LockBit 5.0: Understanding the Latest Developments in Ransomware Threats

Overview
LockBit ransomware is one of the most active and notorious ransomware-as-a-service (RaaS) operations, first appearing in 2019 and having evolved through versions that we have analyzed and written about here and here. Last year, it was reported that law enforcement seized LockBit’s infrastructure and arrested affiliates, but several copycats and spinoffs still surfaced. This week, we analyzed the newest variant, LockBit 5.0.
Infection Cycle
The newest LockBit variant introduces support for command-line parameters, a capability that was not present in previous versions. Using the -h parameter displays a help menu outlining the available command-line options.
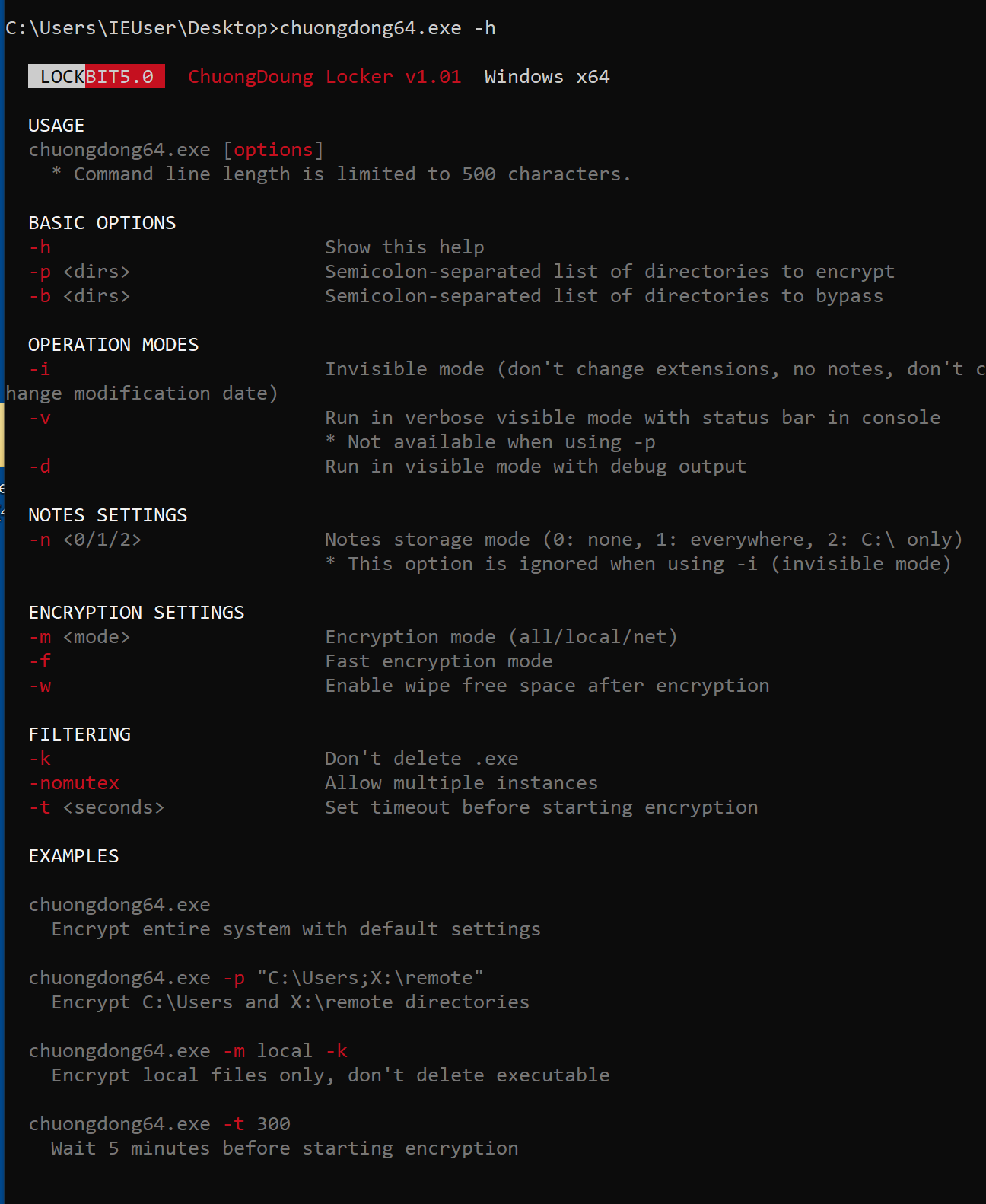
These include basic settings such as specifying target directories for encryption or directories to exclude, choosing whether the ransomware runs in stealth mode or with visible debug output, and controlling how ransom notes are deployed (either none or in all directories). Additional options allow operators to select encryption modes, apply filters (such as preventing the deletion of executable files), enable multiple instances of the malware, or configure a delay before the encryption process begins.
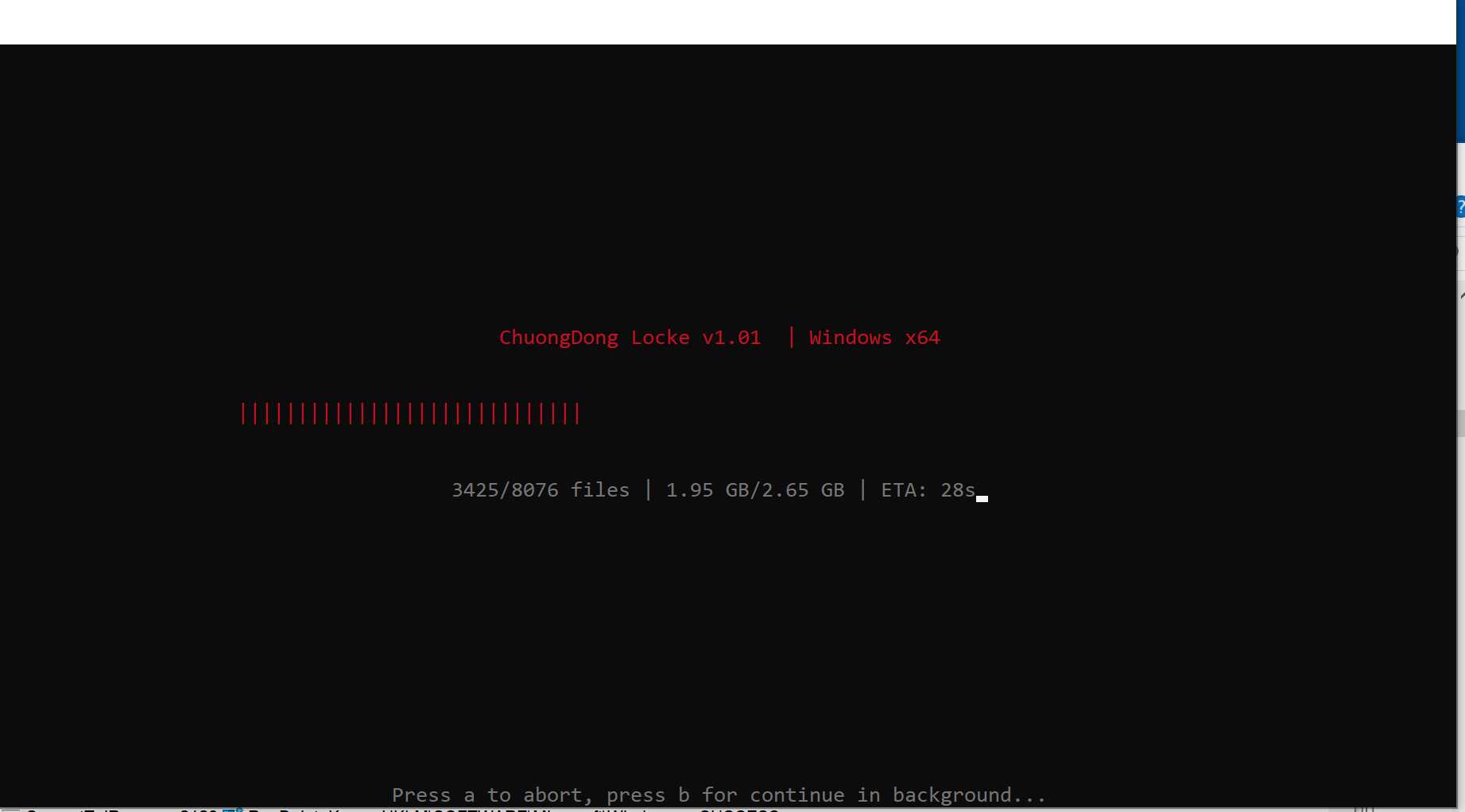
When executing in verbose mode, the program opens a console window with a status bar and provides an option to press ‘a’ to abort the operation.
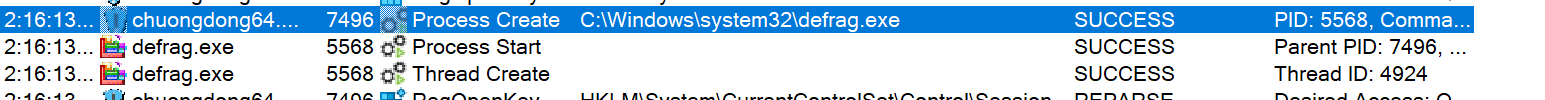
However, if launched without parameters specified, it spawns the legitimate Windows utility defrag.exe to iterate through target files and carry out the encryption process.
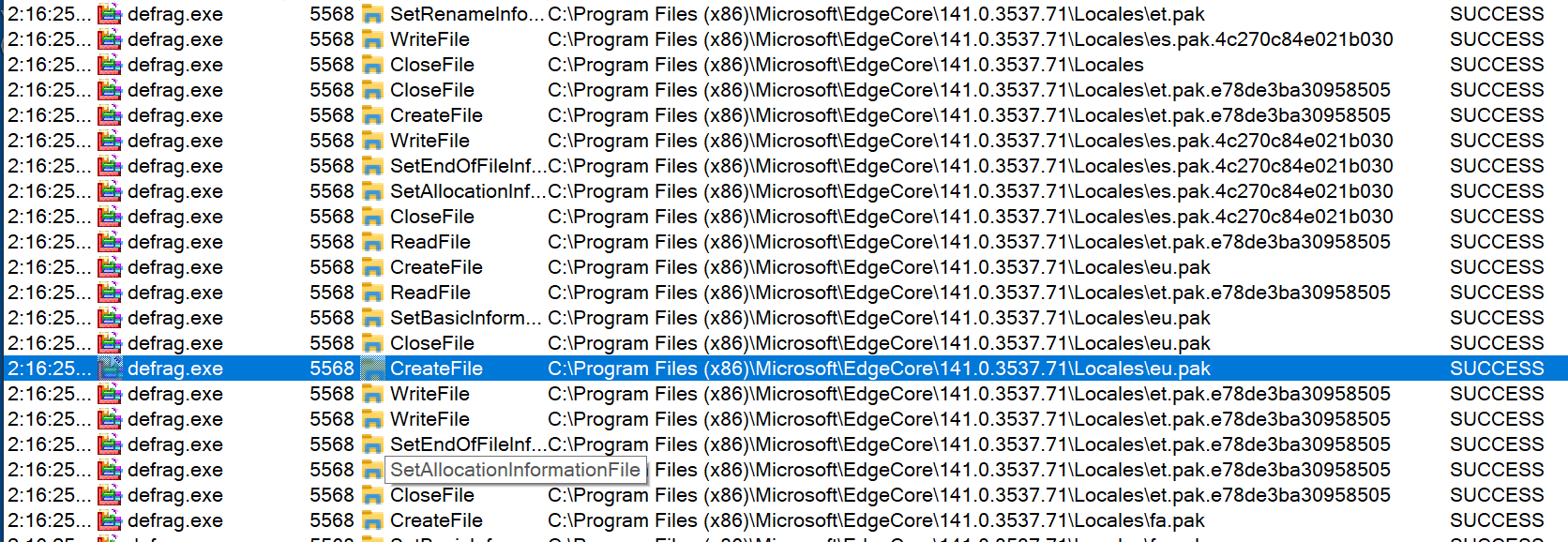
It appends a random 16-character extension to encrypted files.
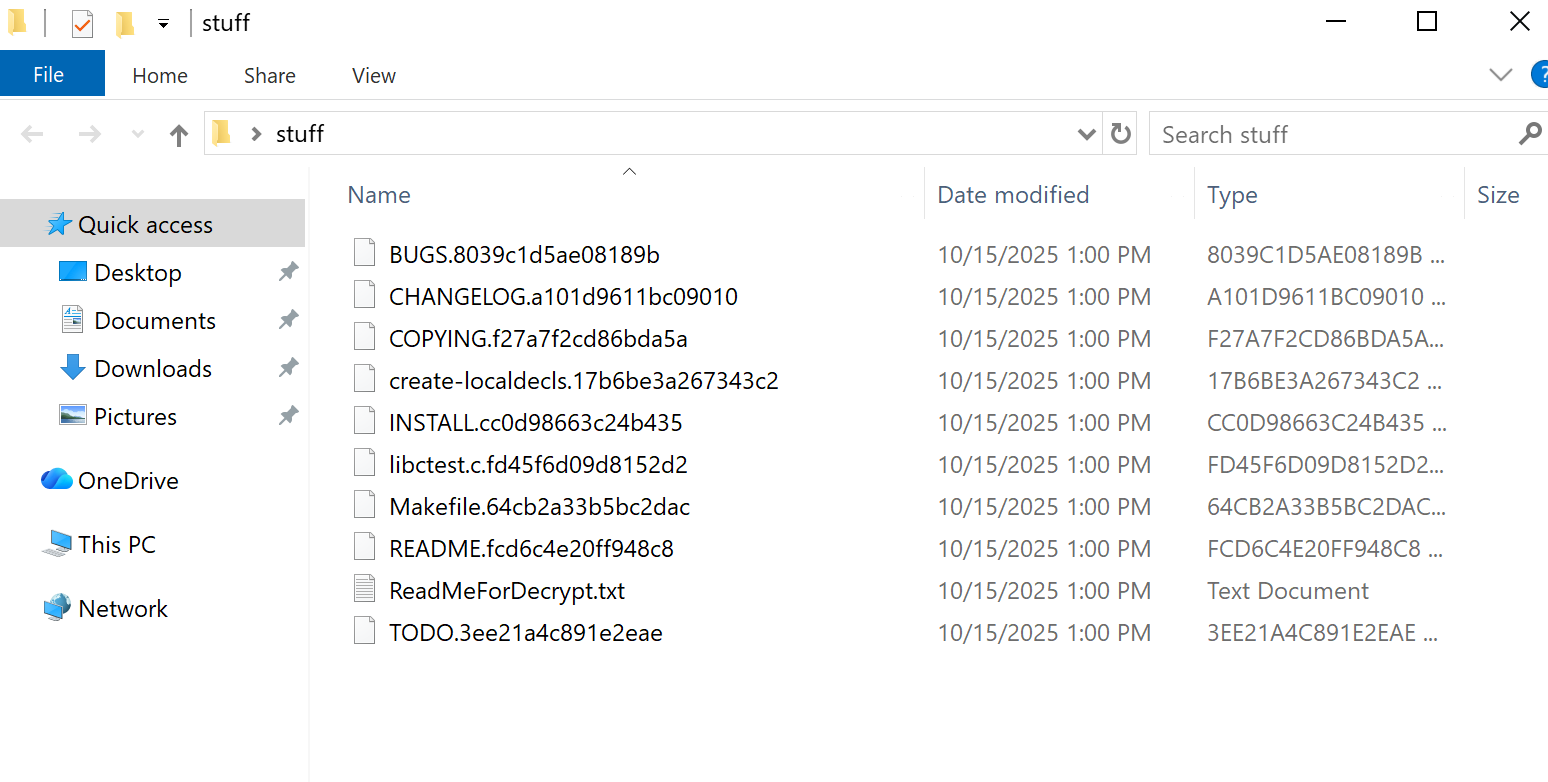
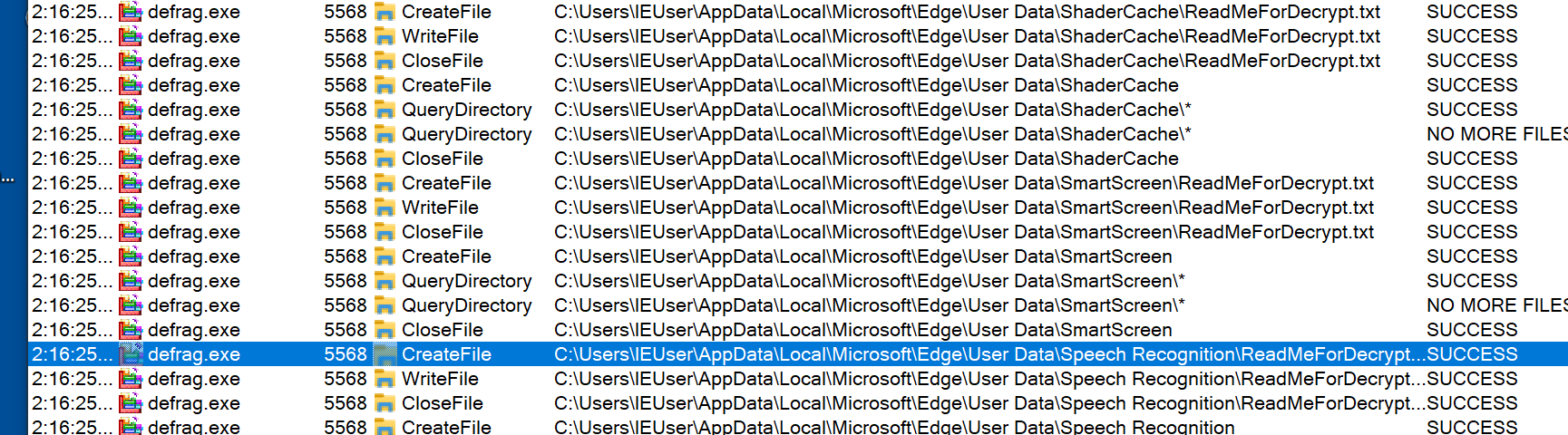
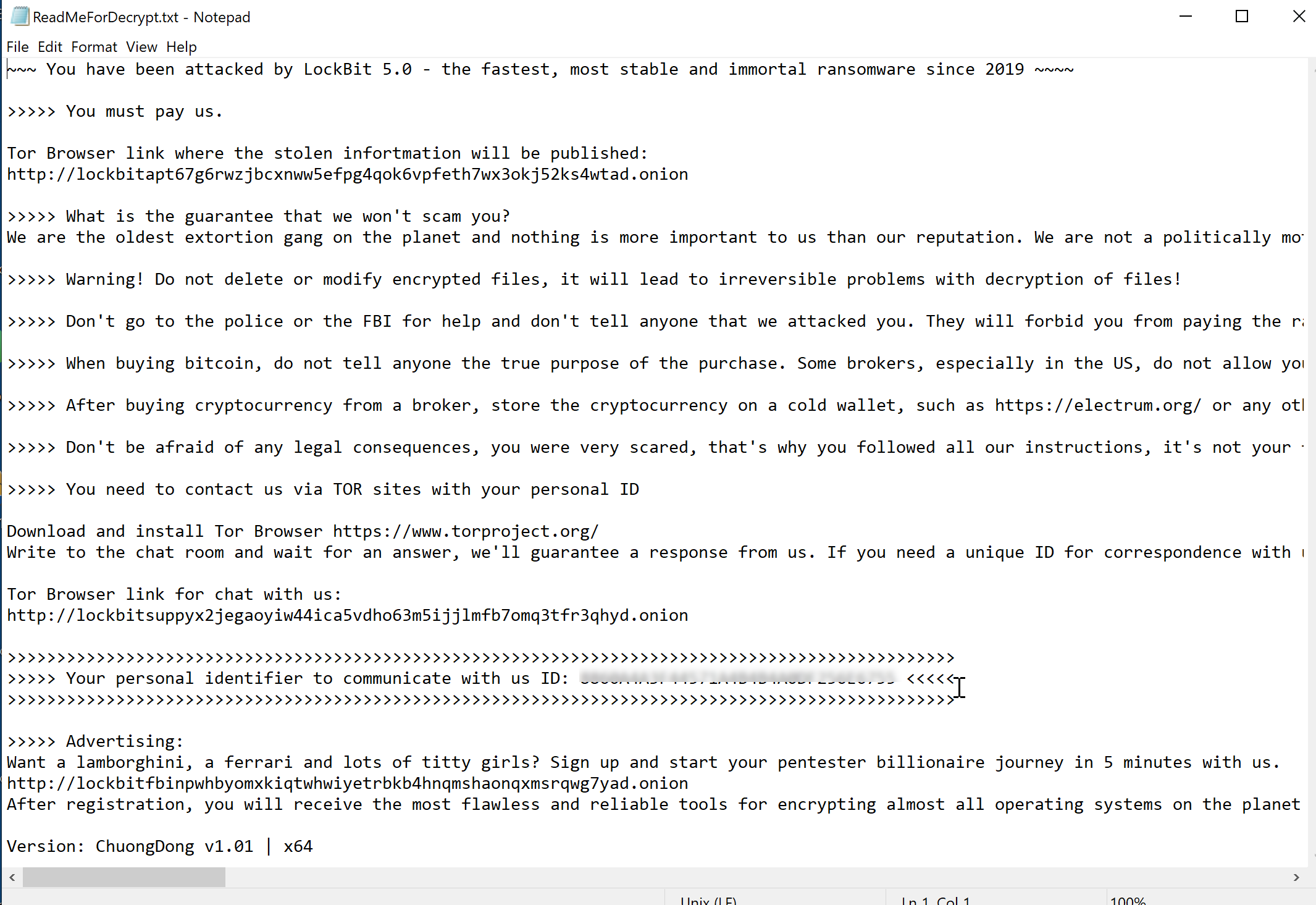
It then adds the ransomware note named ReadMeForDecrypt.txt to every directory with encrypted files.
Recently, LockBit’s official leak site was compromised and defaced with the message “Don’t do crime. Crime is bad.” The incident was first reported on X by a user under the handle “xoxofromprague,” who is believed to be responsible for the breach. Multiple cybersecurity sources have since confirmed the compromise.
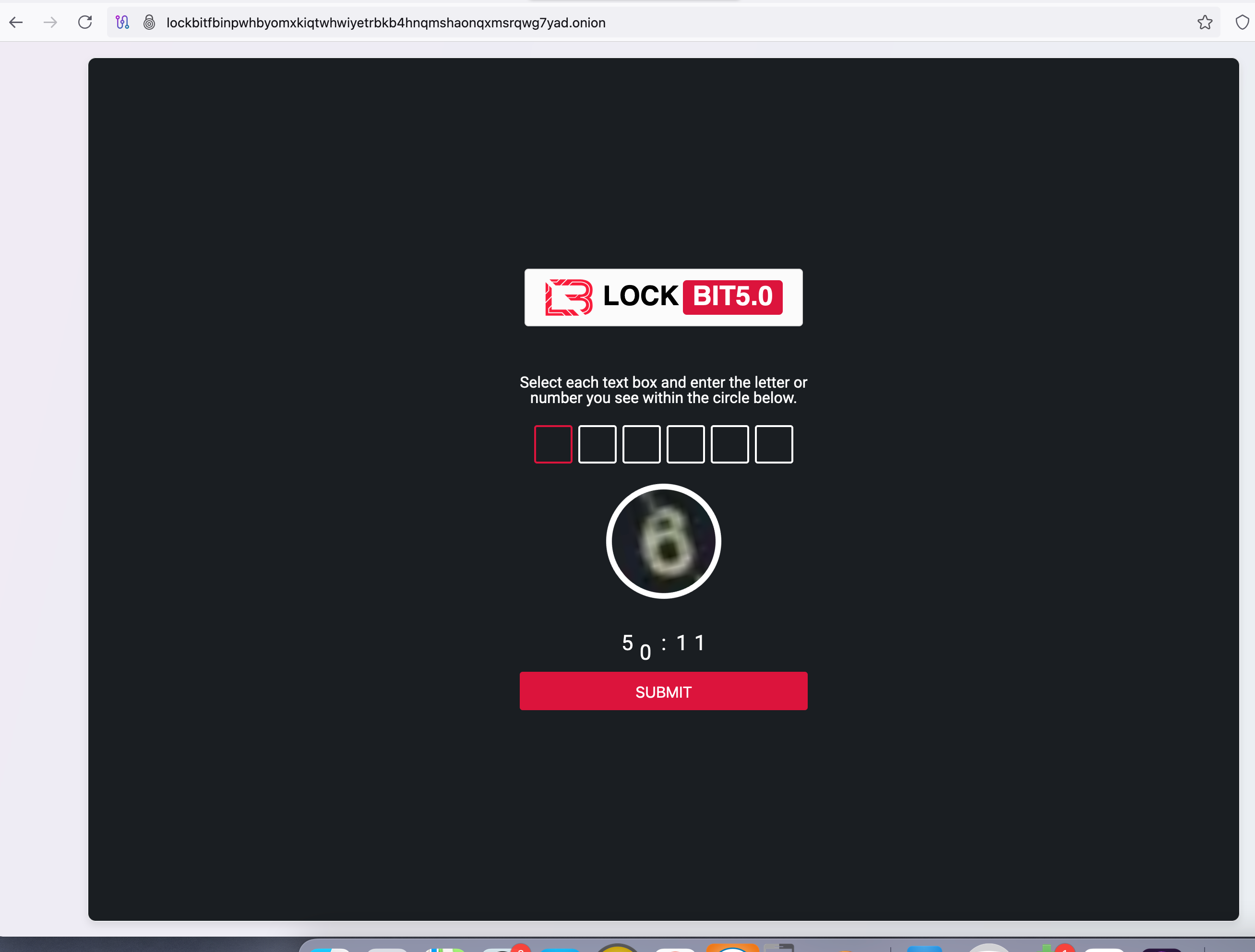
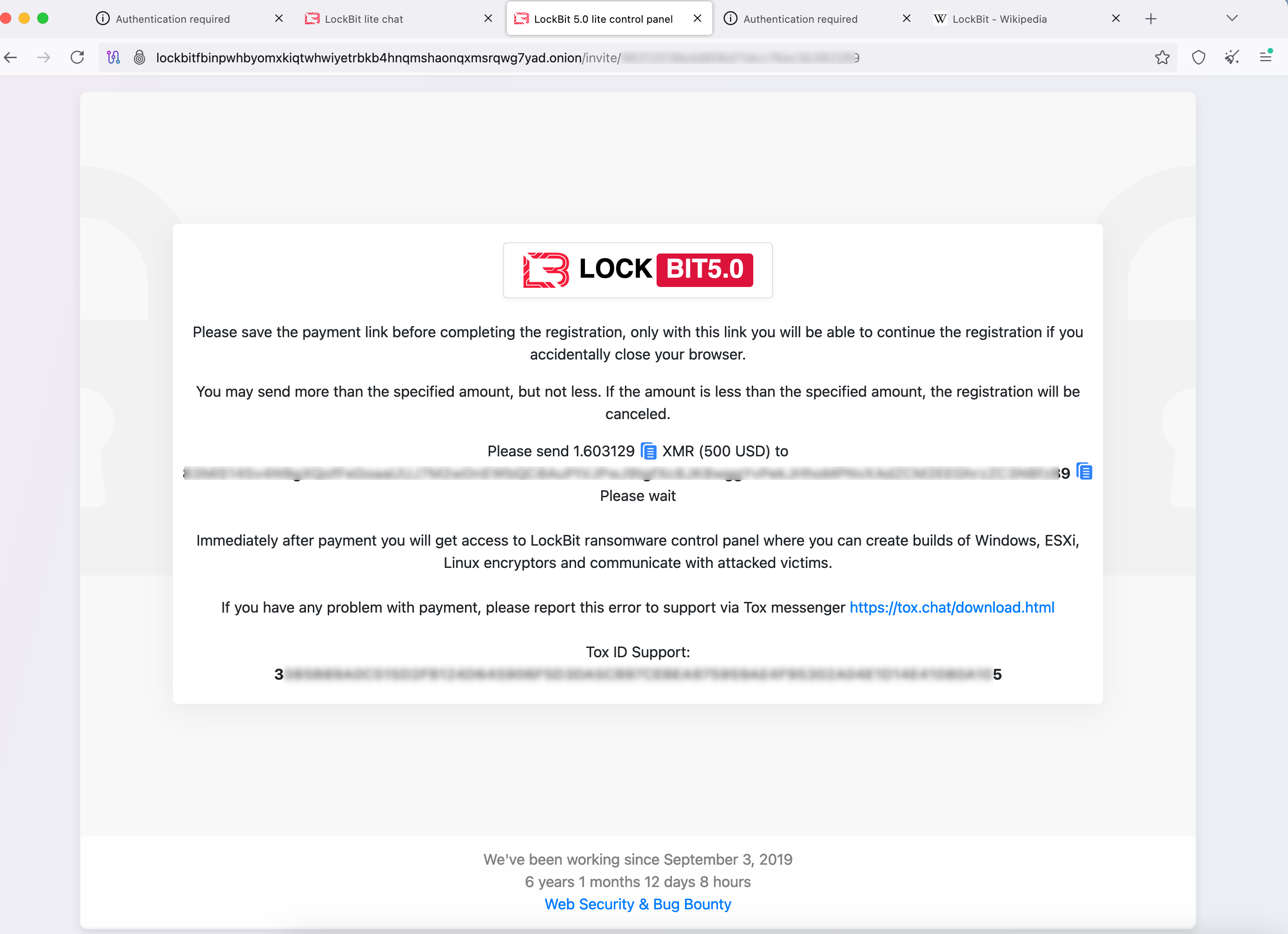
Today, LockBit’s onion site referenced in its ransom notes requires the submission of a unique access key (52 Base32 or 44 Base64 characters) as the initial authentication layer.

The affiliate portal has also implemented additional security controls, including CAPTCHA verification, mandatory account registration, and a $500 access fee payable in BTC or XMR to obtain entry to the ransomware control panel.
Protection
Since its emergence in 2019, LockBit has built one of the most durable and profitable Ransomware-as-a-Service (RaaS) operations in the cyber threat landscape. Despite multiple law enforcement disruptions, which resulted in seizures of infrastructure, arrests, and freezing of cryptocurrency wallets, LockBit has consistently recovered, adapted, and continued operations.
Recent operational enhancements (for example, stricter access controls, paywalls, and key-based authentication on their onion sites) further demonstrate that the group is investing in resiliency and infrastructure hardening. These changes indicate that LockBit’s RaaS model remains active and is unlikely to be disabled by law enforcement in the near term.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Lockbit.RSM_8 (Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI™ and the Capture Client endpoint solution.
Share This Article

An Article By
An Article By
Security News
Security News