RisePro Malware Assembles On-site

Overview
This week, the SonicWall Capture Labs threat research team analyzed a sample of RisePro malware. This is a Malware-as-a-Service family that excels in stealing data, especially related to cryptocurrency wallets. It is a multi-stage executable with layers of obfuscation, indirect API calls and extensive evasion capabilities in the form of dynamically built file types and process monitoring.
Technical Analysis
In what will become a running theme, the detection does not necessarily match the file type. The parent sample is detected as a 19MB NSIS executable.
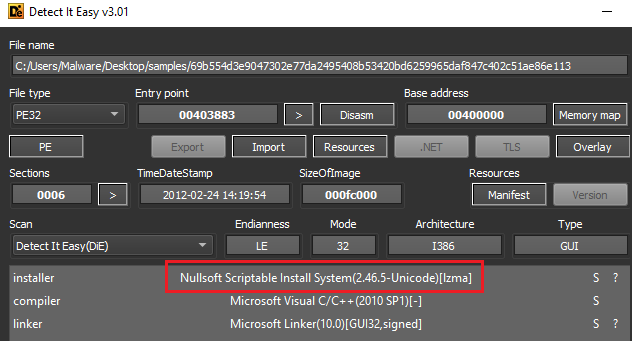
There are several immediate items of note when attempting to unpack or decompress the file. First, while 7zip can open the file to show certain contents, there is only a single ‘$TEMP’ directory with forty-seven files. Each file has an arbitrary name with no extension, and there are no installation scripts.

The next item of note is that the file is artificially inflated; memory offset 0025ae20-012c1220 is a single repeated null byte. Removing these with a debloat tool shows an actual file size of just over 2.4MB. Attempting to decompress the file to see additional instructions or scripts fails as it is not recognized as LZMA, despite detections. A secondary unpacker successfully extracted a complete executable.
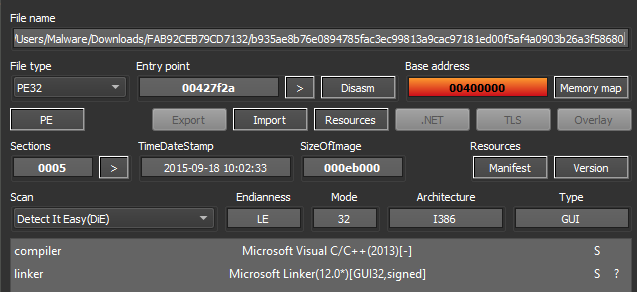
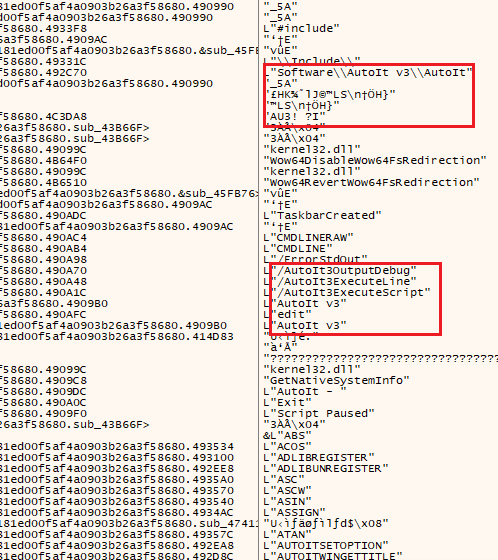
This file shows an AutoIT script residing in the whole of the .rdata section.
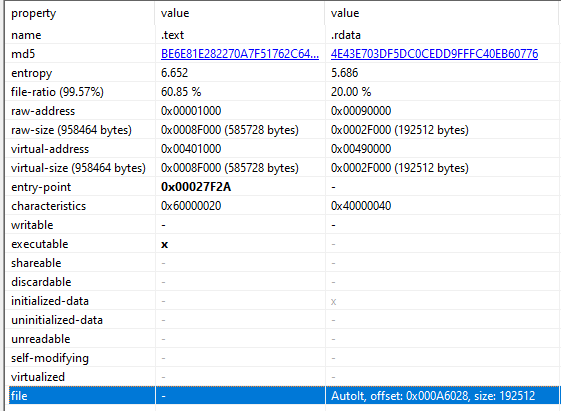
Once again, using binwalk, HxD, and Exe2Aut failed to pull a functional AutoIT script despite detection. Manually carving the bytes to a .bin file shows a large swath of the script is repeating characters, indicative of dynamic decryption at runtime.
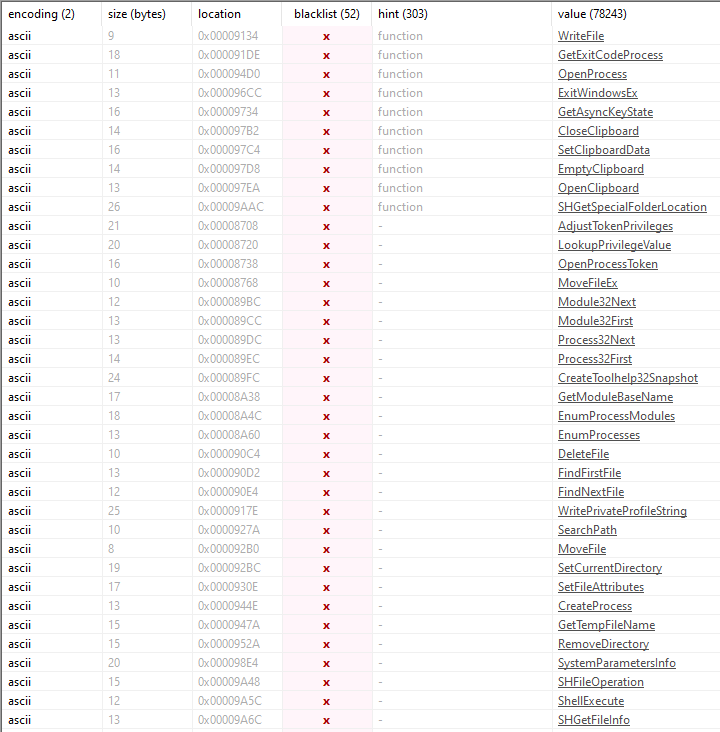
The executable has many cleartext API calls showing the monitoring and enumeration capabilities. Processes, files, drives, and windows can be iterated through using Process32First/Next, Module32First/Next, FindFirstFile, FindNextFile, and SearchPath.
Infection is done in the following manner:
- Runtime begins by checking the locale and languages installed on the system, followed by processes and active windows. The CPU and system hardware are checked via GetNativeSystemInfo and CPUID.
- Emotions and Emotions.cmd are copied and loaded into memory.
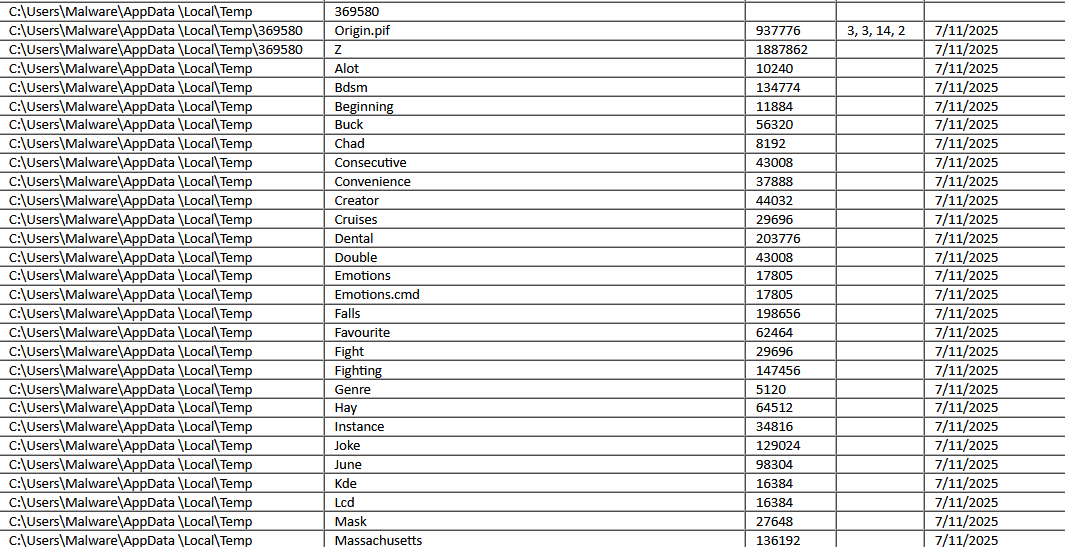
- All extensionless files are dropped to ~AppData/Local/Temp, as well as a directory named ‘369580’ that contains two files: ‘Origin.pif’, and another extensionless file named ‘Z’. Origin is listed as a shortcut but it is in fact an executable.
- Origin.pif creates ‘SecureHawk.js’ and ‘SecureHawk.pif’ (duplicate and renamed Origin file).
- SecureHawk.js runs with the command: schtasks.exe /create /tn "SecureHawk" /tr "wscript //B 'C:\Users\user\AppData\Local\LinkGuard Dynamics\SecureHawk.js'" /sc onlogon /F /RL HIGHEST
- System and drive enumeration occurs
- Socket is opened for backdoor access
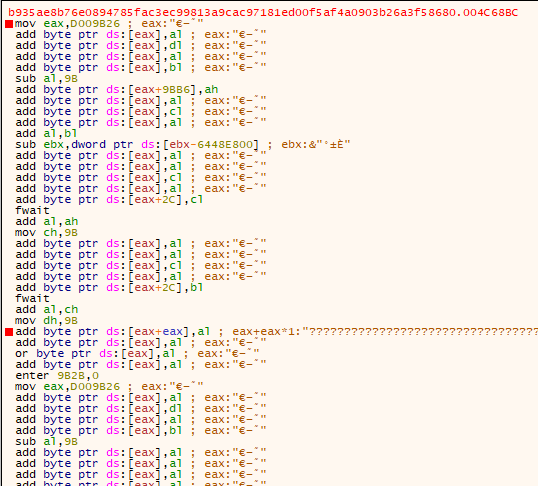
It should be noted that only one of the extensionless files (“Participants”) has magic numbers or shows file types when viewed in a hex editor. During runtime, the process will actively monitor for debugging software using GetProcAddress, OutputDebugString, GetProcHeap, GetLastError, GetTickCount, and QueryPerformanceCounter. It can also use BlockInput to stop keyboard or mouse input, as GetCursorPos is consistently checked, and GetKeyState/GetAsyncKeyState is also monitored.
If using the secondary unpacked file, it will open a dialogue box during runtime (if being debugged) and ask for an AutoIT script. If fed the carved file, the application eventually errors out; otherwise, the file will decode and re-encode bit by bit in memory. Once Origin.pif is built using
Additional enumeration is done with WMIC to gather system and drive information.
WMIC Commands Run:
IWbemServices::ExecQuery - root\cimv2 : SELECT __PATH, ProcessId, CSName, Caption, SessionId, ThreadCount, WorkingSetSize, KernelModeTime, UserModeTime FROM Win32_Process WbemServices::CreateInstanceEnum - root\SecurityCenter2 : AntiVirusProduct
AV Software Checks, Additional:
- wrsa.exe (Webroot Secure Anywhere)
- Opssvc.exe (Office Software Protection)
- avastui.exe (Avast Antivirus)
- avgui.exe (AVG Antivirus)
- bdservicehost.exe (BitDefender Antivirus)
- nswscsvc.exe (Norton Security Service)
- Sophoshealth.exe (Sophos Antivirus)
- C:\Program Files\Windows Defender\mpcmdrun.exe (checks file path)
Privilege escalation is done via token or using the LogonUserW API to logon to Windows as a different user. Given that there are many decision nodes within the code with ties to sleep functions, there are a high number of variables that could be matched for data collection and exfiltration.
Summary
To ensure SonicWall customers are prepared for any exploitation that may occur due to this malware, the following signatures have been released:
- RisePro.NSIS
- RisePro.Components
IOCs
- 69b554d3e9047302e77da2495408b53420bd6259965daf847c402c51ae86e113
- b935ae8b76e0894785fac3ec99813a9cac97181ed00f5af4a0903b26a3f58680
- 8498900e57a490404e7ec4d8159bee29aed5852ae88bd484141780eaadb727bb
- Fb199496184c801eea454e0534dec3ce932573892155fd8dd79efbd4aa734b4b
- 4a6fcc7e68d22a69db4735d3900f3ea63f767d67218610afd43ea8f1af9b4fb5
Share This Article

An Article By
An Article By
Security News
Security News

.png%3Fwith%3D384%26height%3D170&w=828&q=75&dpl=dpl_HuVLH8pYz2MyCXQwFgEmV4JmyVmj)