-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Configuring RADIUS authentication for Global VPN Clients with Network Policy and Access Server



Description
Configuring RADIUS authentication for Global VPN Clients with Network Policy and Access Server from Microsoft Windows 2008.
RADIUS can be used as an Authentication, Authorization and Accounting Server (AAA). The RADIUS server authenticates client requests either with an approval or reject. RADIUS Server not only authenticates users based on the username and password but also authorizes based on the configured policy – whether the User group to which the user belongs is authorized or not; time constraints and various other policies if configured.
Click here for the video tutorial of Radius Authentication.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Configuring WAN Group VPN
- After logging into the firewall UI, navigate to Device | IPSec VPN | Rules and Settings and edit (configure) WAN Group VPN policy accordingly.
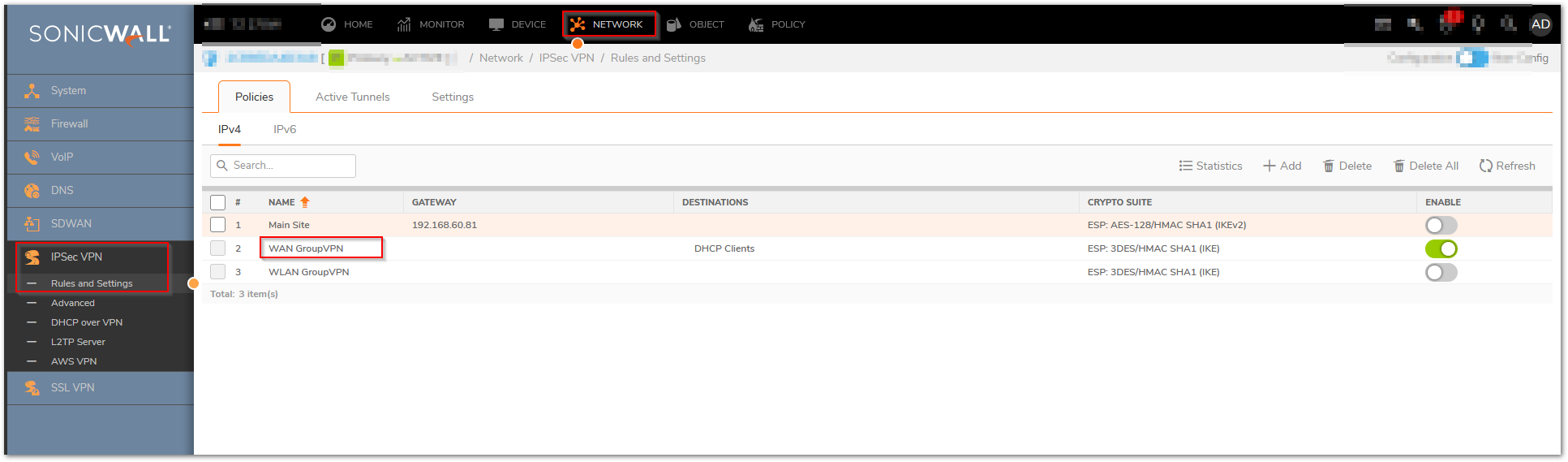
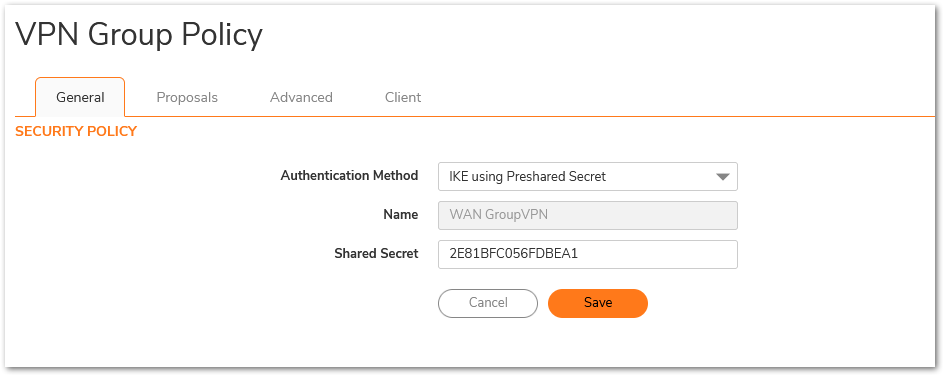
- Configure the policy with shared secret.
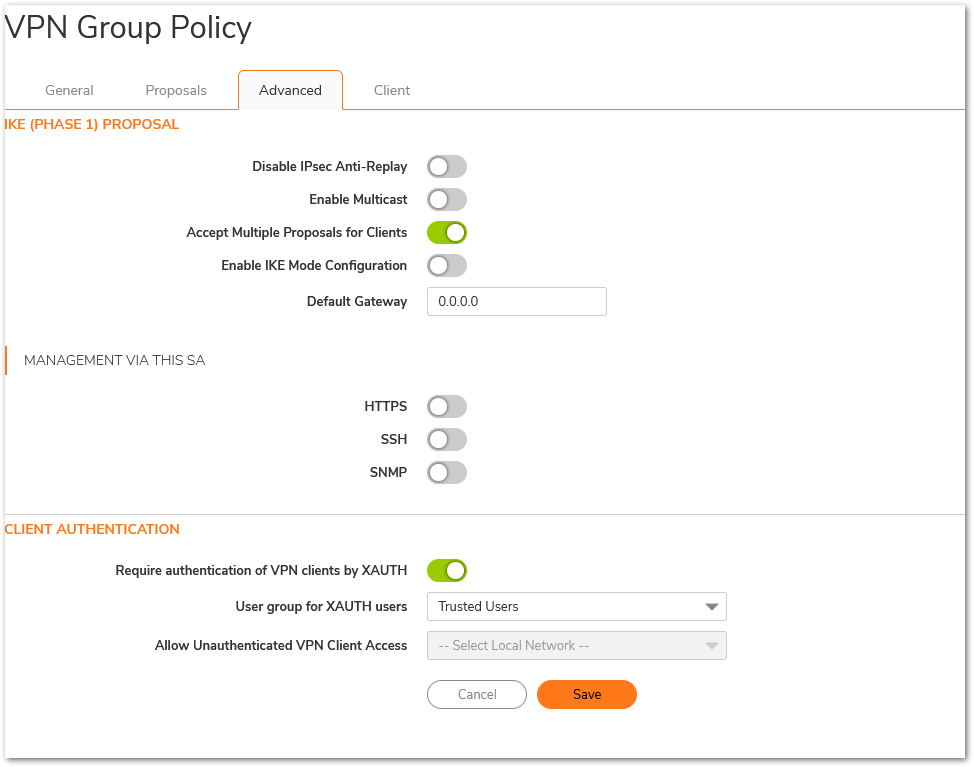
- Set VPN authentication and choose the appropriate group that you want to provide permission. Also you need to make sure that this group has VPN access permission to the desired subnets. You can restrict whether you want to provide access to a single subnet or multiple subnets.
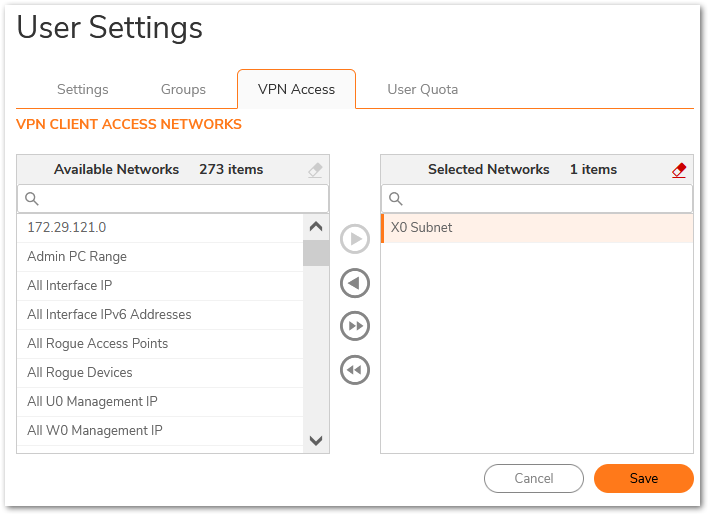
- Edit the user under Device | Users | Local Users & Groups | Local User edit a user and on the VPN Access tab and add the networks that can be accessed by this VPN user.
Configuring RADIUS on Firewall
- Navigate to Device | Users | Settings and click Configure Radius.
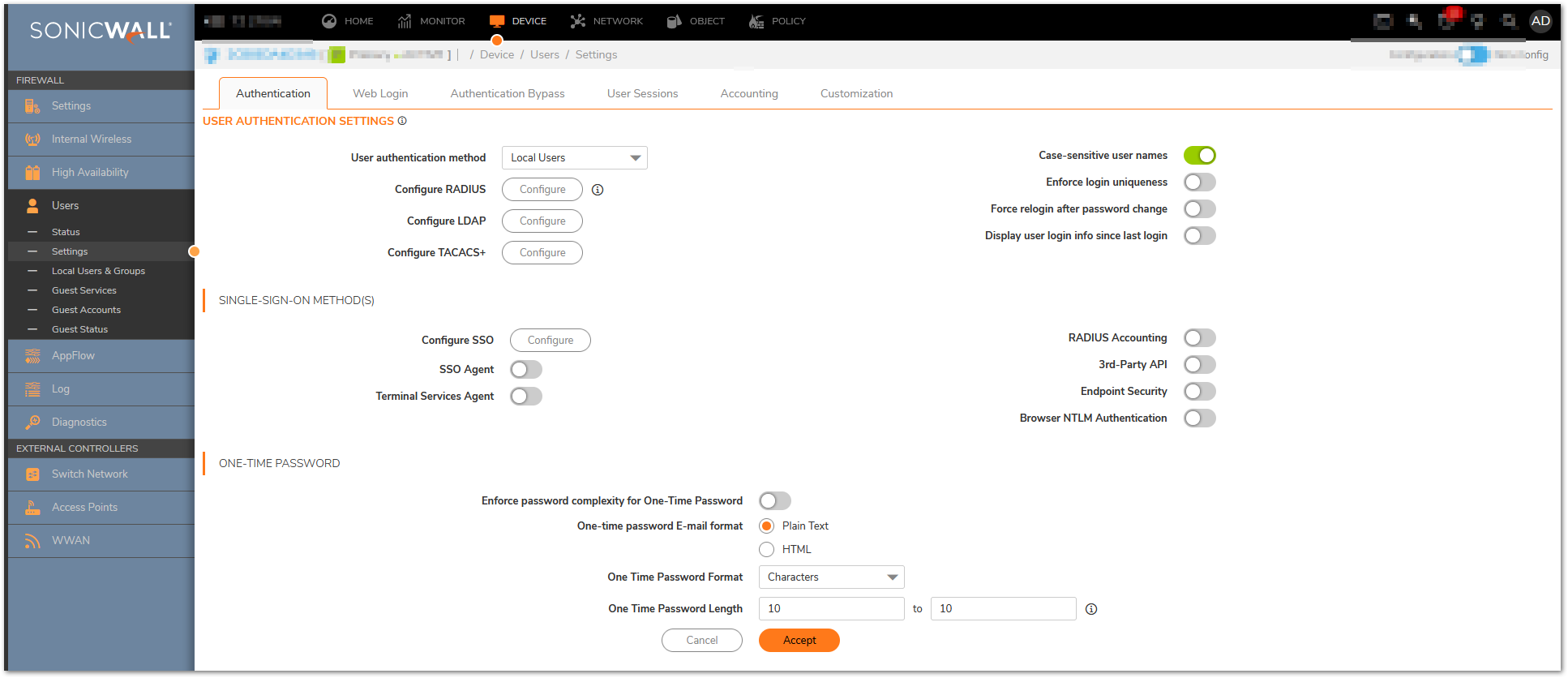
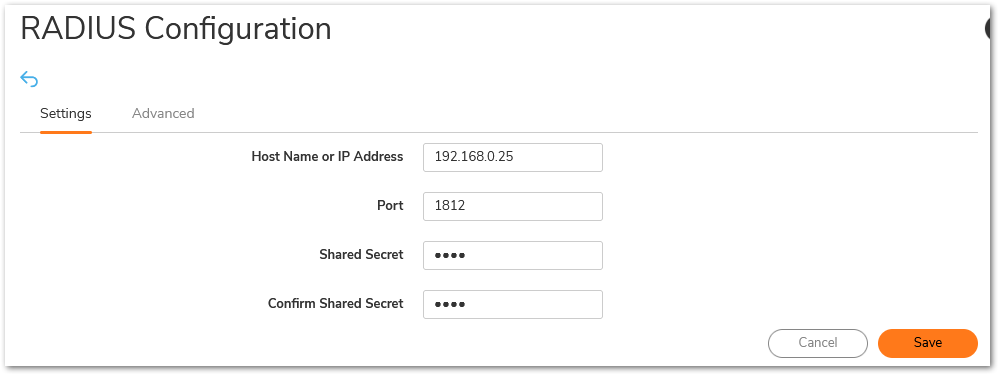
- Click Add and then Enter the IP address of the Primary RADIUS Server and the radius port. Microsoft supports both 1812 and 1645 for authentication. If you have a redundant RADIUS server in your environment, you can use it here. Enter the RADIUS server shared secret in the Shared Secret field. The alphanumeric Shared Secret can range from 1 to 31 characters in length. The shared secret is case sensitive. This Shared secret is used in an encryption process to obscure certain details in RADIUS messages such as user passwords.
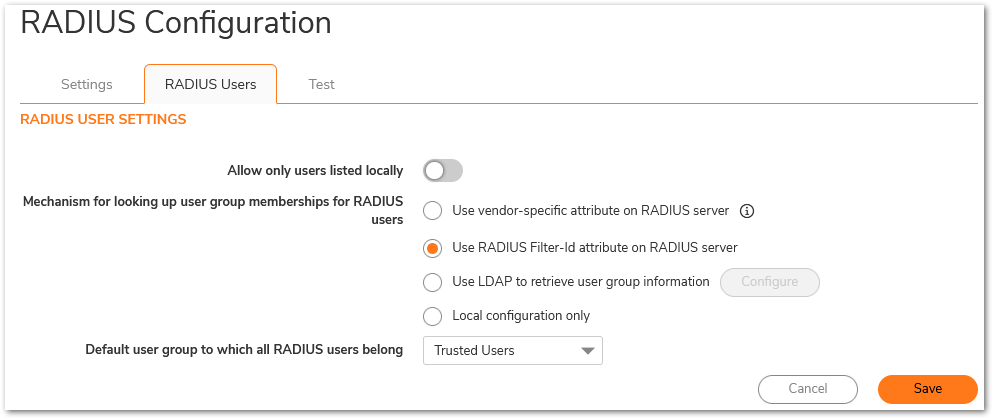
Configuring RADIUS Client and Associated Policy on Network Policy and Access
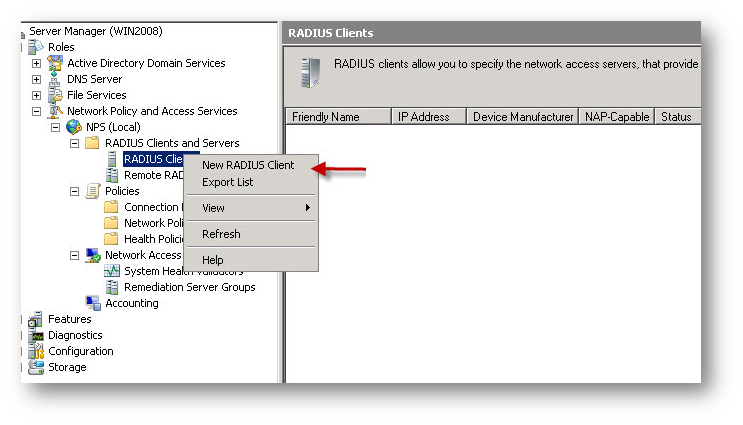
- Configure new RADIUS Client in network in Network Policy and Access Services with IP address of SonicWall Firewall and shared secret.
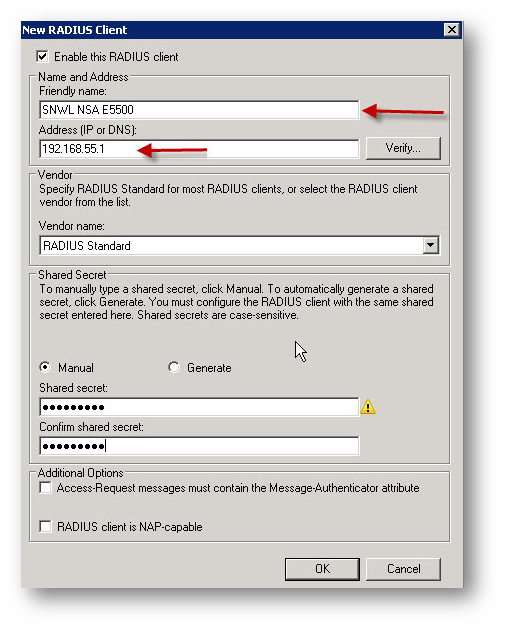
- Configure RADIUS Policy that will allow users to get authenticated.


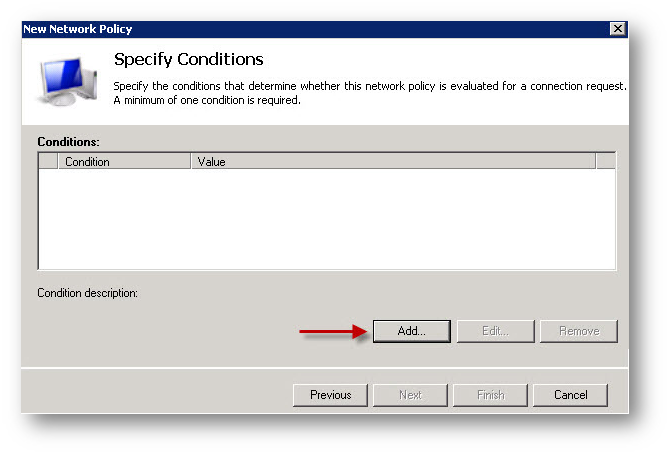
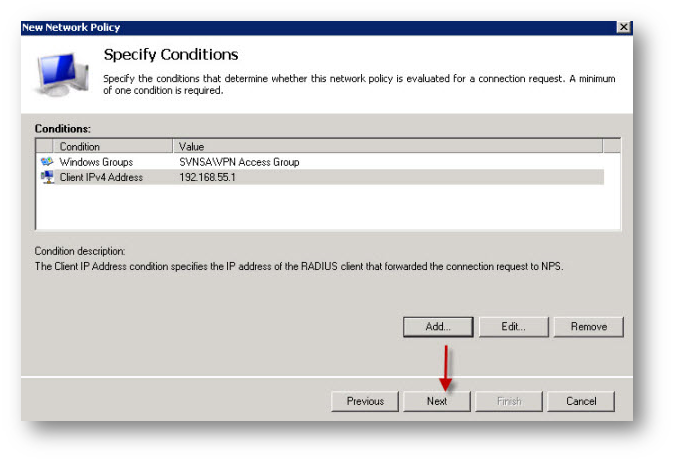
- Specify the LDAP User group that you want to give access to the resources on the network.


- You can optionally add SonicWall Interface IP address (RADIUS Client IP) in the policy so that the server can only accept incoming Radius requests from SonicWall.



- Configure the authentication methods that you want to allow. SonicWall recommends using MS-CHAP or MS-CHAP V2 as an authentication method. When using RADIUS to authenticate VPN client users, RADIUS will be used in its MSCHAP (or MSCHAPv2) mode. The primary reason for choosing to do this would be so that VPN client users can make use of the MSCHAP feature to allow them to change expired passwords at login time.



- Make sure that the configured policy has higher precedence or processing order than the default deny Connections to other access servers policy.
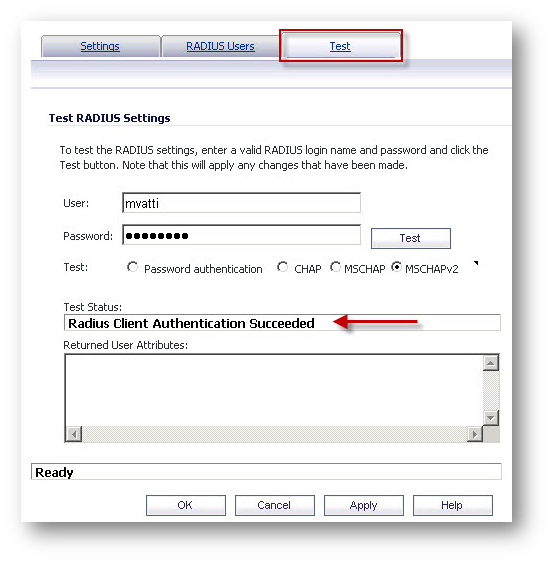
Testing
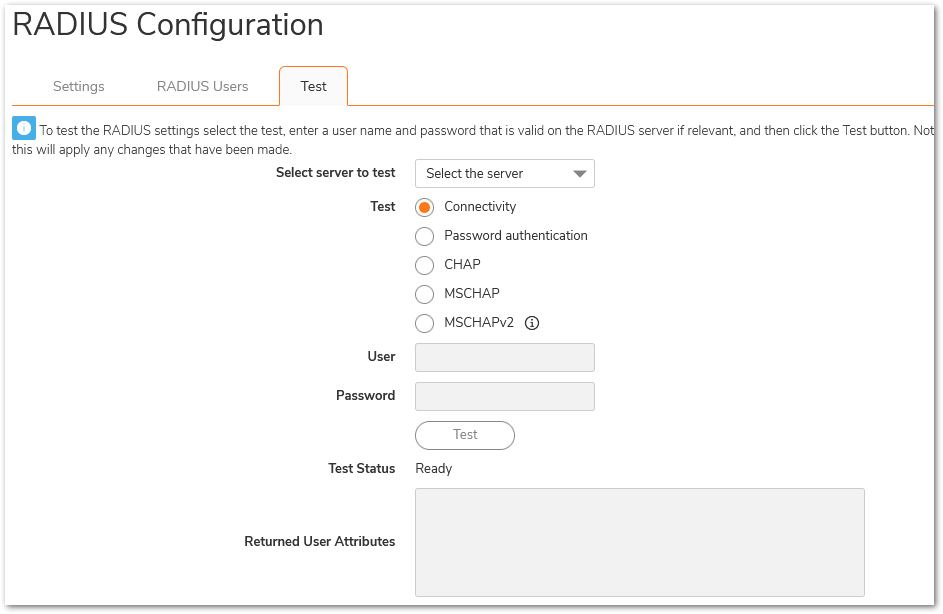
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Configuring WAN Group VPN
- After logging into the firewall UI, navigate to Manage | VPN | Basic Settings and edit (configure) WAN Group VPN policy accordingly.
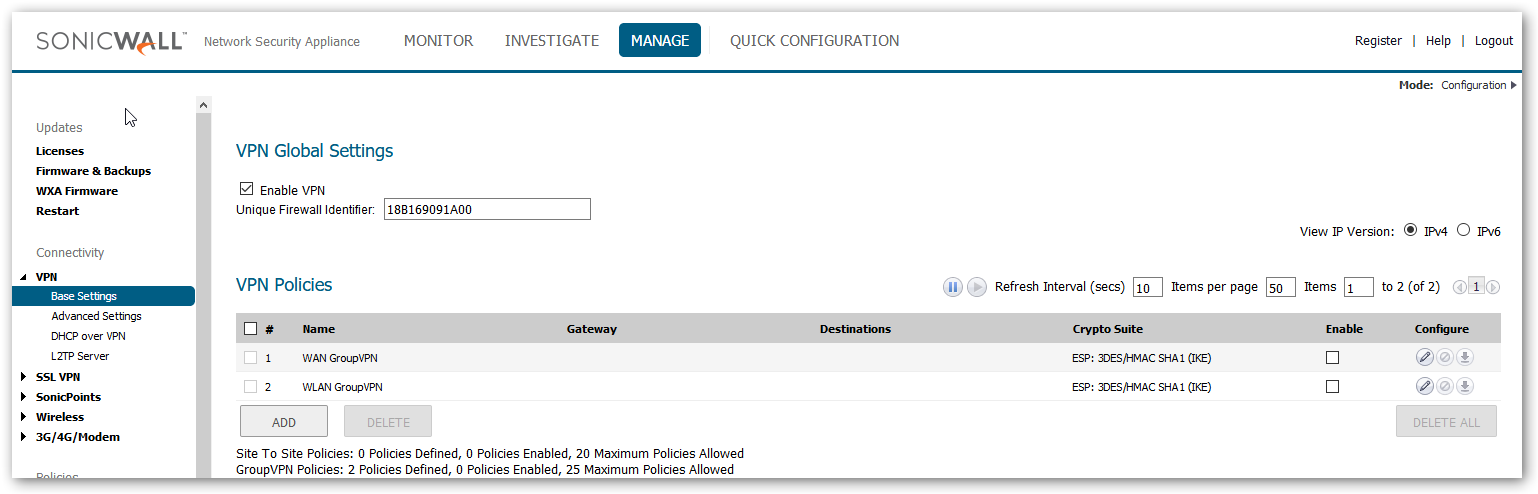
- Configure the policy with shared secret.
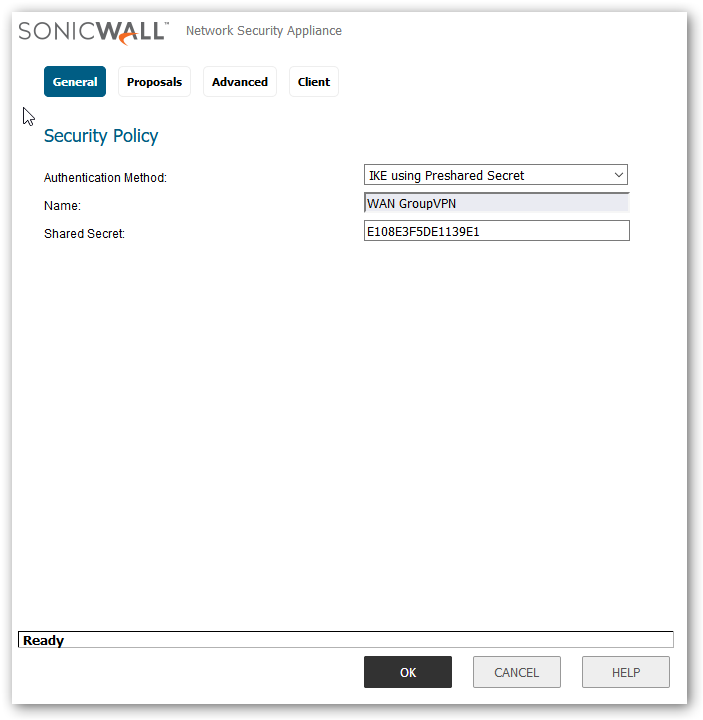
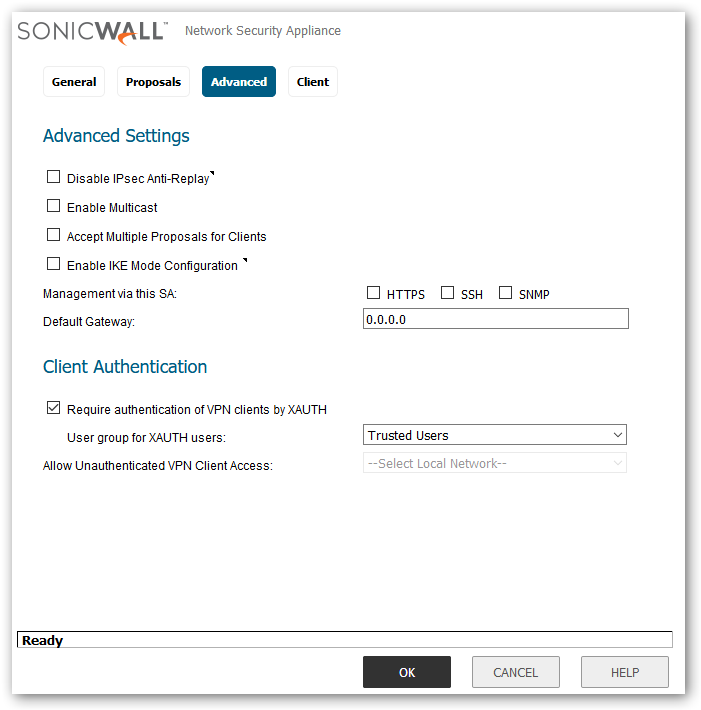
- Set VPN authentication and choose the appropriate group that you want to provide permission. Also you need to make sure that this group has VPN access permission to the desired subnets. You can restrict whether you want to provide access to a single subnet or multiple subnets.
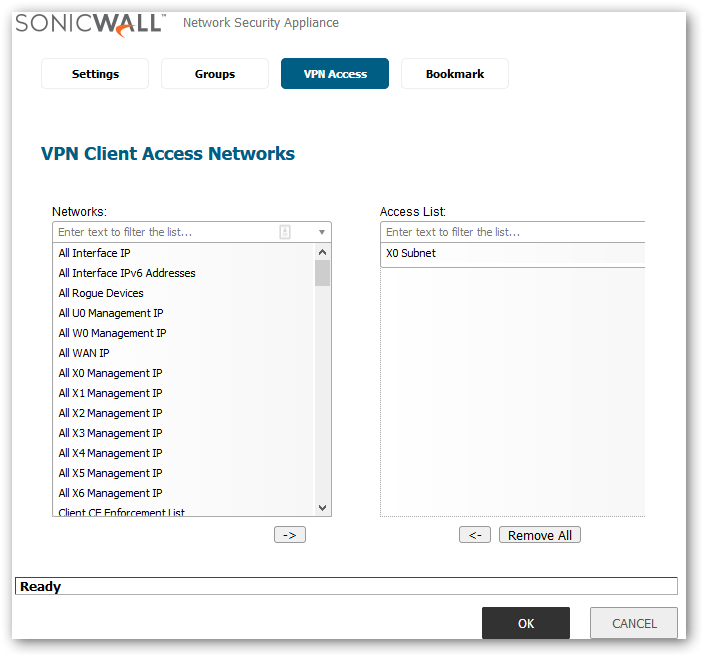
- Edit the user under Manage | Users | Local Users & Groups | Local User edit a user and on the VPN Access tab and add the networks that can be accessed by this VPN user.
Configuring RADIUS on Firewall
- Navigate to Manage | Users | Settings and click Configure Radius.
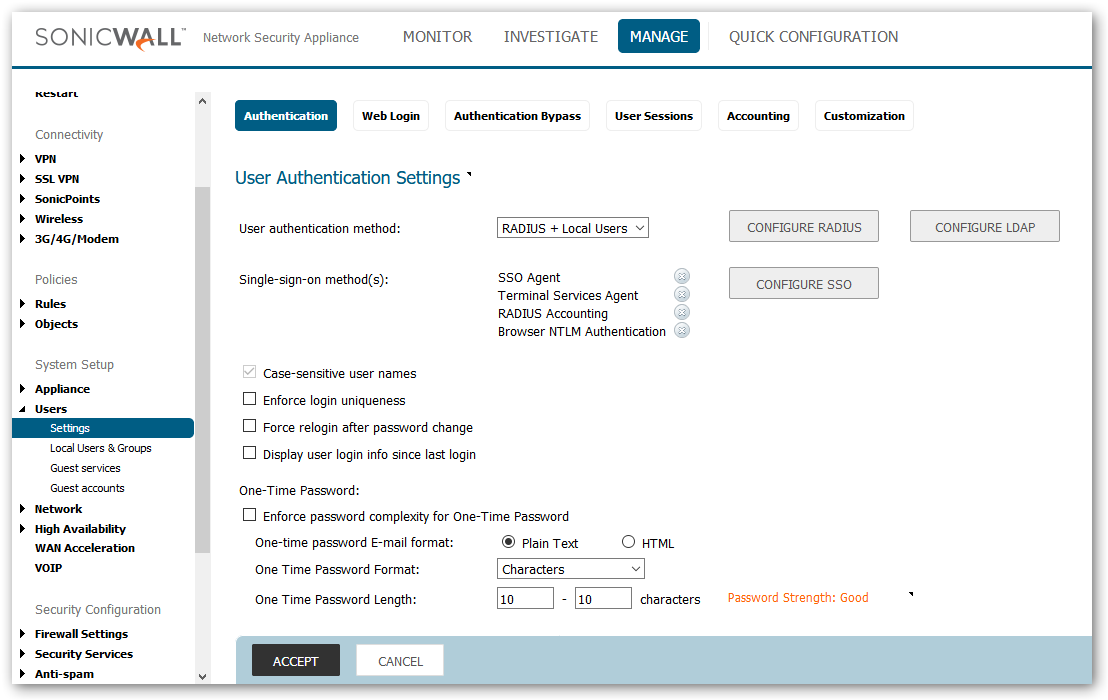
- Click Add and then Enter the IP address of the Primary RADIUS Server and the radius port. Microsoft supports both 1812 and 1645 for authentication. If you have a redundant RADIUS server in your environment, you can use it here. Enter the RADIUS server shared secret in the Shared Secret field. The alphanumeric Shared Secret can range from 1 to 31 characters in length. The shared secret is case sensitive. This Shared secret is used in an encryption process to obscure certain details in RADIUS messages such as user passwords.

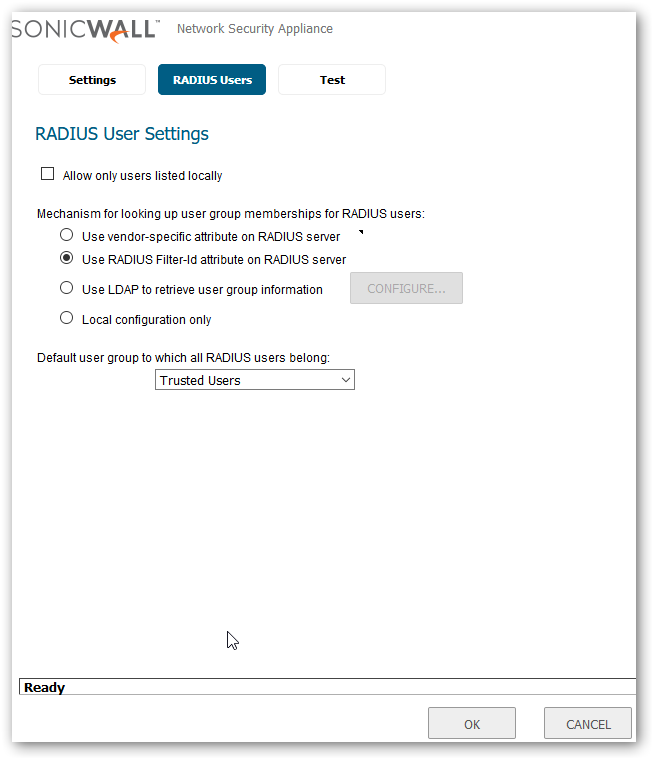
Configuring RADIUS Client and Associated Policy on Network Policy and Access
- Configure new RADIUS Client in network in Network Policy and Access Services with IP address of SonicWall Firewall and shared secret.


- Configure RADIUS Policy that will allow users to get authenticated.



- Specify the LDAP User group that you want to give access to the resources on the network.


- You can optionally add SonicWall Interface IP address (RADIUS Client IP) in the policy so that the server can only accept incoming Radius requests from SonicWall.




- Configure the authentication methods that you want to allow. SonicWall recommends using MS-CHAP or MS-CHAP V2 as an authentication method. When using RADIUS to authenticate VPN client users, RADIUS will be used in its MSCHAP (or MSCHAPv2) mode. The primary reason for choosing to do this would be so that VPN client users can make use of the MSCHAP feature to allow them to change expired passwords at login time.



- Make sure that the configured policy has higher precedence or processing order than the default deny Connections to other access servers policy.
Testing
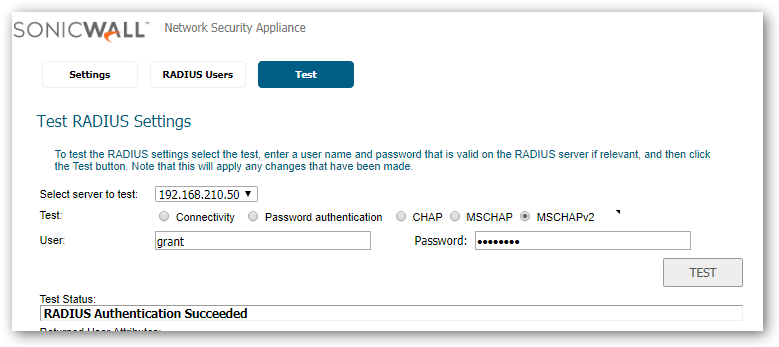
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Configuring WAN Group VPN
- After logging into the firewall UI, navigate to VPN | Settings and edit (configure) WAN Group VPN policy accordingly.

- Configure the policy with shared secret.


- Set VPN authentication and choose the appropriate group that you want to provide permission. Also you need to make sure that this group has VPN access permission to the desired subnets. You can restrict whether you want to provide access to a single subnet or multiple subnets.

- Edit the user under Users tab and add the networks that can be accessed by this VPN user.

Configuring RADIUS on firewall

- Enter the IP address of the Primary RADIUS Server and the radius port. Microsoft supports both 1812 and 1645 for authentication. If you have a redundant RADIUS server in your environment, you can use it here. Enter the RADIUS server shared secret in the Shared Secret field. The alphanumeric Shared Secret can range from 1 to 31 characters in length. The shared secret is case sensitive. This Shared secret is used in an encryption process to obscure certain details in RADIUS messages such as user passwords.


Configuring RADIUS Client and Associated Policy on Network Policy and Access
- Configure new RADIUS Client in Network in Network Policy and Access Services with IP address of SonicWall firewall and shared secret.


- Configure RADIUS Policy that will allow users to get authenticated.



- Specify the LDAP User group that you want to give access to the resources on the network.


- You can optionally add SonicWall Interface IP address (RADIUS Client IP) in the policy so that the server can only accept incoming Radius requests from SonicWall.




- Configure the authentication methods that you want to allow. SonicWall recommends using MS-CHAP or MS-CHAP V2 as an authentication method. When using RADIUS to authenticate VPN client users, RADIUS will be used in its MSCHAP (or MSCHAPv2) mode. The primary reason for choosing to do this would be so that VPN client users can make use of the MSCHAP feature to allow them to change expired passwords at login time.



- Make sure that the configured policy has higher precedence or processing order than the default deny Connections to other access servers policy.
Testing
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > SonicWall SuperMassive 9000 Series > GVC/L2TP
- Firewalls > TZ Series > GVC/L2TP
- Firewalls > NSa Series > GVC/L2TP
- Firewalls > NSv Series > GVC/L2TP






 YES
YES NO
NO