CraftCMS Vulnerability Exposes Systems to Pre-Auth RCE, Now Exploited in the Wild (CVE-2025-32432)

Overview
The SonicWall Capture Labs threat research team became aware of a pre-authentication vulnerability in CraftCMS's asset transform generation feature, assessed its impact and developed mitigation measures. CraftCMS serves as a robust technology platform that functions as both a self-hosted PHP application and a flexible, user-friendly CMS for creating digital experiences over the web and beyond for content management, enabling businesses to unify data, processes and applications from various sources into a cohesive centralized content management ecosystem.
Tracked as CVE-2025-32432, this critical vulnerability exploits a deserialization issue in CraftCMS, the exploit takes advantage of an insecure deserialization in the asset transform generation feature. The vulnerable code path allows an unauthenticated attacker to inject a custom PHP object that gets unserialized, leading to arbitrary code execution. With a high-impact, low-complexity attack vector, it has a maximum CVSS score of 10. The flaw affects Craft CMS 3.0.0 – 3.9.14, 4.0.0 – 4.14.14, and 5.0.0 – 5.6.16. Given the widespread use of Craft CMS instances and active exploitation of this vulnerability in the wild, immediate action is essential. Hence, all Craft users are strongly encouraged to upgrade to the latest patched version, as detailed in the vendor advisory.
Technical Overview
According to Craft CMS documentation, Craft CMS's asset transform generation feature allows for automatic manipulation of images after they've been uploaded, eliminating the need for content editors to upload images at specific sizes. This feature streamlines image handling, saving time for content editors and ensuring visual consistency across the website. Notably, a valid “asset ID” is mandatory for all instances of Craft CMS to create a transformation object, manage document files, and media on a website. This ID is checked before the creation in version 3.x, whereas it is checked after in versions 4.x and 5.x. A valid asset ID is the prime suspect and provides life to the exploitation of CVE-2025-32432.
This vulnerability stems from missing authorization checks and insecure deserialization on a built-in image transformation feature that allows website admins to adjust images to a chosen format by creating a transformation template for a selected image. This vulnerability relies on the fact that an unauthenticated threat actor can send a POST request to the endpoint responsible for image processing, and the data within the POST body would be interpreted by the server. In vulnerable systems, unauthenticated remote attackers could exploit this flaw by sending a specially crafted POST request to the /index.php?p=admin/actions/assets/generate-transform with a specially crafted JSON payload, trying to retrieve a valid asset ID as shown in Figure 2. The payload includes a PHP object that gets deserialized, leading to arbitrary code execution through the GuzzleHttp\Psr7\FnStream class.
Triggering the Vulnerability
The vulnerability works and is exploited in the wild over vulnerable Craft CMS instances if a threat actor follows:
Sending a crafted GET request to /index.php?p=admin/dashboard to retrieve a CSRF token from the CraftCMS admin dashboard as shown in Figure 1.
Sends a POST request to /index.php?p=admin/actions/assets/generate-transform with a specially crafted JSON payload and retrieves a valid asset ID through PHP object injection.
The payload includes a PHP object that gets deserialized, leading to arbitrary code execution through the GuzzleHttp\Psr7\FnStream class.

Exploitation
A sample exploitation request, shown in Figure 2, demonstrates how a malicious POST request can be used to target the vulnerable endpoint and upload an arbitrary file.
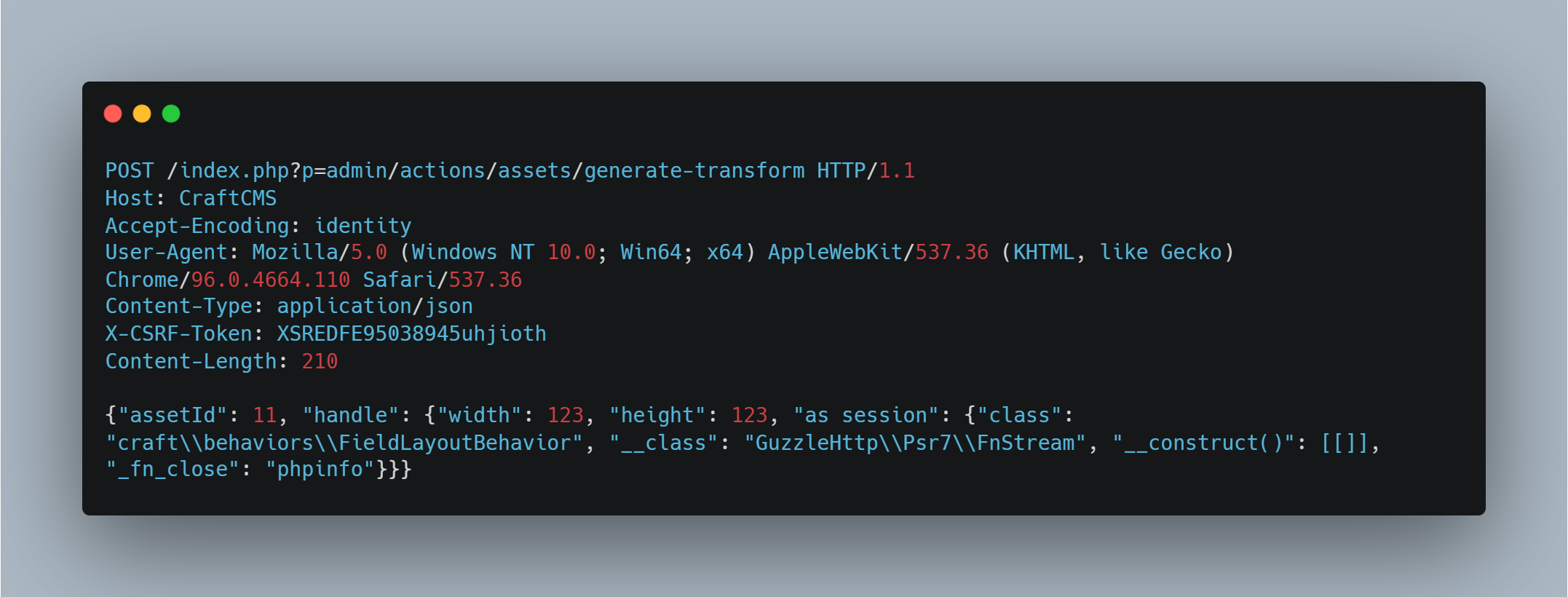
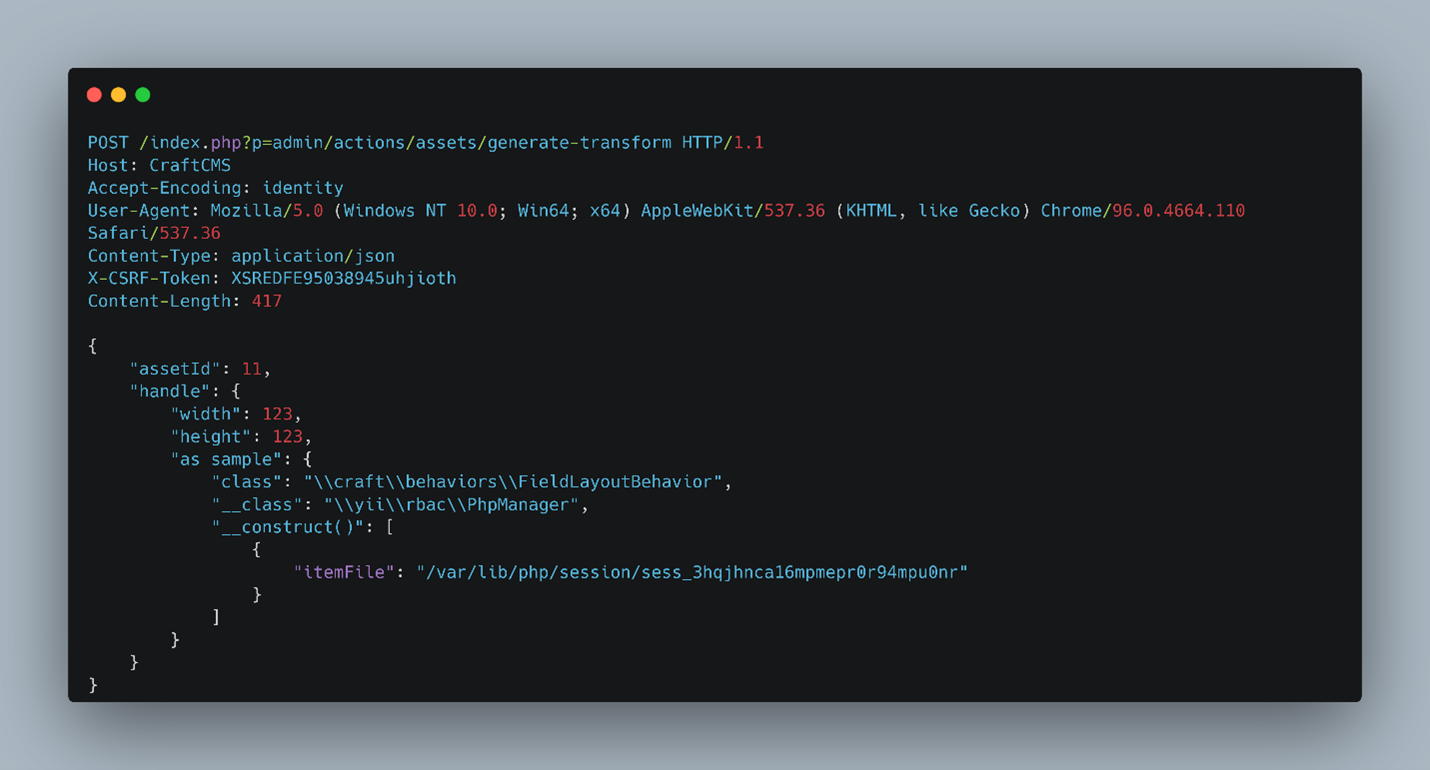
Figure 3 shows the addition of a new field “as sample” to the handle key. The purpose of this new field is to execute PHP code present in the itemfile “/var/lib/php/session/sess_3hqjhnca16mpmepr0r94mpu0nr” using the PHP manager. This file contains the return URL with an injected PHP session code, which is then returned to the visitor as part of the server’s HTTP response, establishing a foothold on the compromised system. The successful exploitation is verified by executing phpinfo() and extracting specific system information. This information can be leveraged later to execute system commands remotely, Denial of Service, or potentially result in full system compromise.
SonicWall Protections
The following signatures have been released to ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability.
IPS: 20950 Craft CMS Remote Code Execution 3
IPS: 20951 Craft CMS Remote Code Execution 4
Remediation Recommendations
Given that vulnerability is actively being exploited in the wild, users are strongly advised to prioritize updating their systems to the latest version, as specified in the vendor advisory.
As per the advisory, an administrator should check the firewall or web server logs and find suspicious POST requests to the actions/assets/generate-transform Craft controller endpoint, specifically with the string __class in the body. Under CMS web logs, one must check for the error “Image transform cannot be created”. Then, your site has at least been scanned for this vulnerability.
Relevant Links
Share This Article

An Article By
An Article By
Dhiren Vaghela
Dhiren Vaghela
Dhiren Vaghela has over a decade of experience in the IPS domain, with a strong focus on defensive security. His expertise lies in identifying, analyzing and mitigating vulnerabilities. Dhiren is well-versed in content-based signature writing, scanner-based alert generation and technical blog writing. By leveraging emerging technologies, he has developed numerous IPS signatures across various protocols. Known for his exceptional signature writing skills and collaborative team spirit, Dhiren is a valuable asset in the field of cybersecurity.
