Medusa RaaS Group Continues Company Focused Triple Extortion Attacks

The SonicWall Capture Labs threat research team continues to track the developments of Medusa ransomware. Medusa is a Russian-speaking Ransomware-as-a-Service (RaaS) operation that has been active since mid-2021. Medusa generally uses a double extortion strategy that operates in two devastating stages: first, the ransomware encrypts victims’ data, locking files with AES-256 while appending a ".meduza51" extension. Next, the attackers threaten to publicly leak all stolen data unless the ransom is paid. They actively maintain a Tor-based “Medusa Blog” leak site with countdown timers, previews of the stolen information, and options for other cybercriminals to purchase leaked data. However, we have seen reports of triple extortion tactics being used against victims.
Infection Cycle
Upon execution, a command prompt window appears showing the malware’s activity:
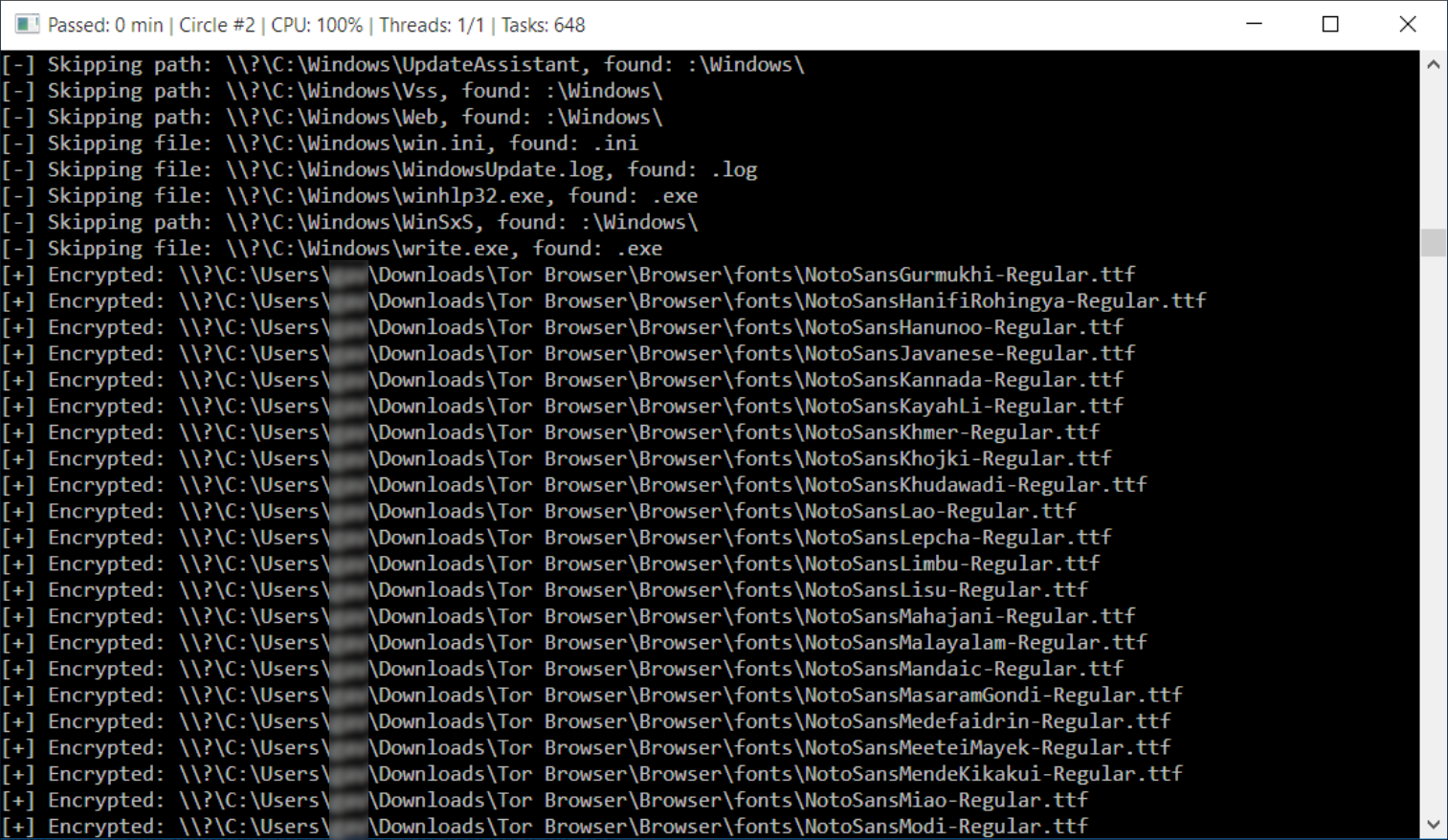
Files on the system are encrypted and given a .meduza51 extension.
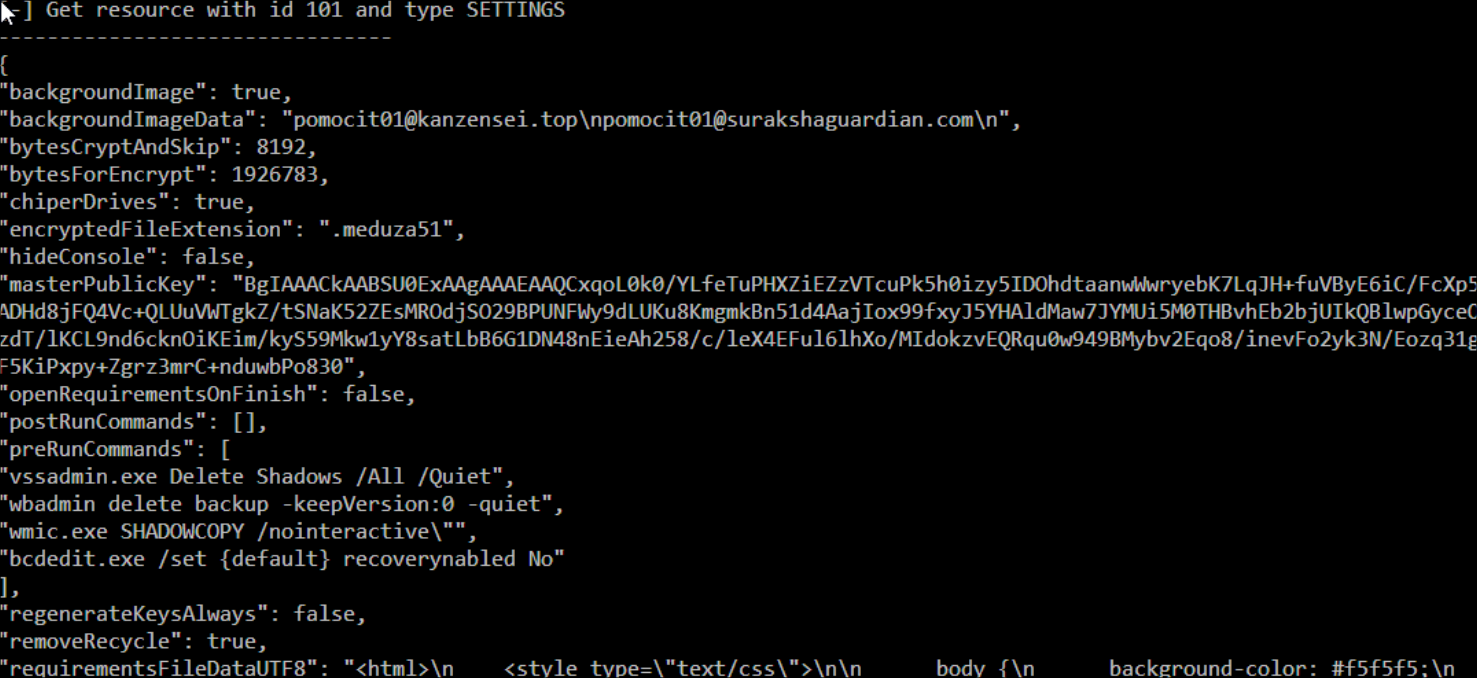
An embedded configuration file in JSON format is printed out at the start of the output:
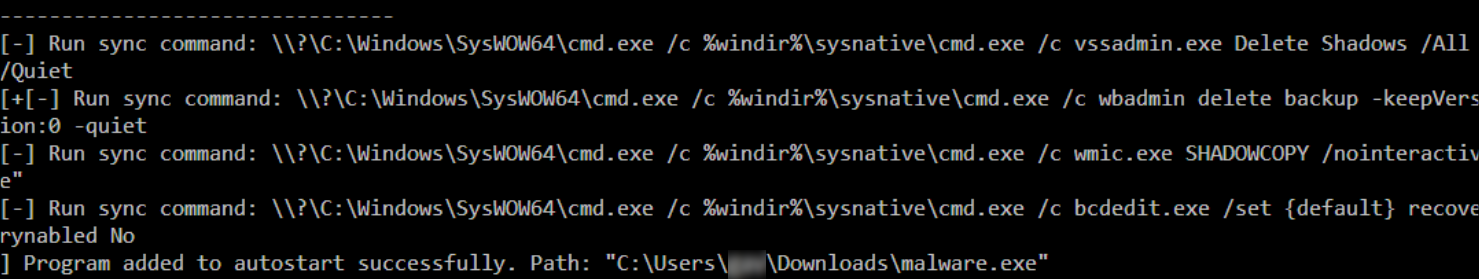
The malware disables system recovery methods:
The following key is added to the registry for persistence after reboot:
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\run
BabyLockerKZ {run location}
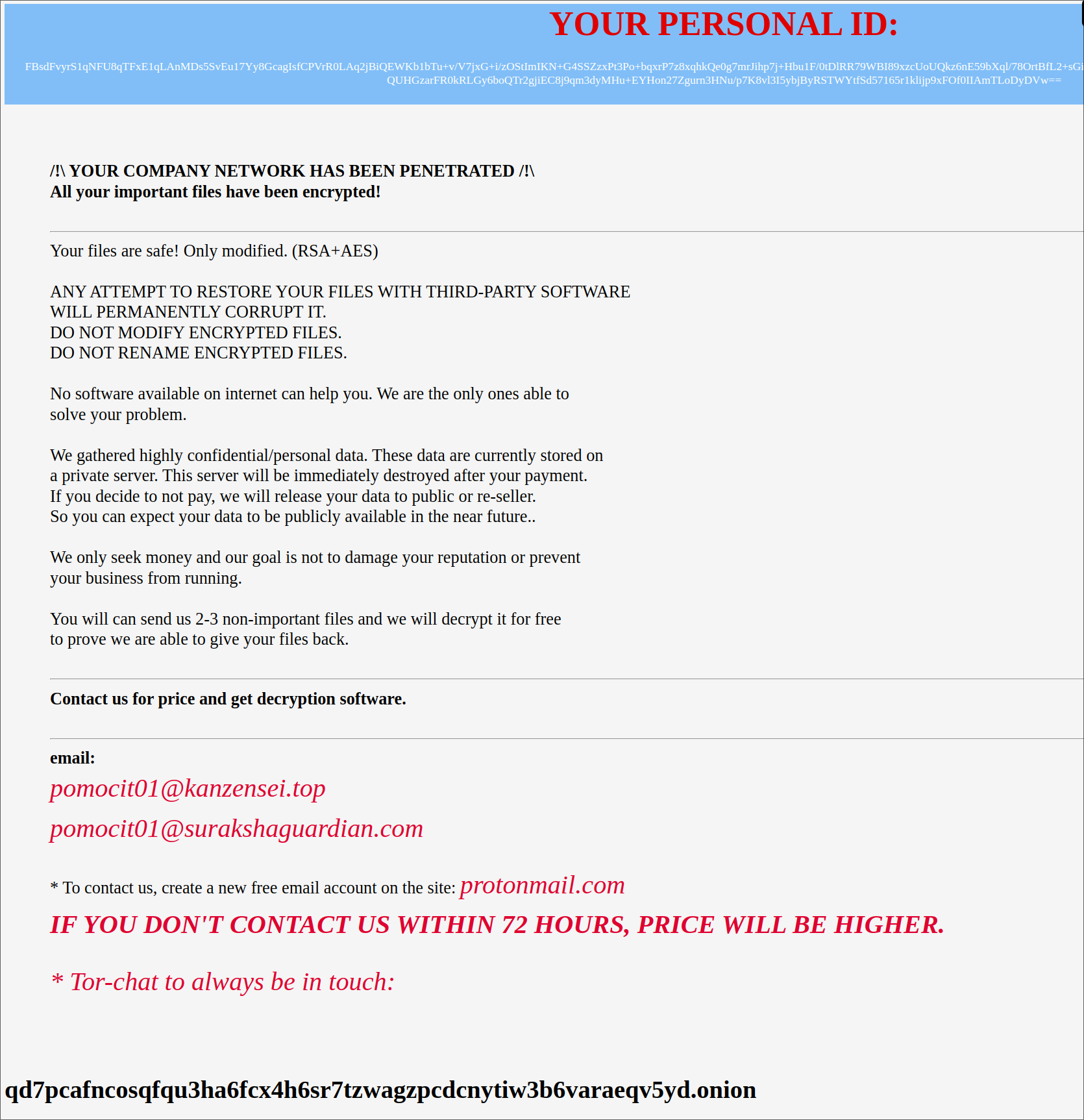
READ_NOTE.html is dropped into all directories containing encrypted files. It contains the following ransom message:
The onion link leads to the following Medusa Locker pages:

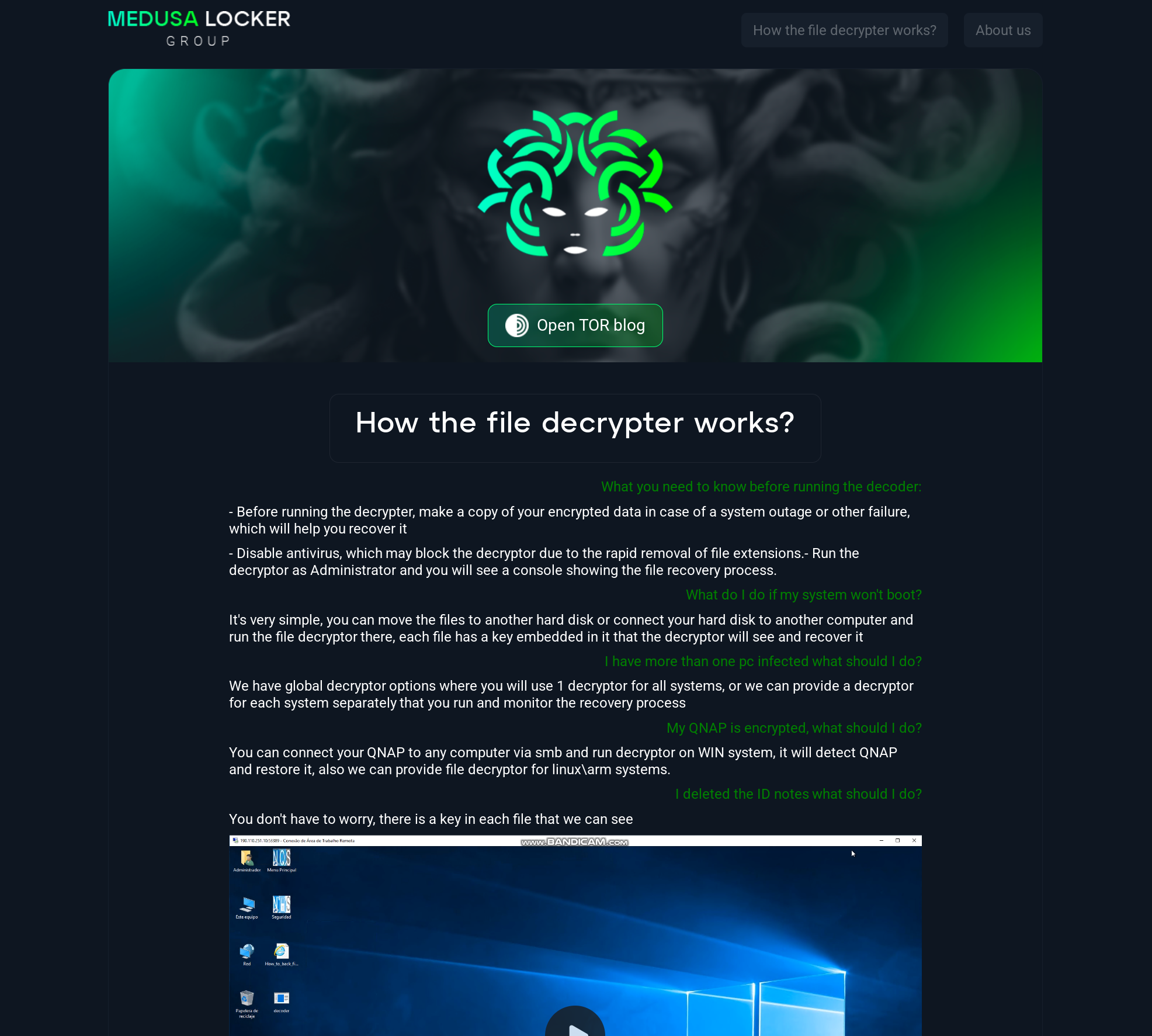
There is a link to a page with a list of small to mid-size companies that have fallen victim to the ransomware. This contains an offer to other criminals to purchase data that has been exfiltrated from these companies by the threat actors:
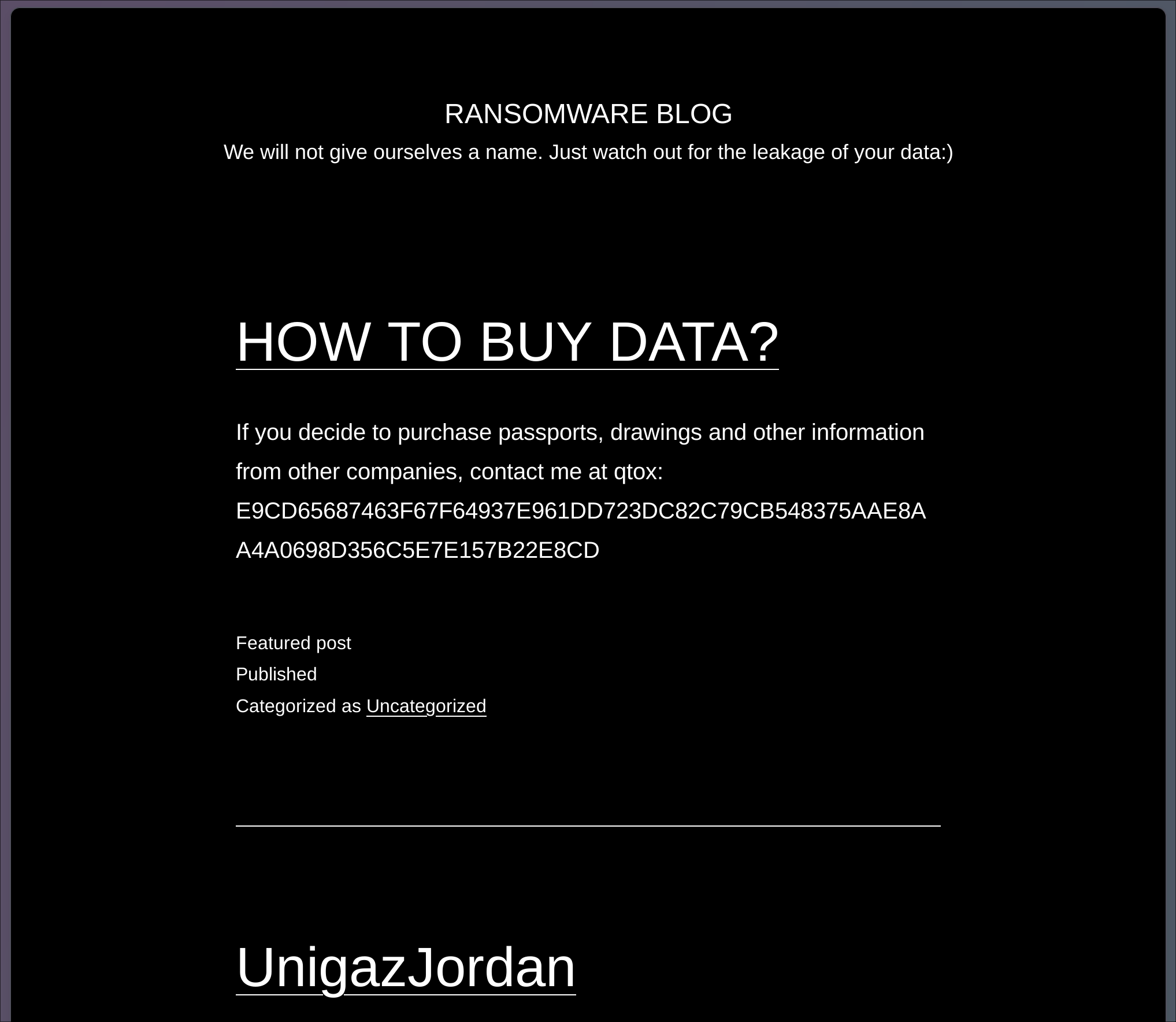
The site contains five pages of summaries that list victim companies. These listings date back to September 2021:
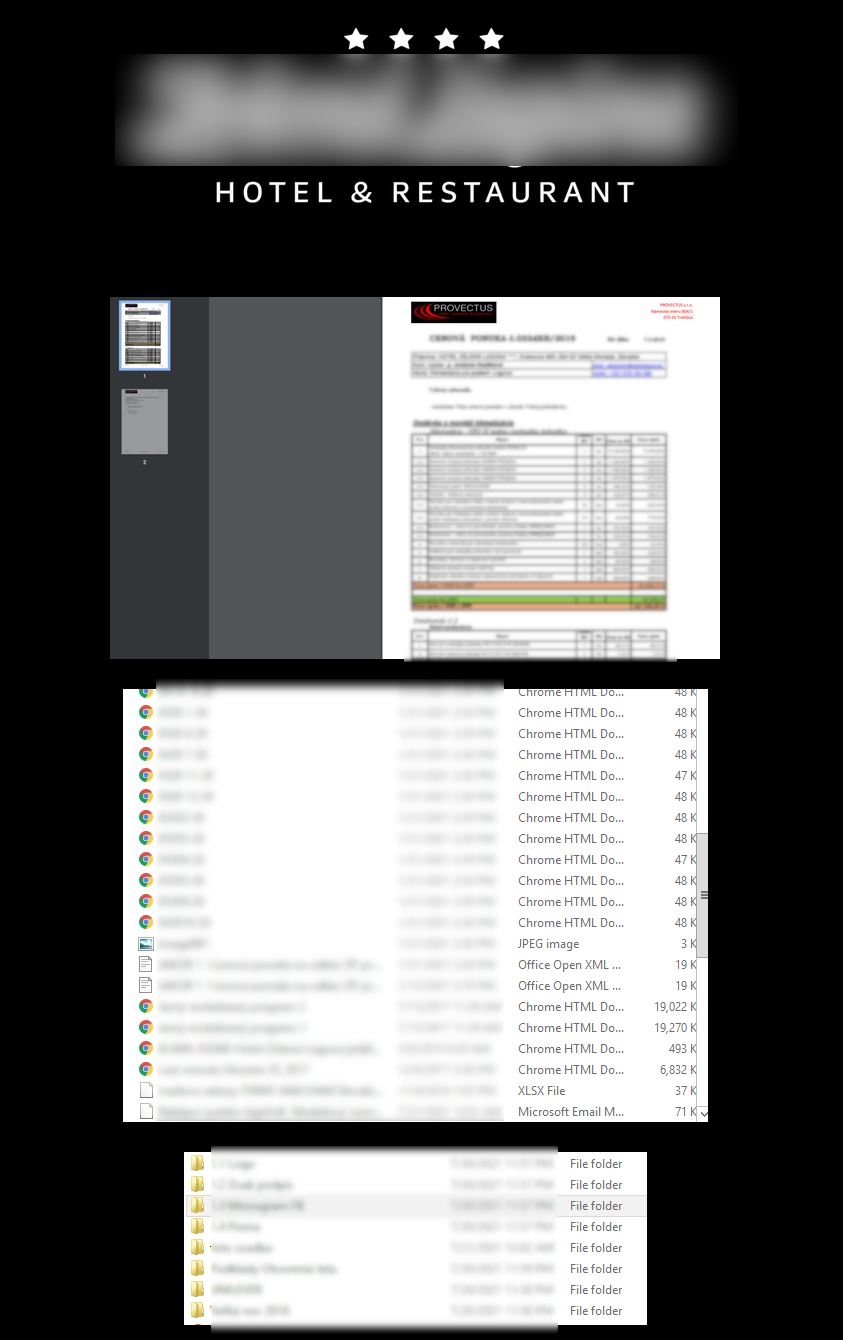
Each blog entry contains either a link to download company data or preview screenshots of the data itself:
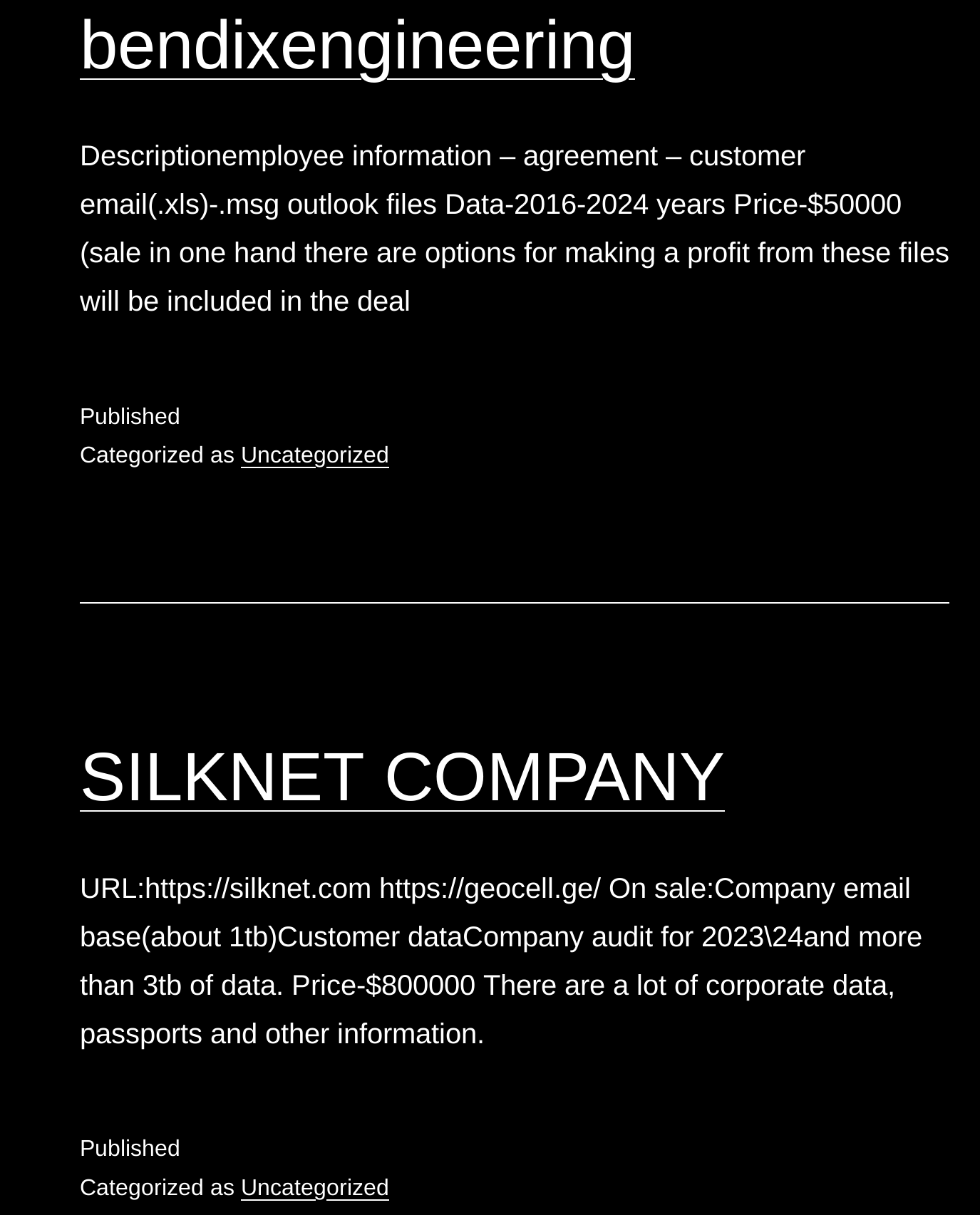
A summary of leaked data and a price are provided:
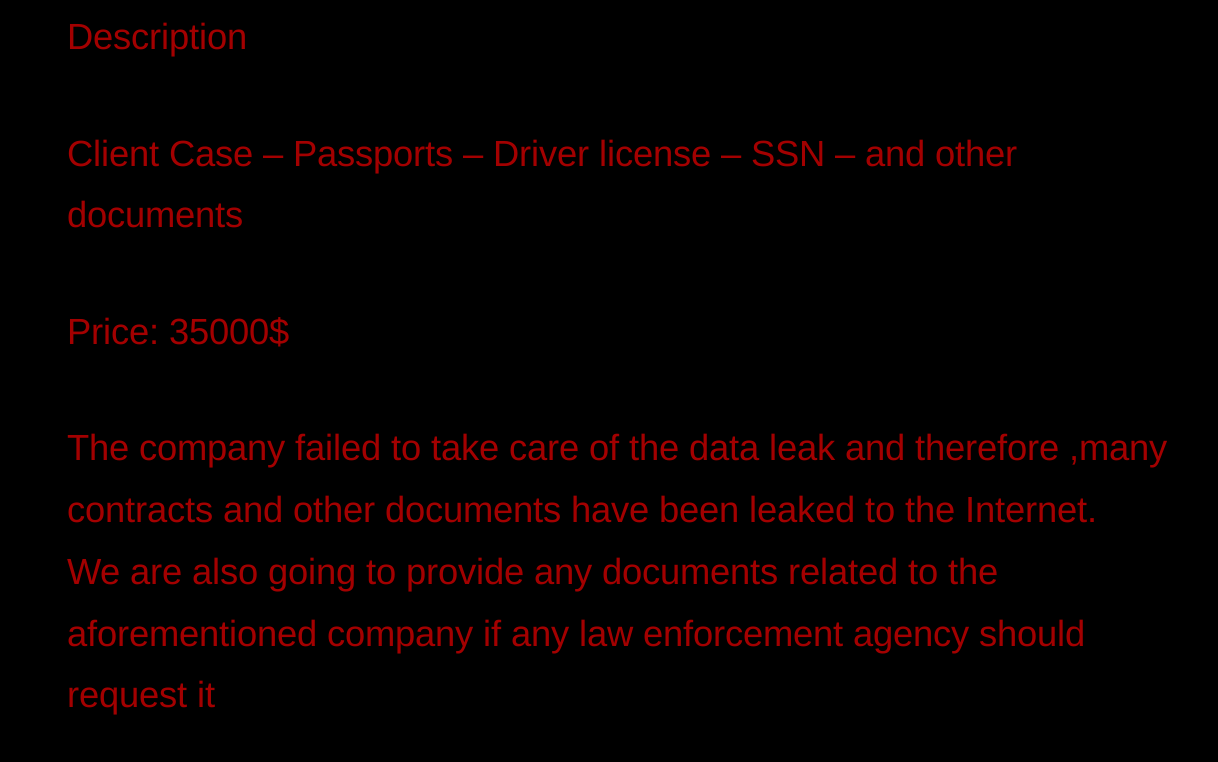
We have also seen reports of triple extortion by the threat actors. Medusa’s triple extortion model builds upon its typical double extortion tactics (decryptor + data leak deadlines) by adding a third, more deceptive payment layer: after victims pay the initial ransom and extension fees (typically $10,000/day to delay data release), a different affiliate may contact the victim claiming the first negotiator pocketed funds and demand an additional payment for the “real” decryptor — effectively tricking the victim into paying three times.
SonicWall Capture Labs provides protection against this threat via the following signature:
GAV: Meduza.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
