-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Using firewall access rules to block Incoming and outgoing traffic



Description
By default, the SonicWall security appliance's Stateful packet inspection allows all communication from the LAN to the Internet, and blocks all traffic to the LAN from the Internet.
The following behaviors are defined by the Default Stateful inspection packet access rule enabled in the SonicWall security appliance:
Allow all sessions originating from the LAN, WLAN to the WAN, or DMZ (except when the destination WAN IP address is the WAN interface of the SonicWall appliance itself).
Allow all sessions originating from the DMZ to the WAN.
Deny all sessions originating from the WAN to the DMZ.
Deny all sessions originating from the WAN and DMZ to the LAN or WLAN.
Additional network access rules can be defined to extend or override the default access rules. For example, access rules can be created that allow access from the LAN zone to the WAN Primary IP address, or block certain types of traffic such as IRC from the LAN to the WAN, or allow certain types of traffic, such as Lotus Notes database synchronization, from specific hosts on the Internet to specific hosts on the LAN, or restrict use of certain protocols such as Telnet to authorized users on the LAN.
Custom access rules evaluate network traffic source IP addresses, destination IP addresses, IP protocol types, and compare the information to access rules created on the SonicWall security appliance. Network access rules take precedence, and can override the SonicWall security appliance's Stateful packet inspection. For example, an access rule that blocks IRC traffic takes precedence over the SonicWall security appliance default setting of allowing this type of traffic.
This article lists the following configuration examples of access rules to be created for blocking incoming and outgoing traffic:
- Blocking hosts in the LAN all access to the WAN
- Blocking hosts in the LAN access to specific services on the WAN
- Blocking IP addresses on the WAN access to the LAN
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Blocking hosts in the LAN all access to the WAN
- Login to the SonicWall management Interface.
- Click Object on the top bar, navigate to the Match objects | Addresses | Address objects page.
- Create Address Object/s or Address Groups of hosts to be blocked.
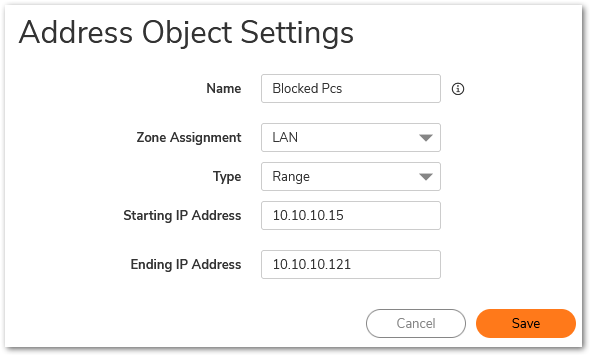
- Navigate to the Policy | Rules and Policies | Access rules page.
- Select the LAN to WAN button to enter the Access Rules (LAN > WAN) page.
- Click on the marked arrow to open the Add Rule window.
- Select Deny as the Action.
- Select Any as the Service
- Select Source as the address objects created earlier.
- Select Any as the Destination
- Click Add and Close.
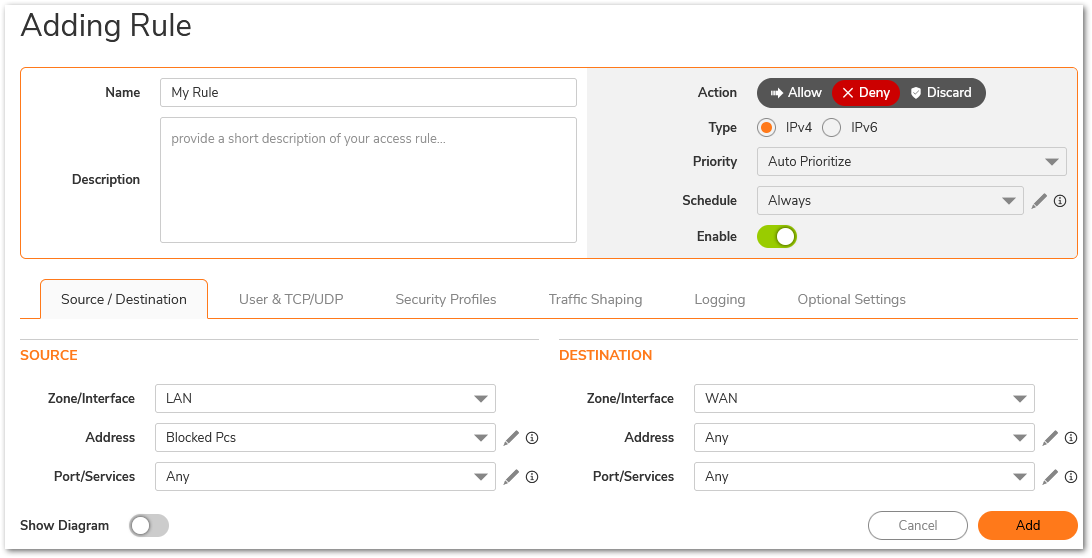
NOTE:Verify that the rule just created has a higher priority than the default rule for LAN to WAN.
Blocking hosts in the LAN access to specific services on the WAN
- This section provides a configuration example for an access rule blocking LAN access to NNTP servers on the Internet. Perform the following steps to configure an access rule blocking LAN access to NNTP servers.
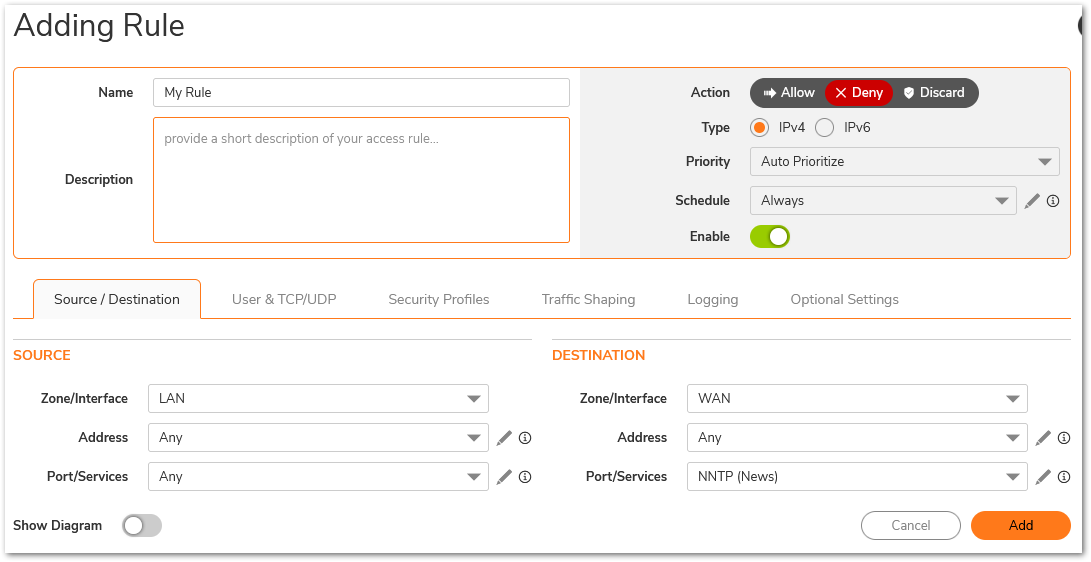
Blocking IP addresses on the WAN access to the LAN
By default all traffic from the WAN are denied access to the LAN, DMZ or any other zone. However, it may be required to allow some specific ports access to a server on the LAN or DMZ by creating the required Access Rules and NAT Policies. In most cases, the source would be set to Any. In such cases, where an access rule already exists to allow traffic from anywhere on the Internet to the LAN or DMZ, it may be required to deny traffic from IP addresses known (or suspected) to be coming from a non-secure source. This is an example of a deny rule.
This section provides a configuration example of an access rule blocking some IP addresses on the Internet access to the LAN zone of the SonicWall. Perform the following steps to configure an access rule blocking access to the LAN zone from the Internet.
- Navigate to Match objects | Addresses | Address objects page.
- Create Address Object/s or Address Groups of hosts to be blocked.
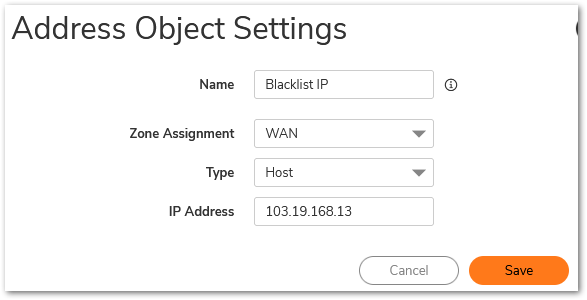
NOTE: Refer Understanding Address Objects In SonicOS for more information on creating Address Objects. Set the zone as WAN when creating Address Objects of IP addresses on the Internet. - Navigate to Policy | Rules and Policies | Access Rules page.
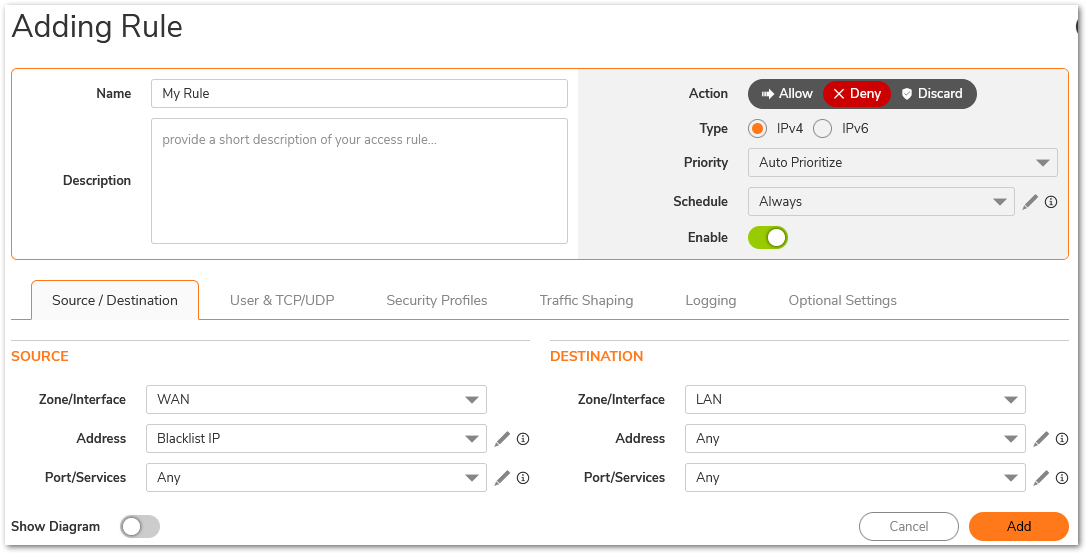
- Select the WAN to LAN button to enter the Access Rules (WAN | LAN) page.
- Click marked arrow to open the Add Rule window.
- Select Deny as the Action.
- Select Any as the Service
- Select Source as the address object or group created earlier.
- Select Any as the Destination
- Click Add and Close.
NOTE: Verify that the rule just created has a higher priority than the default rule for WAN to LAN.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Blocking hosts in the LAN all access to the WAN
- Login to the SonicWall management Interface.
- Click MANAGE on the top bar, navigate to the Policies | Objects | Address Objects page.
- Create Address Object/s or Address Groups of hosts to be blocked.
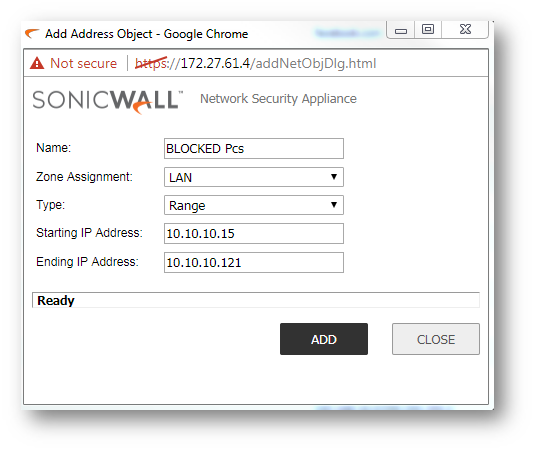
- Navigate to the Policies | Access Rules page.
- Select the LAN to WAN button to enter the Access Rules (LAN > WAN) page.
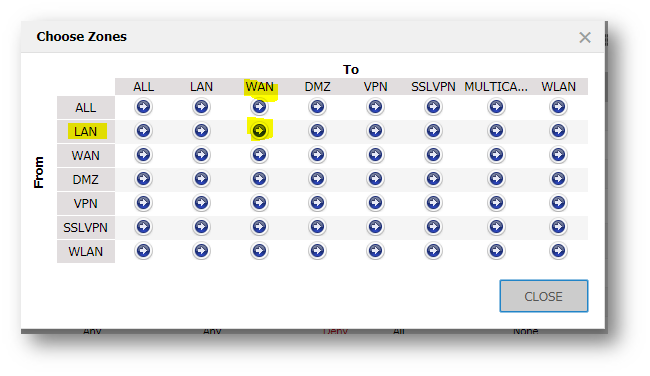
- Click on the marked arrow to open the Add Rule window.
- Select Deny as the Action.
- Select Any as the Service
- Select Source as the address objects created earlier.
- Select Any as the Destination
- Click Add and Close.

 NOTE:Verify that the rule just created has a higher priority than the default rule for LAN to WAN.
NOTE:Verify that the rule just created has a higher priority than the default rule for LAN to WAN.
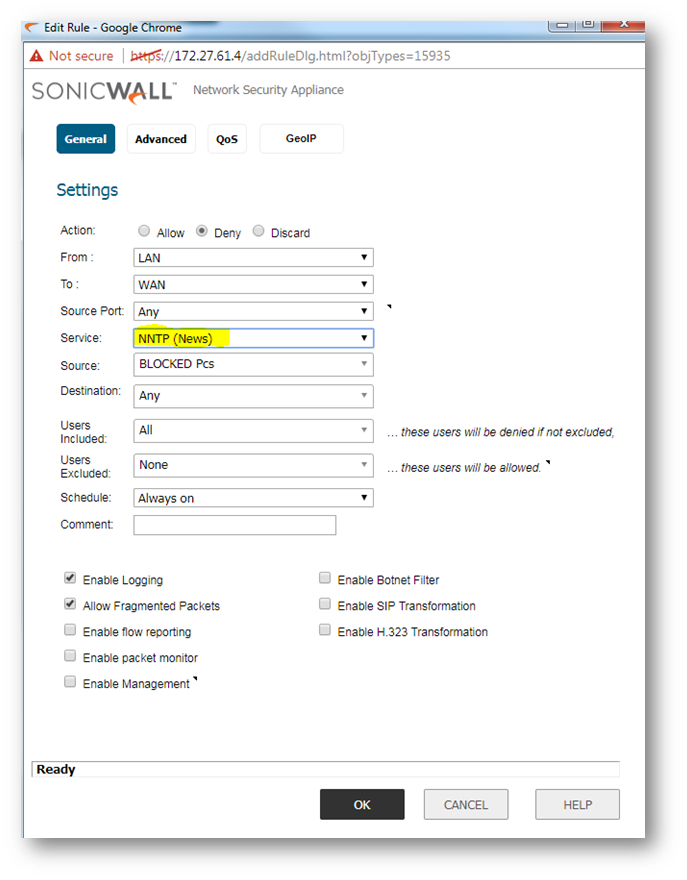
Blocking hosts in the LAN access to specific services on the WAN
- This section provides a configuration example for an access rule blocking LAN access to NNTP servers on the Internet. Perform the following steps to configure an access rule blocking LAN access to NNTP servers.
Blocking IP addresses on the WAN access to the LAN
By default all traffic from the WAN are denied access to the LAN, DMZ or any other zone. However, it may be required to allow some specific ports access to a server on the LAN or DMZ by creating the required Access Rules and NAT Policies. In most cases, the source would be set to Any. In such cases, where an access rule already exists to allow traffic from anywhere on the Internet to the LAN or DMZ, it may be required to deny traffic from IP addresses known (or suspected) to be coming from a non-secure source. This is an example of a deny rule.
This section provides a configuration example of an access rule blocking some IP addresses on the Internet access to the LAN zone of the SonicWall. Perform the following steps to configure an access rule blocking access to the LAN zone from the Internet.
- Navigate to POLICIES | OBJECTS | page.
- Create Address Object/s or Address Groups of hosts to be blocked.
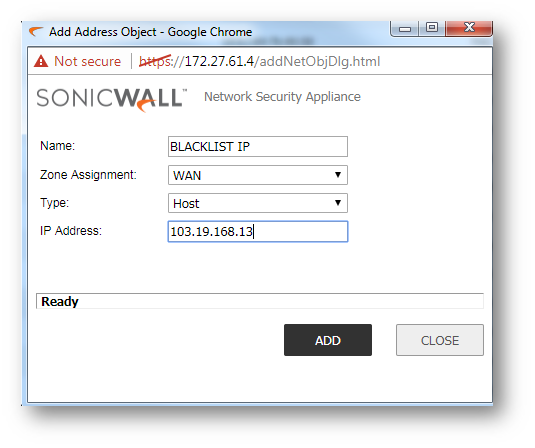
 NOTE: Refer Understanding Address Objects In SonicOS for more information on creating Address Objects. Set the zone as WAN when creating Address Objects of IP addresses on the Internet.
NOTE: Refer Understanding Address Objects In SonicOS for more information on creating Address Objects. Set the zone as WAN when creating Address Objects of IP addresses on the Internet. - Navigate to Policies | Access Rules page.
- Select the WAN to LAN button to enter the Access Rules (WAN | LAN) page.
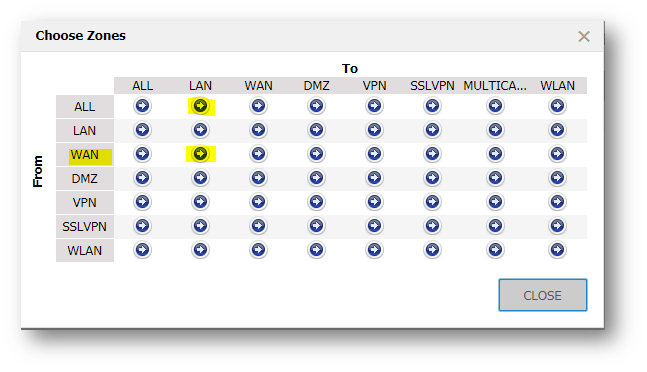
- Click marked arrow to open the Add Rule window.
- Select Deny as the Action.
- Select Any as the Service
- Select Source as the address object or group created earlier.
- Select Any as the Destination
- Click Add and Close.

 NOTE: Verify that the rule just created has a higher priority than the default rule for WAN to LAN.
NOTE: Verify that the rule just created has a higher priority than the default rule for WAN to LAN.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > Networking
- Firewalls > NSv Series > Networking
- Firewalls > SonicWall SuperMassive 9000 Series > Networking
- Firewalls > TZ Series > Networking






 YES
YES NO
NO