New Heracles Stealer in the Wild

Overview
This week, the SonicWall Capture Labs threat research team analyzed a new sample of an infostealer dubbed ‘Heracles’, which has multiple evasion and persistence techniques. The malware is programmed to search for system credentials, installed programs and crypto currency wallets.
Technical Analysis
The file is detected as “Обязанности старшего техника на самолете ТУ-160_вч_85927_Д_Каплунов.exe”, which translates to “Responsibilities of a senior technician on a TU-160 aircraft_vch_85927_D_Kaplunov.exe”. It is a .NET executable.
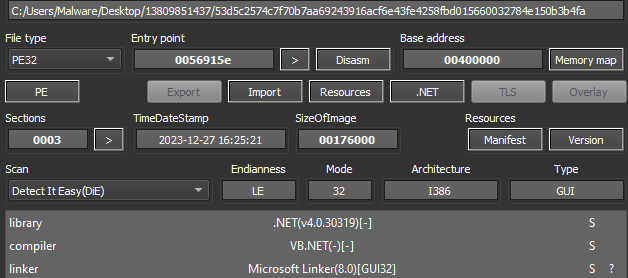
Figure 1: Sample Detection
When attempting to look at the file resources in DNSpy, the records are completely obfuscated.
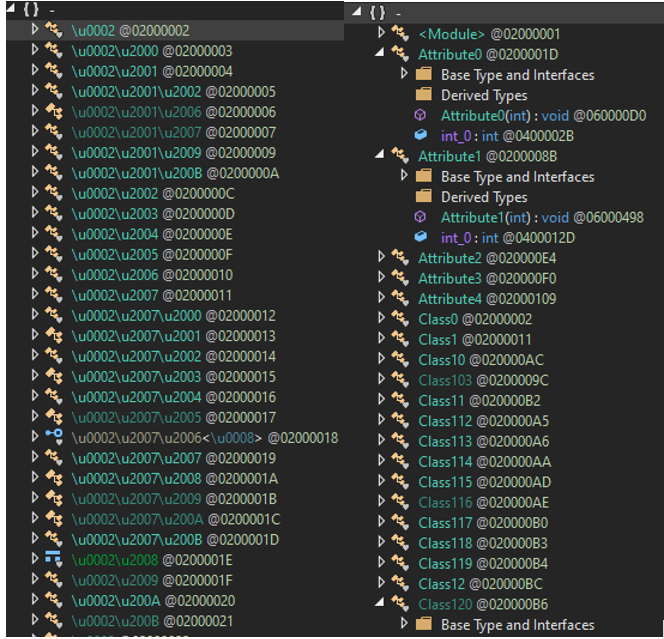
Figure 2: Obfuscated (left) and deobfuscated data (right)
Once the file has been deobfuscated, it shows hundreds of classes and attributes. In a secondary check against the deobfuscated sample, two embedded files are found. The first is ‘DotNetZip.dll’, and the second is another .NET DLL file (“zx_8d21b2346df842017090f44c62fec926.dll”). The former is used for handling zip files in memory and is a legitimate application, while the latter is a secondary payload.
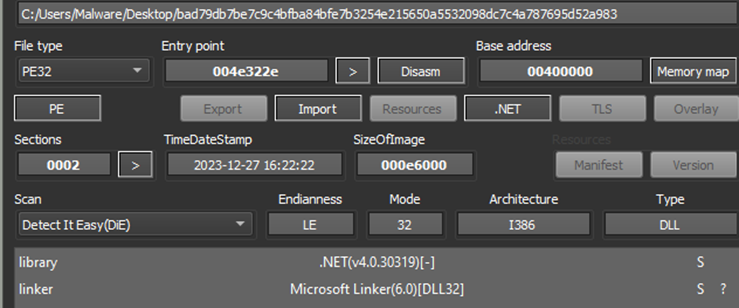
Figure 3: Payload detection
Looking at the payload sample, it shows the name “PDF_Reader” in its resource section. However, it has a number of domains listed related to cryptocurrency and dark web sites, including a .onion address.
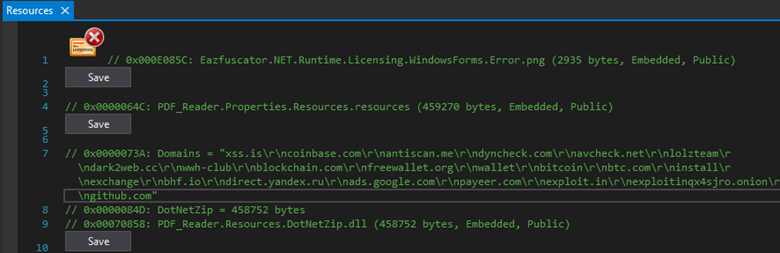
Figure 4: Domains listed in the payload, which also mentions ‘Eazfuscator’, an obfuscation tool
Once runtime occurs, the main file will perform checks against CPU features using WMI using the following queries:
- CreateInstanceEnum - root\cimv2 : Win32_Processor
- ExecQuery - root\cimv2 : SELECT ProcessorId FROM Win32_Processor
- ExecQuery - root\cimv2 : SELECT * FROM Win32_VideoController
- ExecQuery - root\cimv2 : SELECT Capacity FROM Win32_PhysicalMemory
It will also check for VMWare and QEMU virtual environments specifically while running processes and debuggers to ensure it is running on a viable system. All errors are disabled via SetErrorMode to prevent the user/system from detecting activity. Files are dropped into the following locations for persistence and staging:
- ~AppData\Roaming\
\ \Files\Local Settings\Temp - ~AppData\Roaming\
\Files\Start Menu\Programs - ~AppData\Roaming\
\Files\Start Menu\Programs\Windows Powershell - ~AppData\Roaming...\Files\Start Menu\Programs\System Tools\
- ~AppData\Roaming...\Files\Start Menu\Programs\Startup
- ~AppData\Roaming...\Files\Start Menu\Programs\Startup\Administrative Tools\
- ~AppData\Roaming...\Files\Start Menu\Programs\Startup\Maintenance\
- ~AppData\Roaming...\Files\Start Menu\Programs\Startup\Accessories\
- ~AppData\Roaming...\Files\Start Menu\Programs\Startup\Accessibility\
The main sample creates copies of itself in the ‘Temp’ location as ‘.tmp’ files. In testing, these were presented as ‘wct3D66.tmp’ or similar. For all other locations, either ‘.ini’ or ‘.lnk’ files are created that will point back to one or more of the copies. Enumeration begins by going through the main directory and looking for Microsoft Office profiles, cryptocurrency wallets and clipboard data. The main wallets are: Electrum, Ethereum, Exodus, bytecoin and Zcash.
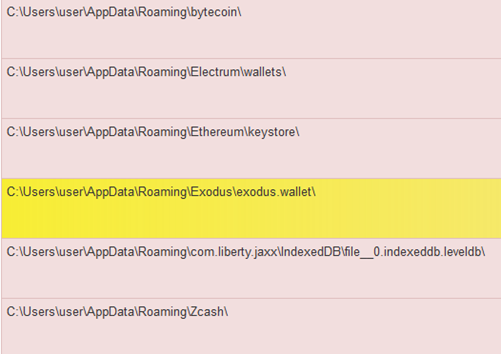
Figure 5: Wallet strings found during runtime
Data is staged in the same ‘Temp’ directory and is compressed via DotNetZip. While no network connections were made, the following IP addresses were found in memory:
208.95.112.1 (ip-api.com)
149.154.167.220 (api.telegram.org)
104.237.62.212 (api.ipify.org)
64.185.227.156 (api.ipify.org)
173.231.16.77 (api.ipify.org)
The telegram IP is used for communications, as it has been confirmed that there is a telegram group associated with this sample (‘https://t{.}me/rusvolcorp’) in other tests. Rusvolcorp is a Russian group fighting on behalf of Ukraine, but it is unknown whether this link is legitimate.
Protection
To ensure SonicWall customers are prepared for any exposure that may occur due to this malware, the following signatures have been released:
- MalAgent.Heracles.A
- MalAgent.Heracles.Payload
IOCs
-
53d5c2574c7f70b7aa69243916acf6e43fe4258fbd015660032784e150b3b4fa (Обязанности старшего техника на самолете ТУ-160_вч_85927_Д_Каплунов.exe)
-
BAD79DB7BE7C9C4BFBA84BFE7B3254E215650A5532098DC7C4A787695D52A983 (PDF_Reader.dll)
URLs
- xss.is
- coinbase.com
- antiscan.me
- dyncheck.com
- avcheck.net
- dark2web.cc
- blockchain.com
- freewallet.org
- btc.com
- bhf.io
- direct.yandex.ru
- payeer.com
- exploit.in
- exploitinqx4sjro.onion
Share This Article

An Article By
An Article By
Security News
Security News