-
Products
- Network Security
- Threat Protection
- Secure Access Service Edge (SASE)
- Managed XDR
- Endpoint Security
- Email Security
- Secure Access
-
Gen 7 Firewalls
SonicWall's Gen 7 platform-ready firewalls offer performance with stability and superior threat protection — all at an industry-leading TCO.
Read More
-
Solutions
- Industries
- Use Cases
-
Widgets
-
Content WidgetFederal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
-
Image Widget

-
-
Partners
- SonicWall Partners
- Partner Resources
-
Widgets
-
Content WidgetPartner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
-
Image Widget

-
-
Support
- Support
- Resources
- Capture Labs
-
Widgets
-
Content WidgetSupport Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
-
Image Widget

-
- Company
- Contact Us
How to Configure DPI-SSL CFS Category-based Exclusions / Inclusions



Description
In previous implementations, Client DPI-SSL was a global setting which, once enabled, affected all SSL traffic passing through the SonicWall. To exclude certain traffic from being inspected by Client DPI-SSL, administrators must add the domain names of each website in the Common Name Exclusions list. For example, in deployments where in order to comply with privacy and legal requirements Client DPI-SSL must not inspect banking and/or health related HTTPS traffic, administrators had to know and add each such website's CN under Common Name Exclusions.
In the current implementation, Client DPI-SSL can be configured to Exclude or Include websites based on their categories. For example, in order to exclude all banking and financial websites, categories 20 and 21 need to be selected for exclusion, while all other categories are included. Or, to exclude all health related websites, category 26 need to be selected for exclusion. This will ensure that all banking and health related transactions will be automatically excluded from any content decryption in the SonicWall.
This feature uses the CFS category list to exclude or include specific categories from DPI-SSL inspection. The CFS categories are provided in the DPI-SSL Client page.
As in Content Filtering Service, the category / rating information related to a domain is obtained by querying an external Rating/Category Server. The domain name for which the rating is queried is obtained from the SSL Handshake between the SonicWall and the server.
Before configuring DPI-SSL CFS category-based exclusion, the following configuration/deployment is expected:
- DPI-SSL license is active
- CFS License is active and enabled
- CFS needs to be enabled (if using zones, CFS needs to be enabled in the zone the user belongs to, ex:LAN zone if the client connection is coming in from the LAN; if using App rules policy, CFS needs to be enabled in the App rule).
- The default Dell SonicWall DPI-SSL CA certificate is imported into the Certificate Store of the hosts behind the SonicWall. The certificate can be download from the DPI-SSL | Client SSL page under the Certificate tab.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
- Log in to the SonicWall management portal
- Navigate to the Policy | Deep packet Inspection | SSL Client deployment page.
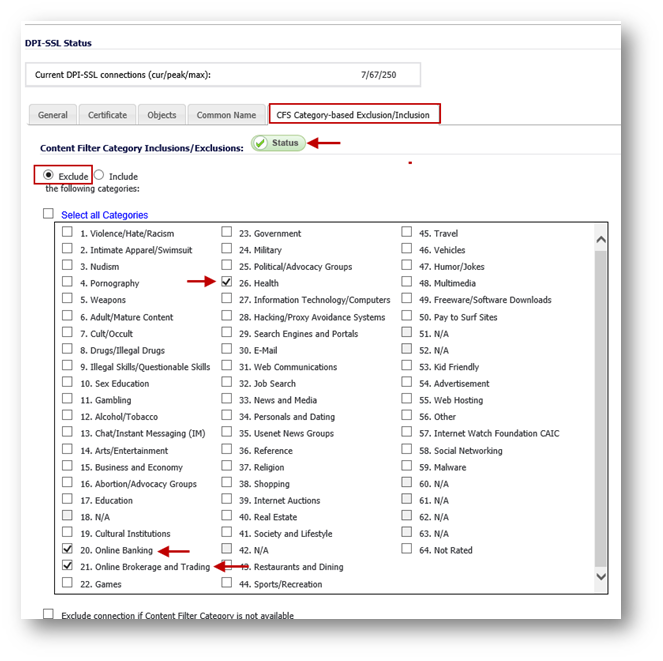
- Click on the CFS Category-based Inclusion/Exclusion tab
- Under Content Filter Category Inclusions/Exclusions, select either Exclude or Include. By default, Exclude is selected. For this article, we go with the default.
- In the Category list, select the category that has to be included for or excluded from DPI-SSL inspection. Note: For this article, the categories 20 (Online Banking) and 21 (Online Brokerage and Trading), and 26 (Health) are selected for exclusion.
- Click on Accept at the bottom to save the settings
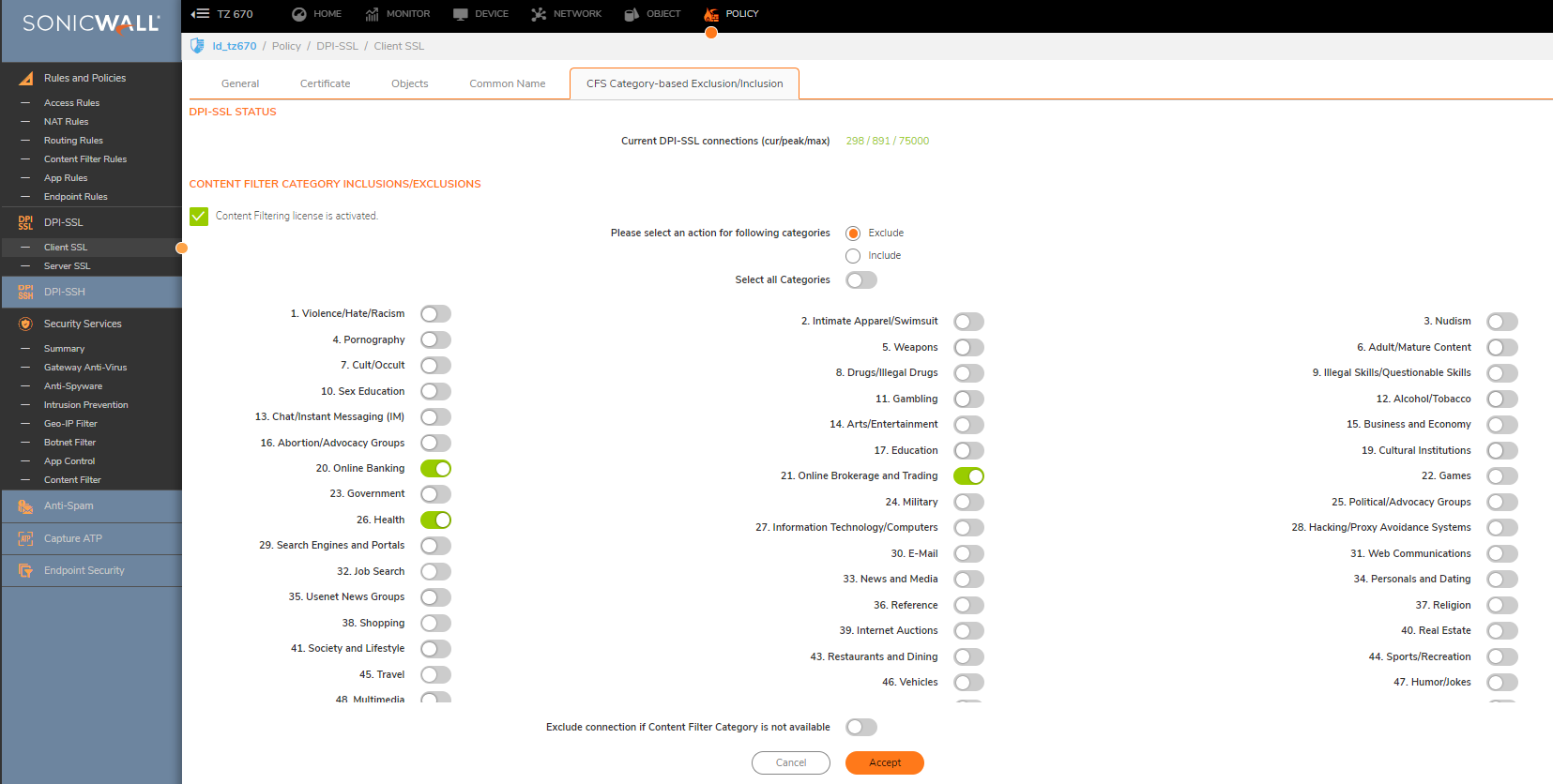
 NOTE: Selecting either category 20 or 21 will automatically result in selection of the other, ie: categories 20 and 21 go hand-in-hand.
NOTE: Selecting either category 20 or 21 will automatically result in selection of the other, ie: categories 20 and 21 go hand-in-hand.
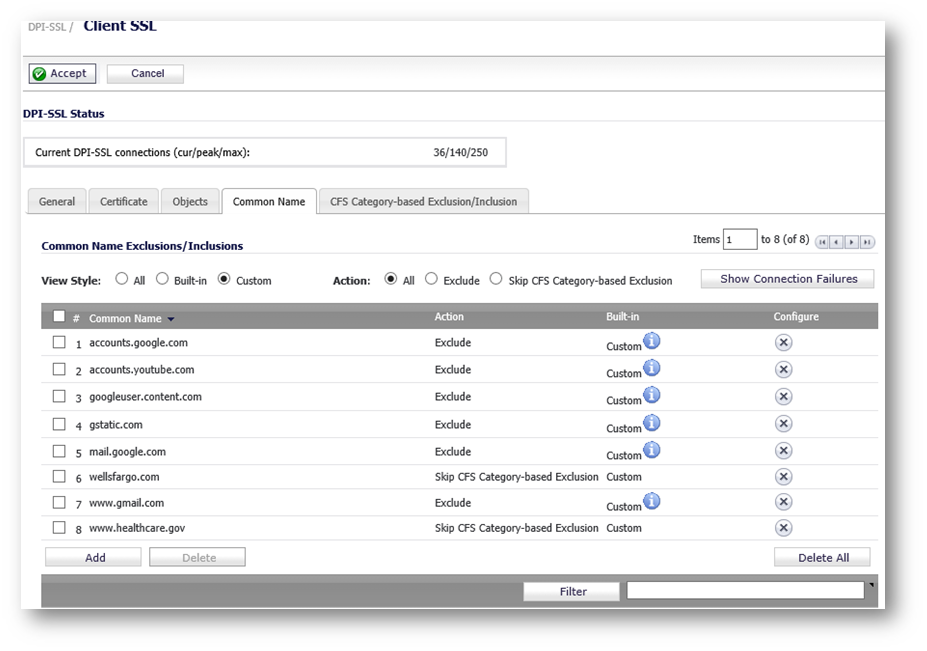
We have selected categories 20,21 and 26 for exclusion. All other categories are included for DPI-SSL inspection. We now add sites that needs to be excluded from DPI-SSL inspection although their associated category is set for inclusion.
- Navigate to the Common Name tab
- Under View Style, select Custom
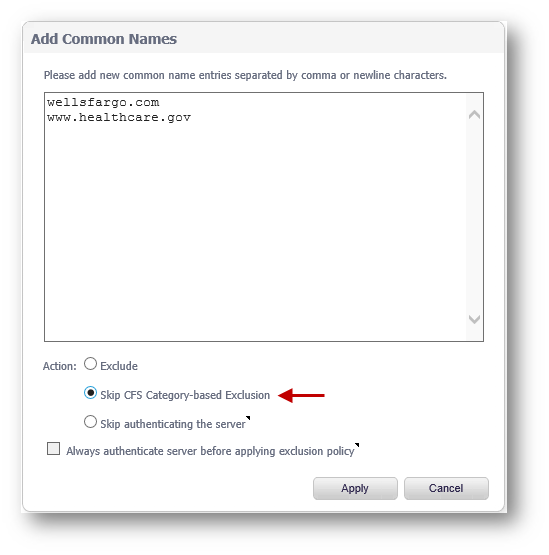
- Click on the Add button
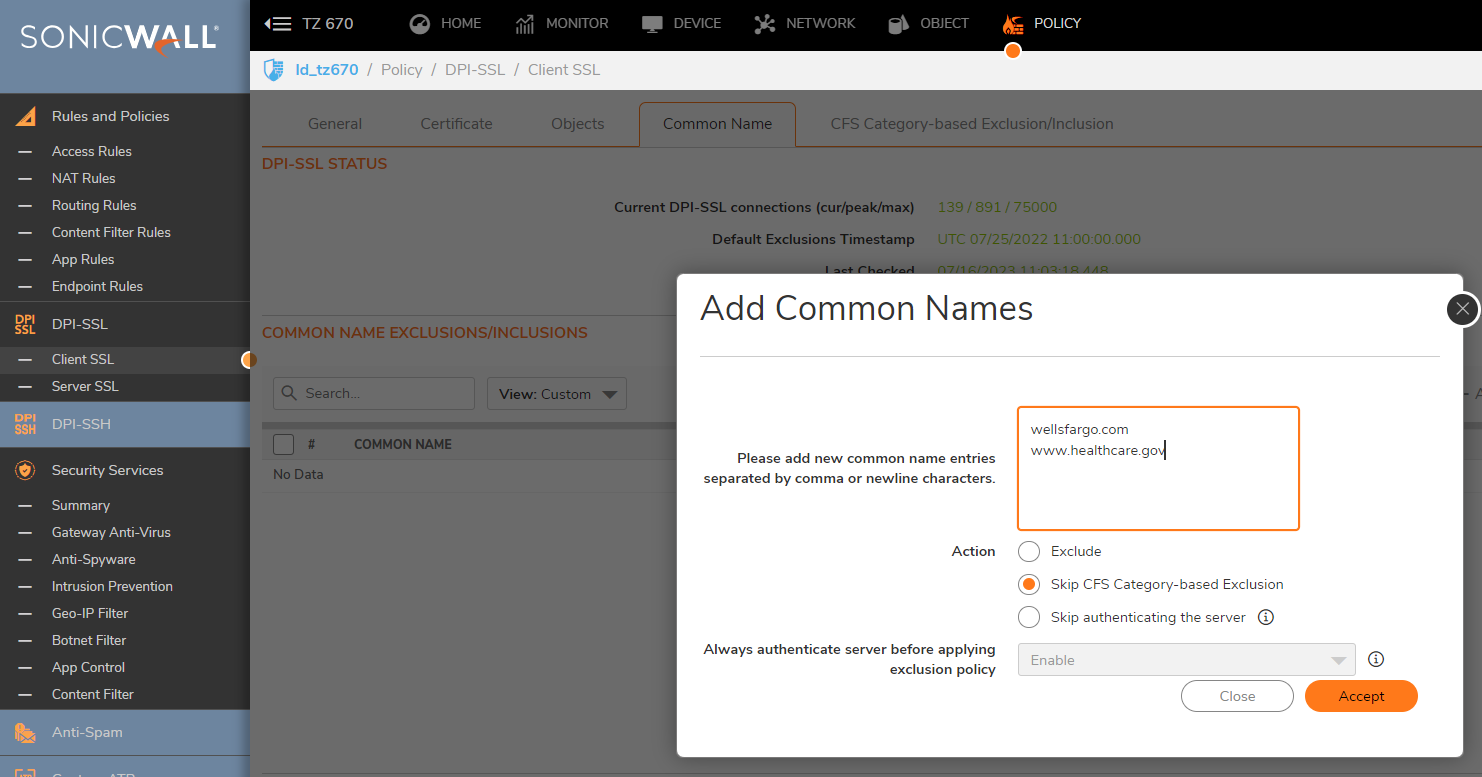
- In the Add Common Names window, enter the Common Names of the sites to be excluded.
- Set Action to Exclude
- Enable the check-box, Always authenticate the server before applying the exclusion policy.
- Click on Accept

Now we add websites that must be included for DPI-SSL inspection although their associated category is set to exclude.
- Click on Add again
- Enter the Common Names of the site you wish to include.
- Set Action to Skip CFS Category-based Exclusion
- Click on Accept
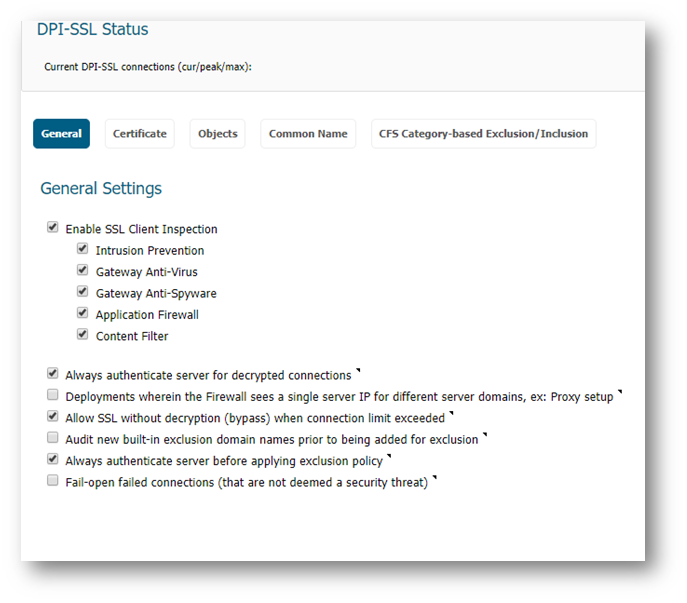
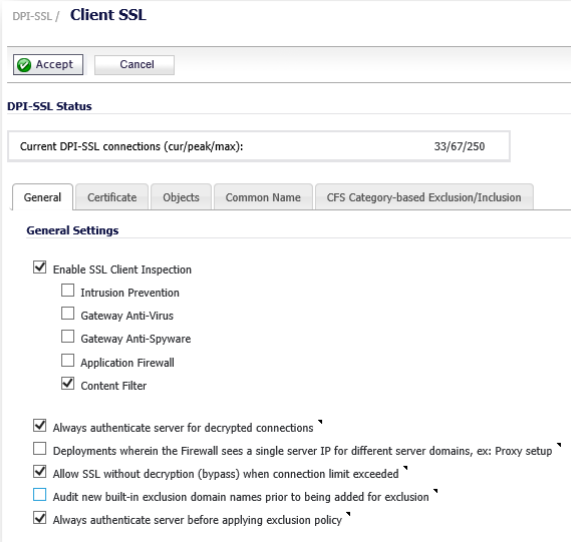
We now enable SSL Client inspection.
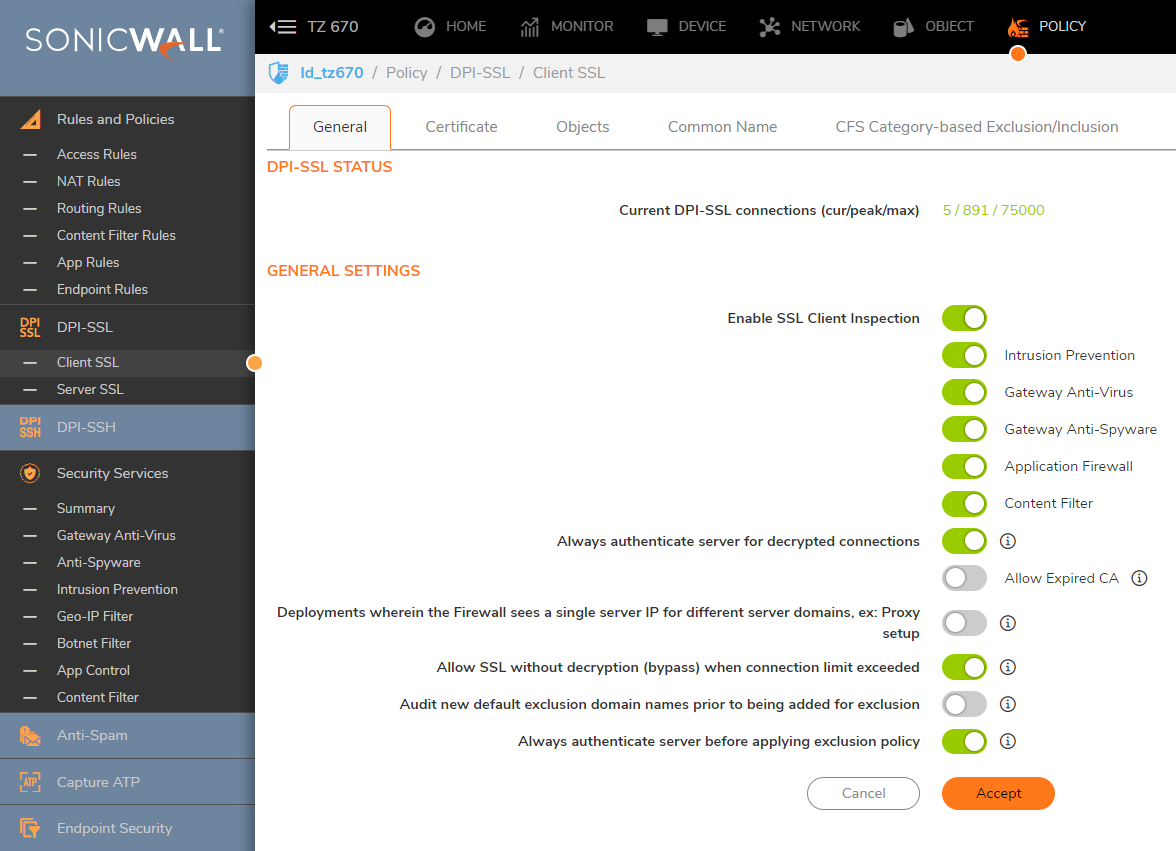
- Navigate to the General tab
- Enable SSL Client Inspection
- Content Filter
- Always authenticate the server for decrypted connections (recommended)
- Always authenticate the server before applying the exclusion policy (recommended)
- All other option could be left at default.
- Click on Accept at the top to save the settings.
Testing
From a host behind the SonicWall, perform the following tests:
- Go to https://online.citi.com. Click on the lock icon and make sure the certificate is issued by a public CA
- Test other banking or health related websites and they must show their certificates as issued by a public CA
- Go to https://www.wellsfargo.com. Click on the lock icon and the certificate should show that it has been issued by SonicWall Firewall DPI-SSL CA.
- Do the same for https://www.healthcare.gov
- Go to https://mail.google.com. The site must show its certificate as issued by a public CA.
- Go to other websites excluding the above and all must show the certificates issued by SonicWall DPI-SSL CA.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
- Log in to the SonicWall management portal
- Navigate to the Deep packet Inspection | SSL Client deployment page.
- Click on the CFS Category-based Inclusion/Exclusion tab
- Under Content Filter Category Inclusions/Exclusions, select either Exclude or Include. By default Exclude is selected. For this article, we go with the default.
- In the Category list, select the category that has to be included for or excluded from DPI-SSL inspection. Note: For this article, the categories 20 (Online Banking) and 21 (Online Brokerage and Trading) and 26 (Health) are selected for exclusion.
- Click on Accept at the bottom to save the settings
 NOTE: Selecting either category 20 or 21 will automatically result in selection of the other, ie: categories 20 and 21 go hand-in-hand.
NOTE: Selecting either category 20 or 21 will automatically result in selection of the other, ie: categories 20 and 21 go hand-in-hand.
We have selected categories 20,21 and 26 for exclusion. All other categories are included for DPI-SSL inspection. We now add sites that needs to be excluded from DPI-SSL inspection although their associated category is set for inclusion.
- Navigate to the Common Name tab
- Under View Style, select Custom
- Click on the Add button
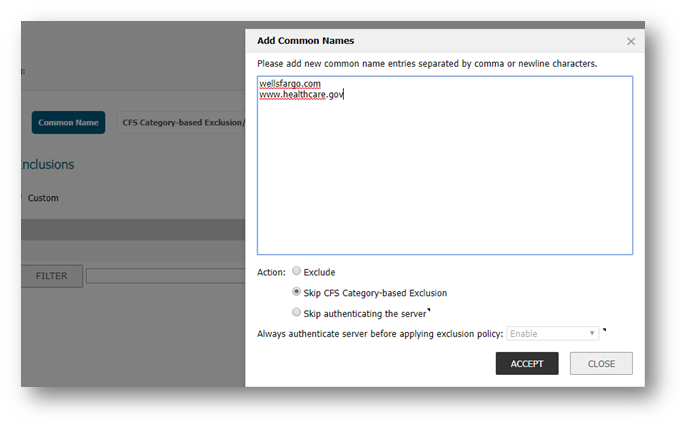
- In the Add Common Names window, enter Common Names of the sites to be excluded.
- Set Action to Exclude
- Enable the check-box, Always authenticate server before applying exclusion policy.
- Click on OK

Now we add websites which must be included for DPI-SSL inspection although their associated category is set to exclude.
- Click on Add again
- Enter Common Names of the site you wish to include.
- Set Action to Skip CFS Category-based Exclusion
- Click on OK
We now enable SSL Client inspection.
- Navigate to the General tab
- Enable the following check-boxes:
- Enable SSL Client Inspection
- Content Filter
- Always authenticate server for decrypted connections (recommended)
- Always authenticate server before applying exclusion policy (recommended)3
- All other option could be left at default.
- Click on Accept at the top to save the settings.
Testing
From a host behind the SonicWall, perform the following tests:
- Go to https://online.citi.com. Click on the lock icon and make sure the certificate is issued by a public CA
- Test other banking or health related websites and they must show their certificates as issued by a public CA
- Go to https://www.wellsfargo.com. Click on the lock icon and the certificate should show that it has been issued by SonicWall Firewall DPI-SSL CA.
- Do the same for https://www.healthcare.gov
- Go to https://mail.google.com. The site must show its certificate as issued by a public CA.
- Go to other websites excluding the above and all must show the certificates issued by SonicWall DPI-SSL CA.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
- Log in to the SonicWall management portal
- Navigate to the DPI-SSL | Client SSL page.
- Click on the CFS Category-based Inclusion/Exclusion tab
- Under Content Filter Category Inclusions/Exclusions, select either Exclude or Include. By default Exclude is selected. For this article, we go with the default.
- In the Category list, select the category that has to be included for or excluded from DPI-SSL inspection. Note: For this article, the categories 20 (Online Banking) and 21 (Online Brokerage and Trading) and 26 (Health) are selected for exclusion.
- Click on Accept at the top to save the settings
 NOTE: Selecting either category 20 or 21 will automatically result in selection of the other, ie: categories 20 and 21 go hand-in-hand.
NOTE: Selecting either category 20 or 21 will automatically result in selection of the other, ie: categories 20 and 21 go hand-in-hand.
We have selected categories 20,21 and 26 for exclusion. All other categories are included for DPI-SSL inspection. We now add sites that needs to be excluded from DPI-SSL inspection although their associated category is set for inclusion.
- Navigate to the Common Name tab
- Under View Style, select Custom
- Click on the Add button
- In the Add Common Names window, enter Common Names of the sites to be excluded.
- Set Action to Exclude
- Enable the check-box, Always authenticate server before applying exclusion policy.
- Click on OK

Now we add websites which must be included for DPI-SSL inspection although their associated category is set to exclude.
- Click on Add again
- Enter Common Names of the site you wish to include.
- Set Action to Skip CFS Category-based Exclusion
- Click on OK
We now enable SSL Client inspection.
- Navigate to the General tab
- Enable SSL Client Inspection
- Content Filter
- Always authenticate server for decrypted connections (recommended)
- Always authenticate server before applying exclusion policy (recommended)
- All other option could be left at default.
- Click on Accept at the top to save the settings.
Testing
From a host behind the SonicWall, perform the following tests:
- Go to https://online.citi.com. Click on the lock icon and make sure the certificate is issued by a public CA
- Test other banking or health related websites and they must show their certificates as issued by a public CA
- Go to https://www.wellsfargo.com. Click on the lock icon and the certificate should show that it has been issued by SonicWall Firewall DPI-SSL CA.
- Do the same for https://www.healthcare.gov
- Go to https://mail.google.com. The site must show its certificate as issued by a public CA.
- Go to other websites excluding the above and all must show the certificates issued by SonicWall DPI-SSL CA.
Related Articles
- Supported SonicWall and 3rd party SFP and SFP+ modules that can be used with SonicWall TZ series
- Certificate Signing Request (CSR) Error: Please enter a valid certificate name for SonicOS 7.1.1
- SNMP OID values that are not supported on Gen7 firewalls
Categories
- Firewalls > SonicWall NSA Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > TZ Series



 YES
YES NO
NO