Triofox Unauthenticated Access Control Vulnerability (CVE-2025-12480)

Overview
The SonicWall Capture Labs threat research team became aware of an Improper Access Control Vulnerability in Gladinet Triofox, assessed its impact, and developed mitigation measures. Triofox enhances file management by combining the simplicity of cloud access with the security of on-premises storage, providing a secure, HTTPS-based solution for seamless file sharing and robust data protection. This ensures remote work agility without the complexity of public clouds. In simple words, Triofox enhances remote work with secure, private file access.
The unauthenticated access vulnerability, identified as CVE-2025-12480, has been discovered in Gladinet Triofox, affecting versions prior to 16.7.10368.56560. These flaws enable remote attackers to exploit the built-in AV feature to achieve code execution on the local host. With ease and a high exploitability rate, unauthenticated threat actors can exploit the vulnerability to gain access to the WebUI to achieve code execution via AV abuse on the host. Flagged by CISA, CVE-2025-12480 enables an adversary to circumvent authentication/ login controls, allowing them to create a new administrator account and gain access to the WebUI using this account. Hence, all organizations that use Gladinet Triofox are strongly encouraged to update their instances to the latest patched version as a matter of urgency.
Technical Overview
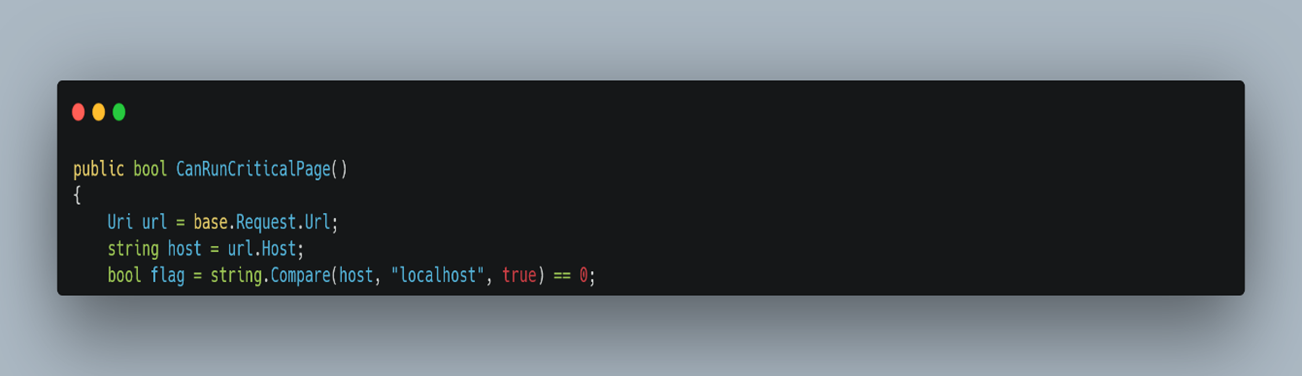
At the heart of the vulnerability lies the core issue: HTTP host headers. A function named CanRunCriticalPage() fails to verify the host origin, allowing the HTTP header “Host” to be set to “localhost”, thereby trusting any user improperly and enabling them to create Admin-level accounts. The application fails to properly authenticate data via the AdminAccount.aspx endpoint, allowing attackers to abuse the AV feature and further PHP backdoors and malicious files, leading to code execution.
Exploitation involves two major components:
- Bypassing Access Controls
The attacker sends a crafted HTTP request with the HTTP header Host is set as localhost, which in general is not considered a legitimate entry when the request originates from an external source. As noted earlier, in vulnerable versions of Triofox instances, the CanRunCriticalPage() function allows suspicious HTTP requests to be processed by trusting them and skipping all further possible access checks, thereby allowing remote actors to authenticate themselves with administrator privileges to the WebUI. An attacker leverages it to create new admin accounts and use them to upload malicious scripts.
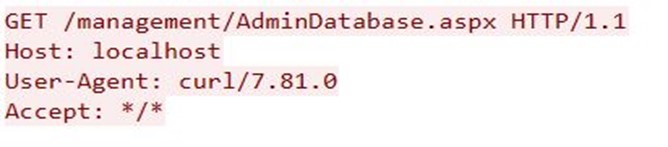
- Anti-Virus Feature Abuse Resulting in Code Execution
By gaining access to WebUI as an administrator via Host Header Injection, adversaries reach the setup page and use the Cluster Admin account to execute malicious scripts through the antivirus configuration path. In Triofox, the built-in AV feature is designed to execute an antivirus executable to scan files on uploaded objects. Further, this feature also allows users to specify an arbitrary path for the selected antivirus. Malicious actors have also exploited this feature, gaining SYSTEM privileges by uploading malicious batch scripts and deploying remote access tools, which can lead to Code Execution.
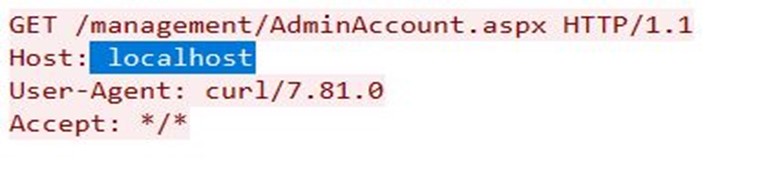
Exploitation
Successful exploitation of CVE-2025-12480 allows remote, unauthenticated attackers to achieve Remote Code Execution (RCE) in vulnerable Triofox file-sharing instances. As shown in Figure 4, an attacker trying to access Triofox Server gains access to its AdminDatabase.aspx by manipulating the Host Header, which is set to localhost. This ease of access with administrator privileges allows remote actors to create new shares or upload malicious content to existing ones. Attackers access Triofox Servers with newly created admin accounts with SYSTEM privileges. Furthermore, abusing the Anti-Virus path to execute malicious scripts by setting up paths as desired helps threat actors to achieve remote code execution in vulnerable Triofox servers. The patched system will reject such requests.
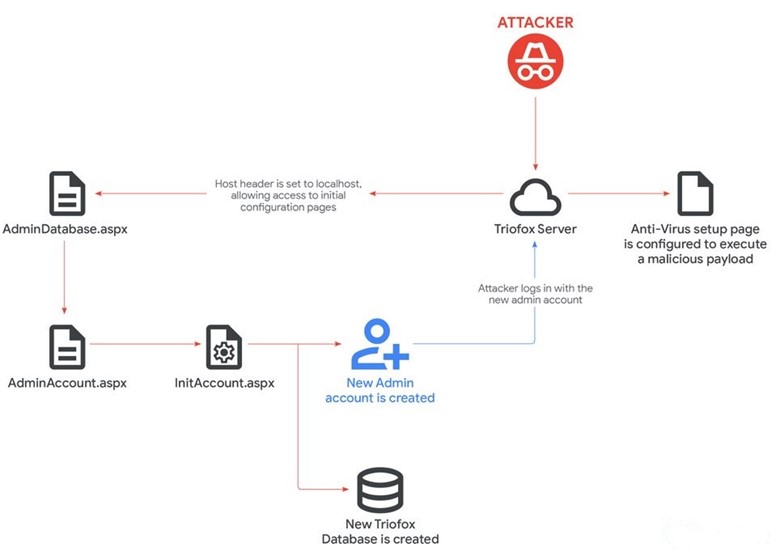
Reference: Mandiant
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS:21638 - Triofox Improper Access Control
Remediation Recommendations
Given that adversary can circumvent authentication/login controls allowing them to create a new administrator account, users are strongly advised to upgrade their instances to the latest patched version as outlined in the official vendor advisory.
Relevant Links
Share This Article

An Article By
An Article By
Dhiren Vaghela
Dhiren Vaghela
Dhiren Vaghela has over a decade of experience in the IPS domain, with a strong focus on defensive security. His expertise lies in identifying, analyzing and mitigating vulnerabilities. Dhiren is well-versed in content-based signature writing, scanner-based alert generation and technical blog writing. By leveraging emerging technologies, he has developed numerous IPS signatures across various protocols. Known for his exceptional signature writing skills and collaborative team spirit, Dhiren is a valuable asset in the field of cybersecurity.
