Deserialization Leads to Command Injection in GoAnywhere MFT: CVE-2025-10035

Overview
The SonicWall Capture Labs threat research team has identified a critical command injection vulnerability in GoAnywhere MFT. Tracked as CVE-2025-10035, this flaw allows attackers with a forged license response signature to deserialize malicious objects, potentially compromising the entire network access control infrastructure. Exploitation could enable data theft, lateral movement, and full system compromise. CVE-2025-10035 has been assigned the maximum severity rating of 10/10 and is listed in the CISA Known Exploited Vulnerabilities Catalog.
All GoAnywhere MFT versions prior to 7.8.4 and Sustain Release versions prior to 7.6.3 are vulnerable. Users of GoAnywhere MFT are strongly advised to upgrade their instances to the latest patched version as outlined in the official vendor advisory.
GoAnywhere MFT is a web-based managed file transfer tool that helps organizations securely transfer files and maintain audit logs of those who access the shared files. Fortra (formerly known as HelpSystems) states that its GoAnywhere software products are utilized by over 3,000 organizations, including numerous Fortune 500 companies.
Technical Overview
The vulnerability resides in the License Servlet of Fortra's GoAnywhere MFT where insufficient input validation leads to initial authentication bypass. License Servlet is a license validation mechanism for GoAnywhere MFT. Furthermore, it is classified as a deserialization vulnerability, meaning the application blindly processes serialized input. This means that the system is assuming the incoming data is safe and verified. Without proper verification, the system cannot verify whether the information it receives is safe. If an attacker sends specially crafted input, the system may process it as if it were fully validated and trusted, which may result in attacker-controlled code.
Triggering Vulnerability
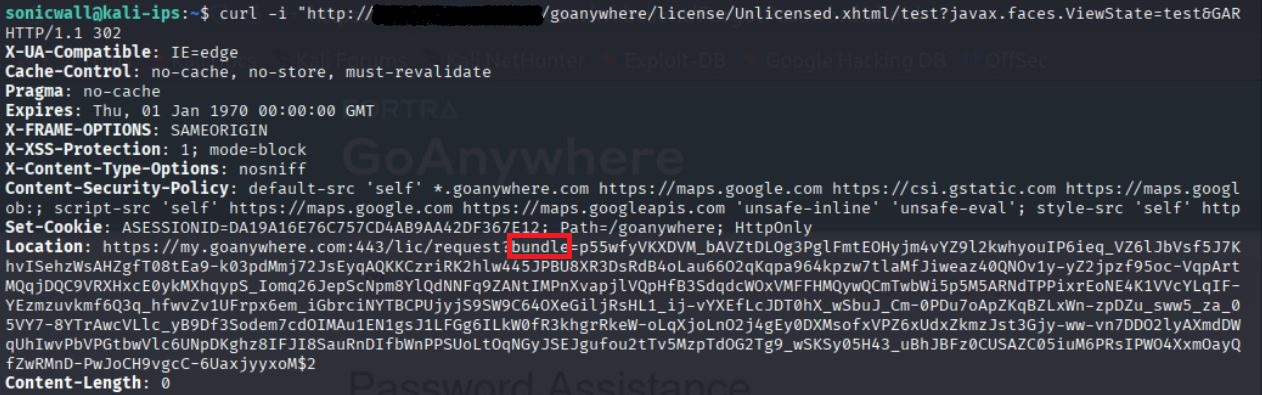
A threat actor able to manipulate the vulnerable endpoint, /goanywhere/lic/accept/<GUID> and retrieve a valid GUID by sending a crafted HTTP GET request bypasses authentication without any user interaction. In the License Servlet mechanism, the user-supplied license key is considered valid once it passes all the checks shown in Figure 1.

If the MFT version is vulnerable, the bundle parameter throws an encrypted hard-coded key that contains a valid GUID when decrypted. Once the token provided by the user matches LicenseAPI.getResponse the vulnerable MFTs will allow server-side deserialization to the underlying input.

The method shown in Figure 2 builds a redirect URL to the GoAnywhere license server, embedding the signed license request inside an HTTP GET bundle parameter.
Figure 3, in response, shows the server redirects and returns a bundle parameter (the license request) plus a cookie where the generated token has been attached. To obtain a valid GUID, the bundle parameter must be decrypted.
In a typical attack scenario, the adversary sends a specially crafted POST request with a valid retrieved GUID to the vulnerable endpoint. Then an attacker can interact with License Servlet and bypass authentication. The target endpoint is /goanywhere/lic/accept/<GUID>. The attacker's request includes a malicious payload containing embedded system commands designed to inject arguments or execute scripts.
Exploitation
Following successful exploitation, attackers typically gain shell access or execute arbitrary commands on the vulnerable GoAnywhere MFT platforms. The following is an example of a typical attack flow.
- Authentication bypass to generate a valid license token.
- The bundle parameter carries a serialized Java object that the server decrypts during processing, retrieving a valid GUID.
- Insecure Server-side Deserialization in License Servlet allows an attacker to control a serialized object.
- A malicious request to achieve Command Injection via Insecure deserialization is shown in Figure 4.

SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 21505 Fortra GoAnywhere MFT Authentication Bypass 3
Remediation Recommendations
Users of GoAnywhere MFT are strongly advised to upgrade their instances to the latest patched version as outlined in the official vendor advisory. The company also advised customers to try to find out if they were impacted by monitoring Admin Audit logs for suspicious activity and check if the log files contain stack trace errors with the SignedObject.getObject string.
Relevant Links
Share This Article

An Article By
An Article By
Dhiren Vaghela
Dhiren Vaghela
Dhiren Vaghela has over a decade of experience in the IPS domain, with a strong focus on defensive security. His expertise lies in identifying, analyzing and mitigating vulnerabilities. Dhiren is well-versed in content-based signature writing, scanner-based alert generation and technical blog writing. By leveraging emerging technologies, he has developed numerous IPS signatures across various protocols. Known for his exceptional signature writing skills and collaborative team spirit, Dhiren is a valuable asset in the field of cybersecurity.
