-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Arctic Wolf vScanner and SonicWall - Best Practices



Description
You may have noticed the Arctic Wolf vScanner generating a high amount of bandwidth and connections on your network. This is due to the fact that the scanner has the ability to scan all 65,535 ports, for both UDP and TCP connections (nmap scan). That is 131,070 different ports in total! The scanner will check each of these ports on every device it finds on the network. This leads to many connections and sessions being created in its discovery process.
SonicWall firewalls are stateful devices, meaning they keep track of the context of the connections. Each model of SonicWall can handle varying amount of connections at any given time.
To check if your SonicWall firewall has reached its peak connection count since its last reboot, navigate to your firewall's Dashboard > Overview to see the connection counter. Please see example below:

If your Peak Connections has reached your device's noted MAX Connections, then some steps need to be addressed as your firewall could be at risk of running out of memory.
For a more detailed look into your connections on your SNWL, go to Monitor > AppFlow Reports > IP Addresses and sort by Sessions. If your Arctic Wolf vScanner has generated a lot of connections, you should see here (keep in mind, these stats are recorded since last reboot).
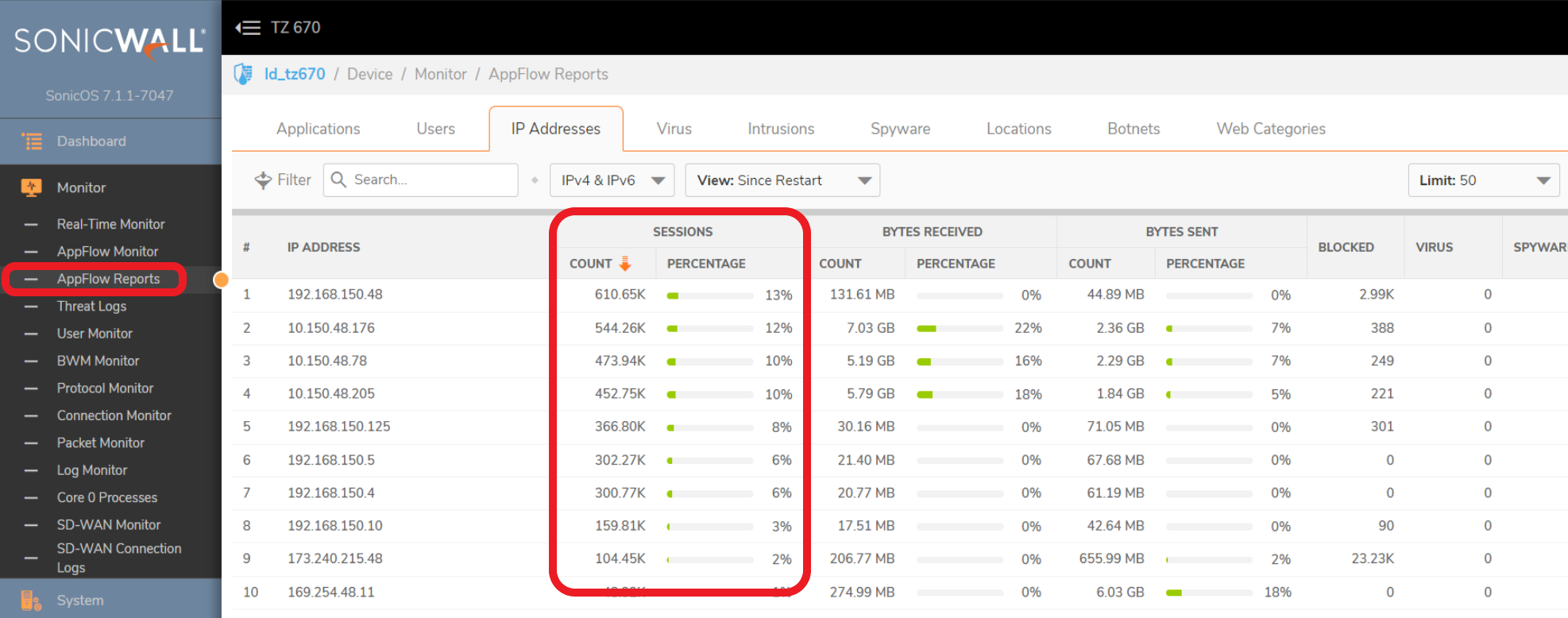
Resolution
When speaking with Arctic Wolf's team, they recommended not running scans through a firewall at all. "The scanner is not expecting to see any limiting firewalls between itself and the scan target, this allows the scanner to enumerate hosts quickly".
If you choose to run the scanner through your firewall anyways (not recommended), here are some steps you can take to cause the least amount of impact to your network:
1. Don't run the scanner during production hours.
Make sure your scanner is scheduled to operate after hours as running the scanner during production hours will put stress on the environment and could affect production.
2. Modify the Scanner's discovery process.
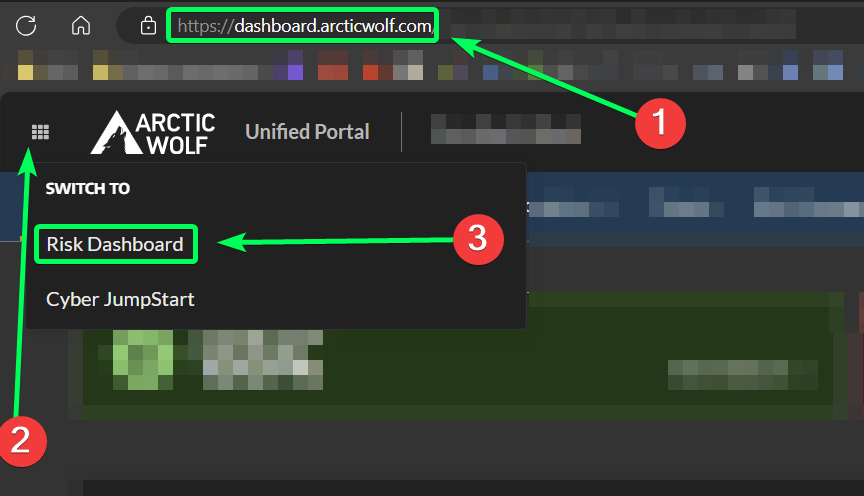
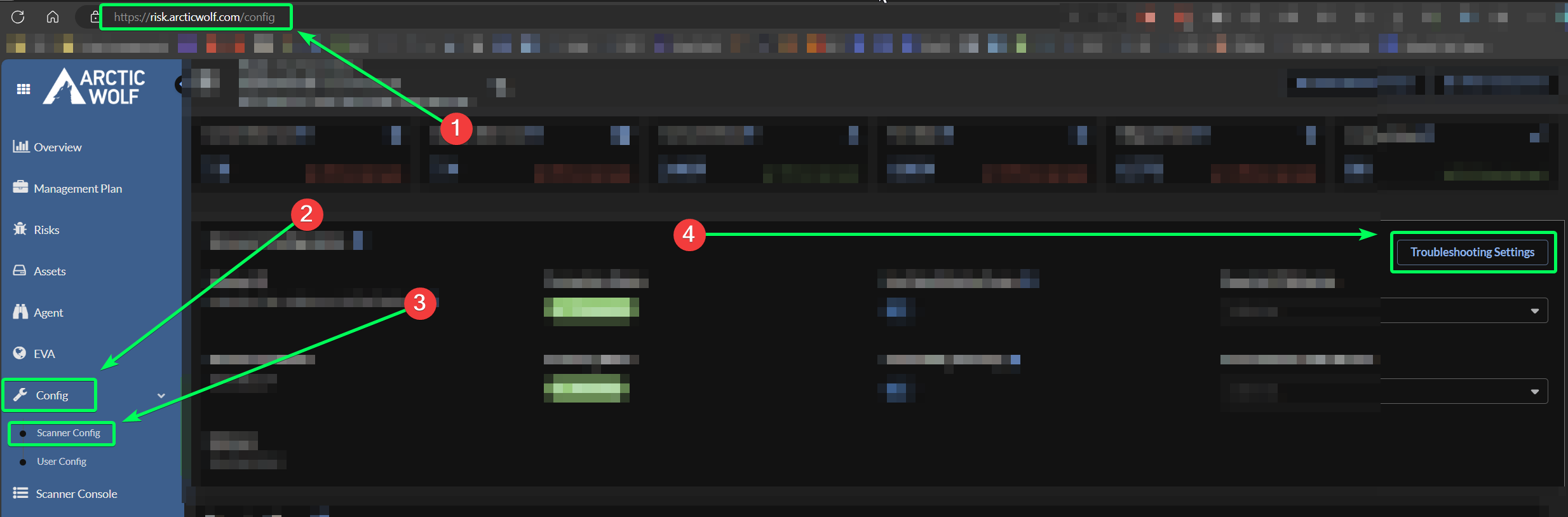
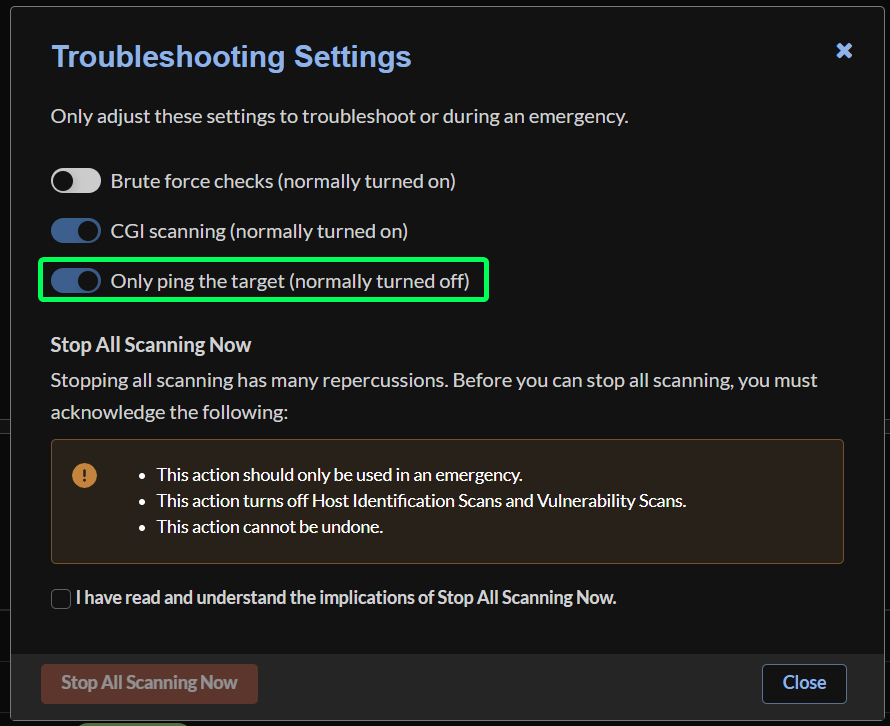
Instead of scanning all 65,535 ports for UDP and TCP for each device on the network, modify your scanner to only ping targets for discovery instead. This process is only for discovery purposes, and does not change the way the devices are scanned/tested once discovered by the vScanner. So long as your device is pingable/discoverable, it can still be scanned/tested by the vScanner. Doing this will drastically reduce the amount of connections/sessions generated on the firewall when the scanner tries to discover devices on the network. Here are the steps to do so:
Step 1:
Step 2:
Step 3:
3. Don't run the scanner over a VPN if not required.
Running the scanner over a VPN will only be more work for the firewall as the traffic must be encrypted, unencrypted, etc. This will add latency, further contributing to the negative impact of production. It is recommended that you run these scanners locally at each site.
4. Ensure you are scanning the correct kind of devices on your network.
Arctic Wolf recommends only scanning workstations and servers according to their FAQ (Managed Risk Scanner FAQ - Arctic Wolf Docs).
Avoid scanning devices like:
- Printers, especially large scale printers
- Medical devices
- Internet-of-Things (IOT) devices
- Scanners
- VoIP phones
- Uninterruptible Power Supplies (UPSs)
- Mainframes
- Small network appliances
- Old devices that likely were not built to handle frequent scanning activity
- ESXi servers — Scanning these servers may lock you out and force you to restart their mgmt service.
5. Exclude the Arctic Wolf Scanner IP from being ran through by the Security Services on SonicWall (IPS, Anti-Spyware, Gateway-Anti-Virus, etc.).
This can help to free up resources on the firewall, allowing the vScanner traffic to not get filtered.
Follow this KB for more info: How do I exclude traffic from firewall security services? | SonicWall
6. Limit the number of new connections allowed through the firewall.
If you are still facing issues where the scanner is generating too many connections on your firewall, please follow the following KB article: How to limit the amount of connections from a source IP | SonicWall
For more information regarding the vScanner from Arctic Wolf, please contact Arctic Wolf support or visit:
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO