GuLoader Brings the Noise — and the Obfuscation

Summary
This week the SonicWall Capture Labs threat research team analyzed a sample of GuLoader, a dropper and infostealer capable of harvesting credentials, evading AV, and creating persistence through a variety of techniques. It drops a number of files and uses them as timers and canaries to ensure uptime on the victim system.
Technical Analysis
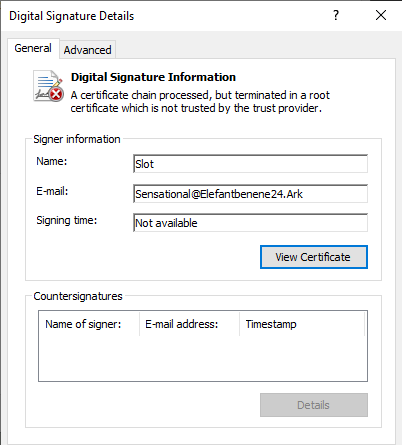
The initial sample is an NSIS installer package. It has an expired digital certificate from “Slot,” along with a non-existent email address.
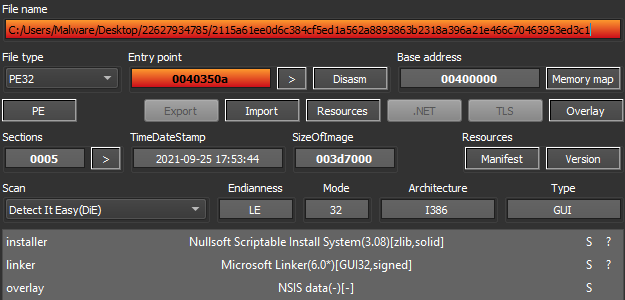
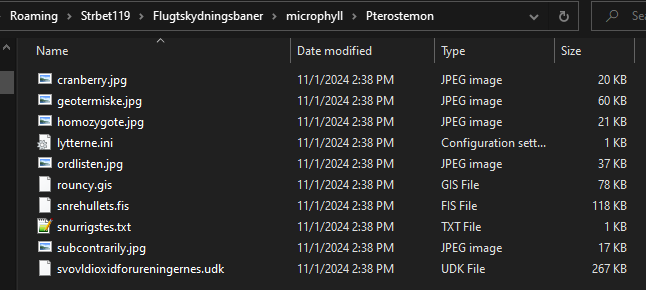
When unpacked using 7-Zip, there are multiple files in a variety of file types and nested directories. Each text file is encoded, and the images are all unrelated.
Directory tree:
- $PLUGINSDIR
- System.dll
- Microphyll
- Pterostemon
- Cranberry.jpg
- Geotemiske.jpg
- Homozygote.jpg
- Lytterne.ini
- Ordlisten.jpg
- Rouncy.jpg
- Snrehullets.fis
- Snurrigstes.txt
- Subcontrarily.jpg
- svovldioxidforureningernes.udk
- cataphoria.jpg
- Grillstegte53.txt
- Kaffefldernes.exe (main executable)
- Harmin.For
- Sandspit.jpg
- Selvbestemmelsesreten186.ist
The DLL “System.dll” is not obfuscated or packed, and based on research appears to be a valid, if not harmful, library used by GuLoader to perform reconnaissance during runtime. These same files are dropped to the following path once the installer runs:
C:\users\User\AppData\Roaming\Strbet119\Flugtskydningsbaner
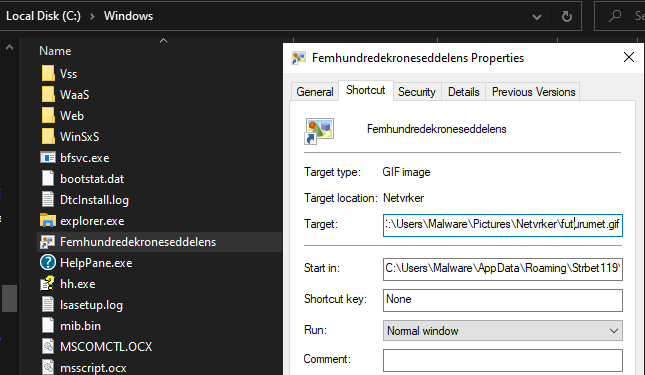
An additional shortcut is dropped to C:\Windows\Femhundredekronesddelens that points to a file named “futurumet.gif”; however, that file is written to disk during installation and immediately deleted. Each .txt or .ini file has text that is encoded, but none of the files were decoded during or after runtime. Here is an example from “Grillstegte53.txt”:
Elektroteknikker picenian bydrengenes erotomaniens fourier biometrisk lvskovenes
;magnetpladerne germanere panentheism,karrusellerne reanimalizes shanty
tangentinstruments beridernes outpassed hereticise.Semicolonial mellemtrins phyllostomidae
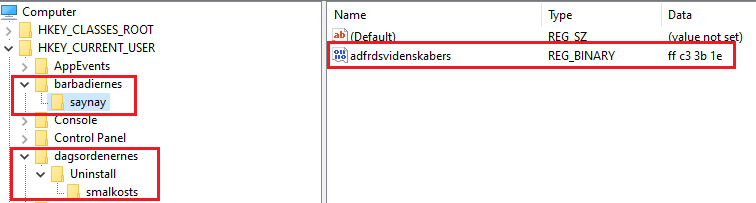
Registry keys written:
- HKEY_CURRENT_USER\barbadiernes\saynay (Value: adfrdsvidenskabers, FF C3 38 1E)
- HKEY_CURRENT_USER\dagsordenernes\Uninstall\smallkosts (Value: likvidationer, 0)
Once installation completes, the window closes and the running process creates a new non-existent process to evade security and monitoring tools. To prevent analysis on the process, the user token is changed to allow debug privileges and it loops to prevent the new process from starting. The program also creates a separate stack and suspended threads with guard pages to prevent analysis on specific memory regions. Regular checks are performed on the debug string output and debugger checks to evade and prevent tools from interfering with the runtime.
Anti-analysis capabilities used:
- Time (GetTickCount, GetFileTime, RDTSC checks)
- Process enumeration (GetToolhelp32Process)
- Active window enumeration (GetWindowRect, GetDlgItem)
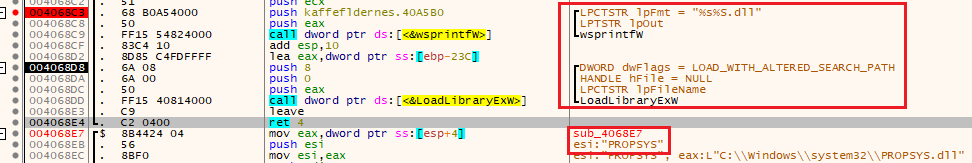
GuLoader uses dynamic API calls and library loading to assist with further levels of obfuscation. Multiple libraries, such as propsys.dll, uxtheme.dll, clbcatq.dll, and others are loaded in function sub_406877 with an altered search path.
WMI calls observed:
- IWbemServices::CreateInstanceEnum - root\cimv2 : Win32_BaseBoard
- IWbemServices::CreateInstanceEnum - root\cimv2 : Win32_Processor
- IWbemServices::CreateInstanceEnum - root\cimv2 : Win32_NetworkAdapterConfiguration
Registry keys queried:
- HKEY_CURRENT_USER\Software\IncrediMail\Identities
- HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume
- HKEY_CURRENT_USER\SOFTWARE\Martin Prikryl\WinSCP 2\Sessions
Known program paths queried:
- C:\Users\user\AppData\Roaming\Microsoft\Credentials\
- C:\Users\user\AppData\Local\Microsoft\Edge\User Data\
- C:\Users\user\AppData\Local\Google\Chrome\User Data\
- C:\Users\user\AppData\Roaming\Flock\Browser\profiles.ini
- C:\Users\user\AppData\Roaming\Postbox\profiles.ini
- C:\Users\user\AppData\Roaming\Waterfox\profiles.ini
- C:\Users\user\AppData\Roaming\Mozilla\icecat\profiles.ini
- C:\Users\user\AppData\Roaming\Mozilla\SeaMonkey\profiles.ini
- C:\Users\user\AppData\Roaming\Mozilla\Firefox\profiles.ini
- C:\Users\user\AppData\Roaming\K-Meleon\profiles.ini
- C:\Users\user\AppData\Roaming\8pecxstudios\Cyberfox\profiles.ini
- C:\Users\user\AppData\Roaming\Comodo\IceDragon\profiles.ini
- C:\Users\user\AppData\Roaming\Moonchild Productions\Pale Moon\profiles.ini
- C:\FTP Navigator\Ftplist.txt
- C:\Users\user\AppData\Roaming\Thunderbird\profiles.ini
- C:\Users\user\AppData\Roaming\NETGATE Technologies\BlackHawk\profiles.ini
With a variety of FileRead and SetFilePointer calls, the main dropped file referenced is “Harmin.For.” However, the only bytes read by GuLoader are null bytes. Additional downloaded payloads may change the activity, but that was not seen during testing. A substantial amount of activity is clouded by bytes being compared from a .tmp file whose contents are deleted after reading. This is an example of how GuLoader can run a variety of tasks based on what other payloads feed it.
Summary
This threat is detected by SonicWall via Capture ATP and covered under the signature:- MalAgent.GuLoader.Micro
IOCs
2115a61ee0d6c384cf5ed1a562a8893863b2318a396a21e466c70463953ed3c1
8dc562cda7217a3a52db898243de3e2ed68b80e62ddcb8619545ed0b4e7f65a8
Share This Article

An Article By
An Article By
Security News
Security News
