-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to configure failover when there are two or more WAN Interfaces?



Description
WAN Failover enables you to configure one of the user-defined interfaces as a secondary WAN port. The secondary WAN port can be used in a simple “active/passive” setup to allow traffic to be only routed if the Primary WAN port is unavailable. This allows the SonicWall to maintain a persistent connection for WAN port traffic by “failing over” to the secondary WAN port, achieved when there is an automatic transfer of control when a failure in internet is detected.
The Failover and Load Balancing settings are described below:
• Enable Load Balancing - This option must be enabled for the user to access the Load balancing Groups and Load balancing Statistics section of the Failover & Load Balancing configuration. If disabled, no options for Failover & Load Balancing are available to be configured.
• Respond to Probes - When enabled, the appliance can reply to probe request packets that arrive on any of the appliance’s interfaces. This should be enabled if there is any type of probing configured under the Default LB group or the individual WAN added inside the group.
• Any TCP-SYN to Port - This option is available when the Respond to Probes option is enabled. When selected, the appliance will only respond to TCP probe request packets having the same packet destination address TCP port number as the configured value (mostly used in GMS).
Load Balancing Members and Groups
WAN interfaces (Load Balancing Members) added to a Load Balancing Group take on certain “roles”. A member can only work in one of the following roles:
• Primary - Only one member can be the Primary per Group. This member always appears first or at the top of the Member List. Note that although a group can be configured with an empty member list, it is impossible to have members without a Primary.
• Alternate - More than one member can be an Alternate, however, it is not possible to have a Group of only Alternate members. This is also called Secondary member.
• Last-Resort - Only one member can be designed as Last-Resort. Last-Resort can only be configured with other group members. It can be left empty as well.
Each member in a group has a rank. The rank is determined by the order of interfaces as they appear in the Interface Ordering for the group determining the usage preferences of the Interfaces, as well as the level of precedence within the group. Thus, the WAN on the top of the table is Primary, then secondary, and so forth.
Type (or method)
Choose the type of LB from the drop-down list (Basic Active/Passive Failover, Round Robin, Spillover-Based, or Percentage-Based). 2, 3, and 4 are Load balancing methods.
- Basic Active/Passive Failover - The multiple WAN interfaces use ‘rank’ to determine the order of preemption when the Preempt checkbox has been enabled. Only a higher-ranked interface can preempt an Active WAN interface.
- Round Robin - This option now allows the user to re-order the WAN interfaces for Round Robin selection. Round-Robin is where network requests are applied to a circular list, in a software-programmed order.
- Spillover - The bandwidth threshold applies to the Primary WAN. Once the threshold is exceeded, new traffic flows are allocated to the Alternates in a Round Robin manner. Once the Primary WAN bandwidth goes below the configured threshold, Round Robin stops, and outbound new flows will again be sent out only through the Primary WAN. Note that existing flows will remain associated with the Alternates (since they are already cached) until they timeout normally
- Ratio—There are now four fields so that percentages can be set for each WAN in the LB group. To avoid problems associated with configuration errors, please ensure that the percentage correctly corresponds to the WAN interface it indicates.
 NOTE: Failover will only work when there is more than1 interface in WAN Zone.
NOTE: Failover will only work when there is more than1 interface in WAN Zone.
To configure a new interface for WAN, please follow How can I configure an interface as secondary WAN port in SonicWall?
For queries - Wan Failover & Load Balancing FAQs
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Let's now see the configuration for Basic Failover, that is when Primary WAN is down, failover to the secondary scenario setting. Log in to the management page.
1. Navigate to Network | System and click WAN Failover & LB. The WAN Failover & LB page displays.
2. Enable the boxes Enable Load Balancing and Respond to Probes
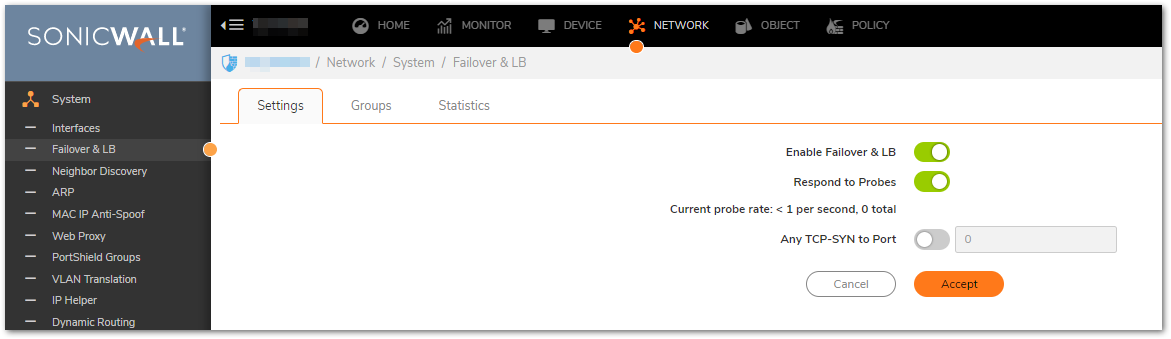
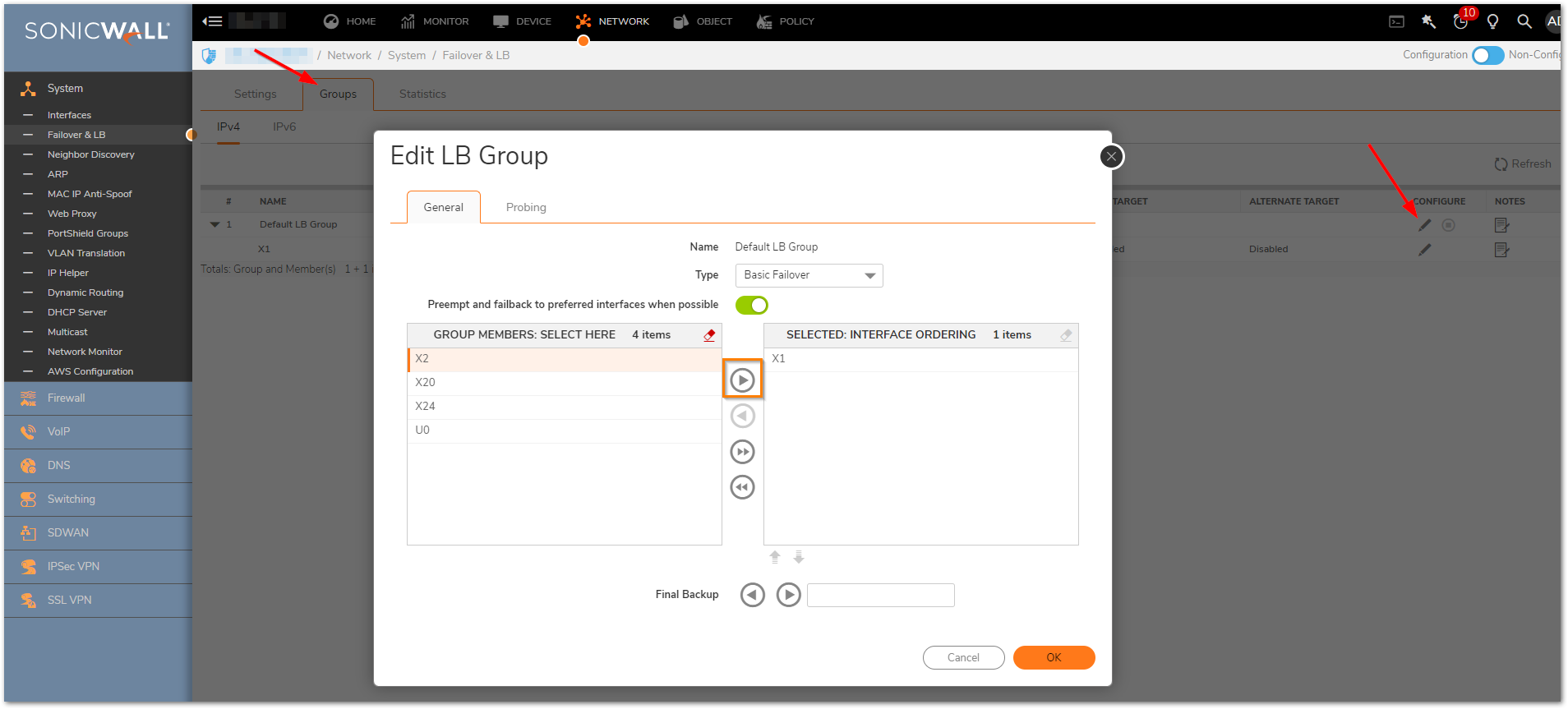
3. To configure failover, click on the tab Groups and click on the pencil/edit icon on the extreme right of the Default LB group
- Select Basic Failover
- Click on the WAN interface and push it from the left box to the right 'Interface Ordering'
- On the right box, the interface which is on top is the Primary WAN
- When the primary WAN fails to provide a connection, it enters standby and allows the secondary device to take over Internet traffic
4. Check “Preempt and failback to Primary WAN when possible” to enable immediate failback to the primary WAN when it is back online
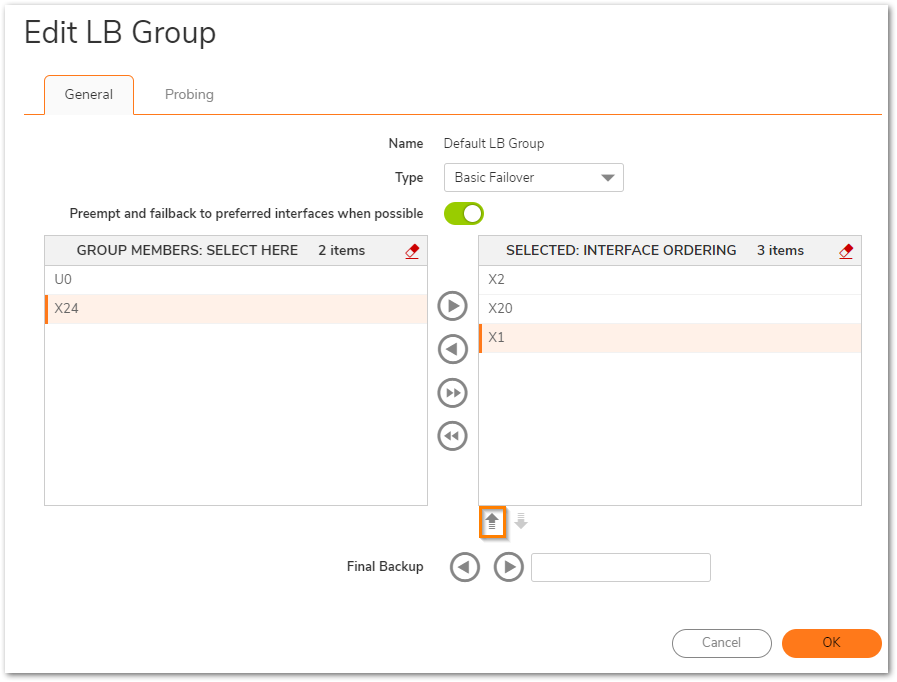
5. The arrow below the right box is used to change the priority of the WAN interface. The interface on top would always be the Primary
6. Click on the Probing tab on the same window. The default probing intervals to find out how often SonicWall should check if there is active internet on one interface and if the internet is down, how long to wait before switching to the secondary WAN.
- Specify how often the SonicWall appliance checks the interface (5-300 seconds) in the Check interface every field (default: 5 seconds).
- Specify the number of times the SonicWall appliance tests the interface as inactive before failing over in the Deactive interface after field (default: 6 times). For example, if the SonicWall appliance tests the interface every five seconds and finds the interface inactive after three successive attempts, it fails over to the secondary interface after 30 seconds. Low value ensures quick failover, however, slight internet breakage can lead to unnecessary failover/failback.
- Specify the number of times the SonicWall appliance tests the interface as active before failing back to the primary interface in the Reactive interface after field (default: 3 times). For example, if the SonicWall appliance tests the interface every five seconds and finds the interface active after three successive attempts, it fails back to the primary interface after 15 seconds.
- Probe responder.global.SonicWall.com on all interfaces in this group - Enable this checkbox to automatically set Logical/Probe Monitoring on all interfaces in the Group. When enabled, this sends TCP probe packets to the global SNWL host that responds to SNWL TCP packets, responder.global.SonicWall.com on port TCP 50000
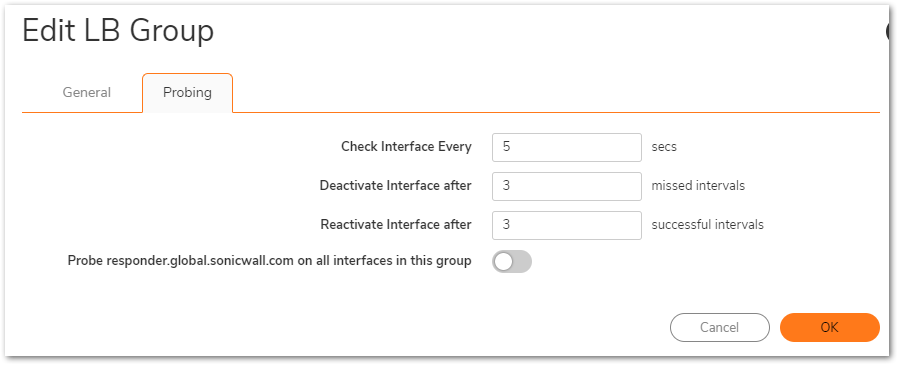
Click OK to save the changes on the Load Balancing group.
Interface Probing:
The next and most important setting that ensures proper failover is the Probing on each of the WAN interface. The SonicWall appliance can monitor the WAN connectivity by detecting whether the link is unplugged or disconnected or by sending probes to a target IP address of an “always available” target upstream device on the WAN network, such as an ISP side router. To enable probe monitoring, select Enable Probe Monitoring Under Manage | Network | Failover and Load Balancing page. Then click on the edit/pencil icon next to the WAN Interface under the LB group. Here you would be able to see 2 options:
- Physical probing - checks for Physical connectivity, like loose ethernet on WAN, WAN modem off and the like. Physical disconnection would rarely be a cause when the internet is lost.
- Logical Probing - checks for Ping (ICMP) or TCP probes to specific hosts. If selected, all the options below it then become available
Now, from the drop-down, select when probe succeeds. There are four options. And the first option is the recommended setting.
- Probe succeeds when either Main Target or Alternate Target responds.
- Probe succeeds when both Main Target and Alternate Target respond.
- Probe succeeds when Main Target responds.
- Succeeds Always (no probing). – Default; all other options are greyed.
Select the protocol (TCP or ICMP) used for monitoring and enter the IP address and port (TCP only) of the target. TCP probing is useful if you do not have ping (ICMP) response enabled on your network devices. In this case, TCP can be used to probe the device on a user-specified port. Ping can be used to any public domain name/IP address.
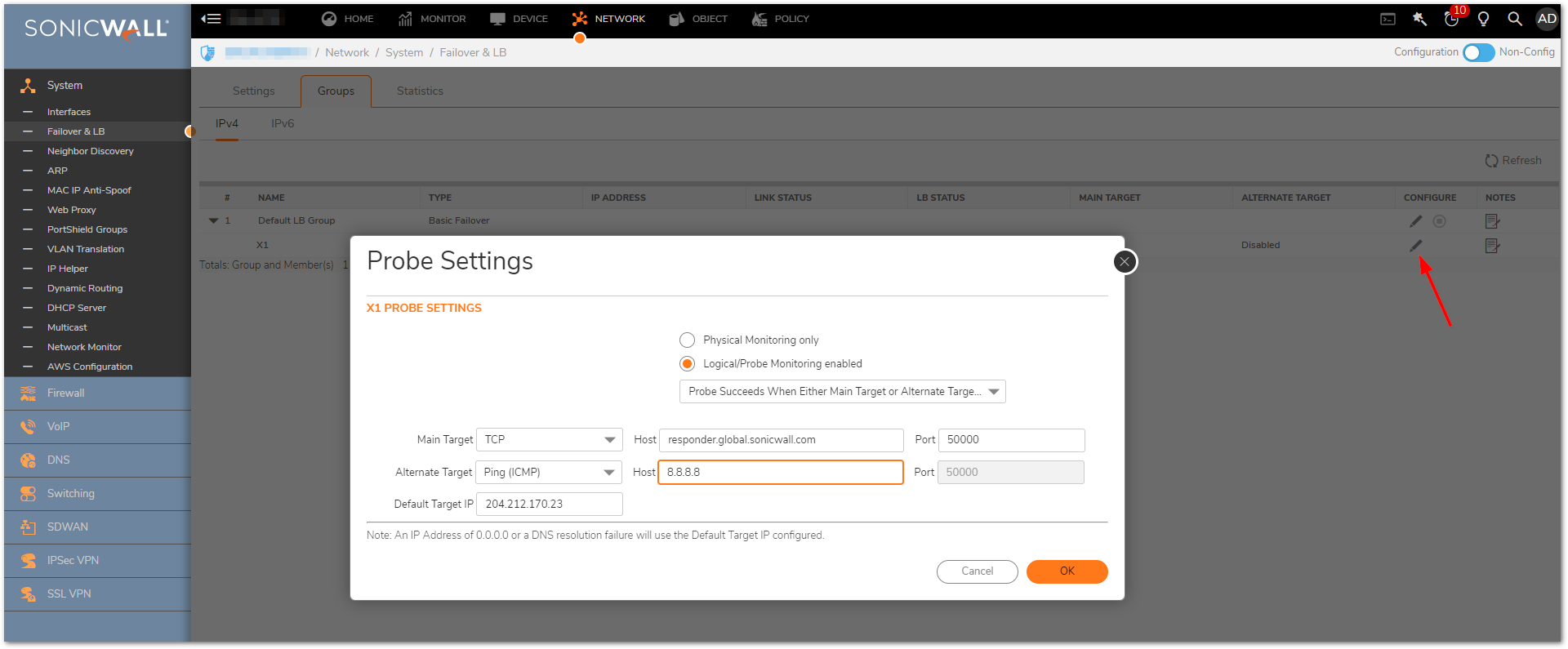
Click OK to save the changes.
This process should be repeated on each WAN interface in the LB group.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
For SonicWalls that are generation 6, we suggest upgrading to the latest release of SonicOS firmware. For the KB article to upgrade firmware How can I upgrade SonicOS Firmware?
Let's now see the configuration for Basic Failover, that is when Primary WAN is down, failover to the secondary scenario setting.
1. Expand the Manage | Network and click WAN Failover & Load Balancing. The WAN Failover & LB page displays.
2. Select Enable Load Balancing
3. To configure failover, click on the pencil icon on to the extreme right of the Default LB Group
- Select Basic Failover
- Push the WAN interfaces from the left box to the right 'Interface Ordering'
- On the right box, the interface which is on top is the Primary WAN
- When the primary fails to provide a connection, it enters standby and allows the secondary device to take over Internet traffic
4. The arrow below the right box is used to change the priority of the WAN interface. The interface on top would always be the Primary
5. Check “Preempt and failback to Primary WAN when possible” to enable immediate failback to the primary WAN when it is back online
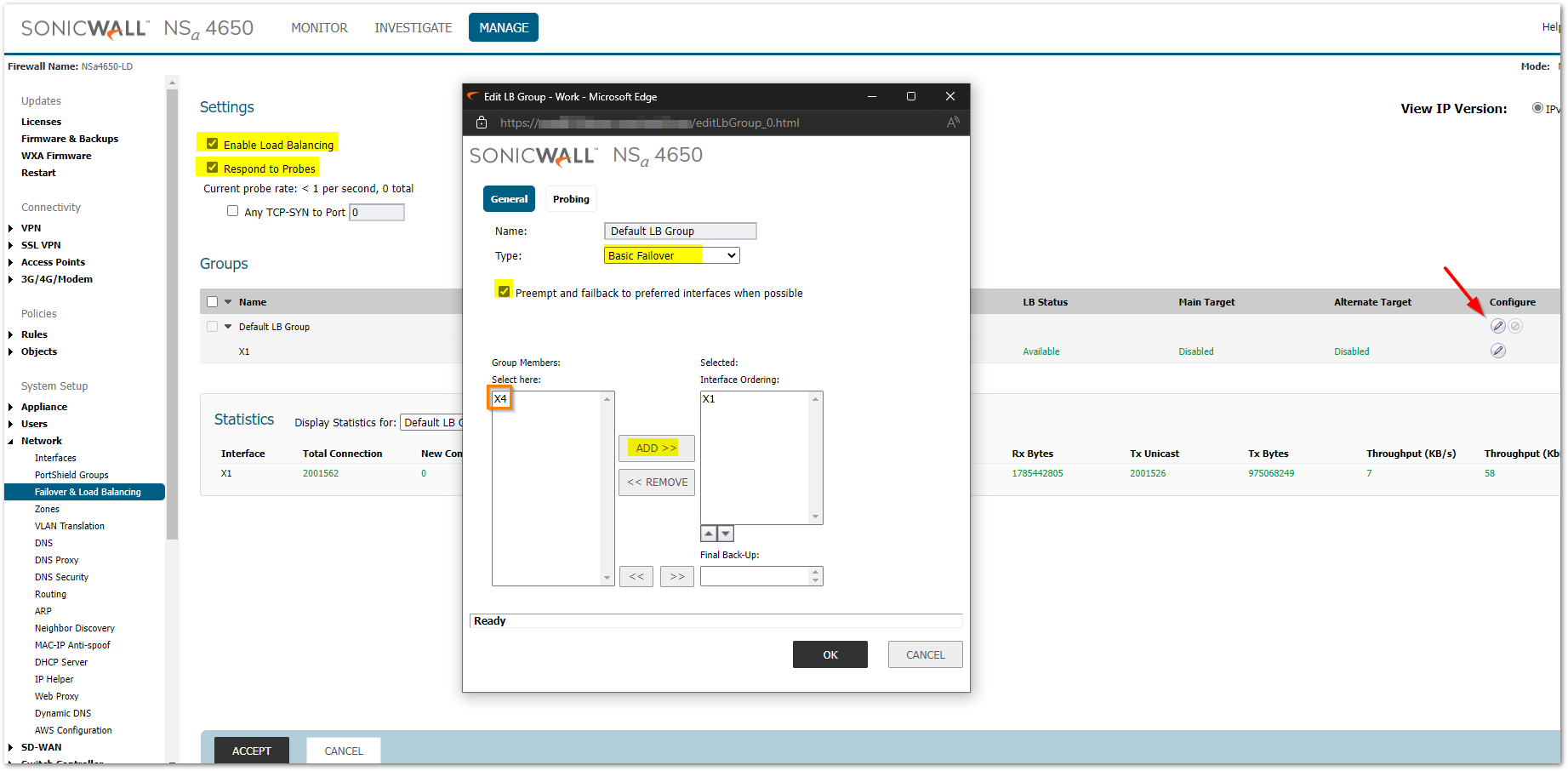
6. Click on the Probing tab in the same window. The default probing intervals to find out how often SonicWall should check if there is active internet on one interface and if the internet is down, how long to wait before switching to the secondary WAN.
- Specify how often the SonicWall appliance checks the interface (5-300 seconds) in the Check interface every field (default: 5 seconds).
- Specify the number of times the SonicWall appliance tests the interface as inactive before failing over in the Deactive interface after field (default: 6 times). For example, if the SonicWall appliance tests the interface every five seconds and finds the interface inactive after three successive attempts, it fails over to the secondary interface after 30 seconds. Low value ensures quick failover, however, slight internet breakage can lead to unnecessary failover/failback.
- Specify the number of times the SonicWall appliance tests the interface as active before failing back to the primary interface in the Reactive interface after field (default: 3 times). For example, if the SonicWall appliance tests the interface every five seconds and finds the interface active after three successive attempts, it fails back to the primary interface after 15 seconds.
- Probe responder.global.SonicWall.com on all interfaces in this group - Enable this checkbox to automatically set Logical/Probe Monitoring on all interfaces in the Group. When enabled, this sends TCP probe packets to the global SNWL host that responds to SNWL TCP packets, responder.global.SonicWall.com on port TCP 50000.
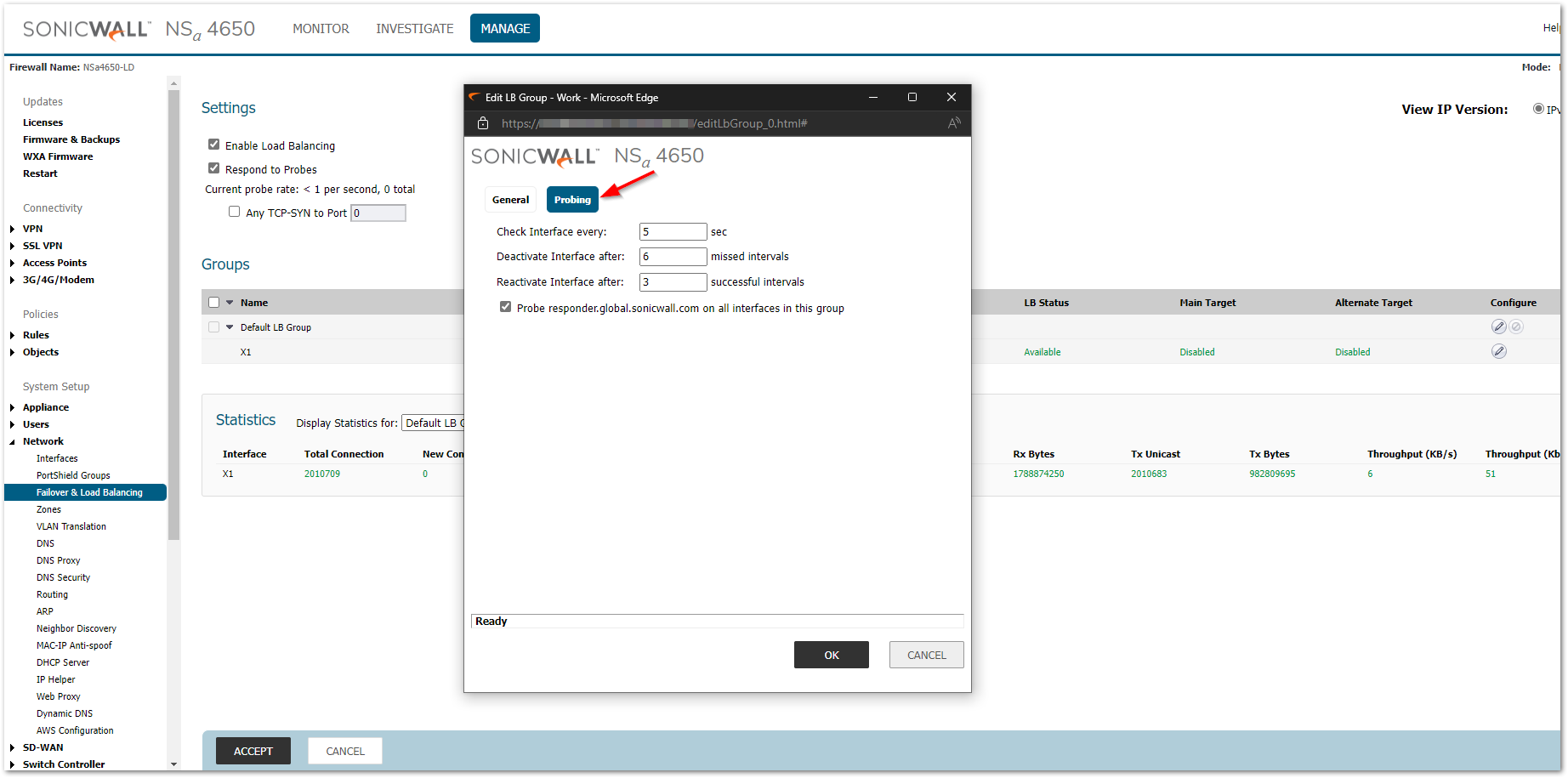
Click OK to save the changes on the Load Balancing group.
Interface Probing:
The next and most important setting that ensures proper failover is the Probing on each of the WAN interface. The SonicWall appliance can monitor the WAN connectivity by detecting whether the link is unplugged or disconnected or by sending probes to a target IP address of an “always available” target upstream device on the WAN network, such as an ISP side router. To enable probe monitoring, select Enable Probe Monitoring Under Manage | Network | Failover and Load Balancing page. Then click on the edit/pencil icon next to the WAN Interface under the LB group. Here you would be able to see 2 options:
- Physical probing - checks for Physical connectivity, like loose ethernet on WAN, WAN modem off and the like. Physical disconnection would rarely be a cause when the internet is lost.
- Logical Probing - checks for Ping (ICMP) or TCP probes to specific hosts. If selected, all the options below it then become available
Now, from the drop-down, select when probe succeeds. There are four options. And the first option is the recommended setting.
- Probe succeeds when either Main Target or Alternate Target responds.
- Probe succeeds when both Main Target and Alternate Target respond.
- Probe succeeds when Main Target responds.
- Succeeds Always (no probing). – Default; all other options are greyed.
Select the protocol (TCP or ICMP) used for monitoring and enter the IP address and port (TCP only) of the target. TCP probing is useful if you do not have ping (ICMP) response enabled on your network devices. In this case, TCP can be used to probe the device on a user-specified port. Ping can be used to any public domain name/IP address.
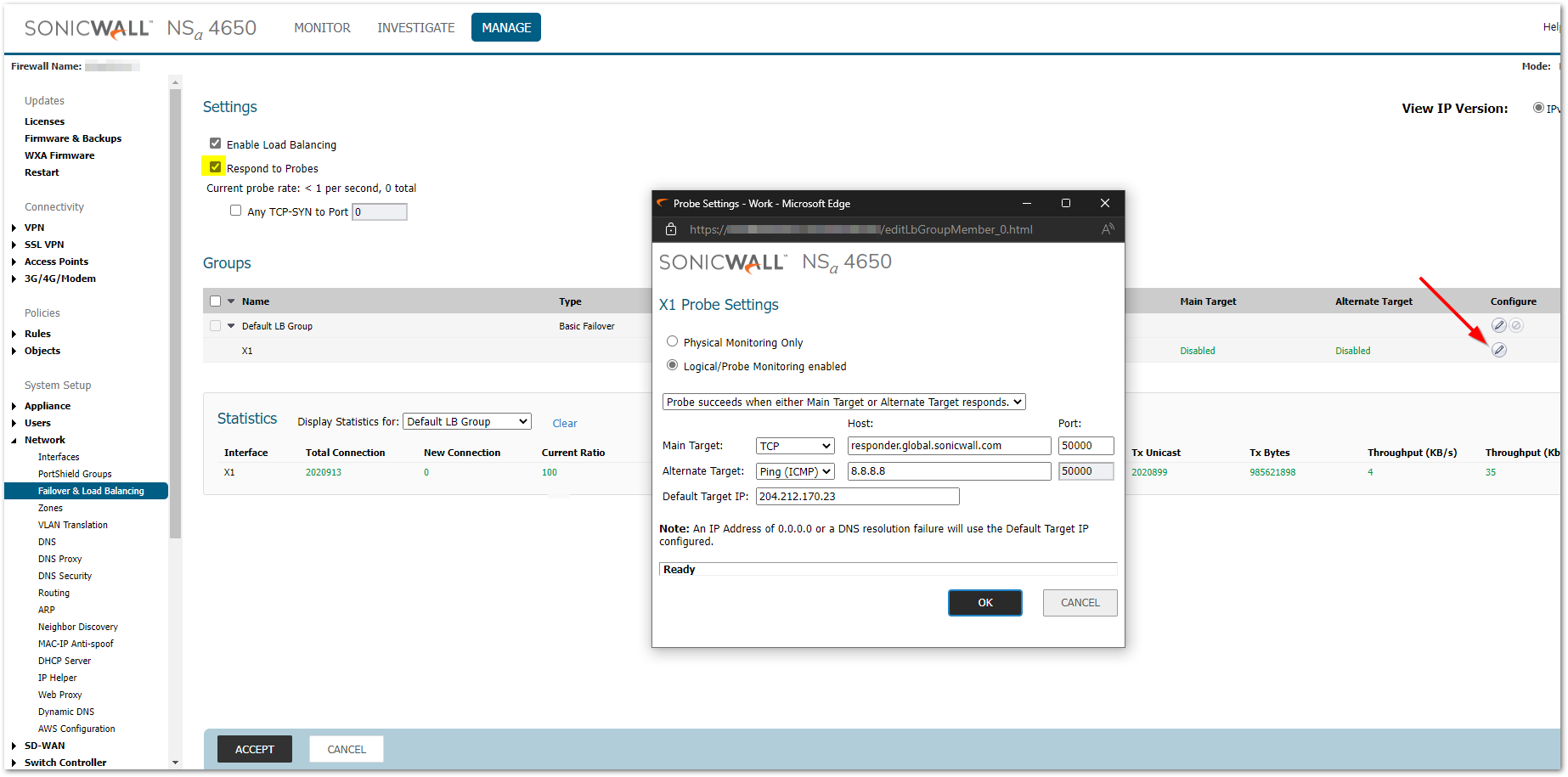
Click OK to save the changes.
This process should be repeated on each WAN interface in the LB group.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation






 YES
YES NO
NO