-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
WAN Connectivity and Self-diagnosis (MTU)



Description
Troubleshooting: WAN Connectivity and Self-diagnosis (MTU)
1. What kind of issues may caused by MTU
The bandwidth of your WAN connectivity is wide enough for WAN applications (include VPN), but you are encountering following issues.
1. You can open only a part of pages of a website.
2. For some online applications (e.g. games, videos), sometimes the surf speed is evidently getting slower.
3. Applications of some websites are sucked or blocked while there is no forbidden policy (App Rule) configured.
In summary, if there is no packet drop but the Internet speed is sometimes fast and sometimes slow, to a large extent, it may caused by improper MTU value.
2. Root Cause Analysis
2.1 MTU and related Concepts.
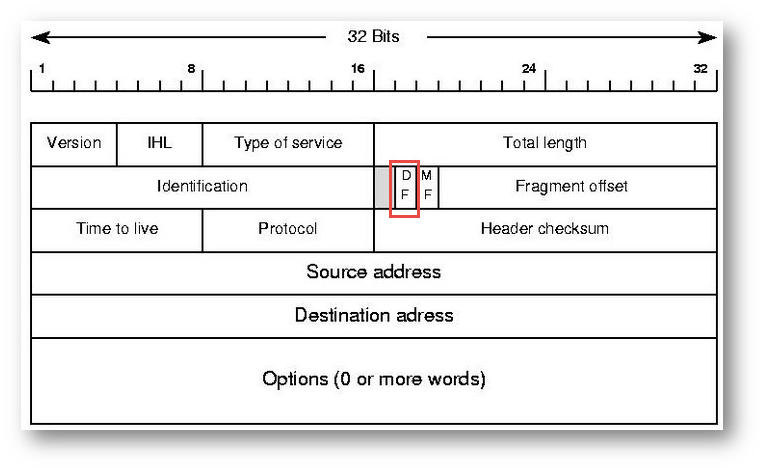
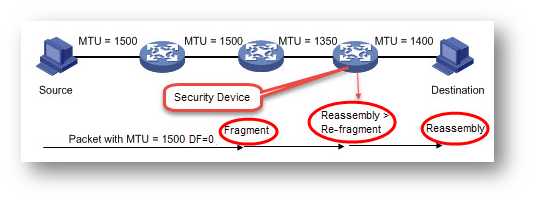
When a packet (IPv4) traverses to a device with an MTU smaller than the packet size, the device will deal with the packet depending on the DF option bit. If the DF bit is set, the device will drop the packet and send back an "ICMP Fragmentation Needed" message with its MTU. If the DF bit is not set, the packet will be fragmented and sent to the destination.
- MTU (Maximum Transmission Unit): The maximum size (in bytes ) of the largest protocol data unit that the layer can pass onwards. MTU parameters usually appear in association with a communications interface.
- PMTU (Path Maximum Transmission Unit): The smallest MTU on the full transmission path (between the source and the destination node).
- PMTU Discovery: The technique in computer networking for determining the MTU size on the network with the goal of avoiding IP fragmentation.
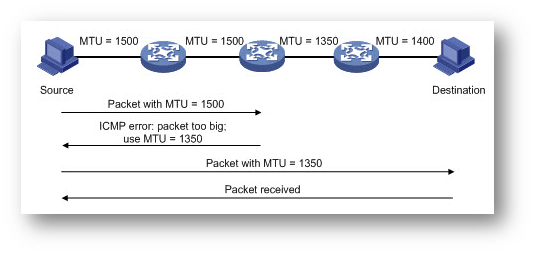
- DF Bit: DF (Don't Fragment) bit in the IP header.
2.2 Why MTU may lead to such problems
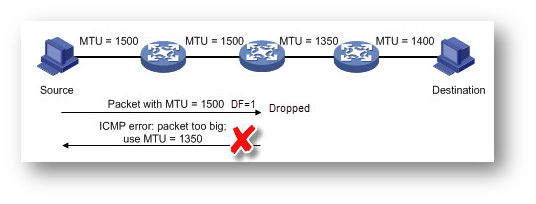
PMTU Black Hole: In today's network, if the source device supports PMTU Discovery, it will set the DF option bit in the IP header of the packet. When a device with a smaller MTU receives the packet, it will send back an ICMP message with the MTU size. The source will adjust the packet size according to the received message then the size of next packets will not exceed the PMTU and transmit without fragment. But during transmission, the packet may encounter PMTU black hole. When the packet with DF option bit set arrives at a device (e.g. router) with smaller MTU, the device drops the packet directly without sending back ICMP message. In such scenario, the source device cannot discover the PMTU and continuously send the packet with the bigger MTU. As a result, the application will be blocked.
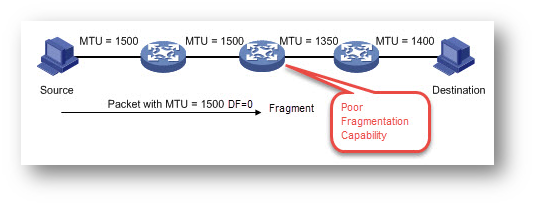
Poor Fragmentation Capability: A packet transmitting from the source to the destination may traverse a large number of devices from various vendors. Some of these devices may have poor fragmentation performance. When the application data need to traverse a device with poor capability for fragment and reassembly, the online application traffic may get slow or even blocked.
Influences from Security Devices: In principle, the fragment and reassembly for an Internet application packet only occurs at the source and destination devices. However, when the fragmented packet traverses a network monitor or security appliance, these devices may require to reassemble the fragmented packet for some particular purposes (e.g. security requirement) . Such behavior may further slower the traffic speed of the application and even cause dis-connectivity.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
How to Troubleshoot:
- Step.1. Check whether you are encountering the above issues listed in section 1.
Internet speed is sometimes fast and sometimes slow or only apart of web pages cannot open.
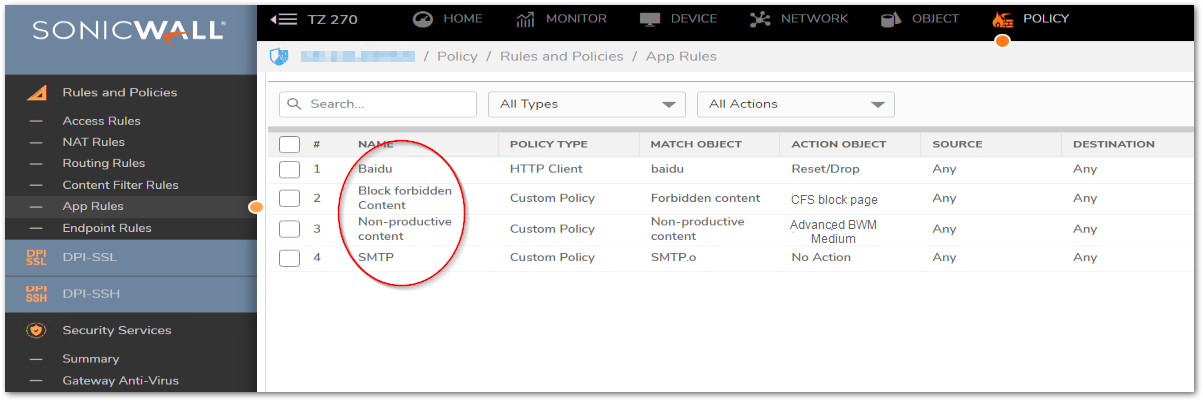
- Step 2. If there is any relevant policy enabled (e.g. CFS Policy or App Rule which may block or do the flow control for the application), login to the firewall | navigate to Policy | Rules and Policies | Content Filter and Firewall | App Rules page to check.
- Step 3. If there is no policy related has been configured, navigate to page Monitor | Tools & monitor | Packet Monitor, you can capture the packet on the WAN interface to monitor whether there is any application related packet has been dropped.
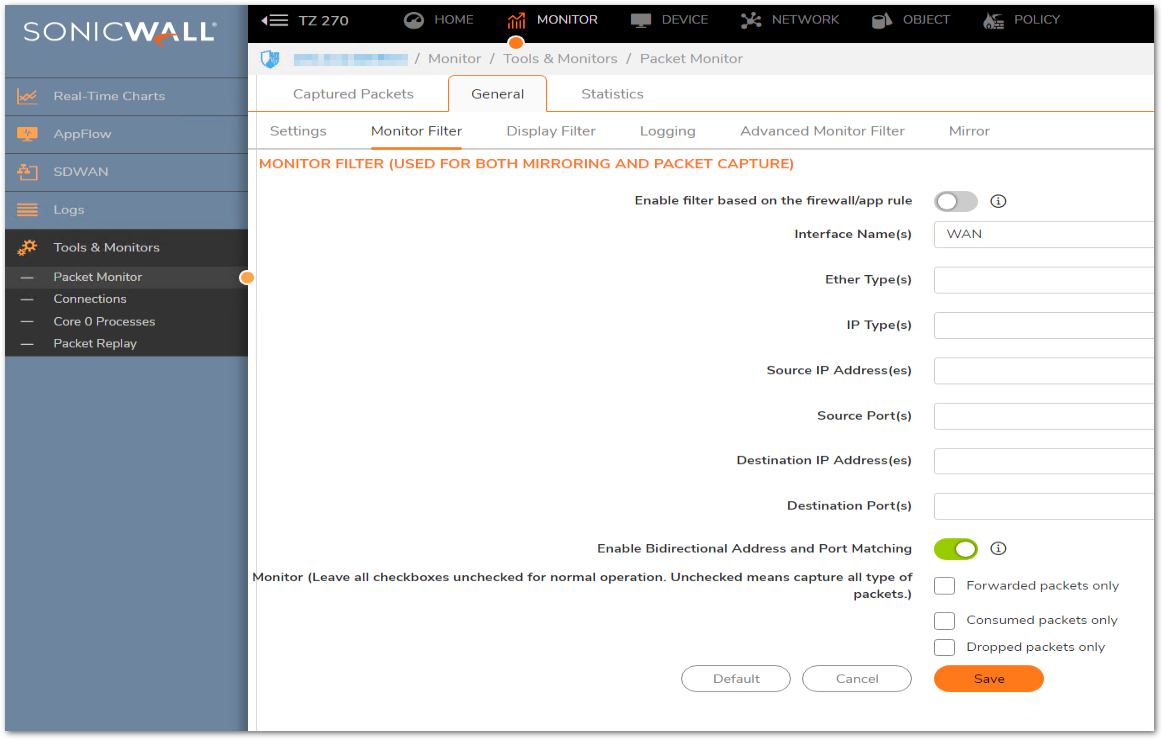
Note: If there is no packet reported dropped, there is a strong possibility that the issue is caused by MTU.
- Step4. Go to page Device | Diagnostics, from version 5.9 and above, SonicWall firewall provides a PMTU Discovery tool. Enter the IP address or host name of the online application and click button Go, system will report the PMTU.
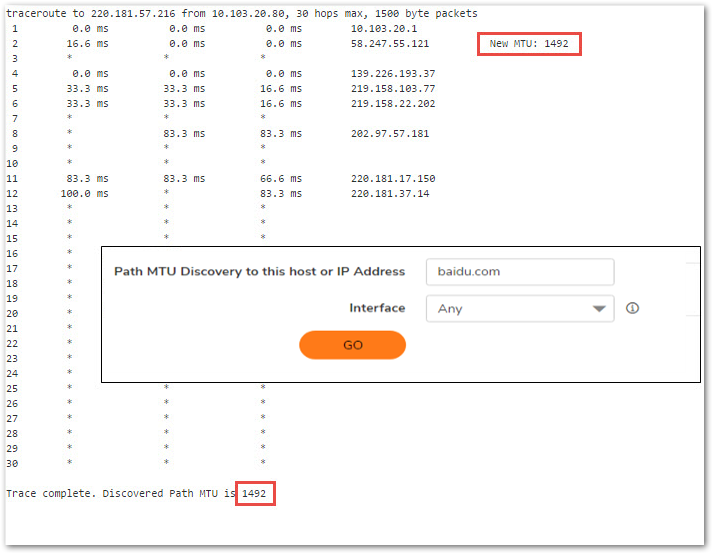
Note: if there is no result, there is maybe a PMTU black hole. Go to Step5.
- Step 5. No result gets from PMTU Discovery Tool, following is the table of default MTUs for various networks. For your reference.
| Network Type | MTU (Bytes) | Reference |
| Max Value | 65535 | RFC 791 |
| Min Value | 68 | RFC 791 |
| FDDI | 4352 | |
| Ethernet | 1500 | |
| IEEE 802.3 | 1492 | |
| PPPoE | 1492 | |
| Cisco GRE | 1476 | |
| X.25 | 576 | |
| PPP | 296 |
- Step 6. Set the appropriate value on the WAN interface of the firewall (Default value is 1500). Go to Network | System | Interfaces page | Click the Edit button of WAN interface | Click tab Advanced | set the value to the Interface MTU field .
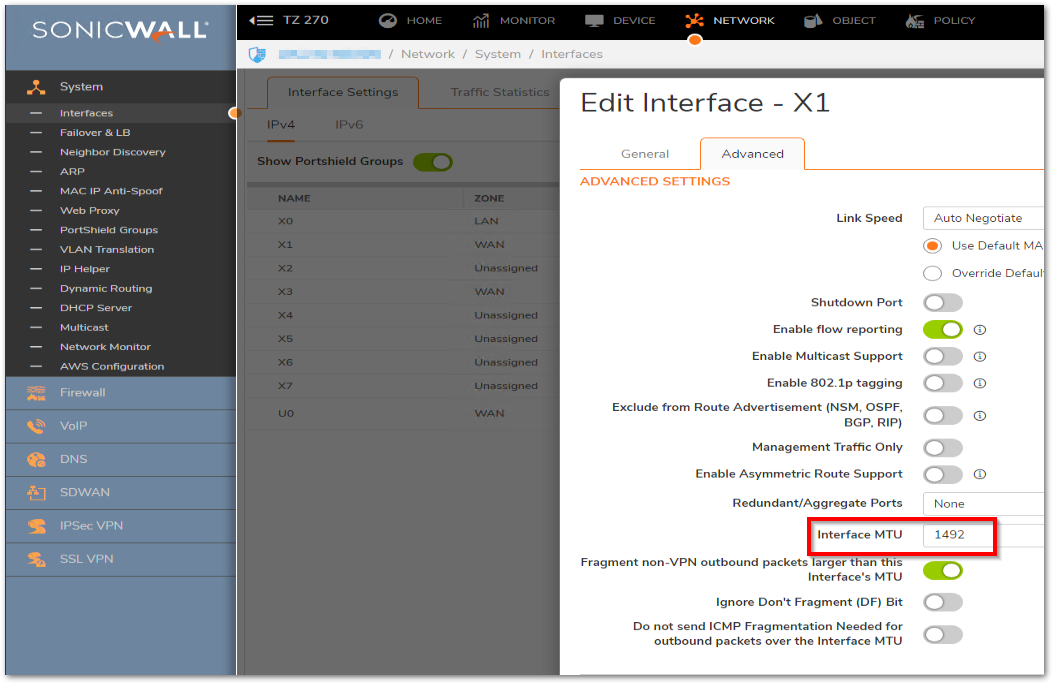
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
How to Troubleshoot:
- Step.1. Check whether you are encountering the above issues listed in section 1.
Internet speed is sometimes fast and sometimes slow or only apart of web pages cannot open.
- Step 2. If there is any relevant policy enabled (e.g. CFS Policy or App Rule which may block or do the flow control for the application), login to the firewall | navigate to Security Services | Content Filter and Firewall | App Rules page to check.

- Step 3. If there is no policy related has been configured, navigate to page System | Packet Monitor, you can capture the packet on the WAN interface to monitor whether there is any application related packet has been dropped.
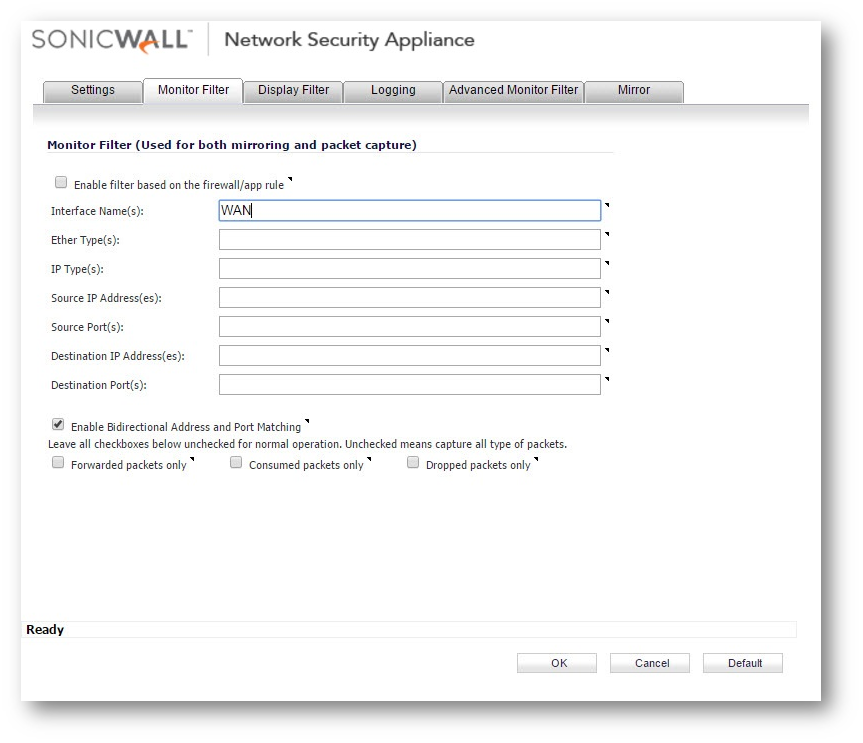
Note: If there is no packet reported dropped, there is a strong possibility that the issue is caused by MTU.
- Step4. Go to page System | Diagnostics, from version 5.9 and above, SonicWall firewall provides a PMTU Discovery tool. Enter the IP address or host name of the online application and click button Go, system will report the PMTU.
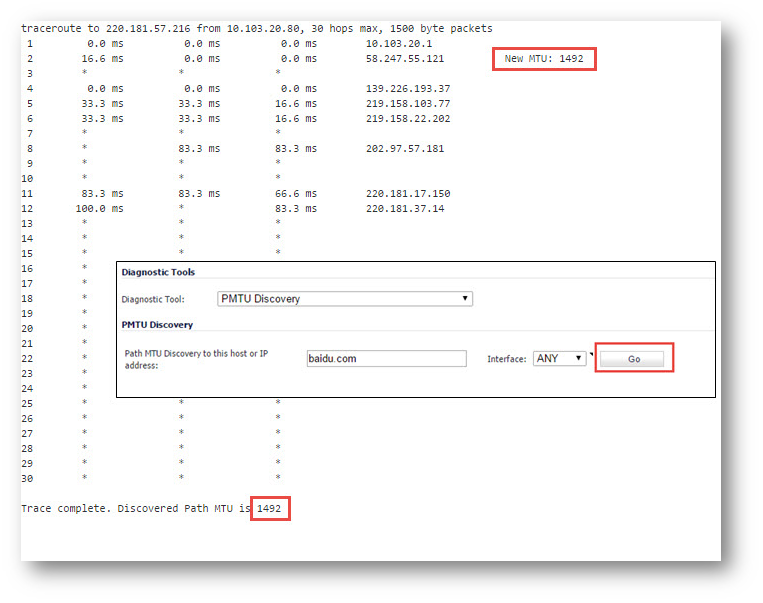
Note: if there is no result, there is maybe a PMTU black hole. Go to Step5.
- Step 5. No result gets from PMTU Discovery Tool, following is the table of default MTUs for various networks. For your reference.
| Network Type | MTU (Bytes) | Reference |
| Max Value | 65535 | RFC 791 |
| Min Value | 68 | RFC 791 |
| FDDI | 4352 | |
| Ethernet | 1500 | |
| IEEE 802.3 | 1492 | |
| PPPoE | 1492 | |
| Cisco GRE | 1476 | |
| X.25 | 576 | |
| PPP | 296 |
- Step 6. Set the appropriate value on the WAN interface of the firewall (Default value is 1500). Go to Network | Interface page | Click the Edit button of WAN interface | Click tab Advanced | set the value to the Interface MTU field .
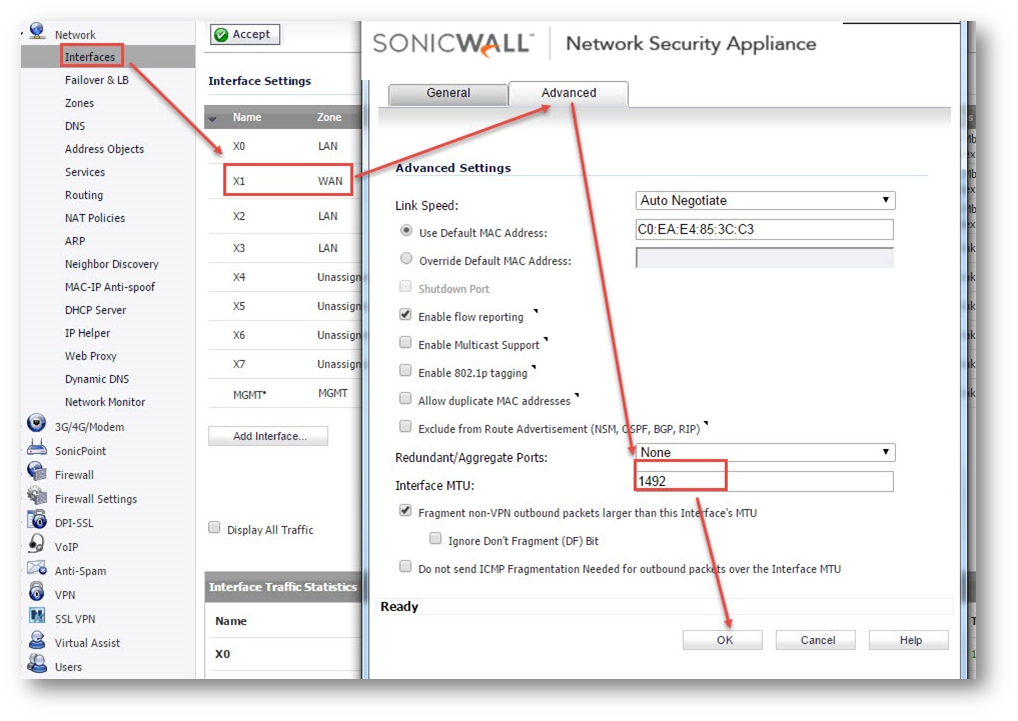
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series






 YES
YES NO
NO