-
Products
-
Gen 7 Firewalls
SonicWall's Gen 7 platform-ready firewalls offer performance with stability and superior threat protection — all at an industry-leading TCO.
Read More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
-
Products
- Network Security
- Threat Protection
- Secure Access Service Edge (SASE)
- Managed XDR
- Endpoint Security
- Email Security
- Secure Access
-
Gen 7 Firewalls
SonicWall's Gen 7 platform-ready firewalls offer performance with stability and superior threat protection — all at an industry-leading TCO.
Read More
-
Solutions
- Industries
- Use Cases
-
Widgets
-
Content WidgetsFederal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
-
Image Widgets

-
-
Partners
- SonicWall Partners
- Partner Resources
-
Widgets
-
Content WidgetsPartner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
-
Image Widgets

-
-
Support
- Support
- Resources
- Capture Labs
-
Widgets
-
Content WidgetsSupport Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
-
Image Widgets

-
- Company
- Promotions
- Managed Services
- Contact Us
Security Notice: SonicWall Global VPN Client DLL Search Order Hijacking via Application Installer
 First Published:04/27/2022
First Published:04/27/2022
 Last Updated:04/29/2022
Last Updated:04/29/2022
SonicWall has confirmed that Global VPN Client (GVC) installer 4.10.7.1117 (32-bit and 64-bit) and earlier versions have three specific vulnerabilities in one of the installer components as outlined below:
- Global VPN Client DLL Search Order Hijacking via Application Installer (RunMSI.exe). This includes both the 32-Bit as well as 64-bit installers.
- Global VPN Client Installer being unable to remove RarSFX folder and its content after installation. Therefore, all organizations and/or users who have installed the latest GVC version have the problematic RarSFX folder and its vulnerable component (RunMSI.exe), which could lead to potential exploitation of the first vulnerability above. Only the last three 64-bit versions 4.10.7.1117, 4.10.6.0913 and 4.10.5.1224 are impacted.
- 32-Bit Global VPN Client DLL Highjacking over Microsoft Foundation Class DLLs. While first two vulnerabilities apply to the installer, this one is in the application itself. Only the 32-bit version of GVC is vulnerable.
IMPORTANT
There is no evidence that these vulnerabilities are being exploited in the wild. All three vulnerabilities can only be exploited after the adversary gains control of the machine, has admin privilege or is able to place malicious files on the machine. The vulnerabilities can’t be exploited on a clean system.
SonicWall strongly urges that organizations using the Global VPN Client (GVC) in your network follow the guidance below.
IMPACT
Successful exploitation via a privileged user could result in command execution in the target system. All vulnerable DLL components are located in the RunMSI.exe part of the installer. A vulnerable installer component (RunMSI.exe) is vulnerable to a total of 15 variations of the DLL Search Order Hijacking.
These vulnerabilities require user interaction and running of the vulnerable installer. Command execution in the target system needs to be executed with administrator privileges. The GVC installer doesn't remove problematic RarSFX folder and its content after installation.
IMPORTANT
If a user does not have administrator privileges, there is no way to execute the vulnerable installers. Only when an administrator explicitly executes the installers, or the target system is already compromised by administrator privileges, potential DLL Hijacking could occur.
RESOLUTION
Please follow the resolution steps below based on your organization’s specific use case(s).
| Vulnerability | Affected Version/Scope | User Resolution |
Global VPN Client DLL Search Order Hijacking via Application Installer (RunMSI.exe) | Previous installers |
|
Problematic RarSFX folders left in host machine after installation | Host machine which are running below 64-bit installers:
|
|
DLL Highjacking over Microsoft Foundation Class DLLs | 32bit GVC (X86 GVC) only |
|
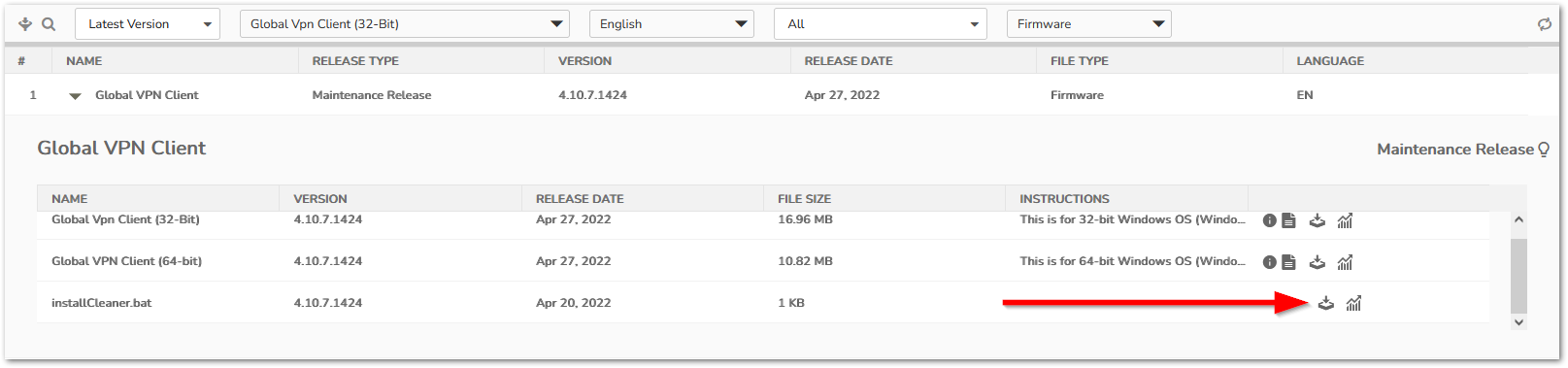
To download the script which will remove the RarSFX folder please perform the following:
- Navigate to https://www.mysonicwall.com/muir/freedownloads
- Select the appropriate GVC bit version in the product drop-down menu.
- Expand the first version 4.10.7.1424 by clicking the arrow.
- The script "installcleaner.bat" is located in the third row.
- Click the download icon to the right of the file to start the download process.
ADDITIONAL RESOURCES
- PSIRT ADVISORY ID: SNWLID-2021-0036
- CVE-2021-20051
- Article: How to Install/Uninstall Global VPN Client (GVC)
- Article: Where to Find Global VPN Client Cleaner Tools
- Video: Walk through of affected GVC versions



