Oracle E-Business Suite Under Siege: Active Exploitation of Dual Zero-Days

Overview
The SonicWall Capture Labs threat research team became aware of multiple remote code execution vulnerabilities in Oracle E-Business Suite, assessed their impact and developed mitigation measures. Oracle E-Business Suite (EBS) is a comprehensive suite of integrated applications that helps organizations manage key business operations across areas like enterprise resource planning (ERP), supply chain management (SCM), and customer relationship management (CRM).
Two critical vulnerabilities, identified as CVE-2025-61882 and CVE-2025-61884, have been discovered in Oracle E-Business Suite, affecting versions 12.2.3 through 12.2.14. These flaws enable remote attackers to execute arbitrary Java code via XSL template injection, posing a significant risk to enterprise environments. Not only are those vulnerabilities flagged by CISA as being exploited in the wild, but also reportedly widely leveraged by the Cl0P ransomware group in a coordinated global extortion campaign. The situation has escalated further, with a working exploit leaked publicly, fueling widespread interest and making these vulnerabilities a prime target for threat actors. Hence, all organizations using the Oracle E-Business Suite are strongly encouraged to update their instances to the latest patched version as a matter of urgency.
Technical Overview
At the heart of both vulnerabilities lies the same core issue: unsafe processing of user-supplied XSL templates, commonly referred to as XSLT Injection. While the specific attack chains differ between CVE-2025-61882 and CVE-2025-61884, the underlying flaw remains the same. The application fails to properly sanitize dynamic XSL input, allowing attackers to inject malicious logic into the transformation process.
CVE-2025-61882 Attack Flow
This vulnerability allows unauthenticated attackers to inject an XSL template directly via a vulnerable endpoint /OA_HTML/SyncServlet.
Malicious Template Submission: The attacker sends a crafted HTTP POST request containing a malicious XSL template to the vulnerable endpoint.
Template stored in the database without validation: The application stores the submitted template directly into the XDO_TEMPLATES_B database table.
Templates are stored with code that starts with TMP (for XSL-TEXT) or DEF (for XML), followed by 16 hex characters.
Triggering the Template Execution: The attacker then invokes the malicious template using the TemplatePreviewPG page, via a specially crafted URL:
/OA_HTML/OA.jsp?page=/oracle/apps/xdo/oa/template/webui/TemplatePreviewPG&TemplateCode=<TMP|DEF><16_HEX_CHARS>&TemplateType=<XSL-TEXT|XML>
Remote Code Execution: When the URL is accessed, the injected XSL is parsed and executed, resulting in arbitrary Java code execution within the context of the application.
CVE-2025-61884 Attack Flow
Unlike CVE-2025-61882, which is a straightforward exploit, CVE-2025-61884 involves a more complex attack chain. It allows unauthenticated attackers to inject malicious XSL templates using a combination of Server-Side Request Forgery (SSRF) and Carriage Return Line Feed (CRLF) injection vulnerabilities. The vulnerable endpoint in this case is /OA_HTML/configurator/UiServlet.
SSRF via UiServlet: The endpoint includes a return_url parameter that does not validate user-supplied input, allowing attackers to manipulate the application into sending arbitrary HTTP requests to both internal and external systems, essentially enabling SSRF.
CRLF Injection: By injecting CRLF characters (\r\n), the attacker can inject or manipulate HTTP headers within the SSRF request, allowing them to:
- Split or spoof headers
- Inject raw payload data
- Bypass internal authentication mechanisms
This chain of SSRF + CRLF is illustrated in Figure 1, showcasing how the malicious request is constructed.
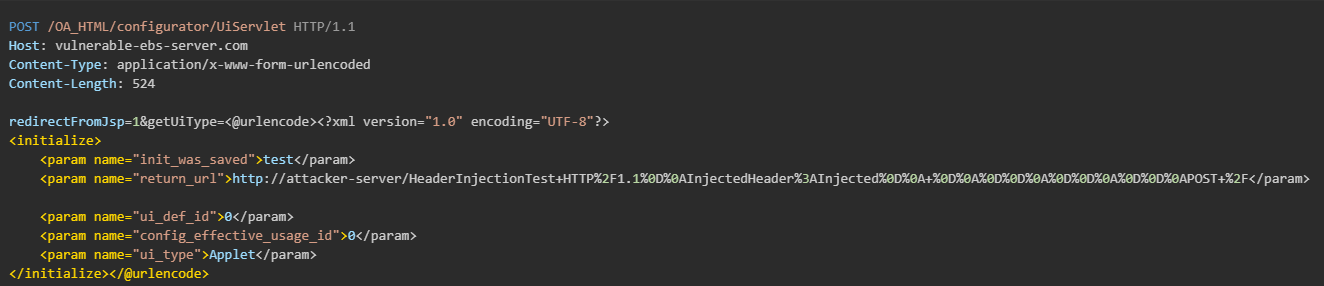
ref: watchtowr
XSL Template Fetch: The attacker’s malicious server listens for the forged request initiated by the target server. Once received, it responds with a crafted XSL template containing embedded Java code designed for remote execution.
Remote Code Execution: The victim server deserializes and processes the XSL template, resulting in arbitrary Java code execution.
CVE-2025-61882 vs CVE-2025-61884
Both vulnerabilities achieve the same goal but through different paths, direct injection in CVE-2025-61882 vs the SSRF chain in CVE-2025-61884. Figure 2 shows the key differences between the exploitation flows of both CVEs.
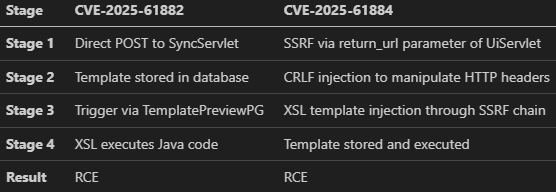
Exploitation
Successful exploitation of either CVE-2025-61882 or CVE-2025-61884 allows remote, unauthenticated attackers to achieve Remote Code Execution (RCE) by leveraging an underlying XSLT injection flaw in Oracle E-Business Suite. The structure of the malicious XSL template used in both vulnerabilities is identical and illustrated in Figure 3. The template is crafted to execute arbitrary Java code once parsed by the Oracle EBS server, effectively giving the attacker control over the system.
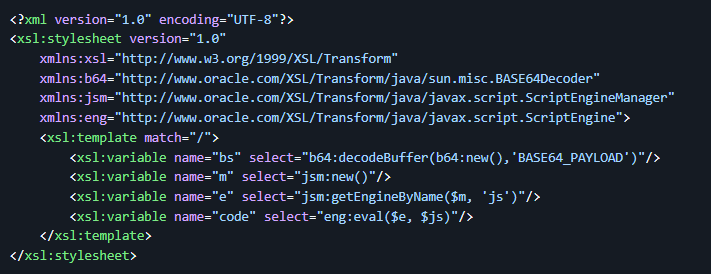
These vulnerabilities have been actively exploited in the wild since July 2025. Notably, the Cl0P group has weaponized them as part of a coordinated global campaign, compromising high-value organizations and exfiltrating sensitive corporate data for extortion purposes. The situation escalated further when the exploit code was leaked publicly, transforming the threat from a targeted campaign into a mass exploitation threat accessible to any attacker. This has dramatically increased the risk, placing any unpatched Oracle EBS instance directly in the crosshairs of cybercriminals.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 21536 Oracle E-Business Suite Possible SSRF Attempt
- IPS: 21537 Oracle E-Business Suite SSRF 2
- IPS: 21538 Oracle E-Business Suite SSRF-CRLF Injection
- IPS: 21539 Oracle E-Business Suite SSRF-CRLF Injection 2
- IPS: 21540 Oracle E-Business Suite SSRF Outbound Request
- IPS: 21581 Oracle E-Business Suite Template Injection
- IPS: 21582 Oracle E-Business Suite Template Injection Trigger 1
- IPS: 21583 Oracle E-Business Suite Template Injection Trigger 2
Remediation Recommendations
Given that Oracle E-Business Suite is deployed by thousands of enterprises worldwide, users are strongly advised to upgrade their instances to the latest patched version as outlined in the official vendor advisory.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
