Cacti v1.2.25 CVE-2023-49085 and CVE-2023-49084 Enable SQLi, LFI, and RCE

Overview
SonicWall Capture Labs threat research team became aware of the threat CVE-2023-49085, assessed its impact and developed mitigation measures for this vulnerability.
CVE-2023-49085 and its companion CVE-2023-49084 expose all Cacti monitoring servers up to v1.2.25 to an attack chain in which an authenticated user leverages a blind SQL-injection in pollers.php to write a malicious record into the database, then triggers a local file inclusion in link.php that reads or executes arbitrary files on the host, yielding full remote code execution (both flaws carry a CVSS v3.1 base score of 8.8 — High — and, although a public proof-of-concept exists, no confirmed in-the-wild exploitation has been reported to date). Because Cacti installations typically run under the same privileges used to poll network devices, a successful exploit can pivot from the monitoring box into switch or router management planes, alter graph data, or exfiltrate stored credentials. The bug class mix—string-concatenated SQL followed by unsanitised path traversal—illustrates how two seemingly limited flaws can combine into a shell with only low-level “Sites/Devices/Data” permissions. Administrators relying on versions 1.2.24 or 1.2.25 should upgrade immediately to v1.2.26, which introduces prepared statements for poller fields and whitelists include paths to block directory traversal (GitHub advisory).
Technical Overview
Cacti 1.2.25 ships with two authentication-required flaws that can be chained for full remote-code execution (RCE):
- CVE-2023-49085 – a classic SQL-injection bug in pollers.php
- CVE-2023-49084 – a local-file-inclusion (LFI) bug in link.php
On their own, the issues permit arbitrary database writes and arbitrary file reads. Together, anyone who can reach the Poller Management page can seize the Cacti host, dump credentials, or pivot deeper into the monitored network.
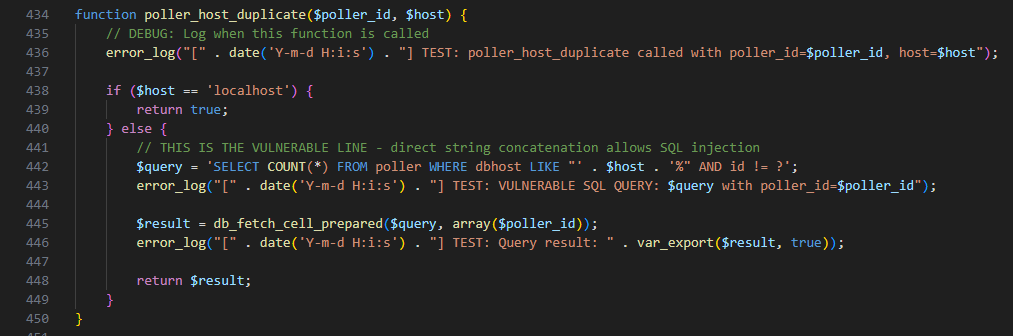
Figure 1: Vulnerable SQL construction in pollers.php
The SQL injection vulnerability arises in the poller_host_duplicate() function (Figure 01) because the $host parameter (from the 'dbhost' form field) is directly concatenated into the SQL query string without proper escaping or parameterization. An attacker can terminate the first SQL statement with a semicolon and append a malicious second statement—e.g., INSERT INTO external_links (id, contentfile, title, enabled) VALUES (99999, '....//....//....//....//....//....//....//....//etc/passwd', 'EXPLOIT', 'on');. This malicious database entry primes the subsequent Local File Inclusion (LFI) vulnerability.
When link.php?id=99999 is later requested (Figure 02), the script retrieves the attacker-controlled contentfile value from the external_links table and constructs a file path using $config['base_path'] . "/include/content/" . str_replace('../', '', $page['contentfile']) (line 78). The insufficient sanitization using str_replace('../', '', ...) can be bypassed with sequences like ....// which become ../ after the replacement. The resulting path is then passed directly to include_once($file) (line 80), enabling directory traversal outside the web root to read arbitrary system files.
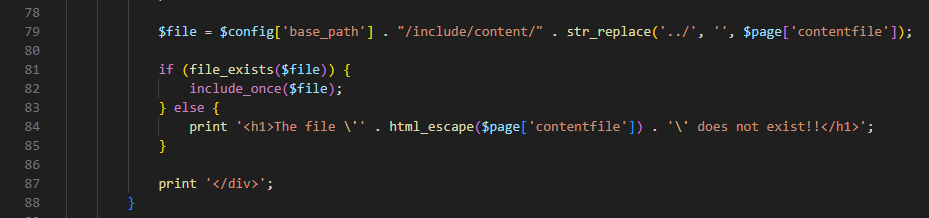
Figure 2: Unvalidated include in link.php
By first writing an attacker-controlled path (such as ....//....//....//....//....//....//....//....//etc/passwd) into the external_links.contentfile column via SQL injection, and then triggering the LFI through link.php?id=[injected_id], the adversary upgrades from database access to arbitrary file read. This can lead to command execution if combined with techniques like writing PHP shells via SELECT ... INTO OUTFILE or including uploaded files.
Version 1.2.26 breaks the exploit chain by: (1) parameterizing the SQL query in pollers.php to prevent injection, and (2) replacing the vulnerable file inclusion logic with realpath() validation a file_get_contents()instead of include_once() to prevent both directory traversal and code execution."
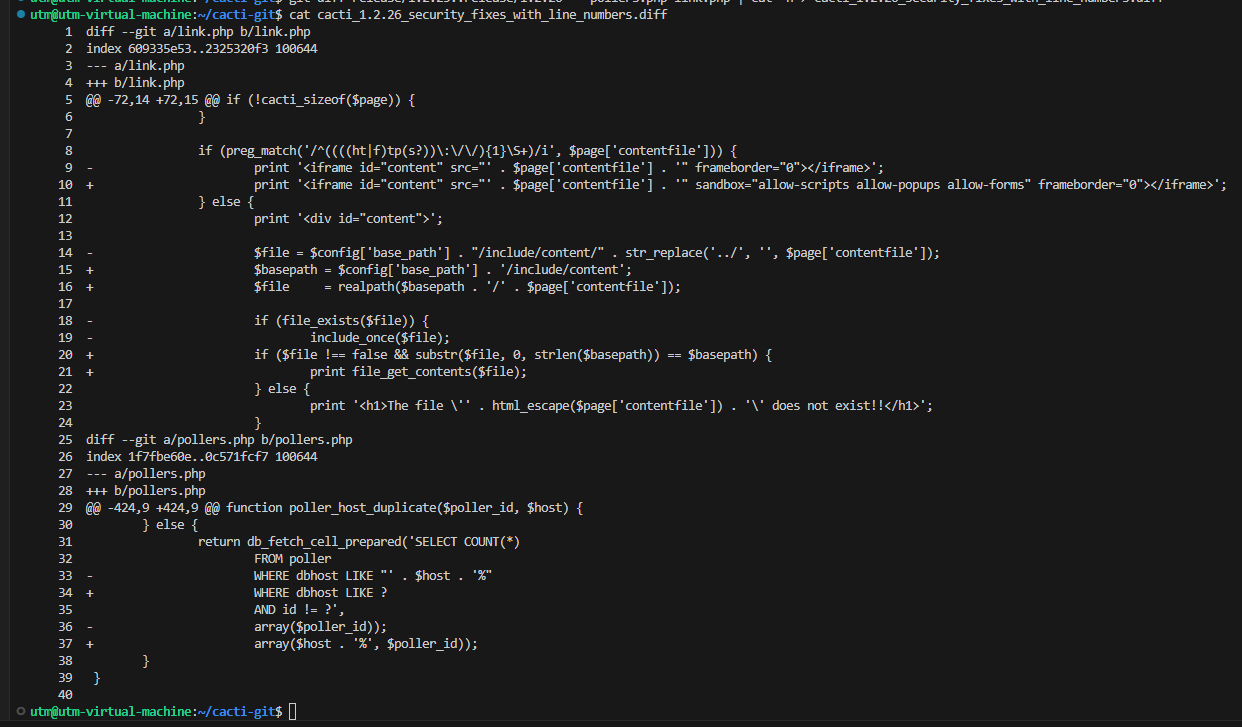
Figure 3: Unified diff showing the 1.2.26 fix
The unified diff between Cacti versions 1.2.25 and 1.2.26 reveals comprehensive security improvements that systematically address both vulnerabilities in the exploit chain. The development team implemented defense-in-depth measures, moving from dangerous string concatenation and unsafe file operations to secure parameterized queries and path validation. The changes in Figure 03 demonstrate how proper input validation and secure coding practices can effectively neutralize sophisticated multi-stage attacks:
• Lines 33-37: pollers.php now uses placeholders, binding $host through ? and eliminating SQL injection.
• Lines 14-21: link.php resolves the requested path with realpath(), confirms it still begins with the authorized base directory, and reads it with file_get_contents() instead of executing it. The <iframe> for external content also gains sandbox="allow-scripts allow-popups allow-forms" for defense-in-depth.
The edits above collectively remove the SQL-injection vector, block local-file inclusion, and tighten the browser sandbox, making Cacti 1.2.26 the first release immune to this exploit chain.
Triggering the Vulnerability
In a lab VM running Cacti 1.2.25, an attacker with only “Sites/Devices/Data” privileges can chain the blind SQL-injection in pollers.php with the local-file-inclusion in link.php without bespoke tooling. At a high level the workflow is:
- Authenticate with any low-privilege operator account.
- Inject a crafted poller entry whose hostname closes the original SQL statement and inserts a malicious record into external_links that points outside the web root (for example, to /etc/passwd).
- Trigger the LFI by requesting link.php?id=<malicious_id>, causing PHP to include the chosen file.
- Verify success by inspecting the HTTP response for the expected file contents (e.g., seeing “root:x:0:0” confirms arbitrary read).
- Optional RCE —if you first place a PHP shell on disk (via a separate upload flaw or filesystem access), set the link to that file and repeat the request to execute code as www-data.
Exploitation
Once link.php processes the malicious ID, PHP resolves the relative path components and attempts to include the targeted file. If the attacker merely wants proof of concept, pointing to /etc/passwd suffices: the browser returns the system password file, demonstrating arbitrary read. For full RCE, the adversary first uploads a one‑liner shell—either through a misconfigured image import or by abusing MySQL’s FILE privilege if enabled—then sets the external link to that location. A subsequent request executes the payload, granting a reverse shell or web command interface. Because pollers often run every five minutes, the implanted shell persists across cron‑driven processes, making detection harder.
Figure 4: /etc/passwd proof of concept
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 15952 “Cacti pollers.php SQL Injection 1”
Remediation Recommendations
The risks posed by CVE-2023-49085 (and the linked LFI) can be mitigated or eliminated by:
- Apply the vendor patch —upgrade Cacti to v1.2.26 or later, which replaces vulnerable string-concatenated SQL with prepared statements and enforces strict include-path validation.
- Utilizing up-to-date IPS signatures to detect and block malicious payloads targeting this vulnerability.
- Restrict interface exposure —bind pollers.php and link.php to trusted management networks and enforce multi-factor authentication for all operator accounts.
- Lock down database privileges —remove INSERT/UPDATE rights on the external_links table for non-administrative roles and disable the MySQL FILE privilege unless absolutely required.
- Harden the host environment —enable AppArmor or SELinux confinement for Apache, disable PHP execution in upload directories, and monitor logs for stacked-query markers (; INSERT) and traversal sequences (....//).
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
