High-Severity Open Redirect Vulnerability in Grafana Leads to Account Takeover: CVE-2025-4123

Overview
The SonicWall Capture Labs threat research team became aware of an open redirect vulnerability in Grafana, assessed its impact and developed mitigation measures. Grafana is known for creating dynamic charts, graphs, and alerts based on data sources, making it a critical component in many monitoring stacks.
Identified as CVE-2025-4123, Grafana versions 10.x, 11.x, and 12.x before v10.4.18+security-01, v11.2.9+security-01, v11.3.6+security-01, v11.4.4+security-01, v11.5.4+security-01, v11.6.1+security-01, and v12.0.0+security-01 allows an attacker to redirect users to malicious websites that host rogue plugins. These plugins can execute arbitrary JavaScript, potentially resulting in account takeover and server-side request forgery (SSRF). Given the availability of a public proof-of-concept (PoC) exploit and Grafana’s widespread use, the risk of exploitation is significantly elevated. Users are strongly urged to update to the latest patched versions immediately, as outlined in the vendor’s advisory, to protect against potential attacks.
Technical Overview
The vulnerability originates from an Open Redirect flaw in the staticHandler function, which is responsible for processing static routes. This function retrieves files from the system based on user-supplied input—a critical point of concern. What makes this particularly noteworthy is how the function resolves routes when the path points to a directory, as demonstrated in the code snippet shown in Figure 1.
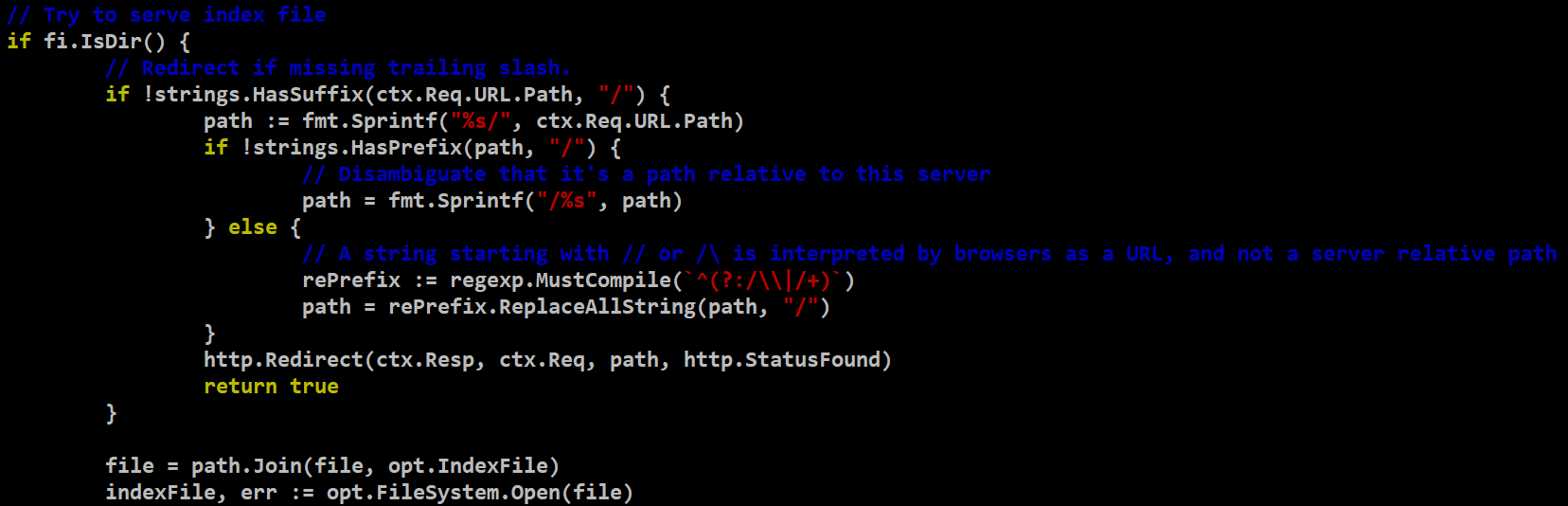
In essence, the function appends a forward slash (/) to the path and attempts to render a default file—typically something like index.html—from the resolved directory. This behavior, illustrated in Figure 2, is what makes the application vulnerable to an open redirect attack.
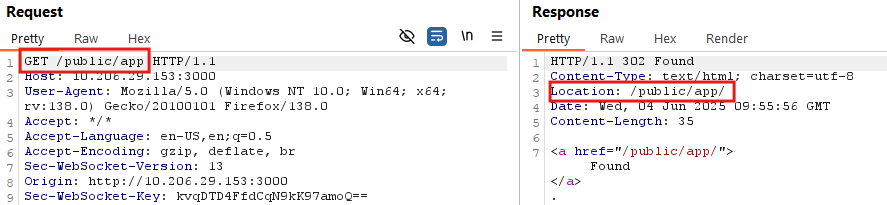
Exploitation
To exploit the open redirect vulnerability, an attacker must craft a path that triggers the IsDir() logic within the staticHandler function. This crafted path manipulates the application into redirecting the user to a malicious website—such as example.com—under the attacker’s control.
Notably, the staticHandler function utilizes opt.FileSystem.Open(file) to resolve file paths and http.Redirect(path) to perform redirections. What makes this particularly interesting is how the use of a question mark (?) can be leveraged to trigger a redirection. While opt.FileSystem.Open(file) treats the ‘?’ character as a literal part of the path, http.Redirect(path) interprets it as the start of URL query parameters. This discrepancy opens the door for a clever exploitation technique.
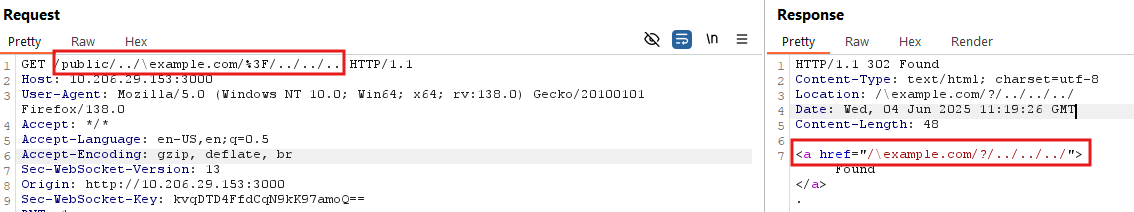
The following payload combines both open redirect and path traversal behaviors to redirect a user to a malicious domain:
/public/../\example.com/%3F/../../..
Here’s how it works:
opt.FileSystem.Open interprets this path as an empty string (“”). On the other hand, http.Redirect processes it as “/\example.com/?/../../../”. As a result, the user is redirected to the attacker-controlled domain example.com, as illustrated in Figure 3.
This redirection behavior can be further exploited to achieve account takeover through a Cross-Site Scripting (XSS) attack. The publicly available PoC demonstrates this by loading a malicious JavaScript file designed to hijack user sessions—ultimately compromising accounts. This exploitation flow is illustrated in Figure 4.
Figure 4: Exploit in action
SonicWall Protections
To ensure SonicWall customers are protected, the following intrusion prevention signatures have been released:
- IPS: 21054 Grafana Open Redirect
- IPS: 21109 Grafana Open Redirect 2
- IPS: 21110 Grafana Open Redirect 3
- IPS: 21111 Grafana Open Redirect 4
Remediation Recommendations
Grafana users are strongly advised to upgrade their instances to the latest patched version as outlined in the official vendor advisory. For those unable to apply the update immediately, a temporary workaround involves configuring a strict Content Security Policy (CSP) to mitigate the risk. An example configuration is provided below.
content_security_policy = true
content_security_policy_template = """script-src 'self' 'unsafe-eval' 'unsafe-inline' 'strict-dynamic' $NONCE;object-src 'none';font-src 'self';style-src 'self' 'unsafe-inline' blob:;img-src * data:;base-uri 'self';connect-src 'self' grafana.com ws://$ROOT_PATH wss://$ROOT_PATH;manifest-src 'self';media-src 'none';form-action 'self';"""
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
