-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to Install and Configure the Data Connectors, Azure Monitor Agent (AMA), and Azure Arc Connected Machine Agent to Enable Microsoft Sentinel Integration



Description
This article covers how to perform the following:
- Install and configure the Data Connectors in your Microsoft Sentinel workspace.
- Install the SonicWall Network Security Solution via the Content Hub.
- Install the Common Event Format (CEF) Solution via the Content Hub.
- Install the Azure Arc Connected Machine Agent
- The Azure Arc Connected Machine agent establishes a secure connection with Azure so the log data is not sent to the cloud in plaintext. The data can be accessed within your Log Analytics/Microsoft Sentinel workspace.
- Install the Azure Monitor Agent (AMA) Extension
- The Azure Monitor Agent provides a Syslog relay. At a high level, you install this agent on a host within the network and configure SonicOS to send ArcSight-formatted Syslog data to the agent.
- Configure a Data Collection Endpoint
- Configure a Data Collection Rule
- Install the Azure Monitor Agent (AMA) Forwarder
Requirements
Instructions
Install the data connectors
- Install the SonicWall Network Security Solution via the Content Hub.
- In the Content Hub, use the search field to find the “Common Event Format” Solution. Optionally, you can filter the provider to “Microsoft” to limit the results.
- Click the “Install” button near the bottom right of the page.
- Once installed, the button becomes “Manage”. Click the “Manage” button near the bottom right of the page.
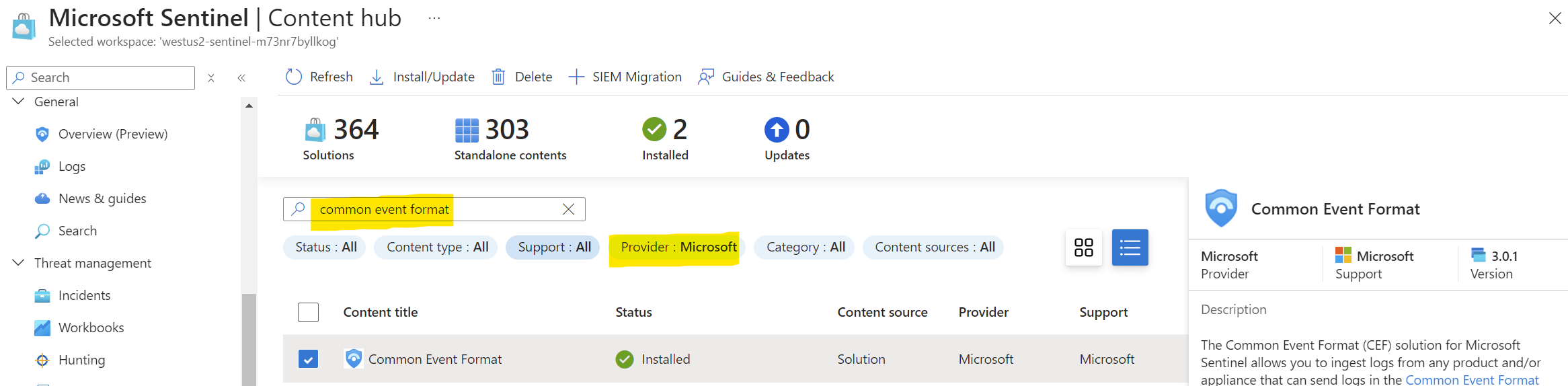
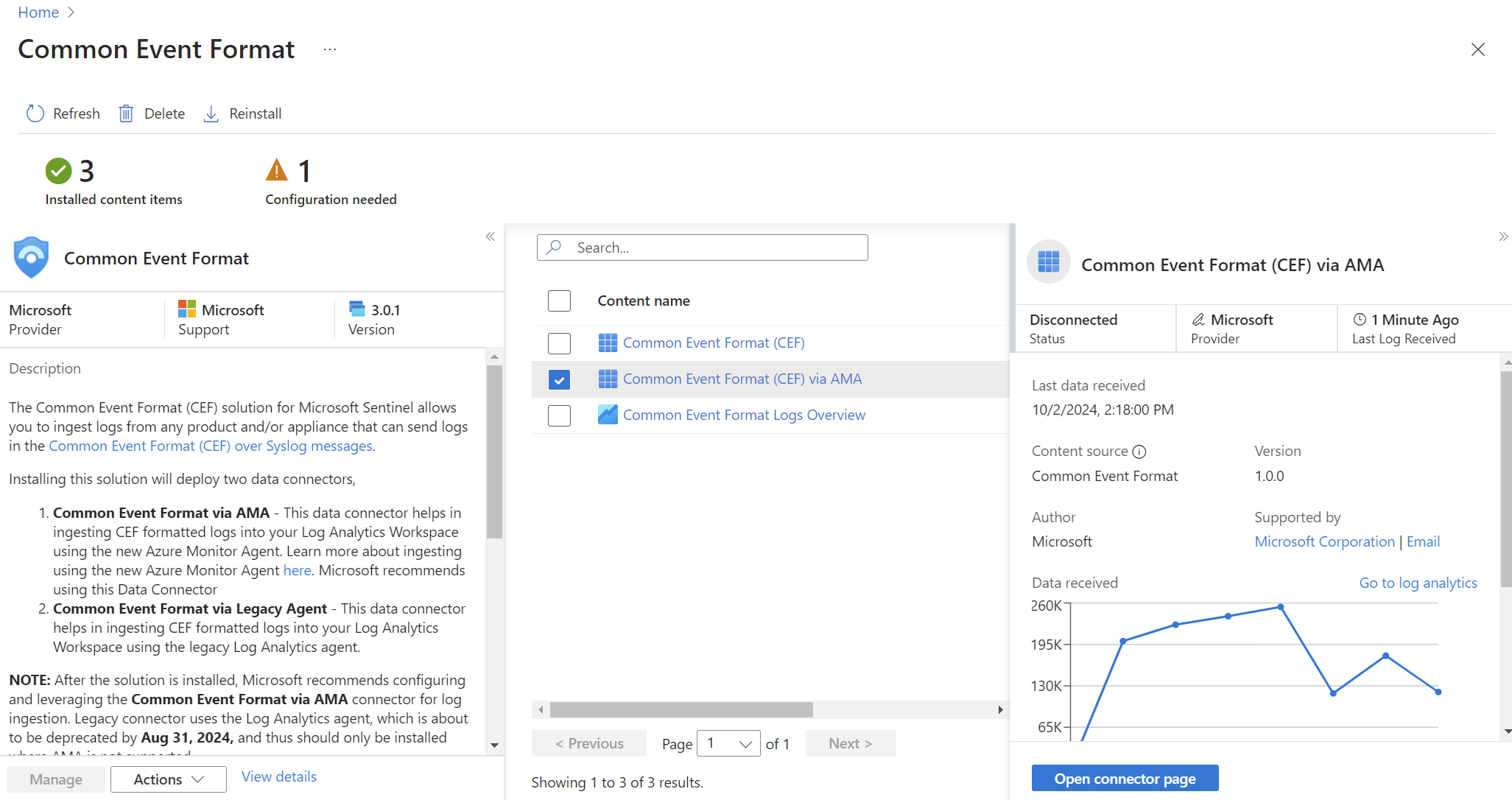
- Select the “Common Event Format (CEF) via AMA” item, then click the “Open connector page” button near the bottom right of the page. Hold on to this page. We’ll need it in an upcoming step.
Install the Azure Arc Connected Machine Agent (on-premises/non-Azure hosts)
If your relay host is on-premises (not hosted in Azure), then another requirement is the Azure Arc Connected Machine agent (AZCM Agent).
Linux Agent installation: https://learn.microsoft.com/en-us/azure/azure-arc/servers/agent-overview#linux-agent-installation-details - On your relay host, run the following set of commands to download and install the Azure Arc Connected Machine Agent:
wget -O install_linux_azcmagent.sh https://aka.ms/azcmagent && chmod u+x install_linux_azcmagent.sh && sudo ./install_linux_azcmagent.sh - Use the sudo azcmagent show command to display the agent status.
Example of Azure Arc Connected Machine Agent status...
sudo azcmagent show
Resource Name :
Resource Group Name :
Resource Namespace :
Resource Id :
Subscription ID :
Tenant ID :
VM ID :
Correlation ID :
VM UUID :
Location :
Cloud :
Agent Version : 1.39.02628.1411
Agent Logfile : /var/opt/azcmagent/log/himds.log
Agent Status : Disconnected
Agent Last Heartbeat :
Agent Error Code :
Agent Error Details :
Agent Error Timestamp :
Using HTTPS Proxy :
Proxy Bypass List :
Cloud Provider : N/A
Cloud Metadata
Manufacturer : VMware, Inc.
Model : VMware Virtual Platform
MSSQL Server Detected : false
Dependent Service Status
GC Service (gcad) : active
Extension Service (extd) : active
Agent Service (himdsd) : active
Portal Page :
Disabled Features : atsauth
Connect the Azure Arc Connected Machine Agent to your resource group
Configure the Subscription, Location, and Cloud. These should be configured to match those associated with your Microsoft Sentinel instance.
Valid Locations: https://azure.microsoft.com/global-infrastructure/services/?products=azure-arc - On your relay host, copy and adjust the following command to connect the agent to your Azure resource group.
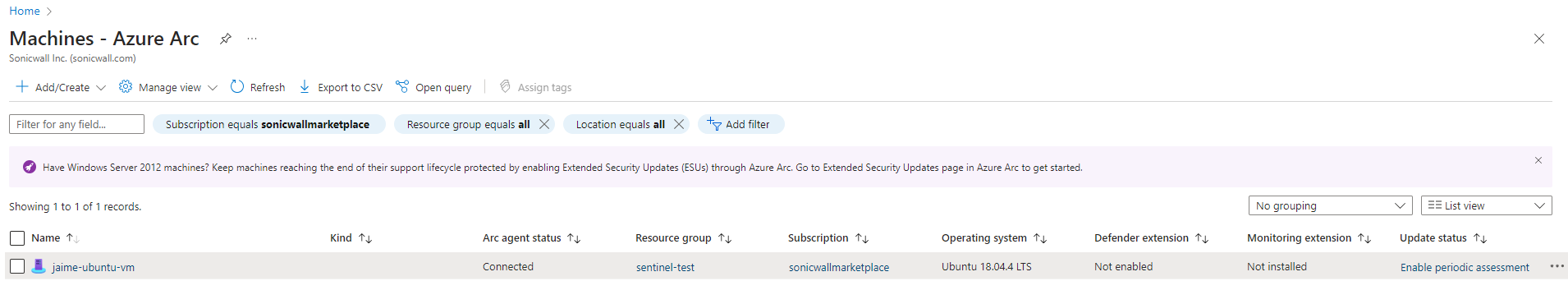
sudo azcmagent connect --location "West US" --resource-group "my-resource-group" --subscription-id xxxxxxxxxxxx-xxxxx-xxxxx-xxxxx-xxxxxxxxxxxxx - You should be prompted to authenticate with a code. Once authenticated, the resource creation will occur and the Arc agent will connect. Another azcmagent show should display an updated connected status with more information than previously displayed.
- Click on this link. You will be taken to the “Machines - Azure Arc” page in the Azure Portal. You should see your host connected.
Install the Azure Monitor Agent Extension
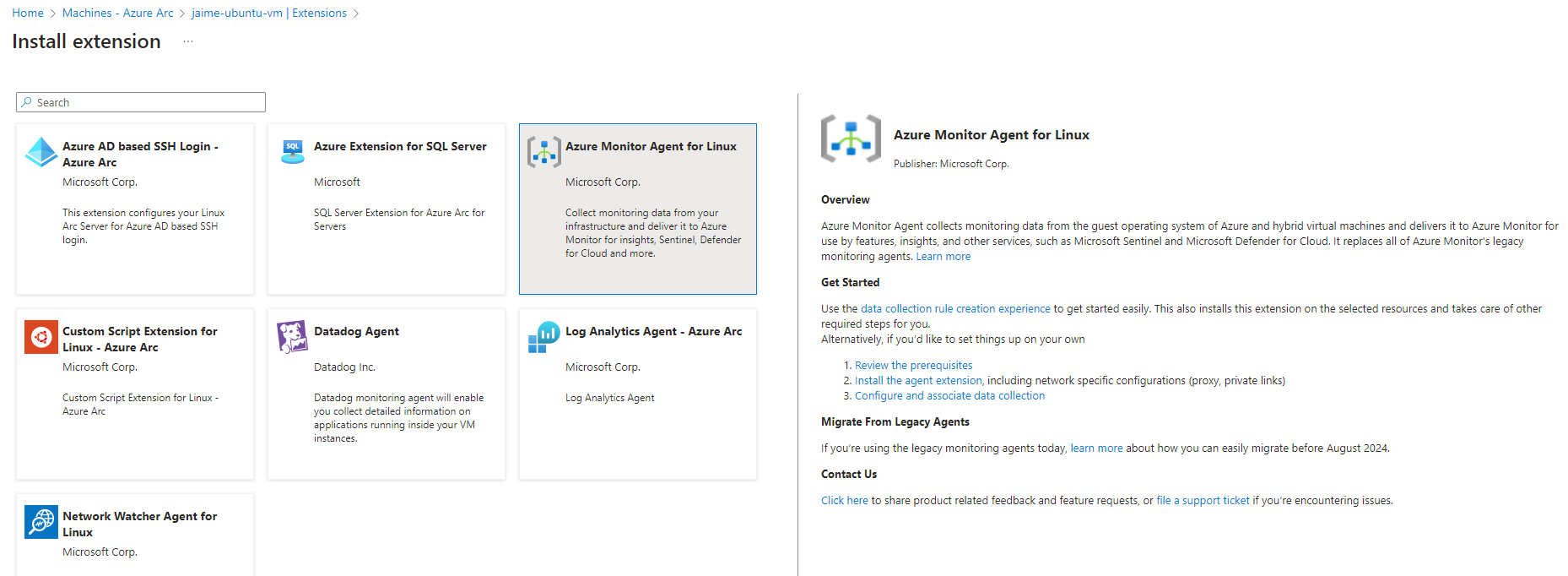
Now that the Azure Arc Connected Machine agent is installed and connected, the Azure Monitor Agent (AMA) service needs to be installed. The AMA is an Azure VM extension that can be installed after the Arc Connected Machine agent (azcmagent) is installed. - On the “Machine - Azure Arc” page, click on the host you connected.
- Navigate to “Settings” > “Extensions”. Click “Azure Monitor Agent for Linux”. Click the “Next” button near the bottom left of the page. Follow the wizard to install the extension.
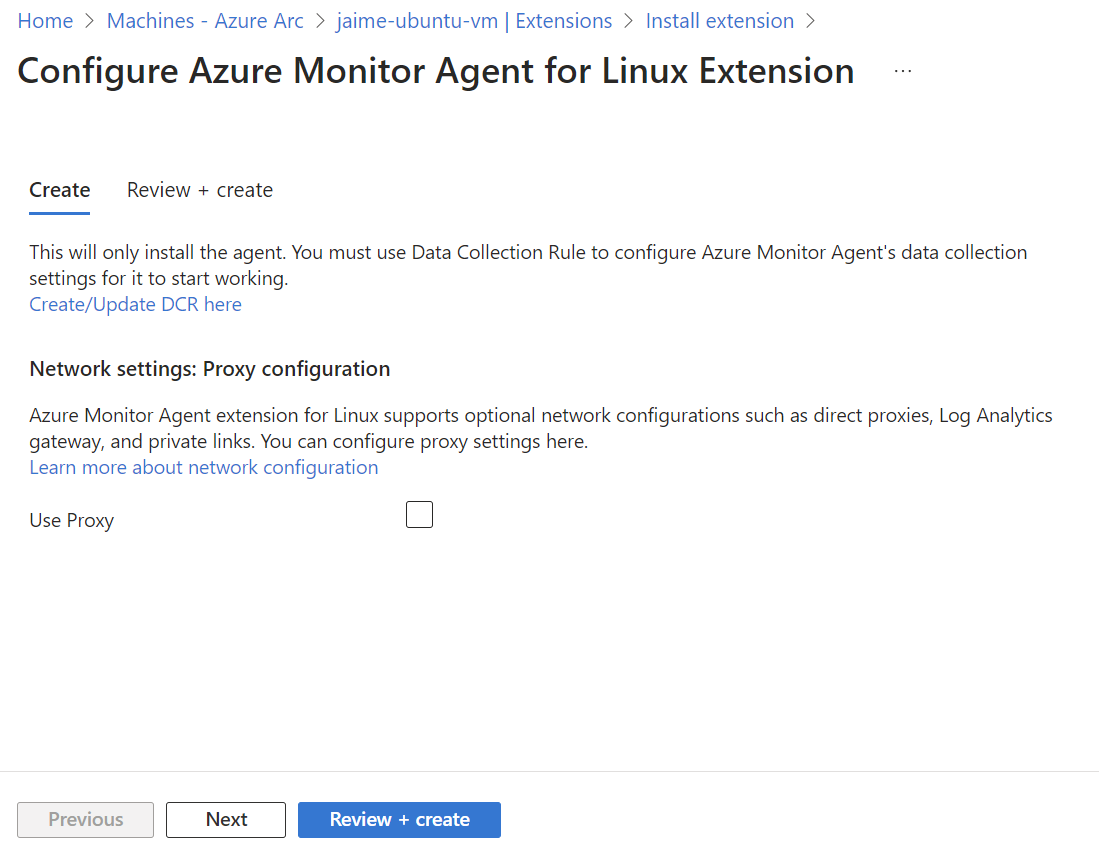
Create/Configure the Data Collection Endpoint (DCE) - Go to the Azure Portal home page and click “More services”.
- Use the search field to find “data collection endpoints”. Click on it.
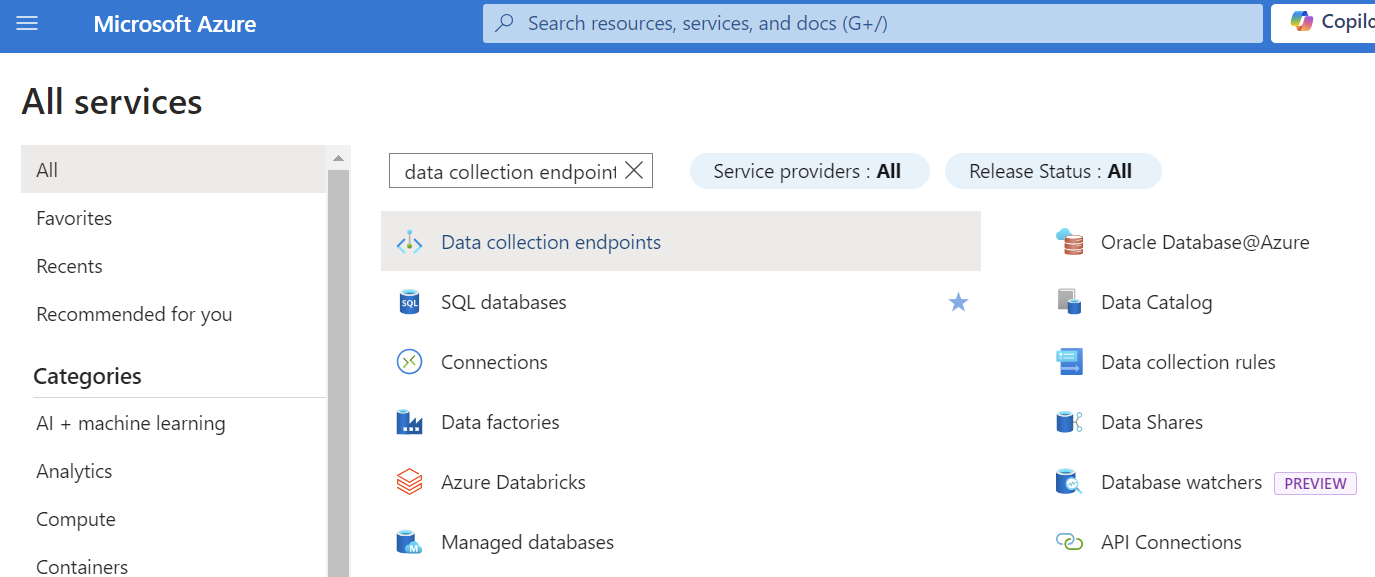
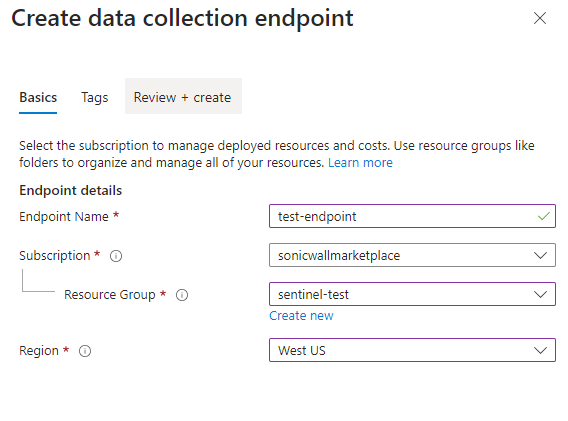
- Click the “Create” button. Provide the subscription, resource group, and region associated with your Microsoft Sentinel workspace. Complete the wizard.
Create/Configure the Data Collection Rule (DCR)
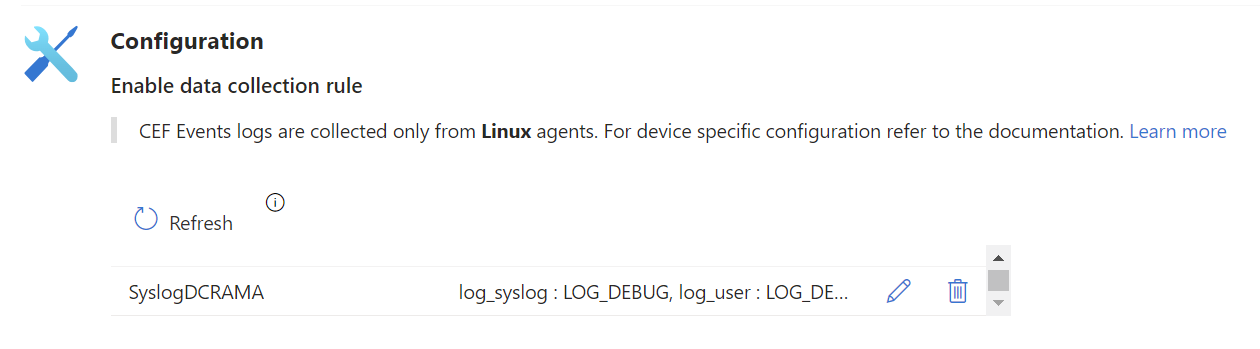
Back at the page you held from step 5… - There’s a table in the middle of the page that may not be easily visible. Use the scroll bar to find a data collection rule. If one is not visible by scrolling up/down, try clicking the “Refresh” button. If there are still no rules in the list, click the “+Create data collection rule“ button.
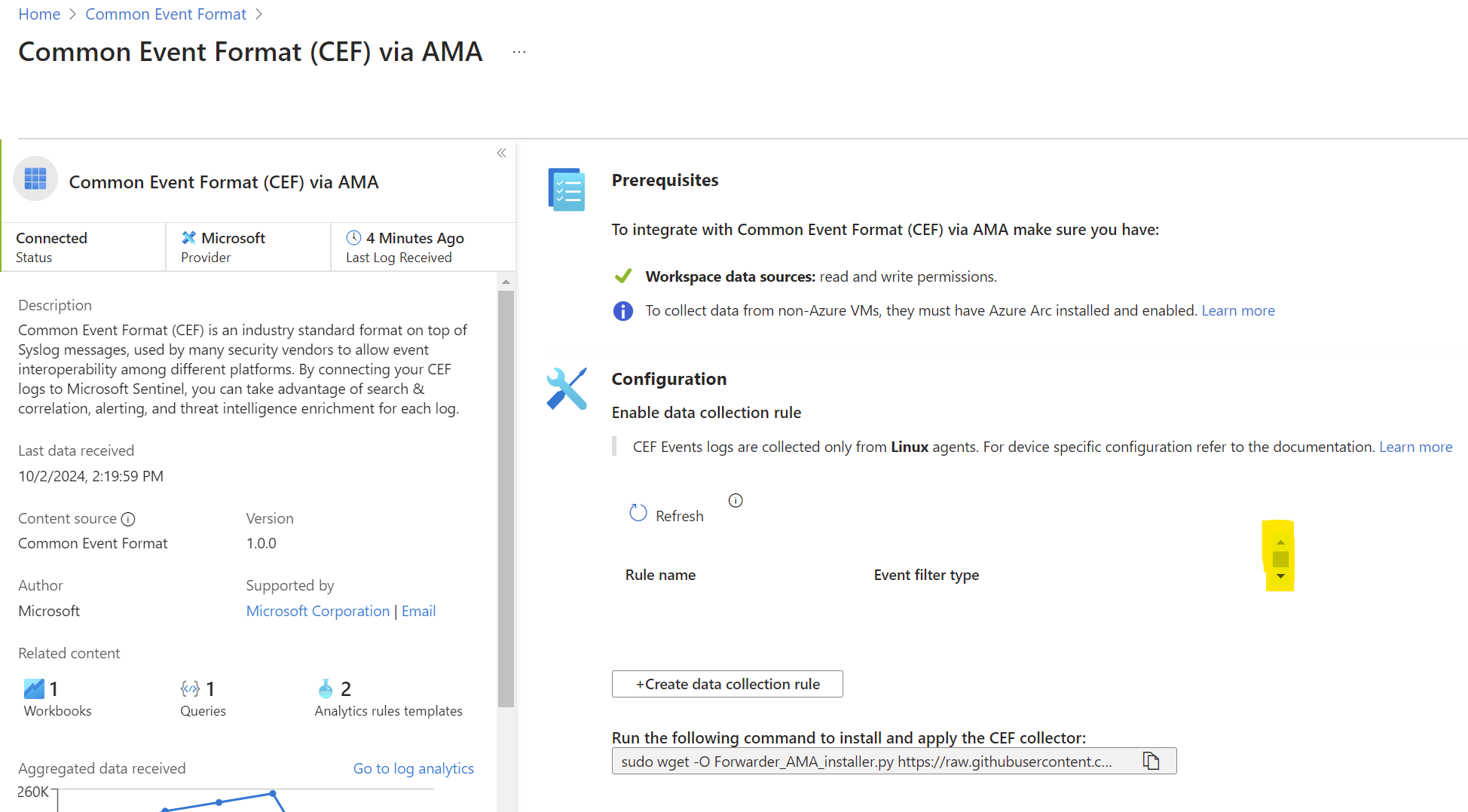
- If you are creating a new Data Collection Rule:
- On the Basics tab, provide a rule name and specify the subscription and resource group.
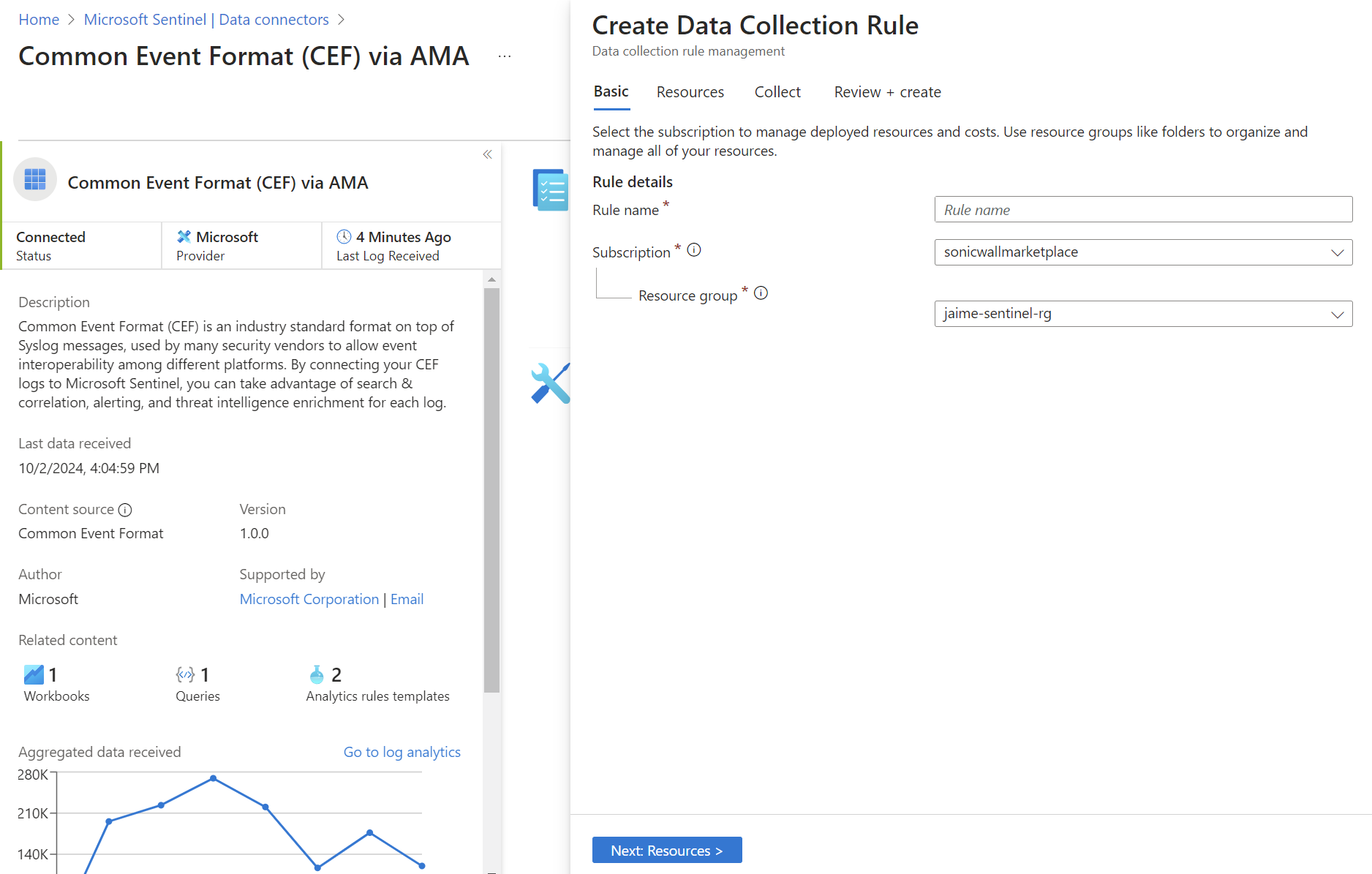
- On the Basics tab, provide a rule name and specify the subscription and resource group.
- If there’s a Data Collection Rule, edit it using the pencil icon. Click on the “Resources” tab. Use the search field to find the Arc host by name. Alternatively, you can browse through the resource groups to find the one where Microsoft Sentinel was deployed, which should also contain your Arc host. Select the Arc host.
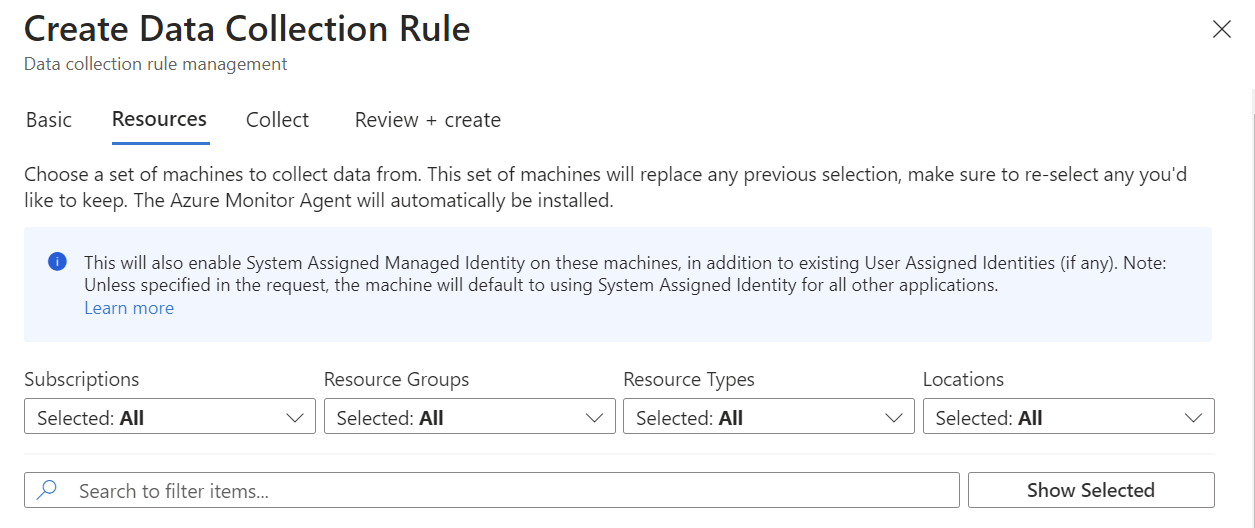
- Click the “Collect” tab.
- Disable “Collect messages without PRI header”.
- Set all of the LOG_* dropdown menus to “none”.
- Set “LOG_SYSLOG” to “LOG_DEBUG”.
- Set “LOG_USER“ to “LOG_DEBUG”.
- Complete the wizard to create the Data Collection Rule.
Install the Azure Monitor Agent (AMA) Forwarder - Use the following set of commands to install the Azure Monitor Agent (AMA) Forwarder. The forwarder
sudo wget -O Forwarder_AMA_installer.py https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/DataConnectors/Syslog/Forwarder_AMA_installer.py&&sudo python3 Forwarder_AMA_installer.py - Validate the connection and check for any failures using the accompanying help information. Use the following set of commands to download and run the Sentinel AMA Troubleshooter script.
sudo wget -O Sentinel_AMA_troubleshoot.py https://raw.githubusercontent.com/Azure/Azure-Sentinel/master/DataConnectors/Syslog/Sentinel_AMA_troubleshoot.py&&sudo python3 Sentinel_AMA_troubleshoot.py --cef
After successfully installing the forwarder and confirming there are no errors and CEF data was found, it may take several minutes to see data in the CommonSecurityLog table in Microsoft Sentinel.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO