Android banker with hardcoded financial targets

SonicWall Threats Research Team received reports of an Android banker campaign that has a multitude of features and commands at its disposal. Samples we analyzed include hardcoded financial institutions whose presence is monitored and fake login pages are shown if these targeted apps are found running on the device.
Sample Details
- MD5: 9d050ee9d306fa2228b3ddb1840bfb61
- Application Name: OLX
- Package Name: man.cube.ship
Infection Cycle
Among the permissions requested, the following are a few sensitive/dangerous ones:
- android.permission.BIND_ACCESSIBILITY_SERVICE
- android.permission.CALL_PHONE
- android.permission.GET_TASKS
- android.permission.READ_SMS
- android.permission.REAL_GET_TASKS
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.RECEIVE_SMS
- android.permission.SEND_SMS
- android.permission.SYSTEM_ALERT_WINDOW
- android.permission.WRITE_SETTINGS
Upon installation and execution, the malware does not show any screens or interface o any kind but continues to perform malicious actions in the background:
The Manifest.xml file points to a Main Activity class that gets invoked when the application runs, but this class is not see in the code base once decompiled:
This indicates that there is a possibility that a dex file containing the actual deobfuscated code is dropped when the application executes. We observe a file getting dropped in the app_DynamicOptDex folder on the device where the app gets installed. The file ZTpqTR.json is actually a DEX file that contains legible malicious code
Observations from the code
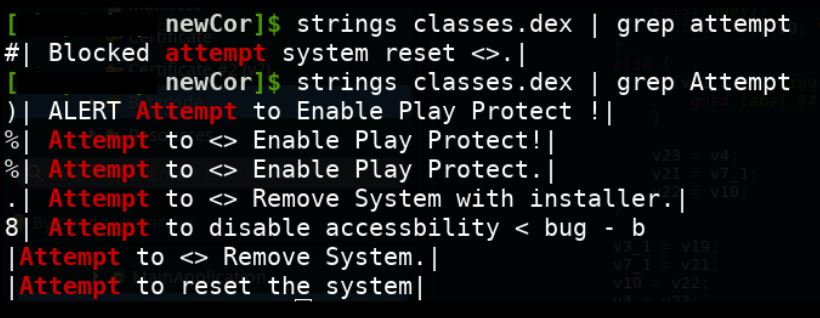
Interesting elements are present in a class file which can be considered as the configuration file. as it contains a number of hardcoded elements:
Server that the malware communicates with:
- http://ro-37[.]in/myaccount/login[.]php
A number of domains marked as Gates:
- http://analkarnavalbubenec[.]pw/3lfk3jGj/
- http://karambga3j[.]net/3lfk3jGj/
- http://lkrishtian1[.]com/3lfk3jGj/
- http://lkrishtifaa[.]com/3lfk3jGj/
A list of financial applications that the malware targets along with what looks like fake login pages uploaded on a domain (which has been taken down as of writing this blog), complete file can be viewed here
The malware has capabilities to accept the following commands and execute the corresponding functionalities:
- registration
- send_sms
- sms_contact
- sms_contacts
- get_push
- tracker
- move_sms_client
- mard_mode - spelling mistake for hard mode
- call_number
- startes_access
Network activity
The malware communicated with the following domains during our analysis:
- ro-27[.]in
- lkrishtifaa[.]com
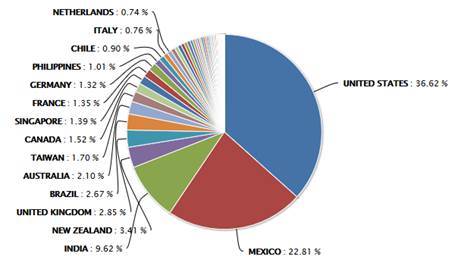
The following VirusTotal graph can be seen for this apk:
Banker Targets
The malware targets a number of financial institutions, notable targets include:
- AlfaBank - Commercial bank in Russia
- OpenBank - An online bank, headquartered in Madrid
- Tinkoff - Russian bank based in Moscow
- VTB24 - Leading universal bank of Russia
- Mbank - Banking group in Poland
- HomeCredit - An international non-bank financial institution headquartered in Netherlands
SonicWall Capture Labs provides protection against this threat via the following signature:
- AndroidOS.Banker.DR_1
Indicators of compromise (IOC):
- 9d050ee9d306fa2228b3ddb1840bfb61
Share This Article

An Article By
An Article By
Security News
Security News