Apache NiFi Code Injection (CVE-2023-34468)

Overview
The SonicWall Capture Labs threat research team became aware of the threat CVE-2023-34468, assessed its impact and developed mitigation measures for this vulnerability.
CVE-2023-34468 affects Apache NiFi’s DBCPConnectionPool and HikariCPConnectionPool controller services, allowing an attacker with privileges to create or modify controller services to supply an H2 JDBC Database URL that results in remote code execution. Affected versions are 0.0.2 through 1.21.0; the issue is fixed in 1.22.0, which rejects H2 JDBC URLs by default and adds URL validation. The vulnerability is classified as CWE 94 (Code Injection) and has a CVSS v3.1 base score of 8.8. The EPSS exploitation probability is 77.21% (the 99th percentile), indicating a high near-term likelihood of active exploitation. Exploitation requires the ability to create or modify controller services that reference JDBC drivers and is triggered when NiFi interacts with the configured H2 data source. Consult the official Apache NiFi security advisories and the CVE/NVD entries for authoritative guidance.
Technical Overview
In NiFi 1.21.0, the vulnerability identified as CVE-2023-34468 stems from insufficient validation of the Database Connection URL property within the DBCPProperties.java class. Specifically, at line 40 (Figure 01), the DATABASE_URL property is validated only with StandardValidators.NON_EMPTY_VALIDATOR, which enforces nothing more than non-null and non-empty input. This oversight means that any JDBC connection string provided by an attacker is accepted without scrutiny. Critically, it allows the use of H2 database URLs, which support embedded commands via parameters such as INIT=, enabling arbitrary code execution on the NiFi server.
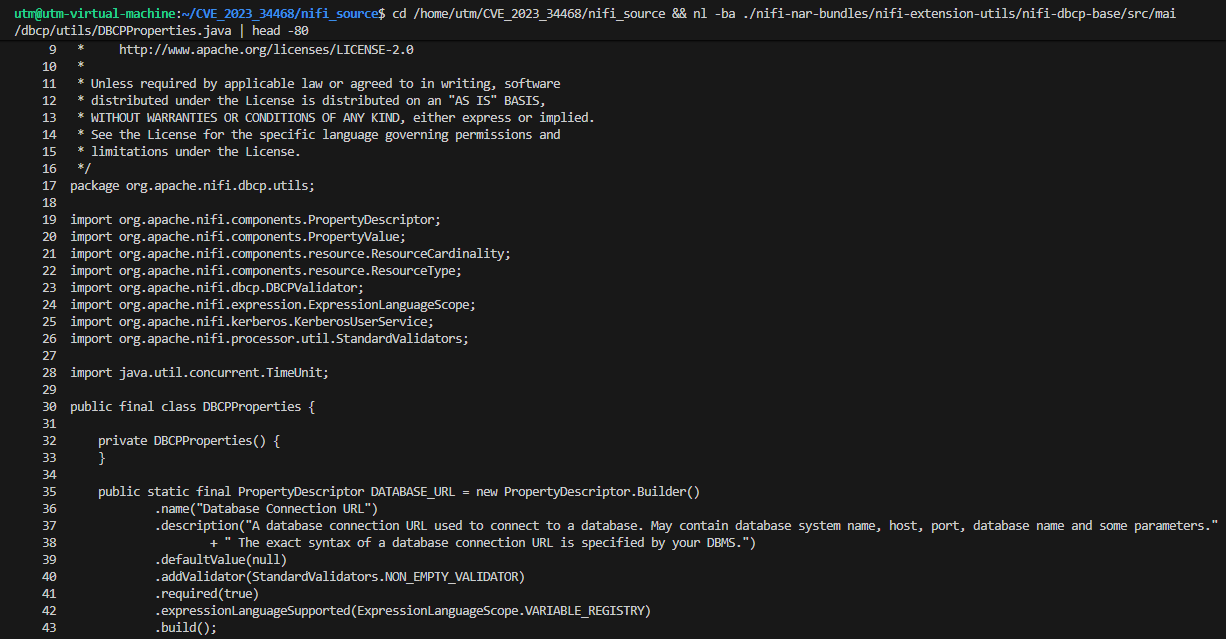
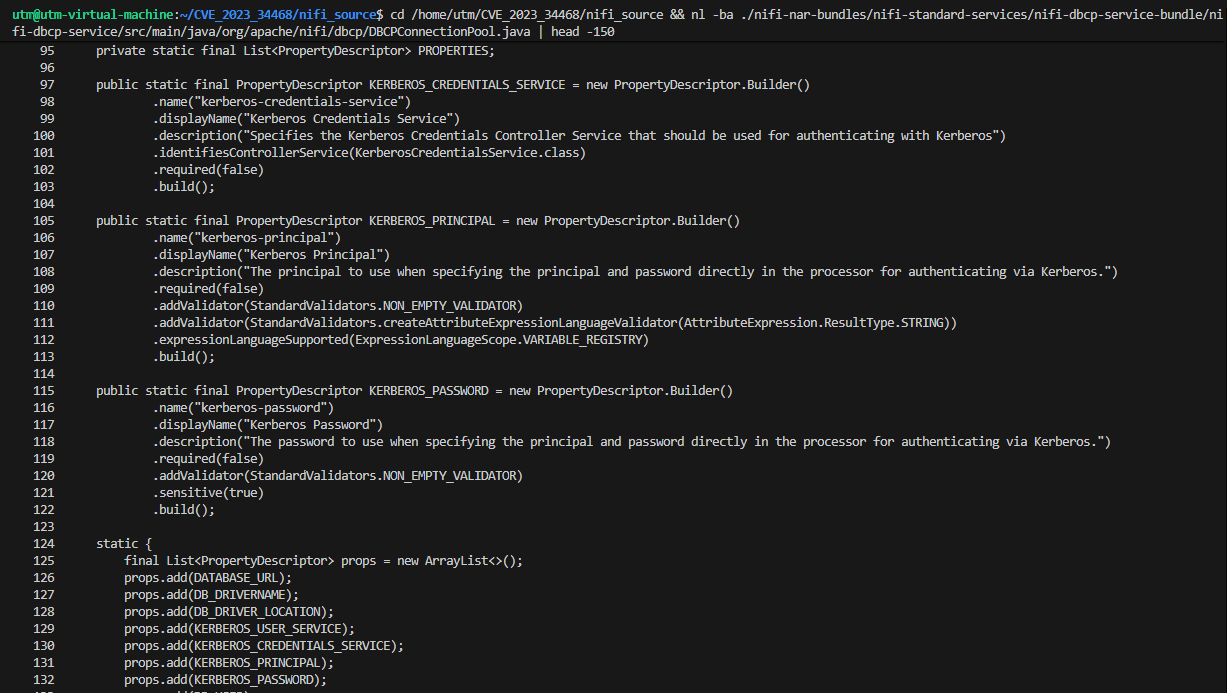
The issue is exacerbated by the way DBCPConnectionPool.java (line 126, Figure 02) directly incorporates this property into the service configuration without additional safeguards. Because the URL is passed verbatim to the underlying JDBC driver, malicious payloads such as jdbc:h2:mem:test;INIT=CREATE ALIAS SHELLEXEC... can execute system commands like whoami. The absence of URL scheme filtering, parameter sanitization, or security checks makes this a direct path for attackers to weaponize controller service configurations.
The patch addresses CVE-2023-34468 by introducing a new ConnectionUrlValidator class (Figure 03) that validates database connection URLs before they can be used in NiFi's DBCP (Database Connection Pooling) services. The validator maintains a list of UNSUPPORTED_SCHEMES that includes dangerous database drivers like "jdbc:h2", "jdbc:derby", and others that could be exploited for remote code execution. When a user attempts to configure a database connection, the validator checks if the URL scheme is in the blacklist and throws a ValidationException if it matches, preventing the connection from being established.
The H2 database driver was particularly dangerous because it allows users to create aliases that can execute arbitrary Java code, effectively giving attackers the ability to run system commands on the NiFi server. By blocking H2 and other risky database schemes at the validation level, the fix ensures that even if an attacker has valid credentials, they cannot abuse the database connection feature to achieve remote code execution.
Triggering the Vulnerability
This vulnerability is triggered when a NiFi DBCPConnectionPool or HikariCPConnectionPool controller service is configured to use the H2 JDBC driver and the Database Connection URL contains H2 features that cause the H2 engine to evaluate code or initialization directives. In affected NiFi releases (<= 1.21.0), an attacker with the ability to create or modify controller services can supply such a URL; when the controller service is enabled and NiFi subsequently opens a connection or executes a query against that data source, the H2 processing of the URL or initialization parameters can lead to code execution within the NiFi process.
- NiFi version is within the vulnerable range (0.0.2 through 1.21.0).
- The H2 JDBC driver is present and referenced by the controller service.
- The actor has privileges to create or modify controller services and to enable them.
- NiFi performs an operation that opens the H2 connection or executes a query (for example, a processor that uses the configured pool).
Exploitation
As demonstrated in the CVE-2023-34468 exploit script, the attacker leverages Apache NiFi's Database Connection Pooling service to inject malicious H2 database connection URLs that bypass input validation. The exploit creates a DBCPConnectionPool controller service with a crafted JDBC URL containing either an inline Java alias definition (CREATE ALIAS SHELLEXEC) or a RUNSCRIPT directive pointing to an attacker-controlled SQL file served over HTTP. Once the controller service is enabled and an ExecuteSQL processor is triggered, the H2 database engine executes the embedded commands during connection initialization before any actual SQL queries run. For proof of concept, the attacker can execute simple commands like creating marker files (touch /tmp/nifi_pwned), while full remote code execution is achieved by injecting reverse shell payloads that spawn a shell with the privileges of the NiFi process. The vulnerability stems from insufficient sanitization of JDBC connection strings, allowing semicolon-delimited parameters containing INIT clauses to pass validation and execute arbitrary code through the H2 database's built-in scripting capabilities.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- IPS: 21428 Apache NiFi DBCPConnectionPool RCE
Remediation Recommendations
The risks posed by CVE-2023-34468 can be mitigated or eliminated by the following actions:
- Upgrade NiFi: promptly move to Apache NiFi version 1.22.0 or later, which disables H2 JDBC URLs by default and adds URL validation.
- Remove or restrict H2 usage: uninstall or disable the H2 driver in NiFi deployments and prohibit H2 JDBC URLs in controller service configurations.
- Harden controller-service access: restrict who can create, modify, or enable controller services by enforcing least privilege, role-based access controls, and strict authentication.
- Utilize IPS signatures: utilize up-to-date IPS signatures to detect and block malicious payloads targeting this vulnerability.
- Monitor and audit: continuously monitor NiFi logs, configuration changes, and network activity for anomalous behavior; employ integrity checks and alerting for unexpected controller-service modifications.
For authoritative guidance and updates, consult the official Apache NiFi security advisories and the CVE/NVD entries.
Relevant Links
CVE Details
Apache Nifi Exploitable Version List
EPSS Score History
National Vulnerability Database (NVD) Entry
CWE-94: Code Injection
CVSS v3.1 Calculator
Share This Article

An Article By
An Article By
Security News
Security News

