Apache Struts2 CVE-2017-5638 Vulnerability Follow-up (Mar 24, 2017)

In previous SonicAlert, we warned a critical remote code execution vulnerability (CVE-2017-5638) (S2-045) targeting Apache Struts2. A remote attacker could exploit this vulnerability by sending certain crafted HTTP request with mal-formed Content-Type value. A successful attack could execute arbitrary command on the web server.
SonicWall customers are protected by following signatures:
- IPS: 12656 - Apache Struts 2 Jakarta Remote Code Execution (S2-045) 1
- IPS: 12660 - Apache Struts 2 Jakarta Remote Code Execution (S2-045) 2
While SonicWall Threat Research Team keeps watching CVE-2017-5638, we observed that since March 23, number of firewalls reporting CVE-2017-5638 exploits has nearly doubled.
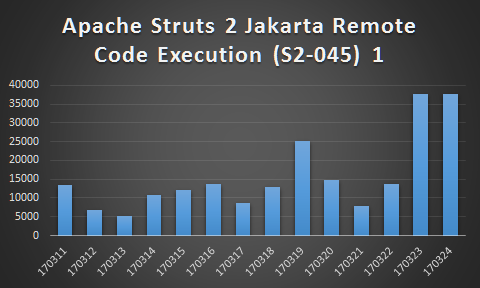
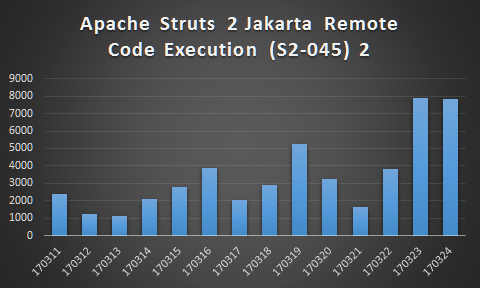
In the meantime, number of incidents has surged 50 times comparing to average incidents in the past 2 weeks.
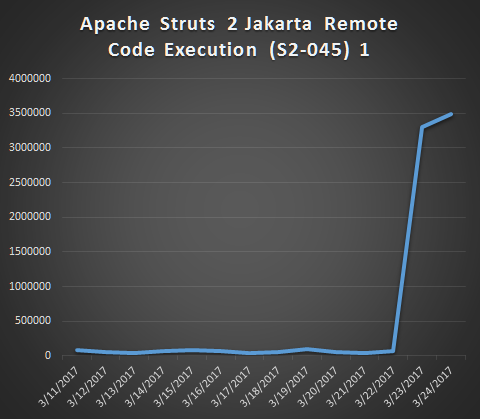
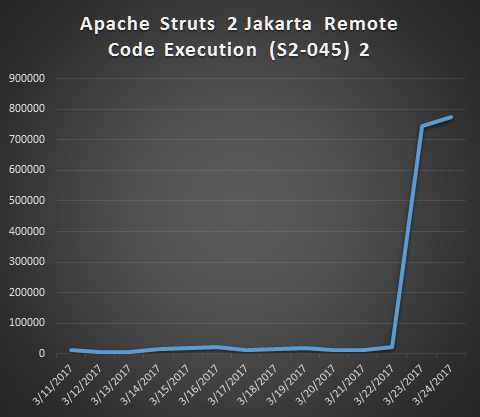
It is possible that attackers are testing and exploiting CVE-2017-5638 with newly developed (and more powerful) tools. SonicWall urges all our customers to review their firewall logs and make sure they are running latest version of Apache Struts2.
Share This Article

An Article By
An Article By
Security News
Security News