanced Application Control page, select Category as PROXY-ACCESS..
- Set Application to encrypted key exchange
- Click on Configure under Application with Encrypted key exchange selected.
- Set Block and Log to Enable.
- Click on OK to save.
6. DPI-SSL Client Inspection
Enabling Client DPI-SSL, although not a mandatory measure, would provide additional security because 1) almost all web and email traffic is over SSL. For example, if a spam email is received over SSL, SonicWall will not be able to detect the malware contents, if any, in it. 2) initial connection to TOR gateway is over SSL. Enabling DPI-SSL will allow SonicWall to decrypt such traffic and scan it for malware. Under the Manage | Deep Packet Inspection | SSL Client deployment page, enable the check boxes under Gateway Anti-virus and Intrusion Prevention.
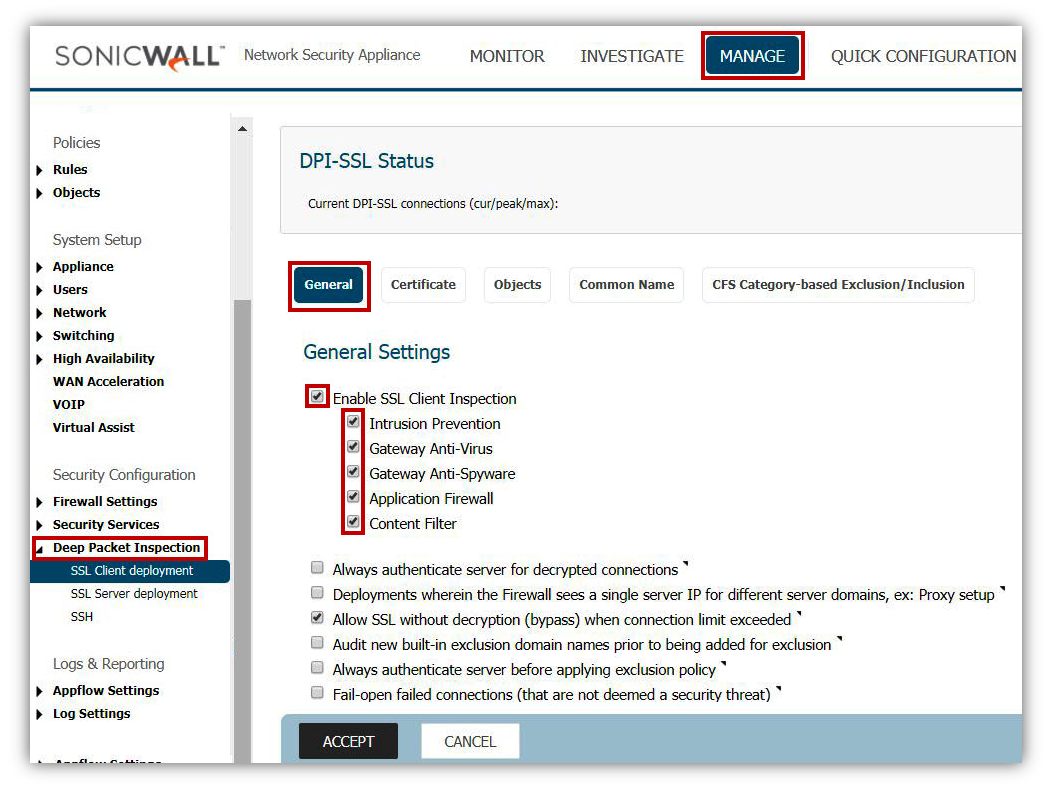
Note: DPI-SSL requires a license and is supported in NSA 220 and higher appliances with SonicOS 5.6 and above firmware.
7.CryptoWall or CryptoLocker infection may not always happen over the Internet.
It could occur over shared files and/or drives or over shared removable media like USB thumb drives and external hard disks. Therefore, Administrators are advised to adhere to basic system level security to protect internal hosts in the network from being infected.
Suggestions include, but not limited to:
- Installing end-point anti-virus software and keeping it updated with the latest signatures
- Updating host Operating Systems, Browsers and Browser plugins with the latest security patches
- Performing regular offline (cold) system back-ups
- Educating users on the dangers of opening unknown files received from unknown sources etc.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Update: A new variant of the above ransomwares is CryptoWall 3.0. It is similar to CryptoLocker and CryptoWall and uses TOR to fetch the encryption keys.
SonicWall Gateway Anti-Virus and SonicWall IPS provide protection against this threat via the following signatures:
| CryptoWall | CryptoLocker |
GAV: Crypwall.H (Trojan) GAV: Cryptowall.A (Trojan) CryptoWall 4.0 GAV: CryptoWall.B (Trojan) GAV: JSCript.Crypto.RES (Trojan) | GAV: Filecoder.BQ (Trojan)
|
SonicWall Application Control can prevent I2P tunnels on your network via the following signatures:
- 5 Encrypted Key Exchange -- Random Encryption (Skype,UltraSurf,Emule)
- 7 Encrypted Key Exchange -- UDP Random Encryption(UltraSurf)
- 10817 I2P -- HTTP Proxy Access 1 [Reqs SID 5 & 7]
- 10817 I2P -- HTTP Proxy Access 2 [Reqs SID 5 & 7]
- 10817 I2P -- HTTP Proxy Access 3 [Reqs SID 5 & 7]
For more information on the workings of this malware, you can refer to the following SonicAlerts:
- Cryptowall 4.0 emerges with new features (Nov 6, 2015)
- CryptoWall 3.0: Ransomware returns with I2P Network
- Cryptowall Ransomware uses Bitcoin and TOR exclusively (June 27, 2014)
- Cryptolocker Ransomware holds files hostage for cash (Sep 19, 2013)
This article describes tips to follow to be protected against this malware.
 NOTE: These Services are Optional, in order to protect may require additional Purchase and also few services like Botnet and DPI SSL are supported with selected products only.
NOTE: These Services are Optional, in order to protect may require additional Purchase and also few services like Botnet and DPI SSL are supported with selected products only.
Recommend to check your product and its capabilities for further details and purchase options.
1. Gateway Anti-virus (GAV)
- Make sure GAV is updated with the latest signatures.
- Enable GAV.
- Enable Cloud GAV
- Enable Inbound and Outbound inspection of HTTP, FTP, IMAP, SMTP, POP3, CIFS/Netbios and TCP Stream.
Under the settings of each protocol (HTTP etc), enable the check boxes under
- Restrict Transfer of password-protected ZIP files
- Restrict Transfer of MS-Office type files containing macros (VBA 5 and above)
- Restrict Transfer of packed executable files (UPX, FSG, etc.)
- Enable GAV on all internal and external zones under Network | Zones.
2. Intrusion Prevention Service (IPS)
- Make sure IPS is updated with the latest signatures?
- Enable Prevention of Medium and High Priority Attacks. This will automatically include the signatures for this malware
- Enable IPS on all internal and external zones under Network | Zones.
3. Botnet Filter
Enabling Botnet Filter will block access to known command and control servers of this malware.
- On the Security Services | Botnet Filter page, enable the check box, Block connections to/from Botnet Command and Control Servers.
- Enable the check box Enable Logging.
4. Content Filter Service (CFS)
Enable CFS and configure to block sites in the “Malware” and “Hacking/Proxy Avoidance Systems”
5. App Control Advanced
CryptoWall is known to use TOR to obtain the encryption keys used for encrypting files. Therefore, use App Control Advanced to block TOR. By enabling the signatures for TOR, CryptoWall will not be able to obtain the keys needed to encrypt files thus mitigating further damage to the infected host computer.
- On the Firewall | App Control Advanced page, select Category as PROXY-ACCESS
- Set Application to TOR.
- Click on Configure under Application with TOR selected.
- Set Block and Log to Enable.
- Click on OK to save.
Tor will use Encrypted key exchange application,in order to block that:
- On the Firewall | App Control Advanced page, select Category as PROXY-ACCESS..
- Set Application to encrypted key exchange
- Click on Configure under Application with Encrypted key exchange selected.
- Set Block and Log to Enable.
- Click on OK to save.
6. DPI-SSL Client Inspection
Enabling Client DPI-SSL, although not a mandatory measure, would provide additional security because 1) almost all web and email traffic is over SSL. For example, if a spam email is received over SSL, SonicWall will not be able to detect the malware contents, if any, in it. 2) initial connection to TOR gateway is over SSL. Enabling DPI-SSL will allow SonicWall to decrypt such traffic and scan it for malware. Under the DPI-SSL | Enable SSL Client Inspection page, enable the check boxes under Gateway Anti-virus and Intrusion Prevention.
Note: DPI-SSL requires a license and is supported in NSA 220 and higher appliances with SonicOS 5.6 and above firmware.
7.CryptoWall or CryptoLocker infection may not always happen over the Internet.
It could occur over shared files and/or drives or over shared removable media like USB thumb drives and external hard disks. Therefore, Administrators are advised to adhere to basic system level security to protect internal hosts in the network from being infected.
Suggestions include, but not limited to:
- Installing end-point anti-virus software and keeping it updated with the latest signatures
- Updating host Operating Systems, Browsers and Browser plugins with the latest security patches
- Performing regular offline (cold) system back-ups
- Educating users on the dangers of opening unknown files received from unknown sources etc.
Related Articles
- Supported SonicWall and 3rd party SFP and SFP+ modules that can be used with SonicWall TZ series
- Certificate Signing Request (CSR) Error: Please enter a valid certificate name for SonicOS 7.1.1
- SNMP OID values that are not supported on Gen7 firewalls
Categories
- Firewalls > SonicWall NSA Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > TZ Series



 YES
YES NO
NO