-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How do I exclude traffic from firewall security services?



Description
At times it's necessary to exclude traffic from security services. This can be necessary when certain applications don't interact well with threat scans, additional throughput is required, or traffic is simply going from trusted device to trusted device. This article will detail how to exclude traffic using a variety of methods, such as IP Address, Port, Signature, etc., from the various SonicWall Threat Engines.
Furthermore this article will describe the different methods of excluding traffic, both by the security services themselves as well as via App Rules.
For the purpose of this article security services will be Gateway Anti-Virus (GAV), Intrusion Prevention (IPS), Anti-Spyware (AS), and App Control. Similar setups will also work for the Botnet Filter and Geo-IP Filter features, although those will not be explicitly touched on.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Excluding Traffic via security service Features TIP: Using the security service feature itself to exclude traffic is the simpler, although less granular, method that we will begin with. If you'd like more granular control over the type of traffic excluded from security services please use the App Rules method detailed below.
TIP: Using the security service feature itself to exclude traffic is the simpler, although less granular, method that we will begin with. If you'd like more granular control over the type of traffic excluded from security services please use the App Rules method detailed below.
- Login to the SonicWall management GUI and navigate to the Feature you'd like to exclude traffic for. Navigate to POLICY | Security Services and select the feature where you want to apply the exclusion.
- Each feature will have a Configure option, select that and a pop-up window will appear. From this menu you may select a single Address Object or Address Group to Exclude from the Security Feature. Once you've made your selections, click OK.
 TIP: If you have multiple IP Address to Exclude, add them to an Address Group.
TIP: If you have multiple IP Address to Exclude, add them to an Address Group.  NOTE: App Control can inherit Exclusions from IPS by using the Use IPS Exclusion List option.
NOTE: App Control can inherit Exclusions from IPS by using the Use IPS Exclusion List option.
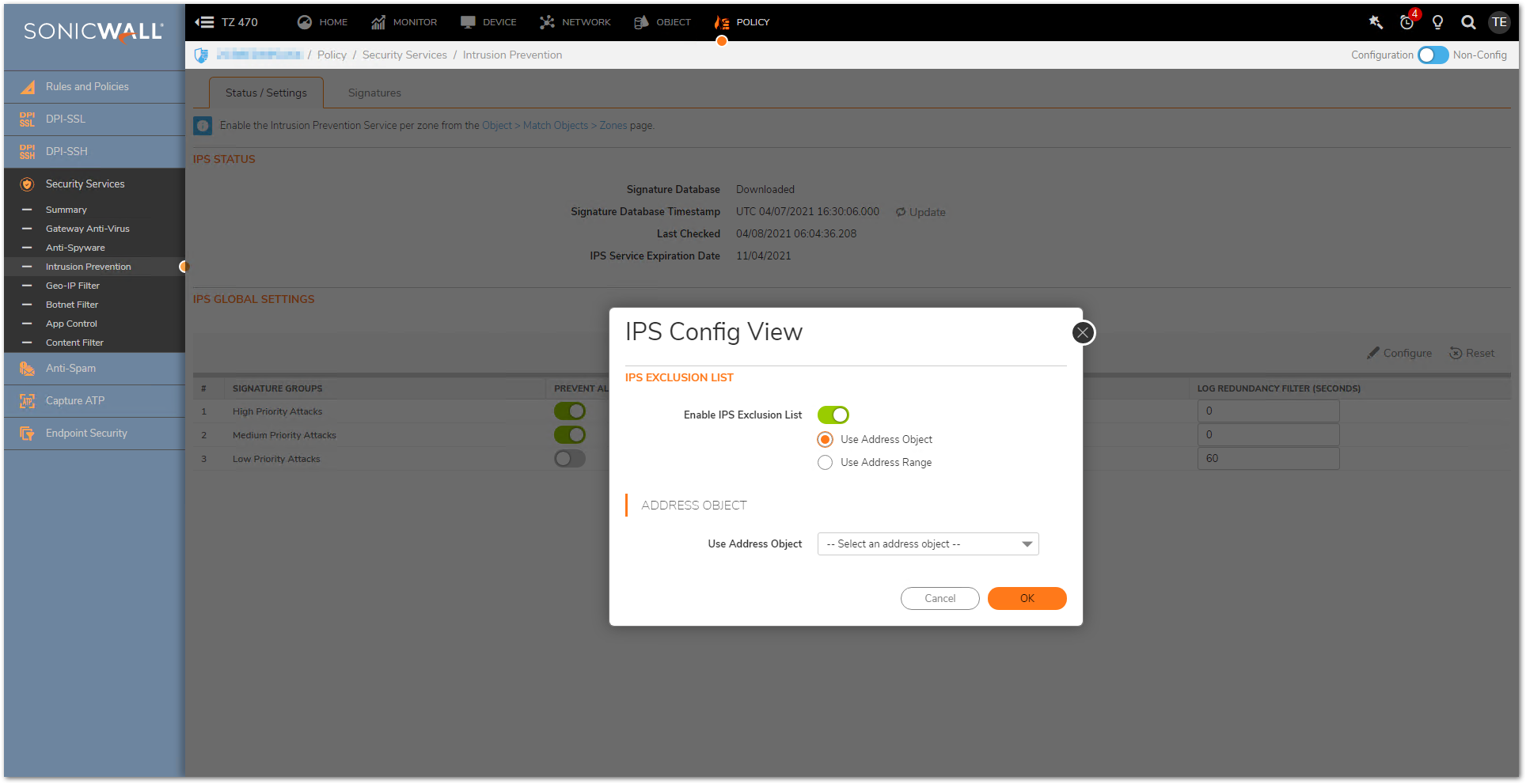
Excluding Traffic via App Rules
 TIP: Excluding Traffic via App Rules allows for more granular control over exemptions but also requires more configuration. If you'd like a quicker, less granular method please use the steps listed above.
TIP: Excluding Traffic via App Rules allows for more granular control over exemptions but also requires more configuration. If you'd like a quicker, less granular method please use the steps listed above.
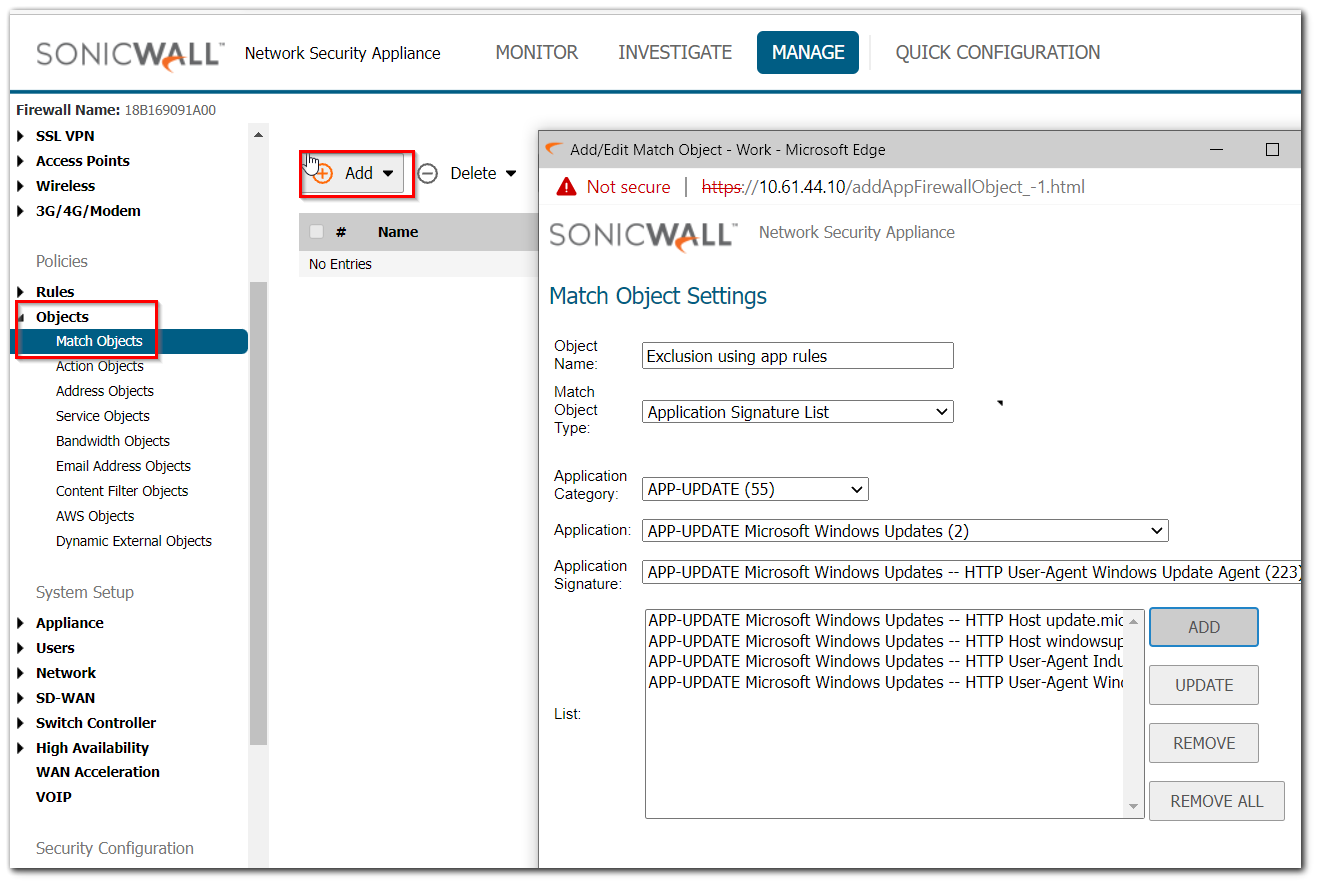
- Login to the SonicWall Management GUI and navigate to OBJECT | Match Objects | Match Objects.
Click Add and a pop-up Match Object Settings window will appear. - Change the Match Object Type field to whatever you wish to use. Typically this will be Application Signature List but any of the available options are valid.
- Select any sub-categories, if necessary, and input any needed values. Click Save.
 EXAMPLE: I'd like to Exclude Windows Updates from being subjected to security services. For my Match Object I select the following:
EXAMPLE: I'd like to Exclude Windows Updates from being subjected to security services. For my Match Object I select the following:- Match Object Type Application Signature List
- Application Category: APP-UPDATE
- Application: APP-UPDATE Microsoft Windows Updates
- Application Signature: Select each entry, select Add, and repeat until all Signatures are included in the List field.
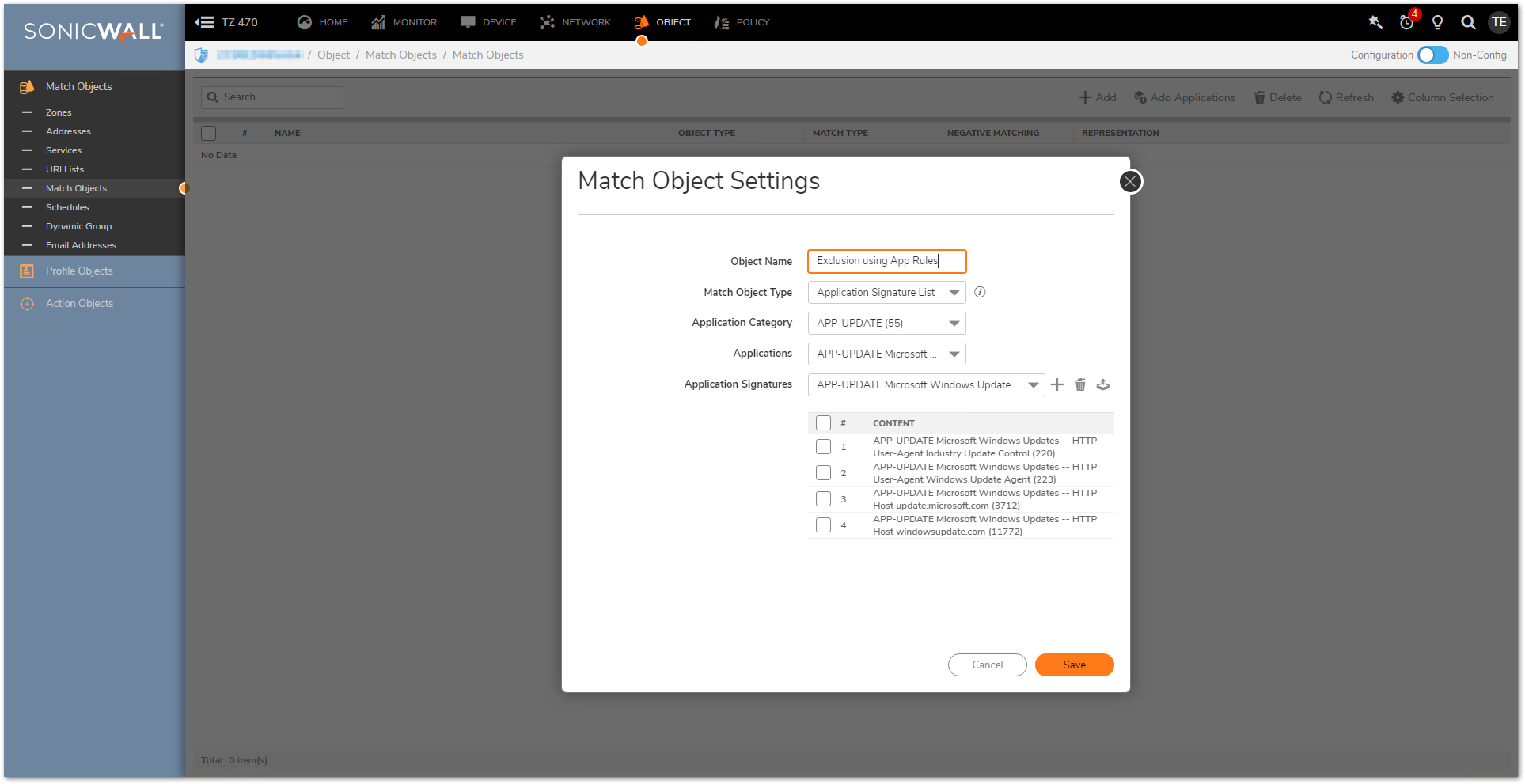
- Nnavigate to POLICY | Rules and Policies | App Rules and click Add Rule. A pop-up window will appear.
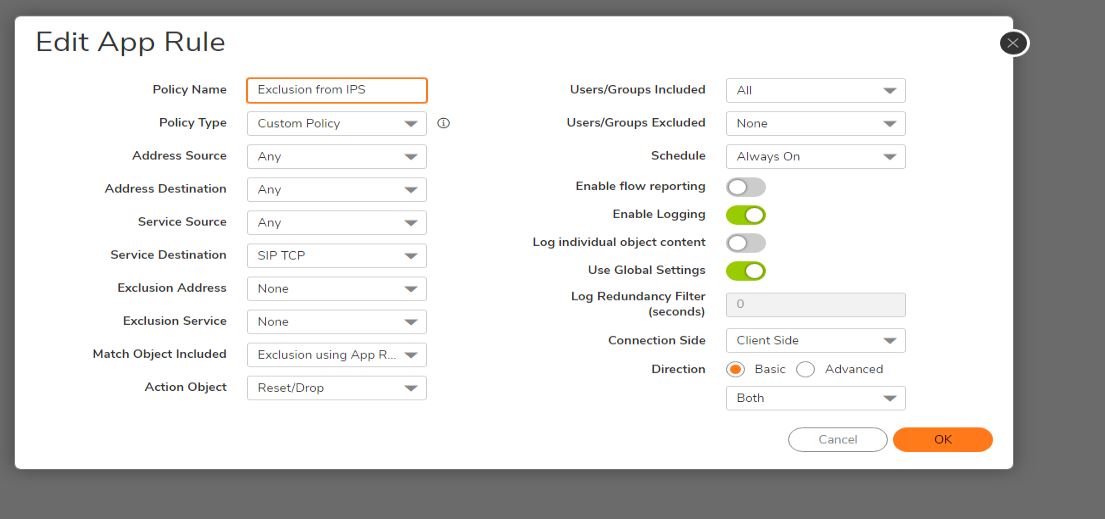
- Set the following information for the App Rule Policy:
- Name - This will be a Friendly Name.
- Policy Type - Set to Custom Policy if you created a Match Object, otherwise set to App Control Content.
- Address | Service | Exclusion Address - Set these as needed. Service is required when going by Ports, Address when going by IP Address.
- Match Object - Select the Match Object created in the earlier steps.
- Action Object - Select the security service you'd like to Bypass, such as IPS.
- Users/Group - Which Users and/or Groups will be included or excluded from this Policy.
- Schedule - You may optionally set a time during which this Policy is in effect.
- Click OK. You should now see your new Policy in the App Rules Table.
 EXAMPLE: In the image below you can see a sample App Rule which exempts all SIP Traffic from the IPS Engine.
EXAMPLE: In the image below you can see a sample App Rule which exempts all SIP Traffic from the IPS Engine.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Excluding Traffic via security service Features
 TIP: Using the security service feature itself to exclude traffic is the simpler, although less granular, method that we will begin with. If you'd like more granular control over the type of traffic excluded from security services please use the App Rules method detailed below.
TIP: Using the security service feature itself to exclude traffic is the simpler, although less granular, method that we will begin with. If you'd like more granular control over the type of traffic excluded from security services please use the App Rules method detailed below.
- Login to the SonicWall Management GUI and navigate to the Feature you'd like to exclude traffic for. For App Control navigate to Manage| Policies| Rules| App Control, for all other Features navigate to Security Configuration| Security Services and select the appropriate option.
- Each feature will have an option for Configure Settings, select that and a pop-up window will appear. From this menu you may select a single Address Object or Address Group to Exclude from the Security Feature. Once you've made your selections, click OK.
 TIP: If you have multiple IP Address to Exclude, add them to an Address Group.
TIP: If you have multiple IP Address to Exclude, add them to an Address Group. NOTE: App Control can inherit Exclusions from IPS by using the Use IPS Exclusion List option.
NOTE: App Control can inherit Exclusions from IPS by using the Use IPS Exclusion List option.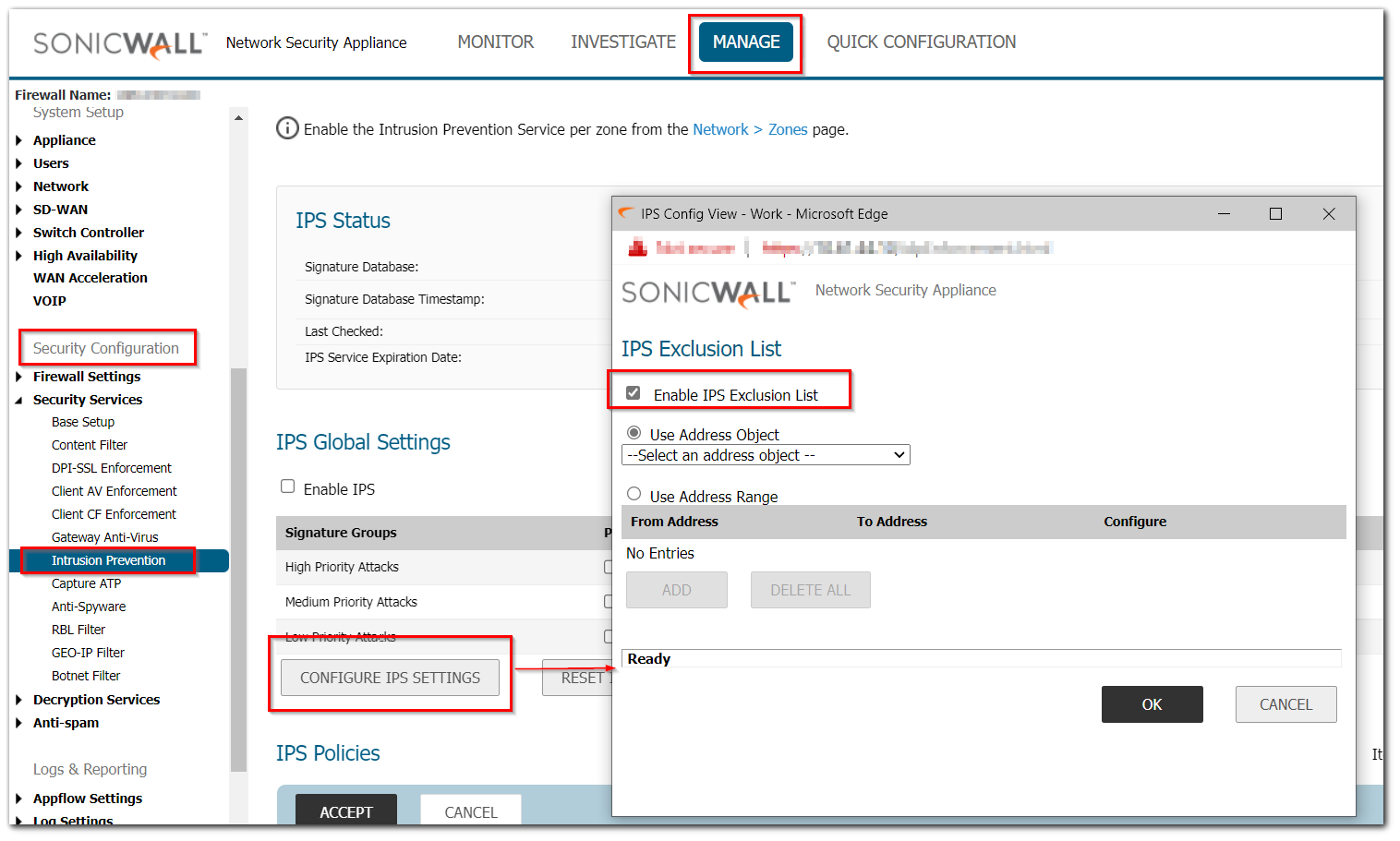
Excluding Traffic via App Rules
 TIP: Excluding Traffic via App Rules allows for more granular control over exemptions but also requires more configuration. If you'd like a quicker, less granular method please use the steps listed above.
TIP: Excluding Traffic via App Rules allows for more granular control over exemptions but also requires more configuration. If you'd like a quicker, less granular method please use the steps listed above.
- Login to the SonicWall Management GUI and navigate to Manage | Policies| Objects | Match Objects.
Select Add New Match Object and a pop-up window will appear. - Change the Match Object Type field to whatever you wish to use. Typically this will be Application Signature List but any of the available options are valid.
- Select any sub-categories, if necessary, and input any needed values. Click OK.
 EXAMPLE: I'd like to Exclude Windows Updates from being subjected to security services. For my Match Object I select the following:
EXAMPLE: I'd like to Exclude Windows Updates from being subjected to security services. For my Match Object I select the following:- Match Object Type Application Signature List
- Application Category: APP-UPDATE
- Application: APP-UPDATE Microsoft Windows Updates
- Application Signature: Select each entry, select Add, and repeat until all Signatures are included in the List field.
- Navigate to Manage | Policies| Rules| App Rules and select Add New Policy. A pop-up window will appear.
- Set the following information for the App Rule Policy:
- Name - This will be a Friendly Name.
- Policy Type - Set to Custom Policy if you created a Match Object, otherwise set to App Control Content.
- Address | Service | Exclusion Address - Set these as needed. Service is required when going by Ports, Address when going by IP Address.
- Match Object - Select the Match Object created in the earlier steps.
- Action Object - Select the security service you'd like to Bypass, such as IPS.
- Users/Group - Which Users and/or Groups will be included or excluded from this Policy.
- Schedule - You may optionally set a time during which this Policy is in effect.
 EXAMPLE: In the image below you can see a sample App Rule which exempts all SIP Traffic from the IPS Engine.
EXAMPLE: In the image below you can see a sample App Rule which exempts all SIP Traffic from the IPS Engine.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series > IPS/GAV/Spyware
- Firewalls > SonicWall SuperMassive 9000 Series > IPS/GAV/Spyware
- Firewalls > SonicWall NSA Series > IPS/GAV/Spyware






 YES
YES NO
NO