-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Troubleshoot steps if a firewall status is Offline on NSM SaaS



Description
There may be a high number of reasons for a firewall to not be acquired by the NSM. From the Internet connection, to configuration issues which can block the connection between the firewall and the CSC, in this article we will discuss a few troubleshoot steps on how to acquire and to get the proper reports from the Firewall on NSM
Cause
By default, if the Cloud Management and Zero Touch are enabled for a Firewall from MySonicWall account, all the configuration regarding the acquirement of the firewall shall be made by the NSM, which will be logged in as an admin to the firewall, hence the reason why the firewall will be set on non-config mode for the users if it will be acquired by the NSM. There are a few conditions in order to have the firewall managed by the NSM
Resolution
Acquire Unit:
- Access the firewall locally, navigate to Device | Settings | Licenses and press the Synchronize button.
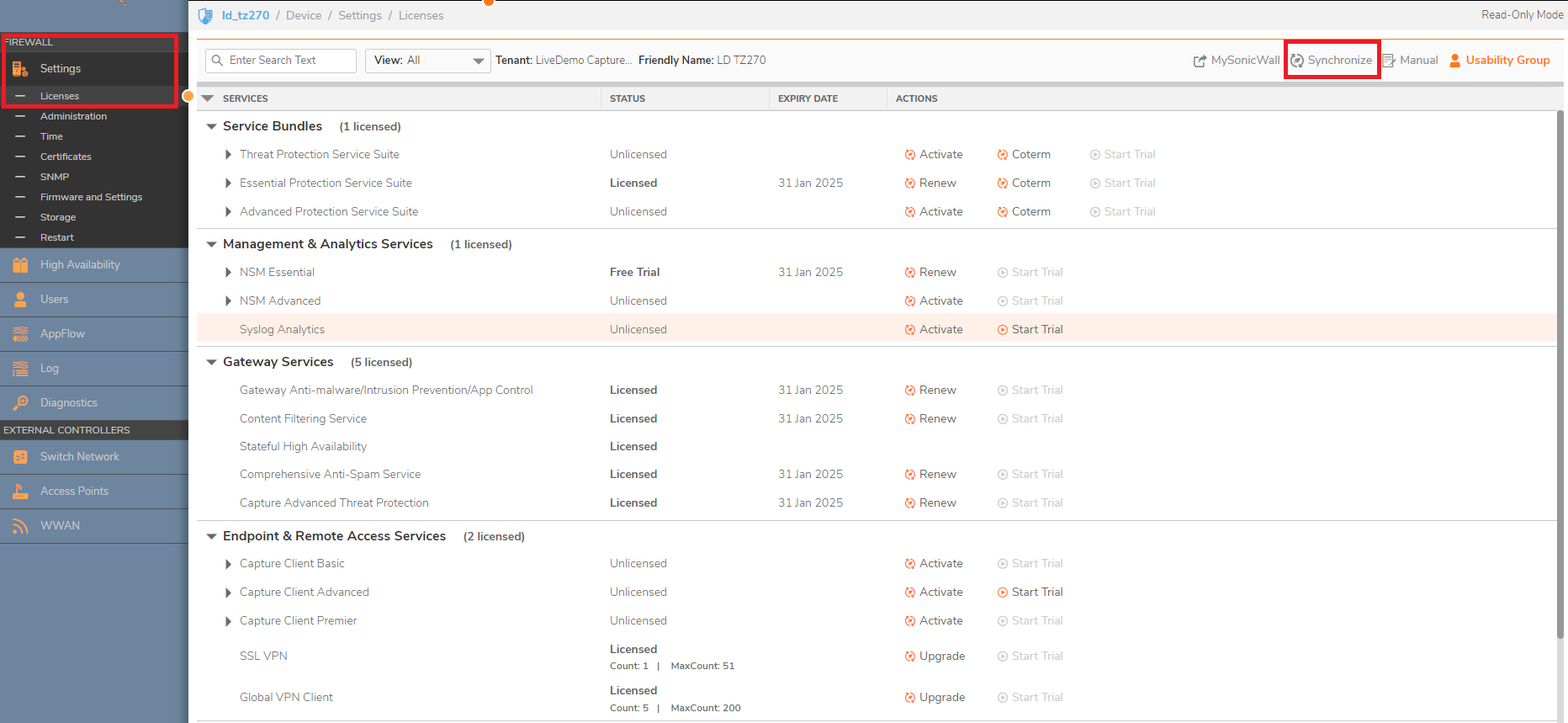
- Navigate to Device | Administration, check if Management using NSM/GMS is enabled
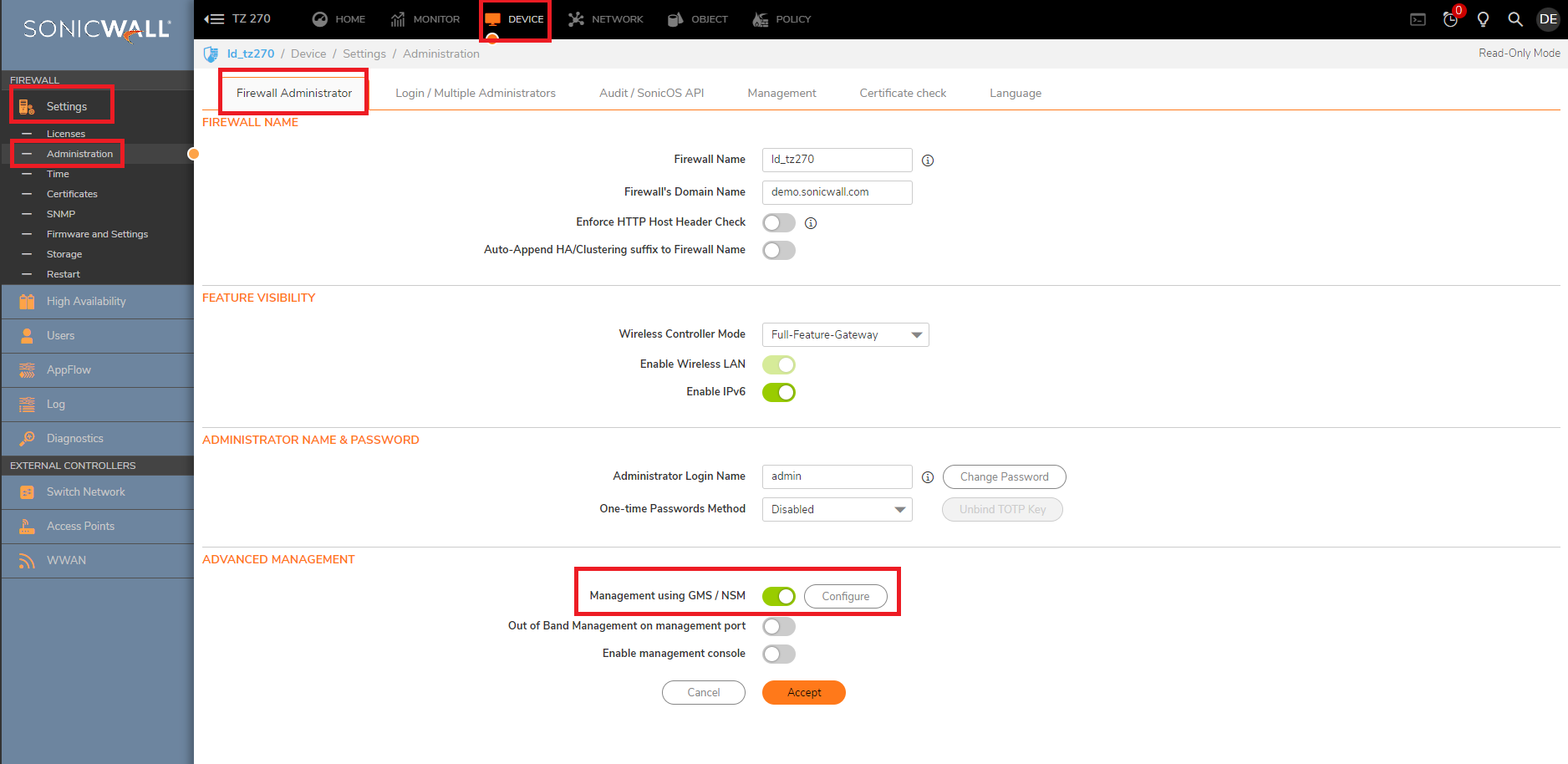
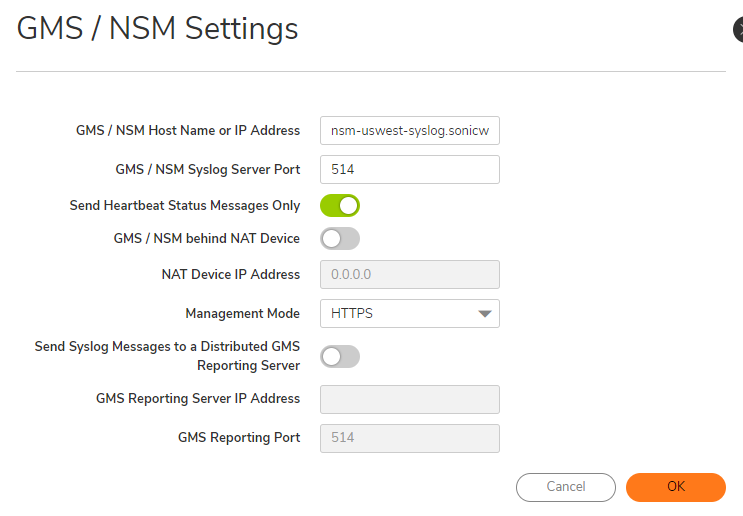
- For GMS/NSM Host Name or IP Address use the following, depending on your collocation:
For US Colo: nsm-uswest-syslog.sonicwall.com
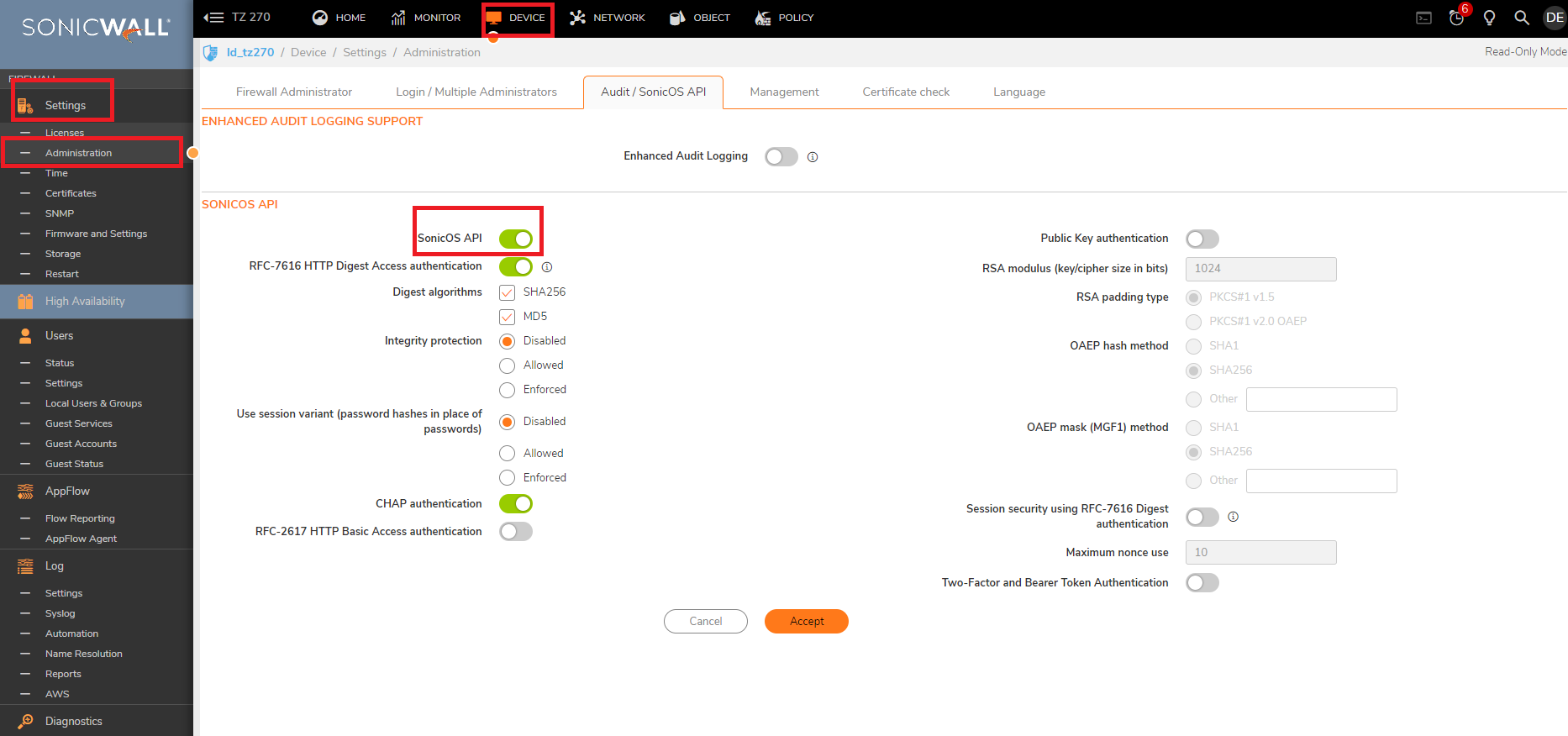
For EU Colo: nsm-eucentral-syslog.sonicwall.com - Under Device | Administration | Audit / SonicOS API, make sure the SonicOS API is enabled as well.
- Access the diag page of the firewall: How to Access the Internal Settings of the firewall
- Use CRTL + F to find "sgms", make sure it's enabled
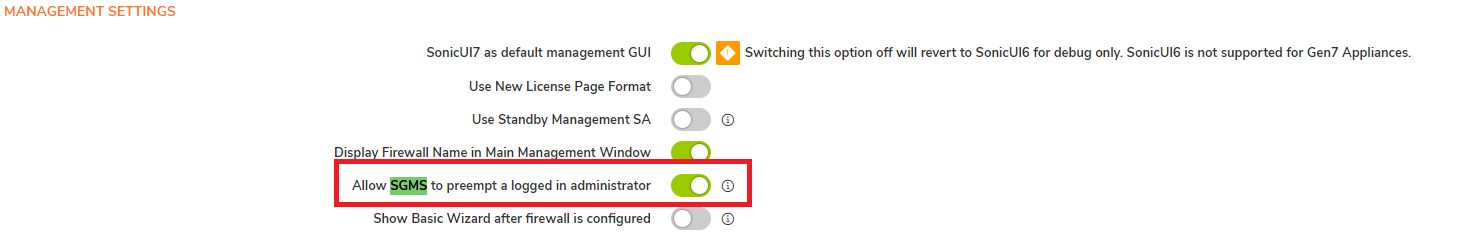
- Also, search also for "zero" and restart the Zero Touch task.
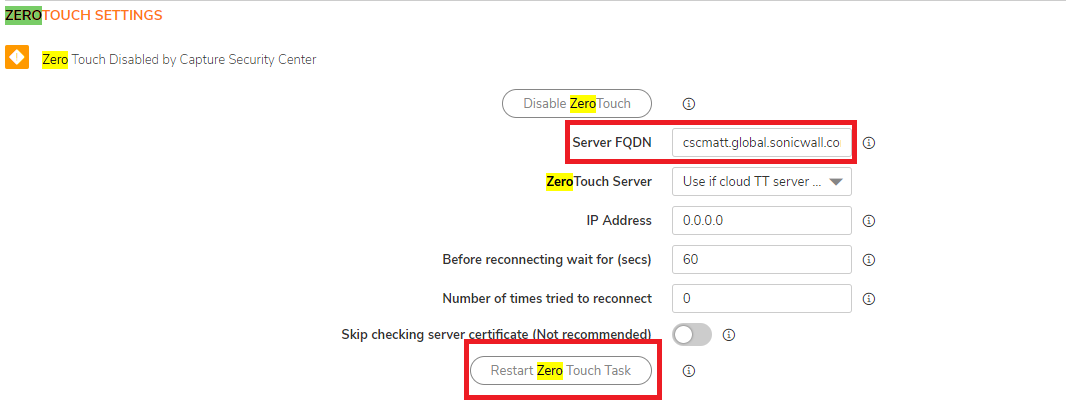
FQDN for the following:
US Colo:
nsm-uswest-zt.sonicwall.com
nsm-uswest-iczt.sonicwall.com (For Instant Connect Zero Touch)
EU Colo:
nsm-eucentral-zt.sonicwall.com
nsm-eucentral-iczt.sonicwall.com - After those steps go to the NSM Inventory and Synchronize again the firewall.
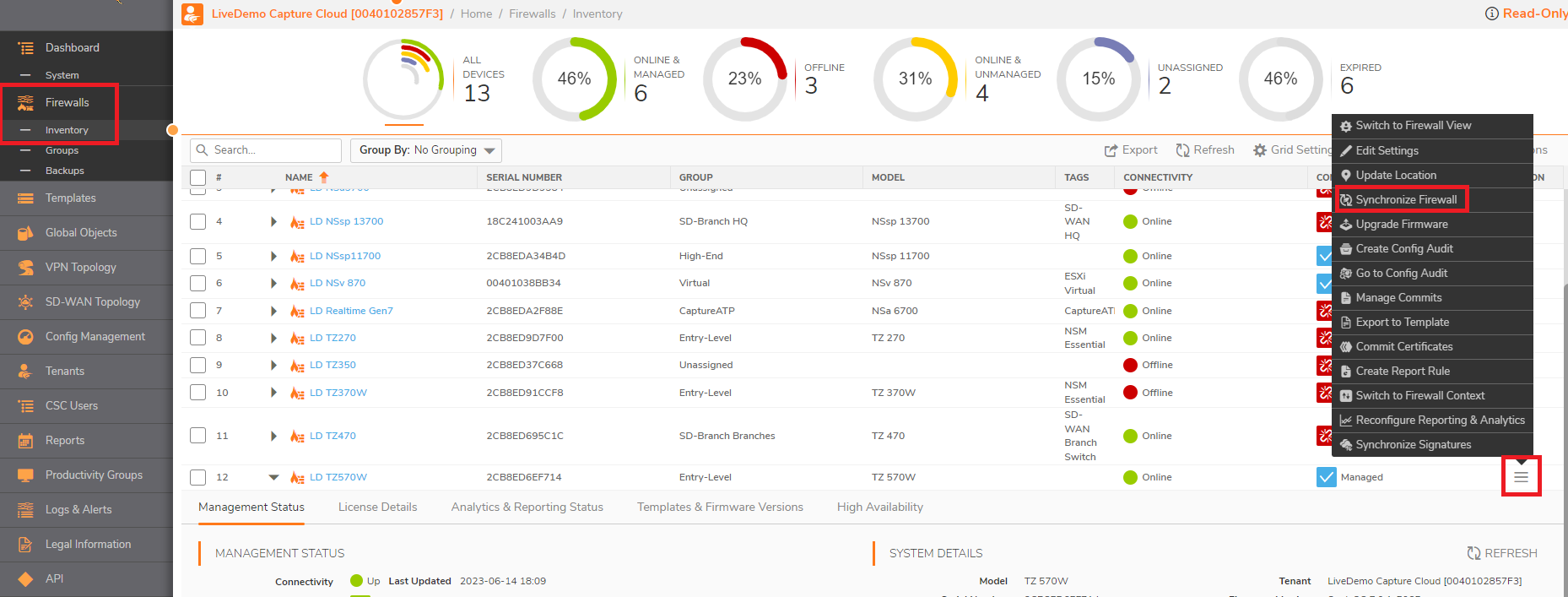
- If it doesn't get online after 5-10 minutes, try again to Synchronize the firewall. If the issue is still persisting, you can try to go to your MySonicwall account and to put the firewall from Cloud management to On-Box and after ~15 minutes to put it again under Cloud management.
- After that, check if the firewall is appearing on the NSM, if it's appearing, to go the firewall locally, access the diag page again, restart the Zero Touch Task again and see if the firewall is going online.
- Reconfigure Reporting and Analytics. and make sure the App Flow is enabled.
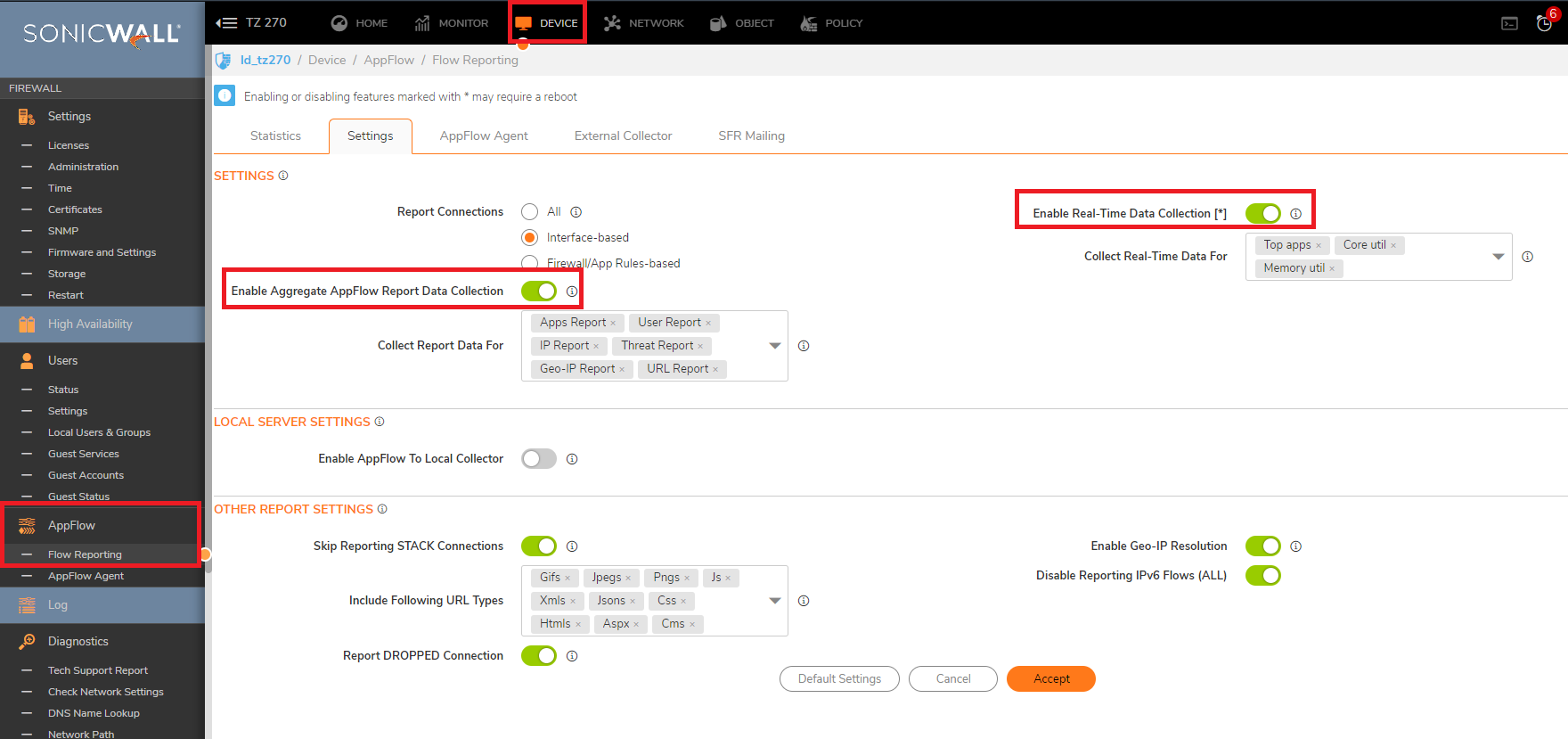
- How to configure and use the Packet Monitor, Set the log level to Inform/Alert, import GMS/Analyzer template on the logs:
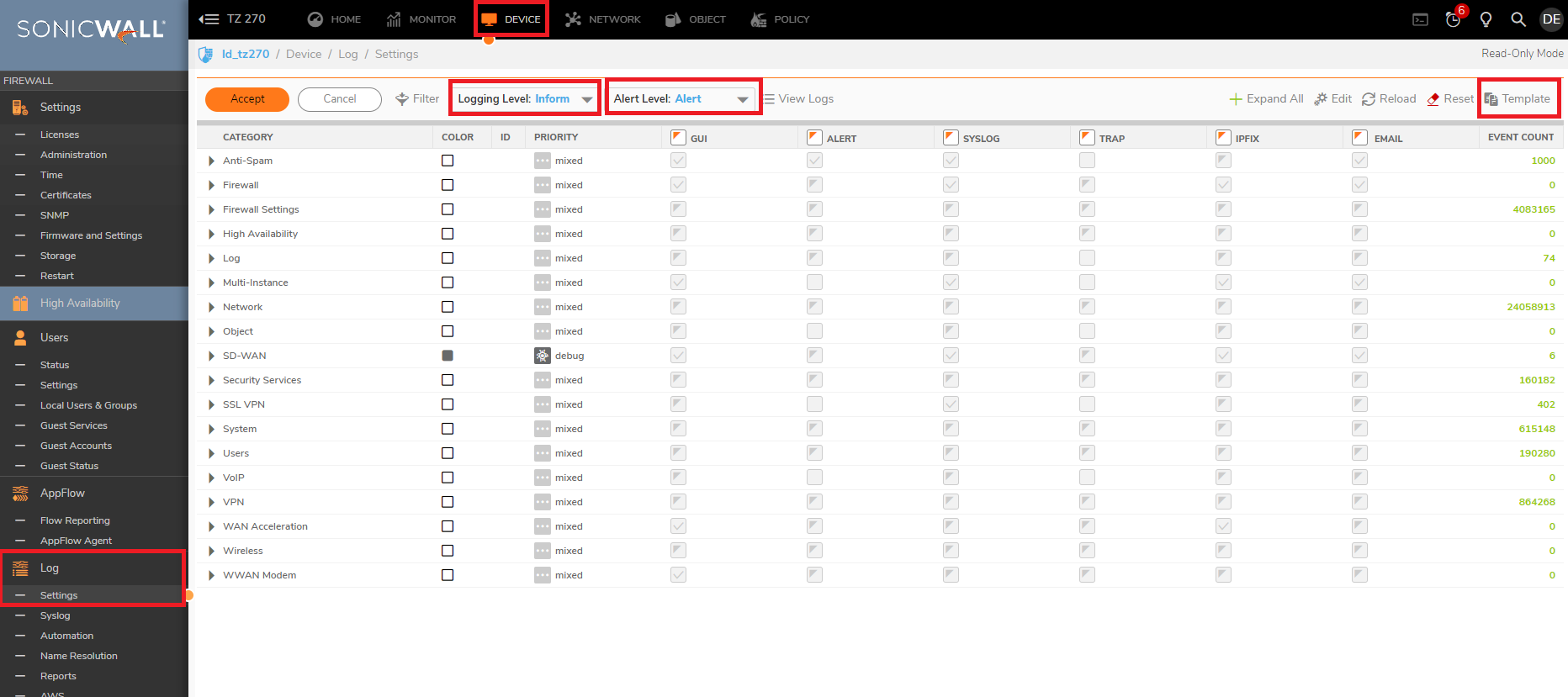
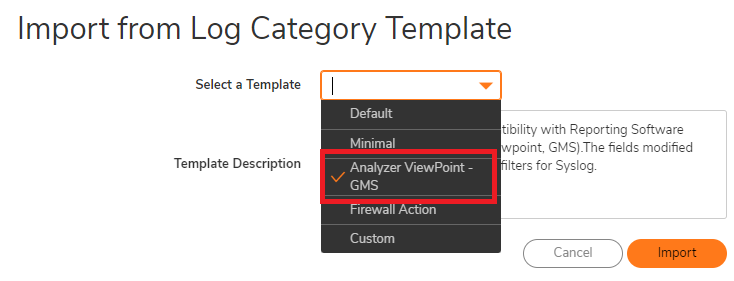
- How to set the Log Settings
- Refresh the licenses from the firewall: Manage and Sync the Licenses from SonicWall GUI
- On the Access Rules, there should be a default Access Rule WAN>WAN, HTTPS management with allow (Enable HTTPS Management on the WAN Interface)
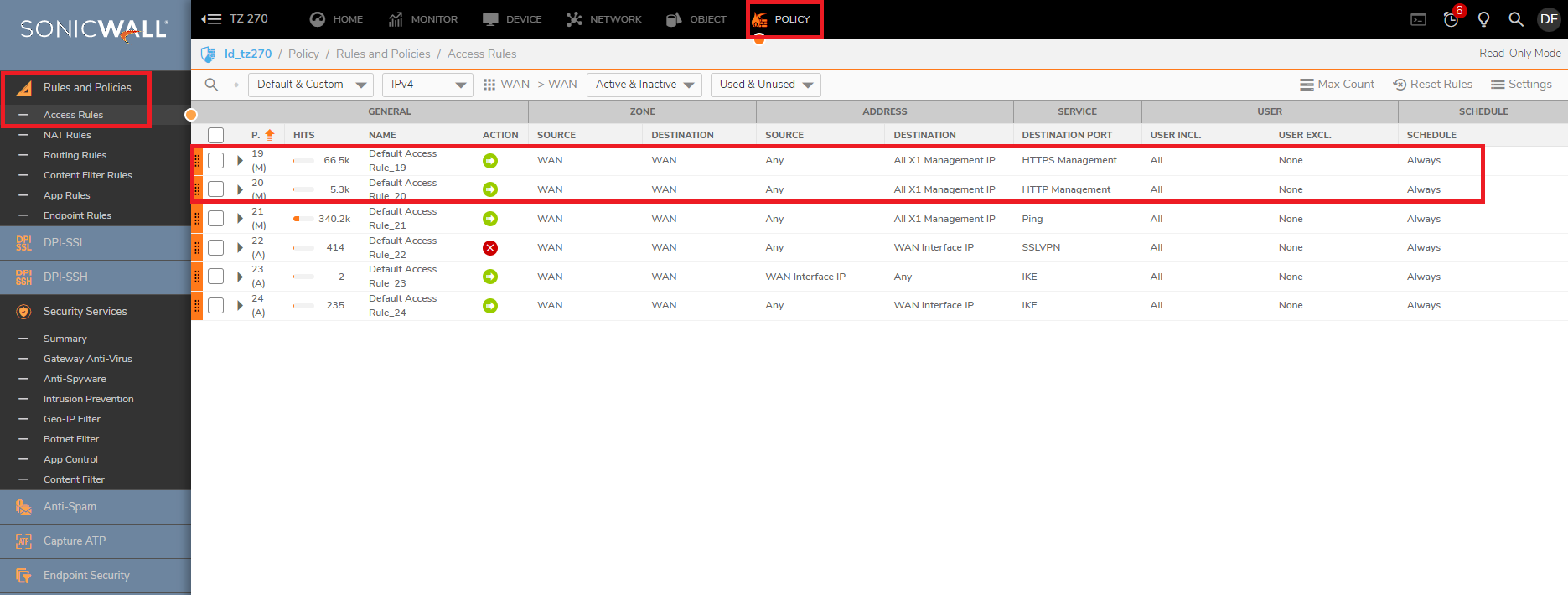
- In case you have made changes to the default Access Rules trough CLI, we need to create a new Access Rule which can let the NSM to manage the firewall
Create a FQDN object with on of the following addresses, depending of your Colo:
US Colo: nsm-uswest.sonicwall.com
EU Colo: nsm-eucentral.sonicwall.com
Create an Access Rule WAN > WAN with:
Source FQDN created
Destination WAN interface management IP
Service: HTTPS Management - Synchronize a few times the firewall after all those steps and try to click on Reconfigure Reporting and Analytics as well and there should be firewall online after 10-15 minutes with data coming in.
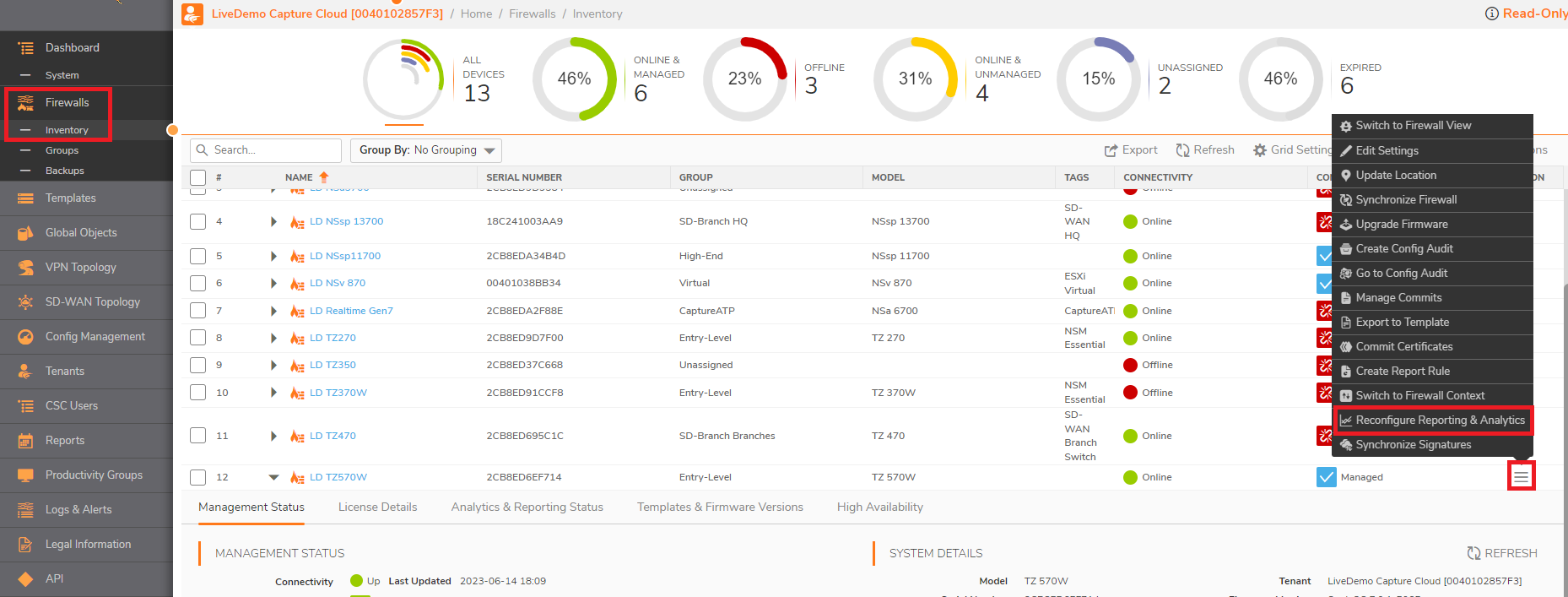
- Also, make sure you have the flow reporting enabled on the CFS default Action Object
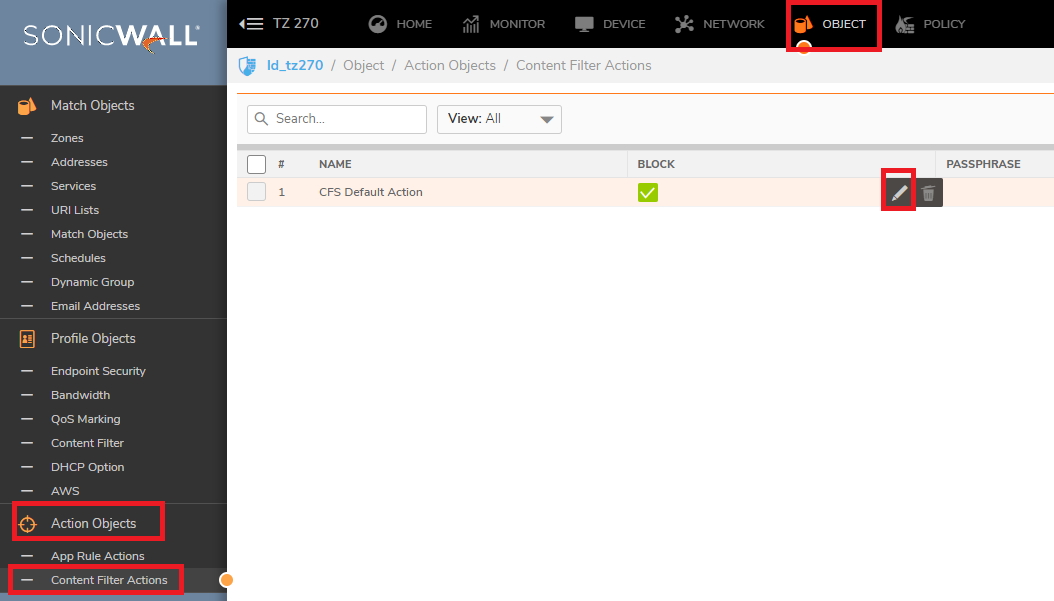
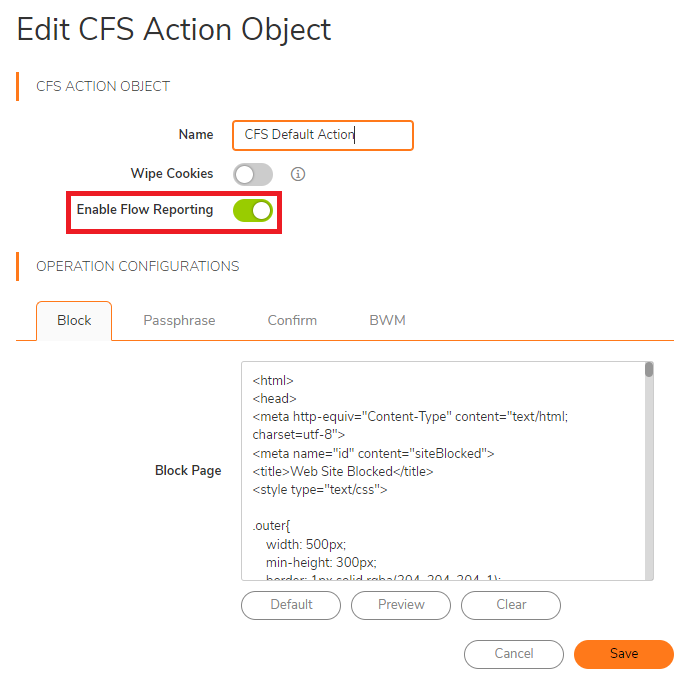
- Enable the App Control and logging for all Apps as well:
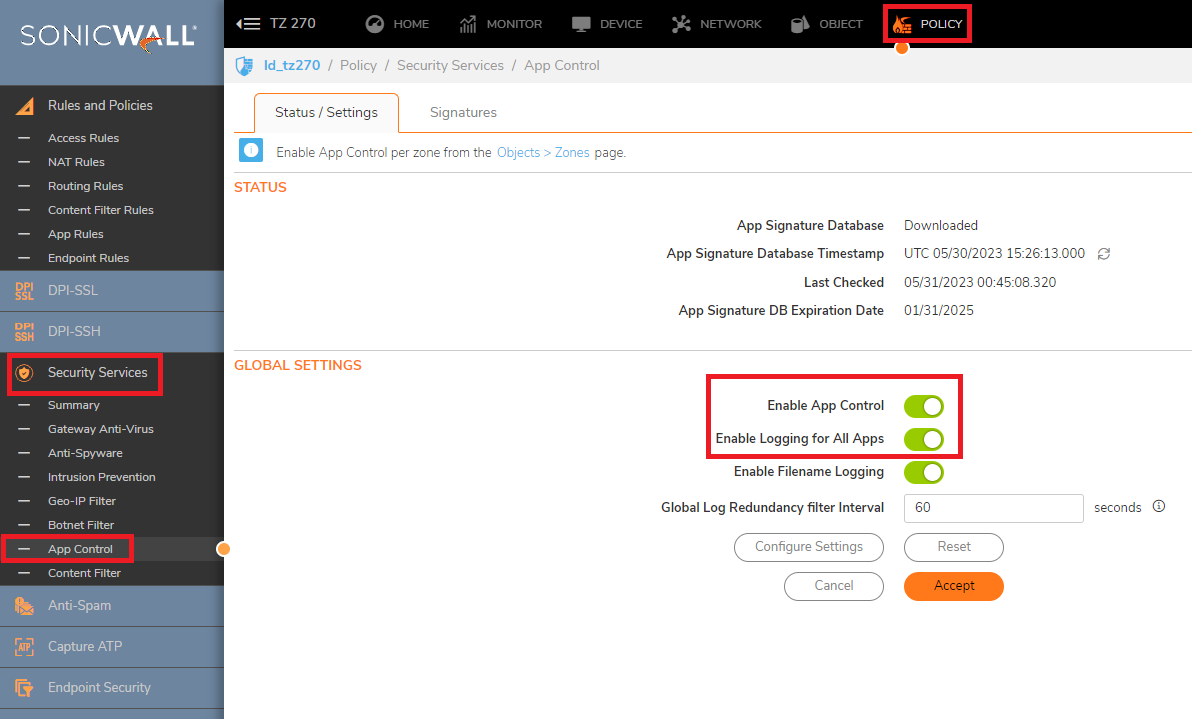
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > TZ Series
- Firewalls > NSa Series
- Management and Reporting > Network Security Manager
- MySonicWall > Support






 YES
YES NO
NO