-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
What are dynamic external objects/groups and how can we configure it?



Description
A Dynamic External Address Group is an Address Group whose members are dynamic. Dynamic External Address Objects are intermediate, internal objects that are dynamically created and placed under a Dynamic External Address Group when a Dynamic External Address Group file is downloaded. The Dynamic External Objects feature eliminates the need for manually modifying an Address Group to add or remove members.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
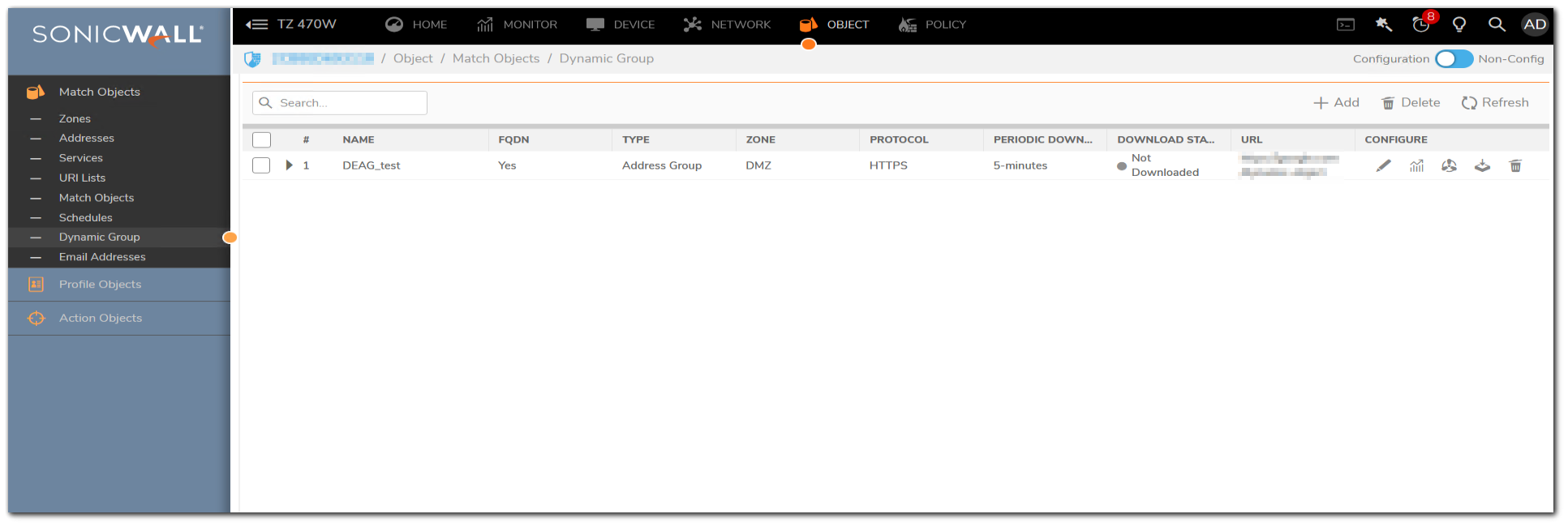
Dynamic External Objects Page:
Multiple Dynamic External Address Groups can be configured, and you can use these DEAGs in access rules or policies. For example, if you want to maintain a group for all partner IP addresses on which certain access rules are enforced, you can create a Dynamic External Address Group / Dynamic External Object.
- Navigate to Manage | Objects | Dynamic External Objects to look at the configured objects.
- Under Comments, a green circle indicates that the DEAG file was successfully downloaded, while a red circle indicates an error.
Dynamic External Address Group File:
The Dynamic External Address Group file (DEAG file) contains a list of IP addresses or Fully Qualified Domain Names (FQDNs) that define the DEAOs which are members of the DEAG. The DEAG file resides externally, on a server for FTP access or on a web page at a specific URL for HTTPS access. The list of IP addresses or FQDNs can be modified at the external location and the associated DEAOs and DEAG in SonicOS are dynamically updated with those changes, if configured to periodically download the file. The DEAG file can contain a text list of either IP addresses or FQDNs formatted as follows:
- A list of IP addresses, one per line. It can include subnets specified in CIDR format.
- A list of FQDNs, one per line. An FQDN is a character string such as www.example.com. It cannot contain any wildcard (*) characters.
- A mixed list of FQDNs and IP addresses/subnets, one per line.
This is only supported for FQDN type DEAGs. A non-FQDN type DEAG will not accept FQDNs in the DEAG file. However, it is not recommended to mix and match IP addresses and FQDNs in the DEAG file, because the IP addresses in this list will also be treated as FQDNs and SonicOS will attempt to resolve them. A better way to mix these input types is to create individual DEAGs of FQDN type and non-FQDN type and then add both DEAGs to a separate address group for use in access rules. For every DEAG, a DEAO with the IP address 0.0.0.0 is automatically created. For example, if there is only one DEAG, the maximum number of IP addresses in the DEAG file is one less than the maximum number of DEAOs allowed, as defined in DEAG and DEAO Maximums.
-
To add a Dynamic External Object:
- Navigate to the MANAGE | Policies | Objects > Dynamic External Objects page.
- Click the Add button. The Add Dynamic External Objects dialog displays.

-
- The Type field is set to Address Group, with no other options.
- Enter a unique, descriptive name for the dynamic external address group in the Name field. “DEAG_” is automatically prepended to the name when saved.
- In the Zone Assignment drop-down list, select the zone for the Dynamic External Address Group.
- If you are using FQDNs for this DEAG, select the FQDN checkbox.
- Select the Enable Periodic Download checkbox for ongoing, periodic downloads of the Dynamic Address Group File.
- If Enable Periodic Download is enabled, select the number of minutes or hours between downloads in the Download interval field. You can select one of:
a) 5 minutes
b) 15 minutes
c) 1 hour
d) 24 hours - Select the type of protocol to use for downloading the DEAG file from the Protocol drop-down list. The choices are FTP or HTTPS. The remaining fields in the dialog are different for FTP and HTTPS.
- If you selected FTP as the protocol, specify the following:
a) Server IP Address – the IP address of the FTP server where the DEAG file resides
b) Login ID – the user name for logging into the FTP server
c) Password – the password for logging into the FTP server
d) Directory Path – the folder in which the DEAG file resides on the FTP server
e) File Name – the name of the DEAG file on the FTP server - If you selected HTTPS as the protocol, specify the following:
URL Name – the URL which has the list of IP addresses or FQDNs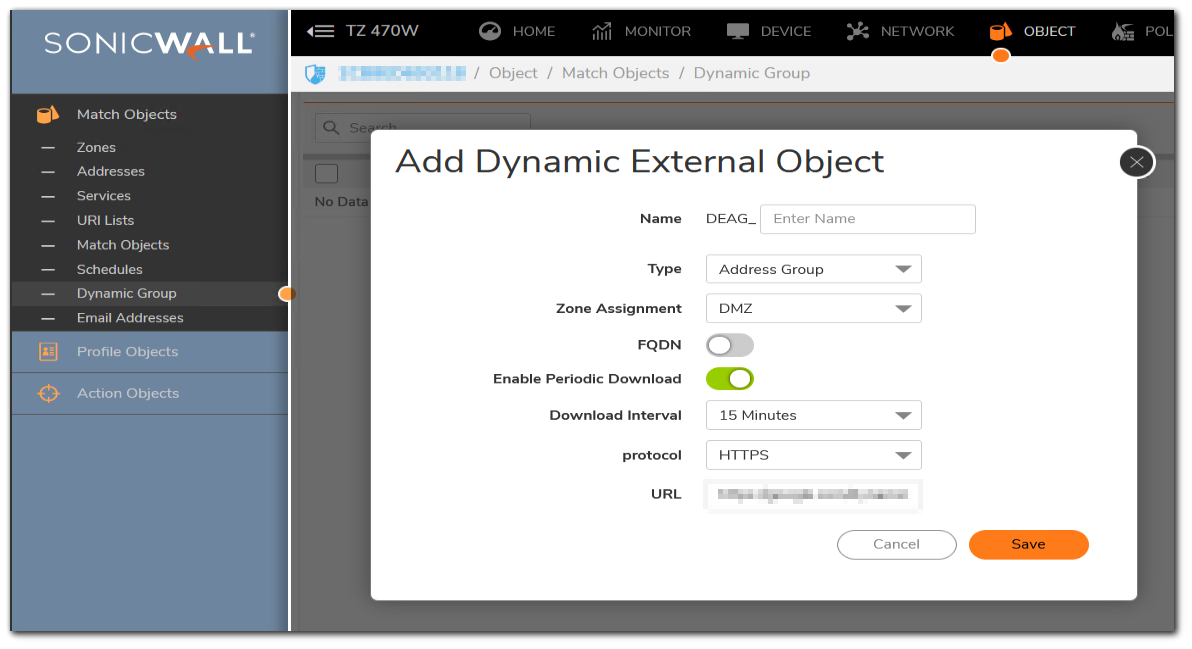
-
- The URL Name should start with https:// and follow with the page name. This page contains the list of IP addresses or FQDNs.
- Click OK.
Based on the configuration, the firewall reads the list of IP addresses or FQDNs from the file or URL. Then SonicOS automatically creates the following:
a) Address group with the name provided in the Add Dynamic External Object dialog. This address group is read-only, meaning that you cannot edit or delete it.
b) Address objects for every valid unique IP address or FQDN in the file. These address objects are also read-only.
The individual address objects are then added to the Dynamic External Address Group / Dynamic External Object. You can use this in access rules and policies.
 NOTE: We cannot change the Name of the DEAG or the Zone Assignment when editing the Dynamic External Object. Also, if a Dynamic External Address Group is in use, such as when an access rule is using it, the deletion attempt will fail.
NOTE: We cannot change the Name of the DEAG or the Zone Assignment when editing the Dynamic External Object. Also, if a Dynamic External Address Group is in use, such as when an access rule is using it, the deletion attempt will fail.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
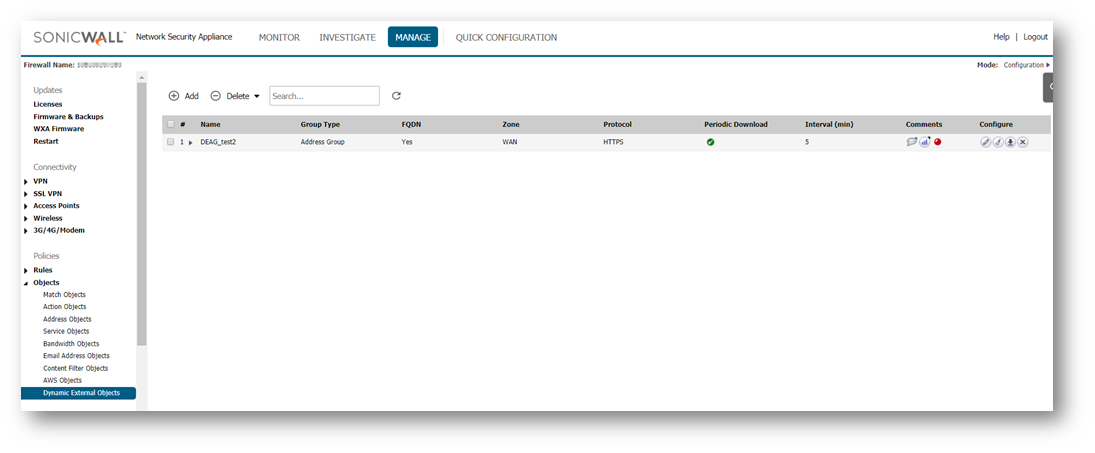
Dynamic External Objects Page:
Multiple Dynamic External Address Groups can be configured, and you can use these DEAGs in access rules or policies. For example, if you want to maintain a group for all partner IP addresses on which certain access rules are enforced, you can create a Dynamic External Address Group / Dynamic External Object.
- Navigate to Manage | Objects | Dynamic External Objects to look at the configured objects.
- Under Comments, a green circle indicates that the DEAG file was successfully downloaded, while a red circle indicates an error.
Dynamic External Address Group File:
The Dynamic External Address Group file (DEAG file) contains a list of IP addresses or Fully Qualified Domain Names (FQDNs) that define the DEAOs which are members of the DEAG. The DEAG file resides externally, on a server for FTP access or on a web page at a specific URL for HTTPS access. The list of IP addresses or FQDNs can be modified at the external location and the associated DEAOs and DEAG in SonicOS are dynamically updated with those changes, if configured to periodically download the file. The DEAG file can contain a text list of either IP addresses or FQDNs formatted as follows:
- A list of IP addresses, one per line. It can include subnets specified in CIDR format.
- A list of FQDNs, one per line. An FQDN is a character string such as www.example.com. It cannot contain any wildcard (*) characters.
- A mixed list of FQDNs and IP addresses/subnets, one per line.
This is only supported for FQDN type DEAGs. A non-FQDN type DEAG will not accept FQDNs in the DEAG file. However, it is not recommended to mix and match IP addresses and FQDNs in the DEAG file, because the IP addresses in this list will also be treated as FQDNs and SonicOS will attempt to resolve them. A better way to mix these input types is to create individual DEAGs of FQDN type and non-FQDN type and then add both DEAGs to a separate address group for use in access rules. For every DEAG, a DEAO with the IP address 0.0.0.0 is automatically created. For example, if there is only one DEAG, the maximum number of IP addresses in the DEAG file is one less than the maximum number of DEAOs allowed, as defined in DEAG and DEAO Maximums.
-
To add a Dynamic External Object:
- Navigate to the MANAGE | Policies | Objects > Dynamic External Objects page.
- Click the Add button. The Add Dynamic External Objects dialog displays.

- The Type field is set to Address Group, with no other options.
- Enter a unique, descriptive name for the dynamic external address group in the Name field. “DEAG_” is automatically prepended to the name when saved.
- In the Zone Assignment drop-down list, select the zone for the Dynamic External Address Group.
- If you are using FQDNs for this DEAG, select the FQDN checkbox.
- Select the Enable Periodic Download checkbox for ongoing, periodic downloads of the Dynamic Address Group File.
- If Enable Periodic Download is enabled, select the number of minutes or hours between downloads in the Download interval field. You can select one of:
a) 5 minutes
b) 15 minutes
c) 1 hour
d) 24 hours - Select the type of protocol to use for downloading the DEAG file from the Protocol drop-down list. The choices are FTP or HTTPS. The remaining fields in the dialog are different for FTP and HTTPS.
- If you selected FTP as the protocol, specify the following:
a) Server IP Address – the IP address of the FTP server where the DEAG file resides
b) Login ID – the user name for logging into the FTP server
c) Password – the password for logging into the FTP server
d) Directory Path – the folder in which the DEAG file resides on the FTP server
e) File Name – the name of the DEAG file on the FTP server - If you selected HTTPS as the protocol, specify the following:
URL Name – the URL which has the list of IP addresses or FQDNs
The URL Name should start with https:// and follow with the page name. This page contains the list of IP addresses or FQDNs. - Click OK.
Based on the configuration, the firewall reads the list of IP addresses or FQDNs from the file or URL. Then SonicOS automatically creates the following:
a) Address group with the name provided in the Add Dynamic External Object dialog. This address group is read-only, meaning that you cannot edit or delete it.
b) Address objects for every valid unique IP address or FQDN in the file. These address objects are also read-only.
The individual address objects are then added to the Dynamic External Address Group / Dynamic External Object. You can use this in access rules and policies.
 NOTE: We cannot change the Name of the DEAG or the Zone Assignment when editing the Dynamic External Object. Also, if a Dynamic External Address Group is in use, such as when an access rule is using it, the deletion attempt will fail.
NOTE: We cannot change the Name of the DEAG or the Zone Assignment when editing the Dynamic External Object. Also, if a Dynamic External Address Group is in use, such as when an access rule is using it, the deletion attempt will fail.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM






 YES
YES NO
NO