-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How To Control GVC User Access Using Radius Authentication



Description
This article describes how to control GVC users' access to network resources when using Radius Authentication. In this scenario two groups of Active Directory users needs to be allowed two types of access. One group shall have access to LAN Subnets and the other group shall have access only to a server on the LAN.
Resolution
Creating User Groups and configuring User Management for Radius Authentication in Active Directory.
- Open Active Directory Users and Computers and create the following two user groups in the Users folder.
- Full Access
- Restricted Users
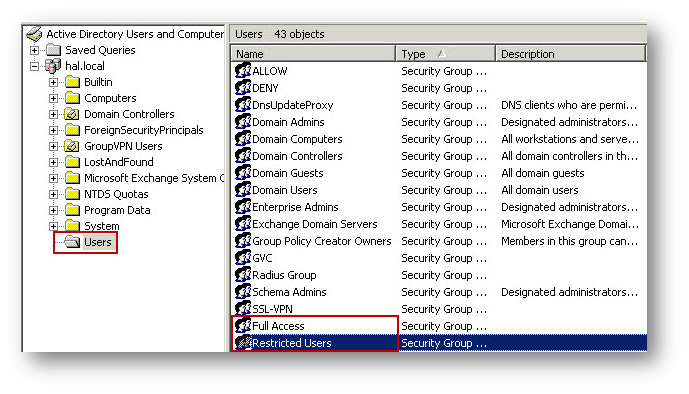
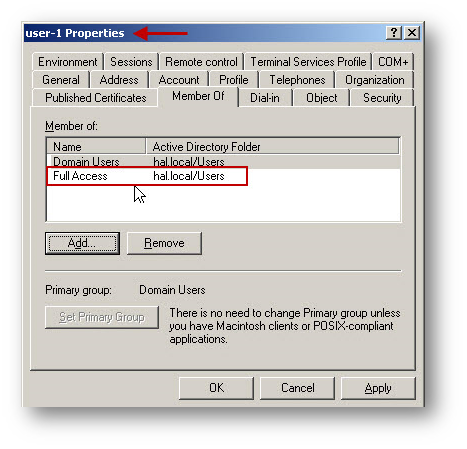
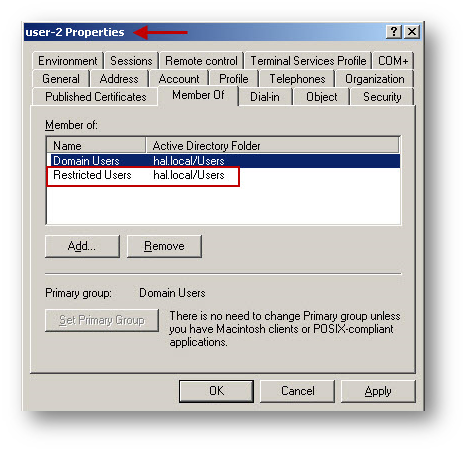
- Create two users and add each of them as a member of each User Group.
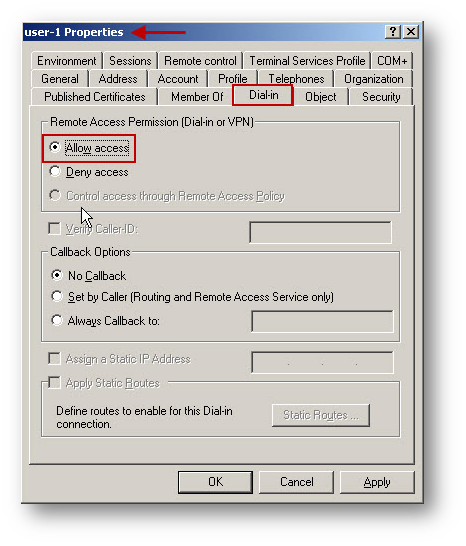
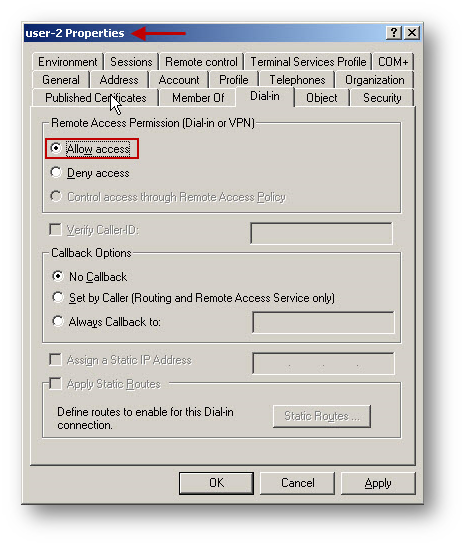
- Select the Dial-in tab and enable the Allow access option under Remote Access Permission.
Configuring the IAS Server to Support Radius Clients
- On the Windows 2003 Server, verify that you have applied the latest Service Pack and hotfixes. Also, verify that the “Remote Access and Routing Service” is running. To configure Radius Authentication in Windows Server 2008 please refer to Configuring RADIUS authentication for Global VPN Clients with Network Policy and Access Server.
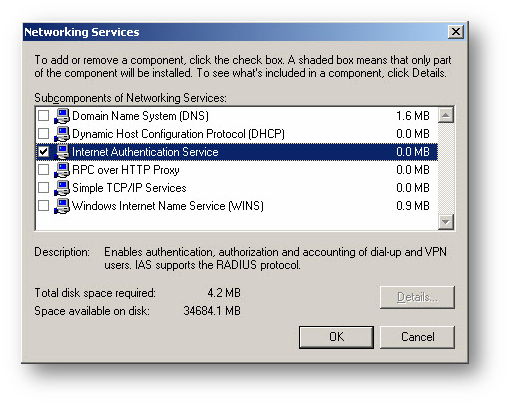
- Open Control Panel | Add or Remove Programs | Add/Remove Windows Components and find Networking Services. Press Details and check Internet Authentication Services and click OK.
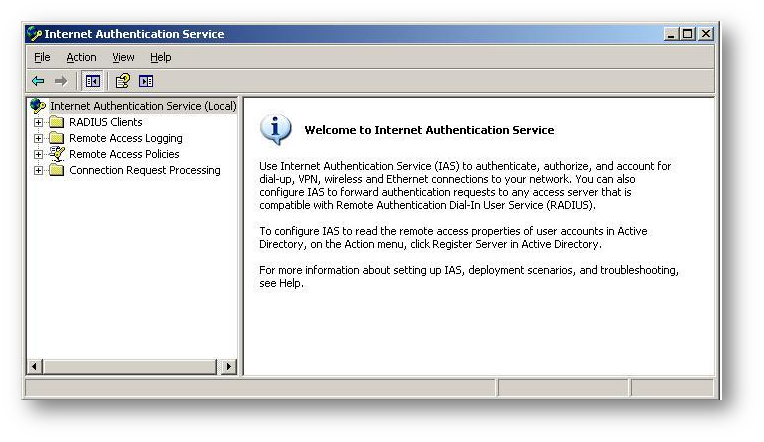
- Launch the IAS Console by clicking on Start | All Program| Administrative Tools | Internet Authentication Service. The following IAS console will appear.
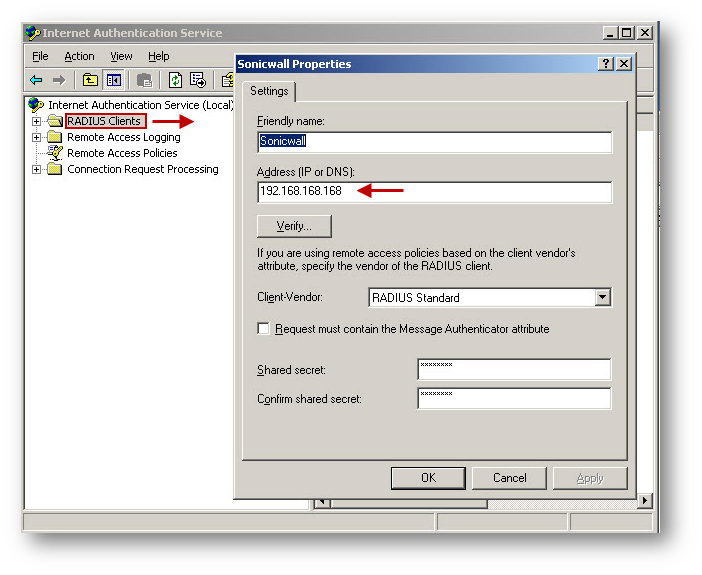
- Right click the RADIUS Clients folder in the left pane and select New RADIUS Client from the menu.
- Enter a name for the new Radius client and enter the LAN IP Address of the SonicWall.
- Select RADIUS Standard, (also the default option), enter a Shared Secret. This shared secret is needed later on the SonicWall security appliance, so note this for future reference.
- Click Finish.
- To setup the access criteria for users, right click on the Remote Access Policies and select New Remote Access Policy.
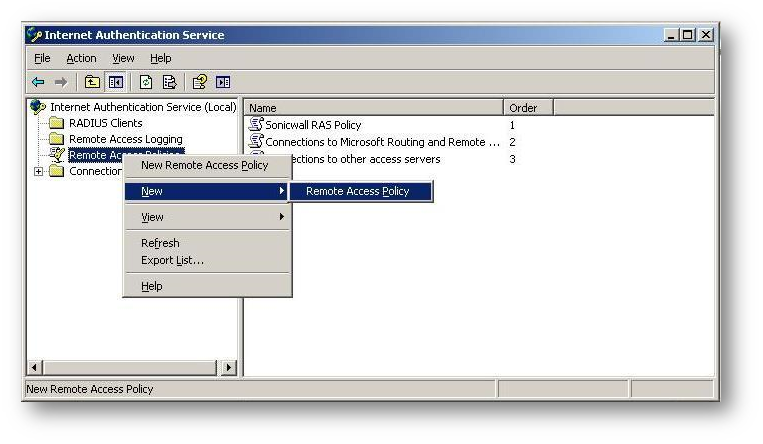
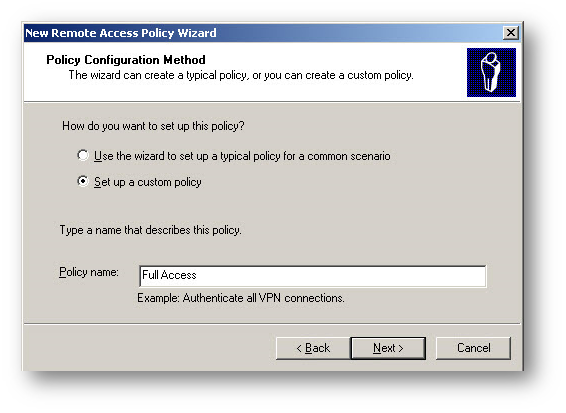
- Click Next on New Policy Wizard. Select “Set up a custom policy” radio button and then enter a name for this policy.
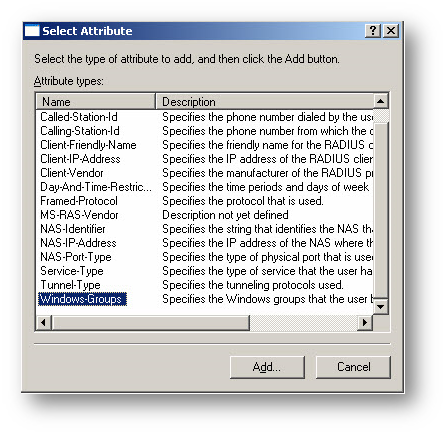
- Click Add on the Policy Conditions window.
- From this list, select Windows Groups, and click OK. By selecting Windows Groups, you can authenticate a user who is a member of a User Group in the Windows AD.
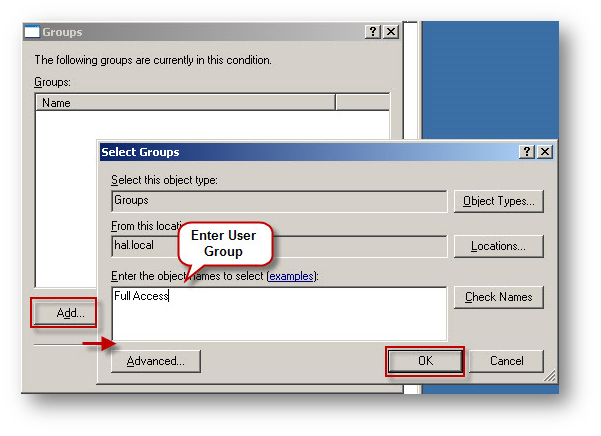
- Click Add, then enter the Windows User Group "Full Access". Click OK.
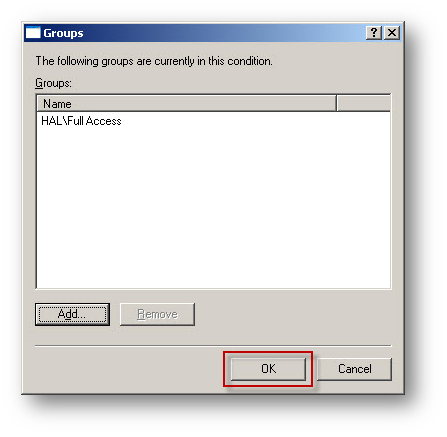
- Back on the New Remote Access Policy window, click Next.
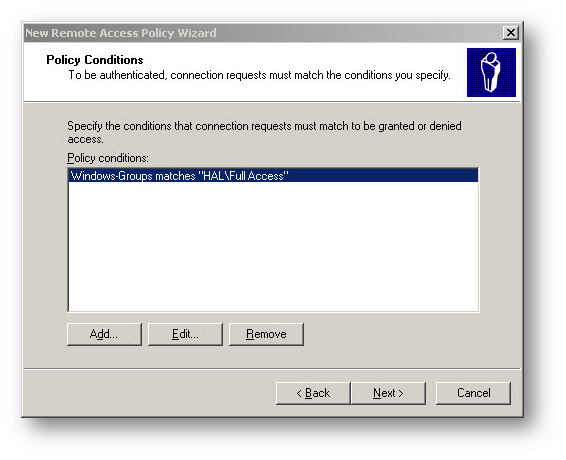
- Select the Grant remote access permission radio button under the option If a connection request matches the specified conditions.
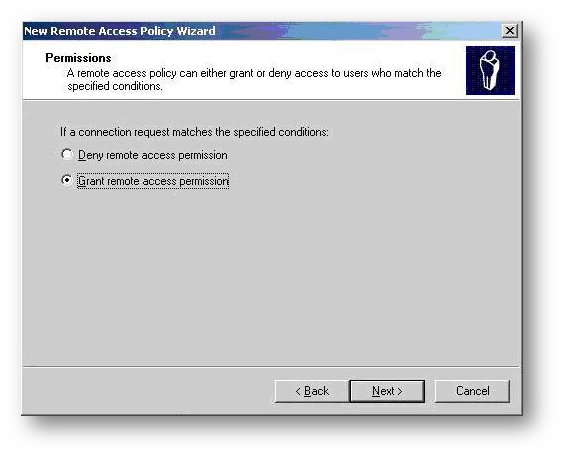
- On the Profile window click on the Edit Profile button
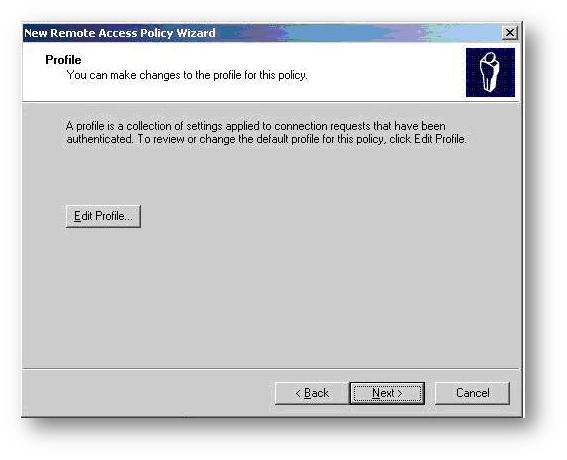
- The Edit Dial-in Profile window will appear. Click on the Authentication tab.
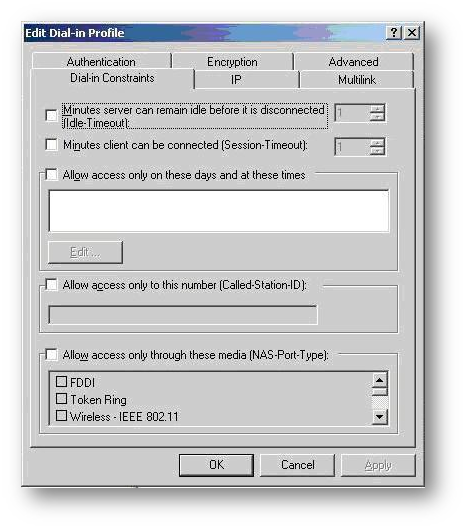
- Under the Authentication tab select MS-CHAP-V2, MS-CHAP and PAP as authentication method.
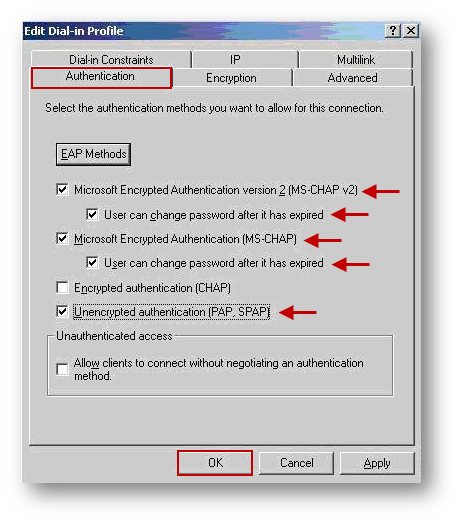
- The following message box appears, Click No on the help message box
- Click Next on the Policy Window and then click Finish to complete.
- Create another Policy named "Restricted Access" with identical settings as above except the Policy Condition would be Windows User Group "Restricted User"
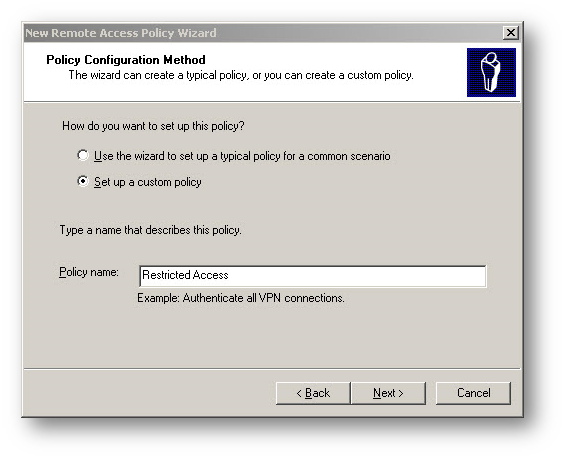
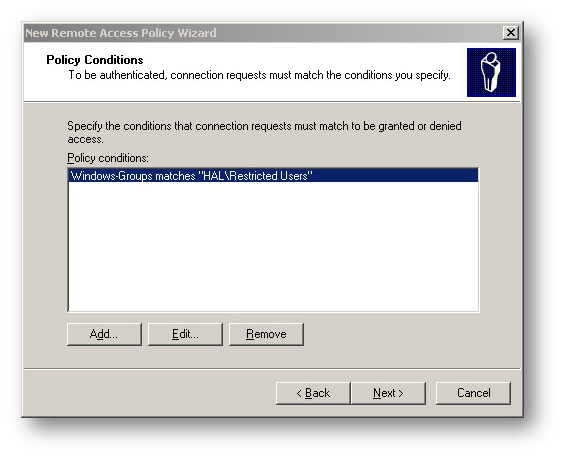
This completes the IAS configuration. If you have other groups on the AD that needs different access, you can add more Remote authentication policies.
Duplicating Active Directory User Groups in the SonicWall Security Appliance
- Login to the SonicWall Management interface.
- Go to the Users | Local Groups.
- Create the following 3 User Groups
- GVC Users
- Full Access (This has to be identical to the User Group created in the Active Directory)
- Restricted Users (This has to be identical to the User Group created in the Active Directory)
- Add users groups Full Access and Restricted Users as members of GVC Users
Set the VPN Access for user group Full Access as LAN Subnets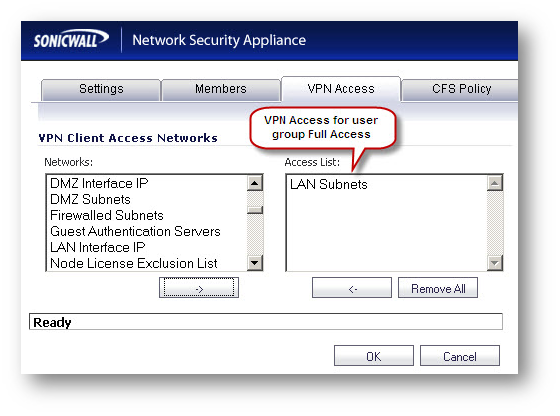
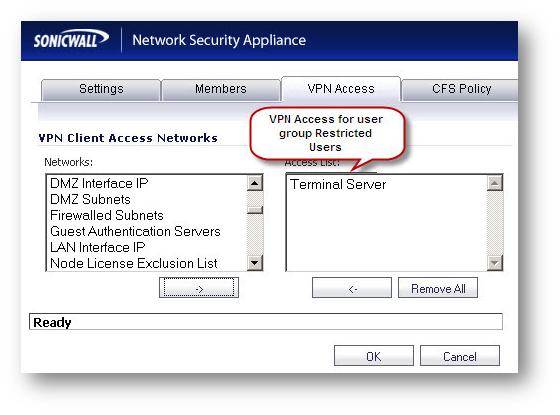
- Set the VPN Access for user group Restricted Users as a server on the LAN.
Configuring WAN GroupVPN in the SonicWall Security Appliance.
- Navigate to VPN | Settings.
- Configure WAN GroupVPN as normal except under the Advanced tab of WAN GroupVPN, set Client Authentication to GVC Users
- Set Virtual Adapter Settings to DHCP Lease
- Set Allow Connections to to Split Tunnels.
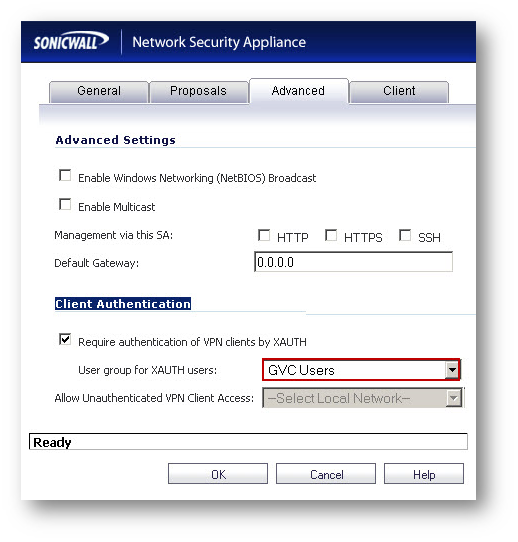
Configuring Users Settings for Radius Authentication.
- Navigate to Users | Settings.
- Select RADIUS + Local Users under Authentication method for login and click Configure.
- Enter the IP address of the Radius Server and the Shared Secret for the RADIUS server. Note: The Shared Secret has to be identical to the one entered in the Radius Client in IAS.
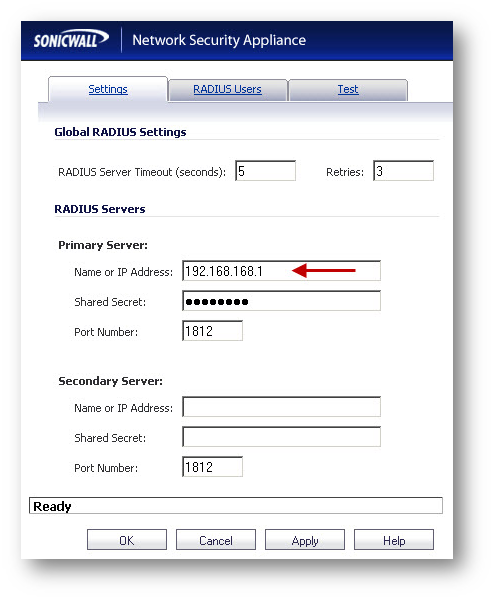
- Click on the Radius Users tab and select the radio button under Use RADIUS Filter-Id attribute on RADIUS server.
- Click Apply and then click on the Test tab. Type in the domain user name and password and test the authentication.
How to Test:
- Initiate a connection from a remote GVC client.
- When prompted for username and password, enter the username "user-1" and the password set for that user.
- On successfully connecting after being authenticated, try to ping the IP Address of a host in the LAN.
- According to the VPN Access for this user's group you should be able to access the entire LAN resources.
- Disconnect the GVC connection.
- Reconnect with username as "user-2" and the password set for that user.
- On successfully connecting after being authenticated, try to ping the IP Address of the Terminal Server in the LAN.
- Try to ping the IP Address of a host in the LAN and it should fail.
- According to the VPN Access for this user's group you should be able to access only the Terminal Server.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > User Login
- Firewalls > NSv Series > User Login
- Firewalls > TZ Series > User Login






 YES
YES NO
NO