-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
VIDEO: How to block web browsers like (IE, Google Chrome, Firefox, etc) using Application Firewall



Description
VIDEO: How to block web browsers like (IE, Google Chrome, Firefox, etc) using Application Firewall feature
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Video Tutorial: Click here for the video tutorial of this topic.
Feature/Application:
This article describes how the Application Firewall feature in the Sonicwall UTM appliance is used to block Browsers. Application Firewall blocks browser like Internet Explorer (MSIE), Firefox, Netscape. An application object that allows enumeration of the various textual strings that can be used to match the name various browsers use to identify themselves. This information is contained in the User-Agent header of an HTTP GET request.
 NOTE: To block HTTPS traffic you need to use the DPI-SSL feature
NOTE: To block HTTPS traffic you need to use the DPI-SSL feature
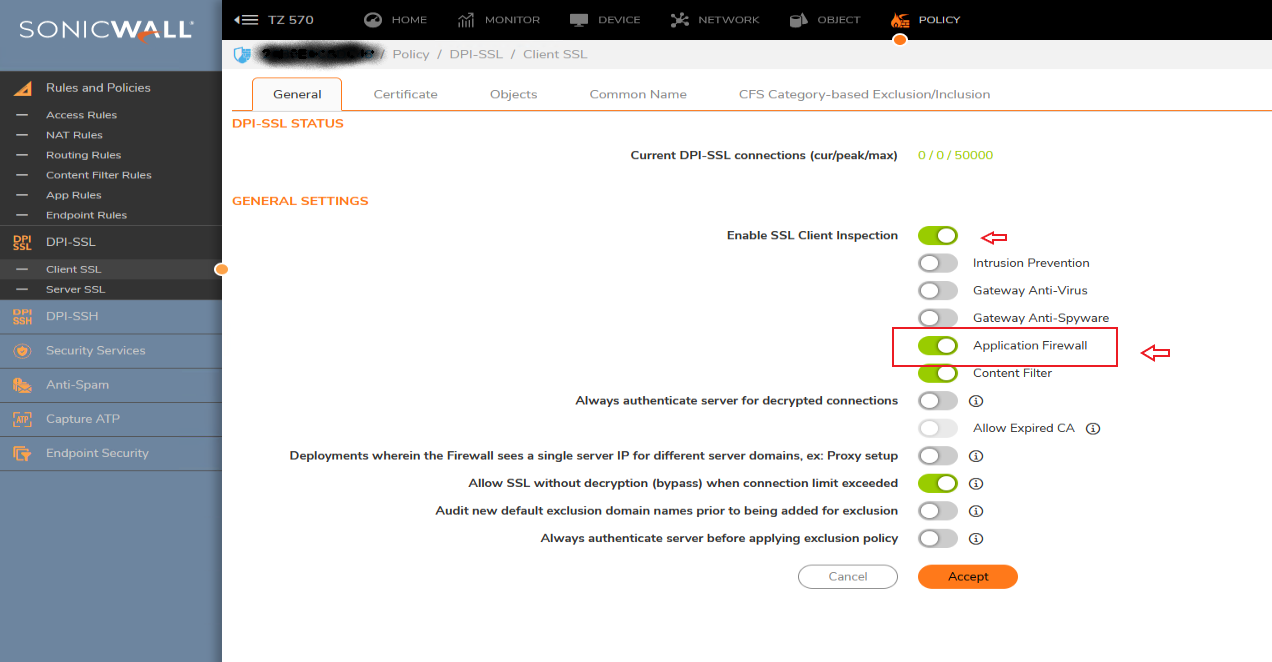
Procedure:
STEP 1:
- Login to the Sonicwall Management interface.
- Navigate to the Application Firewall > Enable "Application Firewall" > Go to Application Objects page.
- Click on the Add New Object button to create an Application Object with the following properties:
Object Name: Browse
Application Object Type: Web Browser
Browser: Select the browsers to be allowed / blocked and click “Add”
Enable Negative Matching: Enabling Negative Matching for an application object and then using such object in a policy would create a policy that will perform a specified action based on absence of the content specified in the application object. In our case, we allow MSIE, Firefox,
Netscape and block Google Chrome. so, Negative Matching is "Enabled"
STEP 2:
- Navigate to the Application Firewall > Policies page.
- Check the Enable Application Firewall box.
- Click on the Add New Policy button
- In the Application Firewall Policy Settings window enter the following:
Policy Name: Block Chrome
Policy Type: HTTP Client
Address Source: Any
Address Destination: Any
Service Source: Any
Service Destination: HTTP
Exclusion Address: None
Application Object: Browser (select the Application Object created earlier)
Action: Reset/Drop
Users/Groups Included: All
Users/Groups Excluded: None
Schedule: Always on
Enable Logging: Checked
Log individual object content: Unchecked
Log Redundancy Filter: Use Global Settings checked
Connection Side: Client Side
Direction (Basic): Both
Click on OK to save.
How to Test:
Open the chrome browser and try accessing HTTP/HTTPS site. A “This webpage is not available / the page cannot be displayed” error will be displayed on the browser.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Video Tutorial: Click here for the video tutorial of this topic.
Feature/Application:
This article describes how the Application Firewall feature in the Sonicwall UTM appliance is used to block Browsers. Application Firewall blocks browser like Internet Explorer (MSIE), Firefox, Netscape. An application object that allows enumeration of the various textual strings that can be used to match the name various browsers use to identify themselves. This information is contained in the User-Agent header of an HTTP GET request.
 NOTE: To block HTTPS traffic you need to use the DPI-SSL feature (available on firmware: SonicOS 5.6 and above)
NOTE: To block HTTPS traffic you need to use the DPI-SSL feature (available on firmware: SonicOS 5.6 and above)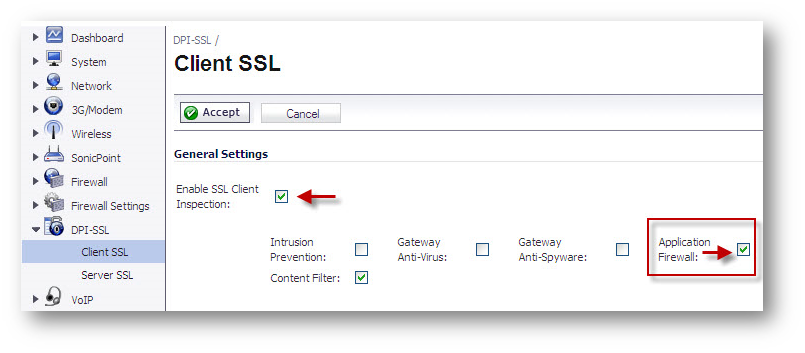
Procedure:
STEP 1:
1. Login to the Sonicwall Management interface.
2. Navigate to the Application Firewall > Enable "Application Firewall" > Go to Application Objects page.
3. Click on the Add New Object button to create an Application Object with the following properties:
Object Name: Browse
Application Object Type: Web Browser
Browser: Select the browsers to be allowed / blocked and click “Add”
Enable Negative Matching: Enabling Negative Matching for an application object and then using such object in a policy would create a policy that will perform a specified action based on absence of the content specified in the application object. In our case, we allow MSIE, Firefox,
Netscape and block Google Chrome. so, Negative Matching is "Enabled"
STEP 2:
1. Navigate to the Application Firewall > Policies page.
2. Check the Enable Application Firewall box.
3. Click on the Add New Policy button
4. In the Application Firewall Policy Settings window enter the following:
Policy Name: Block Chrome
Policy Type: HTTP Client
Address Source: Any
Address Destination: Any
Service Source: Any
Service Destination: HTTP
Exclusion Address: None
Application Object: Browser (select the Application Object created earlier)
Action: Reset/Drop
Users/Groups Included: All
Users/Groups Excluded: None
Schedule: Always on
Enable Logging: Checked
Log individual object content: Unchecked
Log Redundancy Filter: Use Global Settings checked
Connection Side: Client Side
Direction (Basic): Both
Click on OK to save.

How to Test:
Open the chrome browser and try accessing HTTP/HTTPS site. A “This webpage is not available / the page cannot be displayed” error will be displayed on the browser.

Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > TZ Series
- Firewalls > SonicWall SuperMassive E10000 Series
- Firewalls > SonicWall SuperMassive 9000 Series
- Firewalls > SonicWall NSA Series






 YES
YES NO
NO