-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
What is the anti-phishing Technique?



Description
Phishing attacks are a form of fraud. They use email with fraudulent content to steal consumers' personal identity data and financial account credentials. According to a recent SonicWall Cyber Threat Report, more than 90% of cyber-attacks begin with a successful phishing campaign that often starts with malware. About 66% of malware installed in a computer comes from a malicious email attachment.
This anti-phishing technique allows administrative management of incoming email. To activate, control, or customize your anti-phishing technique, select the Anti-Phishing option found on ES UI to take action on messages that are phishing attacks or that are likely to contain phishing attacks.
Resolution
Navigate to Manage | Security Services | Anti-Phishing
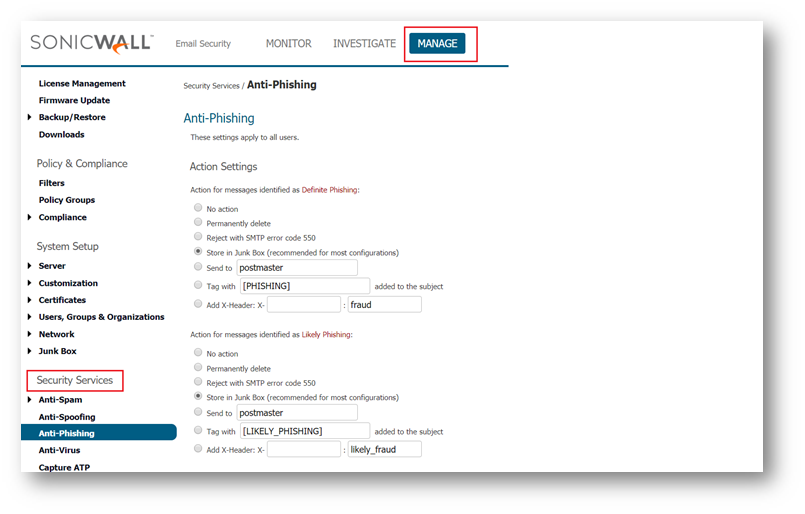
This option will help you take action against messages identified as phishing attacks or are likely to contain phishing attacks. Under the Action Settings option, you may specify different actions for messages identified as Definite Phishing" and those that are Likely Phishing:
- No Action -- Allows suspected emails to be delivered to all users.
- Permanently delete -- Use this option with caution. You cannot retrieve deleted emails.
- Reject with SMTP error code 550 -- Bounce the email back to the sender (return the email message) so that it does not appear in any inbox.
- Store in Junk Box -- Recommended for most configurations. It will store suspected phishing email messages in a "Junk Box" for a previously specified number of days
- Send to ____________ -- Forward suspicious email messages to a specified email address for review.
- Tag with _________ -- Tag suspicious email messages with text that will appear in the beginning of the subject line. The message is delivered to the addressed recipient.
- Add X-Header -- Add an X-Header with the key and value specified to the email message. This option will not take any protective action against the email; however, it will add a header to the email to help with other filtering. The first text field defines the X-Header, and the second text field is the value of the X-Header. For instance, you may add a header type "X-EMSJudgedThisEmail" with a value like "DefinitePhishing." The result will be that the message is delivered to the recipient with a header: "X-EMSJudgedThisEmail: DefinitePhishing."
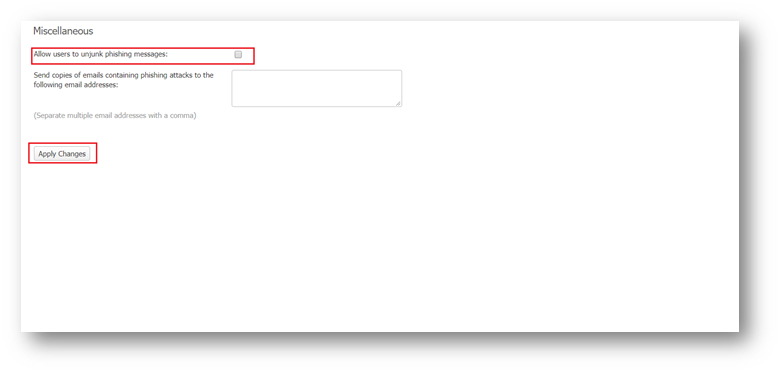
- Allow users to unjunk phishing: Allow users to unjunk messages containing phishing attacks.
- Send copies of emails containing phishing attacks to the following email addresses: This option sends a copy of phishing emails to a number of email addresses. We can enter the email addresses of administrators or others in this text box- separate multiple email addresses with a comma.
Related Articles
- Email Security: How to download the Outlook Junk Tool?
- Configuring SonicWall Email Security to Ensure Maximum effectiveness, High Throughput
- How to exclude the domain from DHA scanning?
Categories
- Email Security > Email Security Appliance
- Email Security > Email Security Software
- Email Security > Hosted Email Security






 YES
YES NO
NO