-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Using Digital Certificates in WAN GroupVPN & Global VPN Client connections



Description
Using digital certificates for authentication instead of preshared keys in a VPN configuration is considered more secure. In SonicWall UTM devices, digital certificates are one way of authenticating two peer devices to establish an IPsec VPN tunnel. The other is IKE using preshared key. The KB article describes the method to configure WAN GroupVPN and Global VPN Clients (GVC) to use digital certificates for authentication before establishing an IPsec VPN tunnel.
Features of IKE Authentication with Certificates in SonicWall WAN GroupVPN and GVC.
- A digital certificate, either obtained from a third party CA (like Verisign) or from a private CA (like Microsoft CA or OpenSSL), can be used for this configuration.
- When importing a signed certificate into the GVC client, it must be in the PKCS#12 format (.pfx or .p12 extension).
- In the SonicWall, the administrator has the option to create a Certificate Signing Request (CSR) and get it signed by a CA or import a signed certificate in the PKCS#12 format (.pfx or .p12 extension).
- Both peers must trust the issuer of the certificate. In other words, the CA certificate of the user certificate must be imported into the SonicWall as well as the remote GVC client.
- If a certificate has already been imported into the SonicWall signed by a 3rd party CA (for example, Versign), this can be selected in the WAN GroupVPN. The CA certificate must be imported into the GVC client.
- Both SonicWall and the remote GVC client can use the same certificate (3rd party or otherwise) provided the issuing CA is imported into both peers.
- SonicWall supports digital certificates issued by different CAs to be imported into the SonicWall UTM device and the remote GVC client.
- SonicWall also supports forcing both peers to use certificates issued by the same CA.
- In the WANGroupVPN configuration, Peer ID types of Distinguished Name, Email Address or Domain Name can be set. The IDs must be of the certificate to be used in the remote client (GVC). A similar setting, to set the ID, is not available in the GVC client.
- ID type of Email Address or Domain Name must be used only if the certificate has a Subject Alternative Name field with a value of either RFC822 Name=<local-part@domain.com>or DNS Name=. If a certificate has both these values, only the first value listed can be set for ID type.
- The E-Mail ID and Domain Name filters can contain a string or partial string identifying the acceptable range required. The strings entered are not case sensitive and can contain the wild card characters * (for more than 1 character) and ? (for a single character). For example, the string *@sonicwall.com when E-Mail ID is selected, would allow anyone with an email address that ended in SonicWall.com to have access; the string *sv.us.SonicWall.com when Domain Name is selected, would allow anyone with a domain name that ended in sv.us.SonicWall.com to have access.
- Distinguished Name (DN) is based on the certificates Subject Distinguished Name field, which is contained in all certificates by default. The format of any Subject Distinguished Name is determined by the issuing Certificate Authority. Common fields are Country (C=), Organization (O=), Organizational Unit (OU=), Common Name (CN=), Locality (L=), and vary with the issuing Certificate Authority. The actual Subject Distinguished Name field in an X.509 Certificate is a binary object which must be converted to a string for matching purposes. The fields are separated by the forward slash character, for example: /C=US/O=SonicWall, Inc./OU=TechPubs/CN=Joe Pub.
DN is a specific reference to a particular certificate. To use DN for multiple users with certificates from the same domain, you must use a field common to all the user certificates.
For example, for a Subject DN such as this: /C=IN/ST=KA/O=SonicWallInc./CN=gvc.kb-soniclab.local/emailAddress=admin@kb-soniclab.local. Any of the following could be used:
O=SonicWall Inc. or
CN=gvc.kb-soniclab.local
Resolution
The certificate signing process described here is using a Windows Server 2008 CA. To configure a Microsoft CA to accept a Subject Alternative Name attribute from a certificate request, refer this Microsoft article: How to configure a CA to accept a SAN attribute from a certificate request
- Creating Certificate Signing Request (CSR) in the SonicWall
- Obtaining certificates using Windows Server Certificate Enrollment Web Services
- Configuring WAN GroupVPN
- Importing the user certificate into the GVC client and establishing a connection
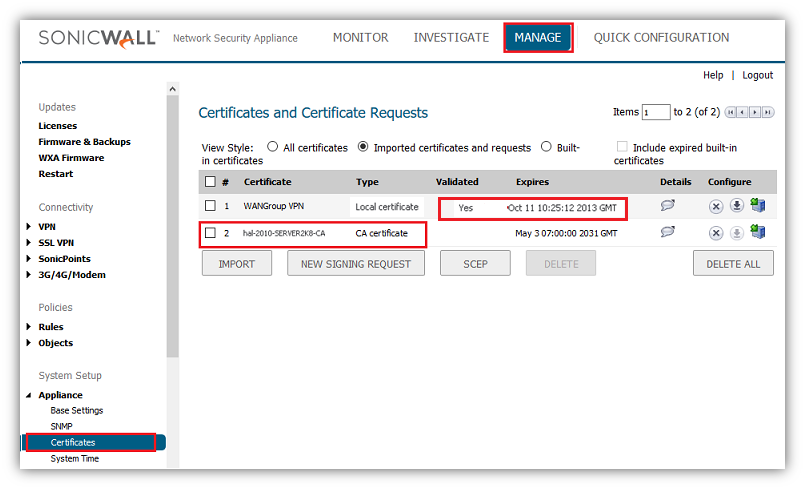
Creating Certificate Signing Request (CSR) in the SonicWall
Login to the SonicWall management GUI
- Click Manage in the top navigation menu
- Navigate to the Appliance | Certificates page.
- Click on New Signing Request to create a similar CSR as under
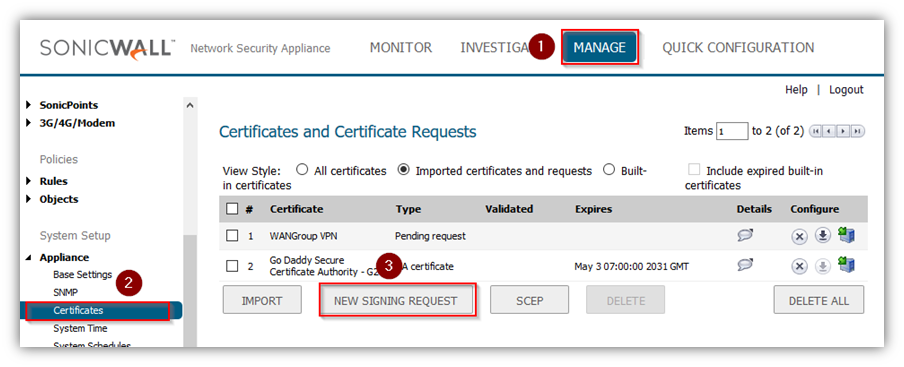
Click on Generate to save.
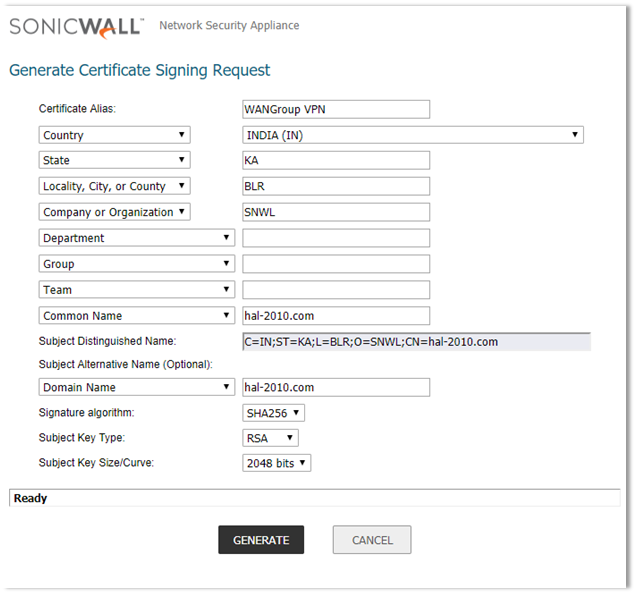
Refresh the page.
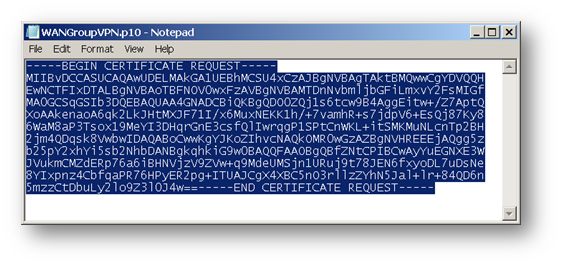
Click on the download button to download the CSR.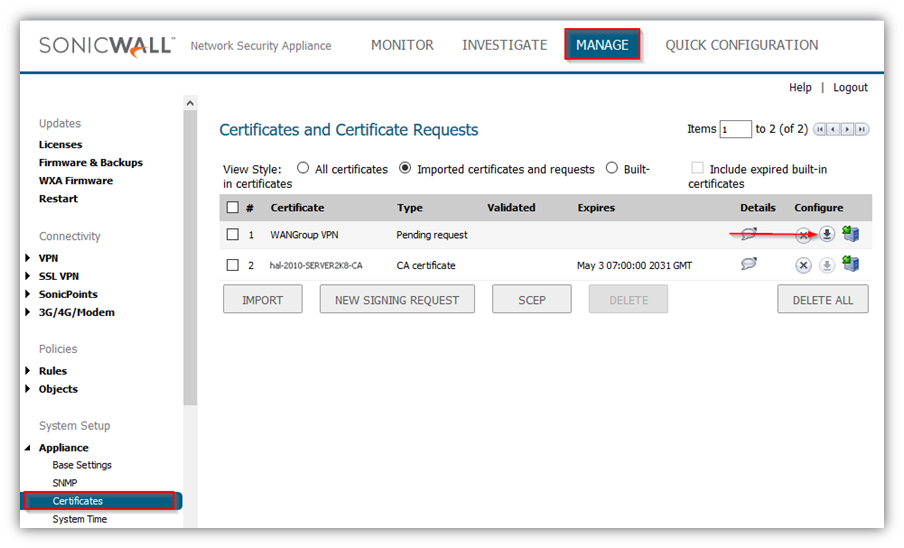
Obtaining certificates using Windows Server Certificate Enrollment Web Services
Obtaining a Gateway certificate to use in WAN GroupVPN configuration
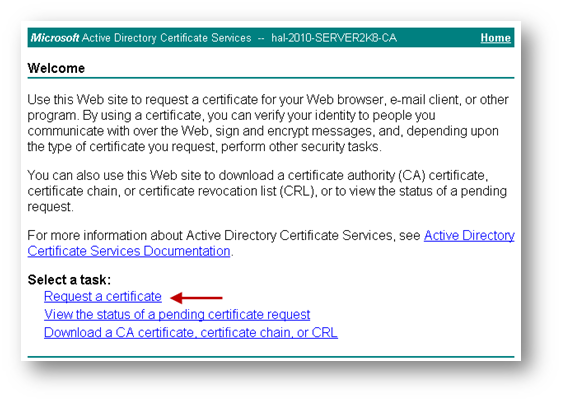
Open a browser and navigate to the Microsoft Windows Certificate Enrollment page: http:///CertSrv
When prompted for authentication, enter username and password of Administrator.
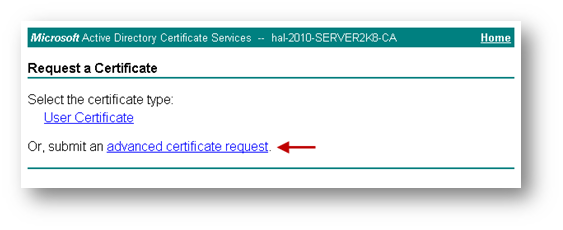
Click on Request a certificate
Click on advanced certificate request.
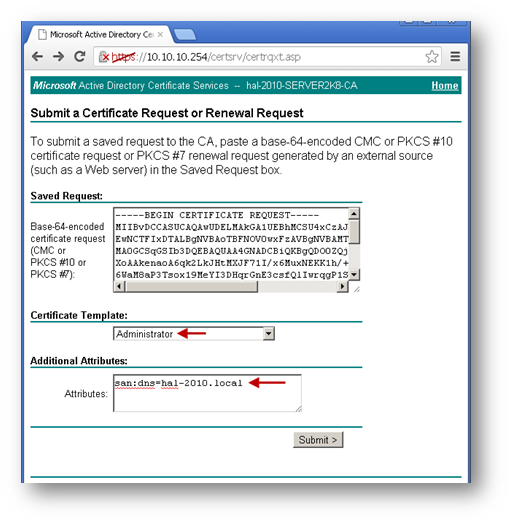
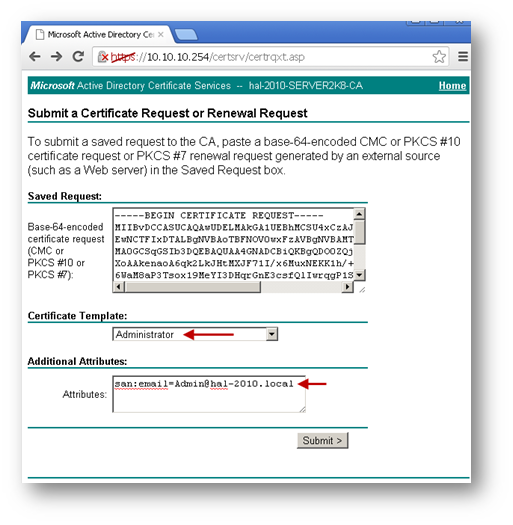
Copy the contents of CSR in the Saved Request box.
Select Administrator under Certificate Template. Note: User or Web Server template also could be selected.
Under Attributes, either enter san:dns=yourdomainname.com or san:email=<local-part@domain.com>. Note: To configure a Microsoft CA to accept a Subject Alternative Name attribute from a certificate request, refer this Microsoft article: How to configure a CA to accept a SAN attribute from a certificate request
Click on Submit and you will taken to the next page.
On this page click on Download certificate or Download certificate chain to save the signed certificate to disk.
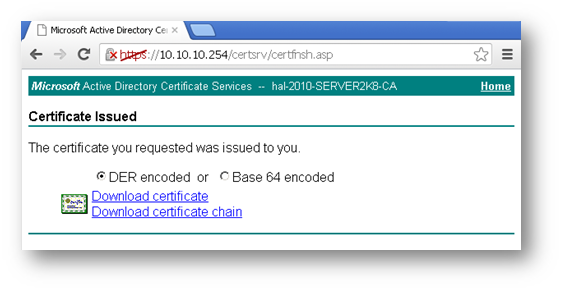
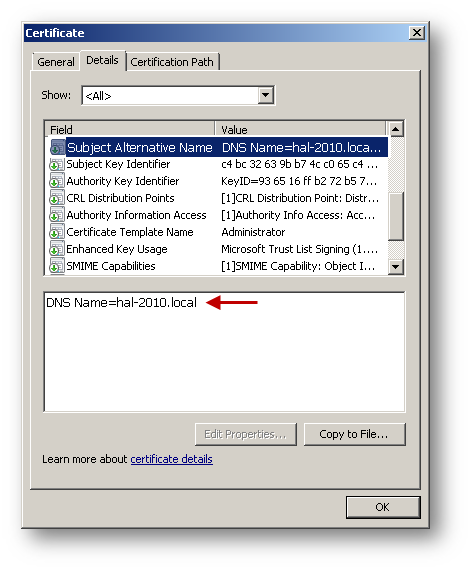
Below is an example of a signed certificate's Subject Alternative Name (SAN):
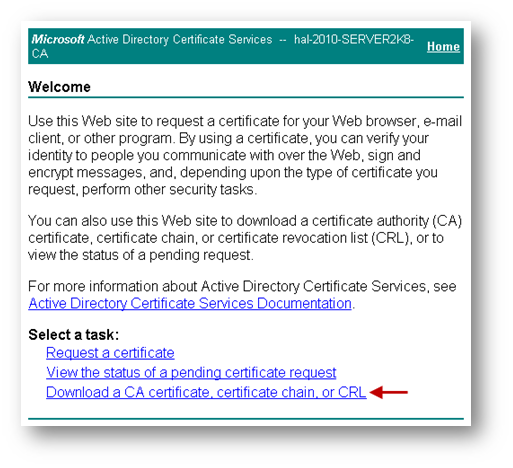
Downloading the CA certificate for the signed certificate.
Navigate to the Microsoft Windows Certificate Enrollment page: http:///CertSrv
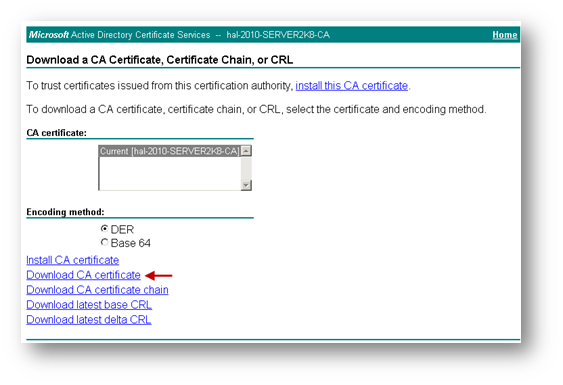
Click on Download a CA certificate....
On the next page, click on Download CA certificate and save the certificate to disk.
Upload the signed certificate into the SonicWall via the upload button of the CSR pending request.
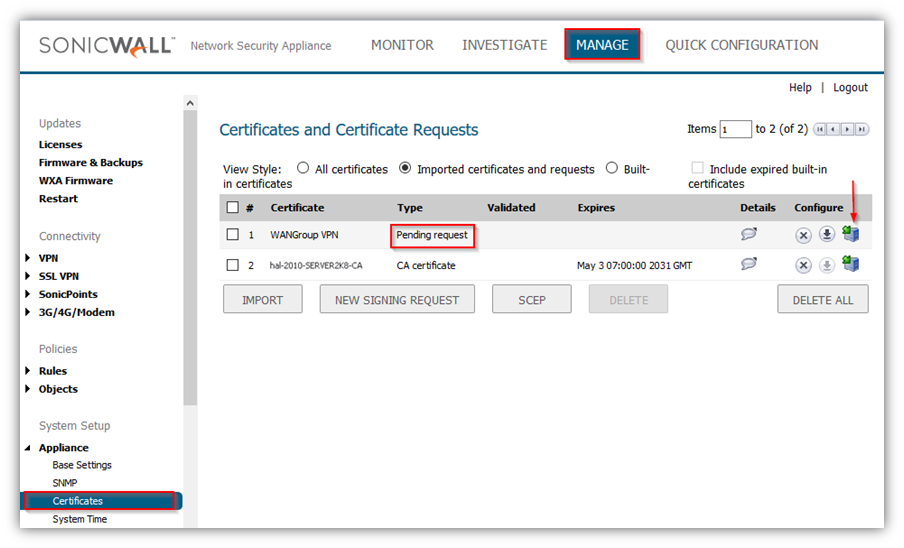
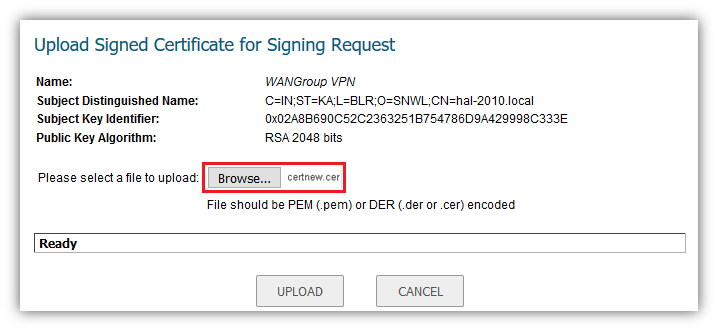
To establish trust and complete the validation of the signed certificate, import the CA certificate
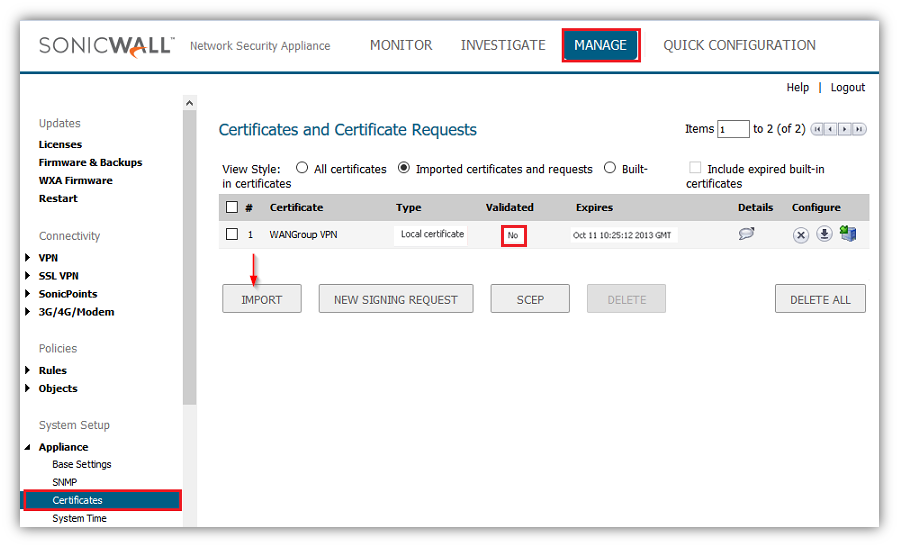
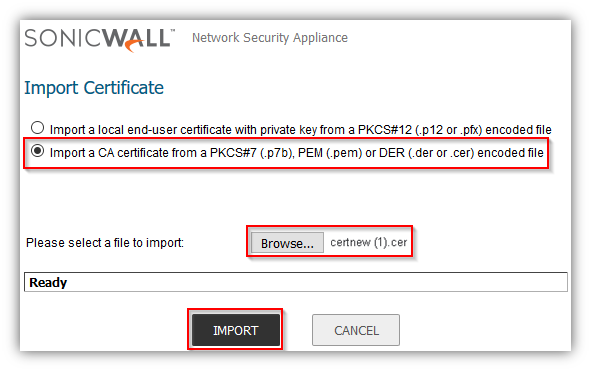
Obtaining a user certificate for GVC clients.
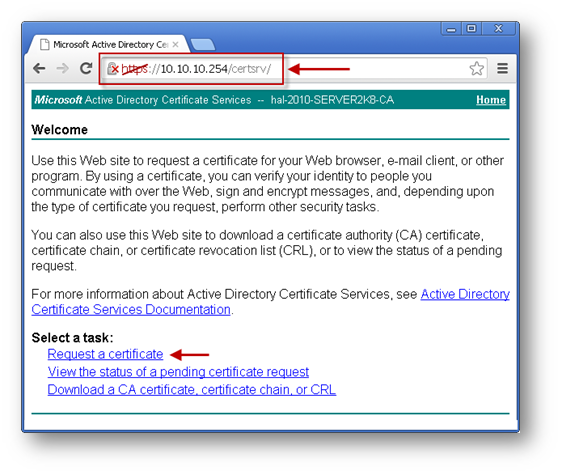
Navigate to the Microsoft Windows Certificate Enrollment page: http:///CertSrv
When prompted for authentication, enter username and password of a Domain User.
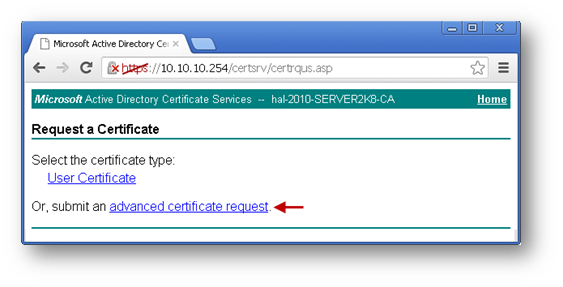
Click on Request a certificate
Click on advanced certificate request.
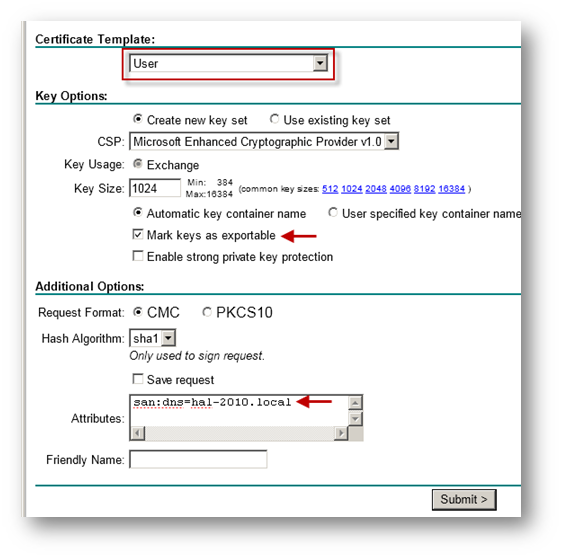
Select User under Certificate Template. Note: Administrator or Web Server template also could be selected.
Under Attributes, either enter san:dns=yourdomainname.com or san:email=<local-part@domain.com>. Note: To configure a Microsoft CA to accept a Subject Alternative Name attribute from a certificate request, refer this Microsoft article: How to configure a CA to accept a SAN attribute from a certificate request
Click on Submit and you will taken to the next page.
On this page click on Download certificate or Download certificate chain to save the signed certificate to disk.
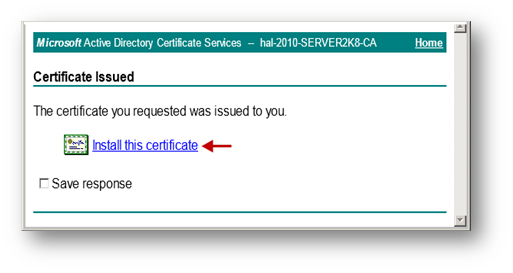
The signed certificate will be installed within the browser.
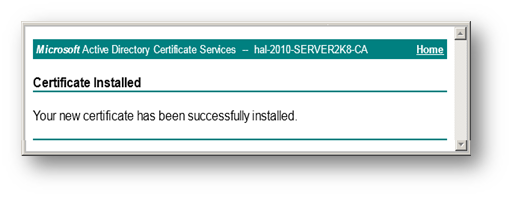
Export the certificate with its private key from the browser.
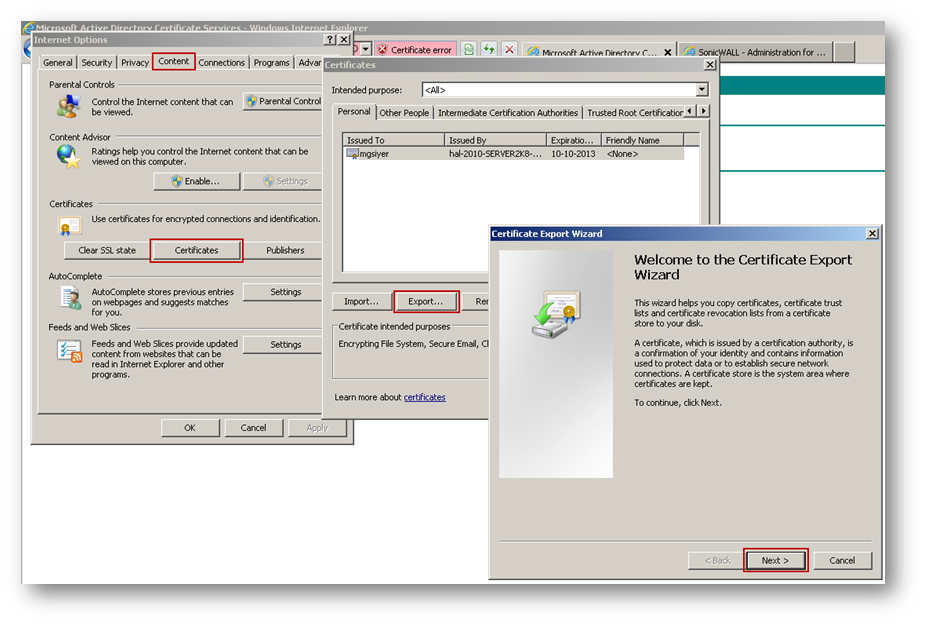
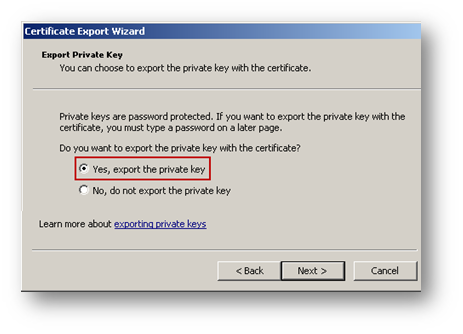

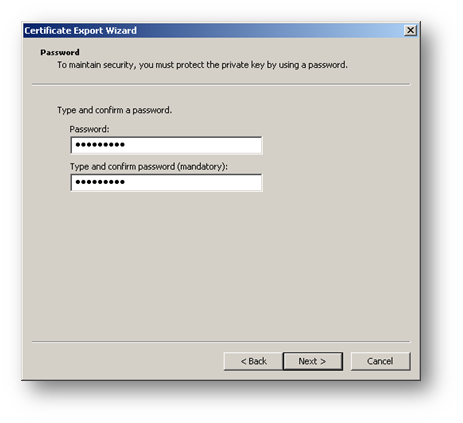
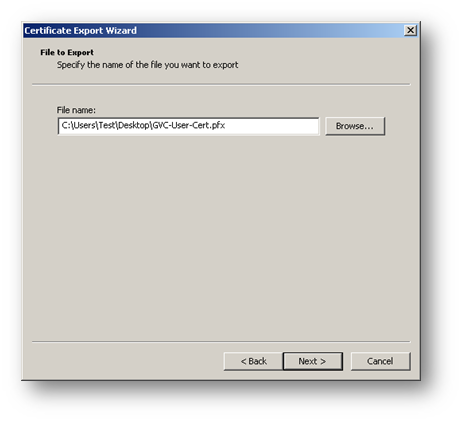
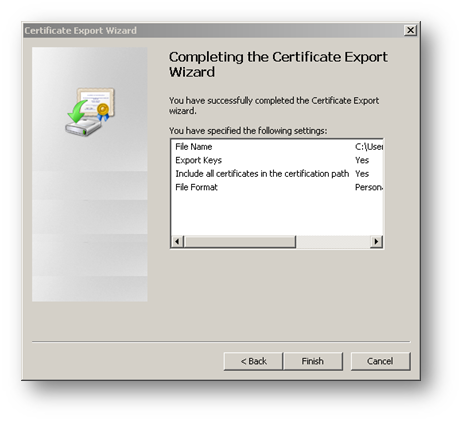
Configuring WAN GroupVPN
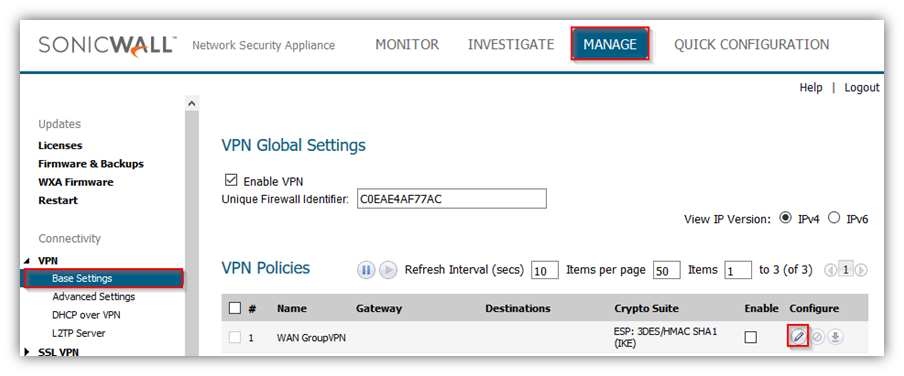
Login to the SonicWall management GUI
Navigate to the VPN | Base Settings page.
Enable the Enable VPN check box at the top and the Enable check box of WAN GroupVPN.
Click on Accept at the top to save the changes.
Click on the configure button under WAN GroupVPN to open the VPN Policy window.
Select Authentication Method as IKE using 3rd Party Certificates.
Select the signed certificate, imported into the SonicWall earlier, under Gateway Certificate
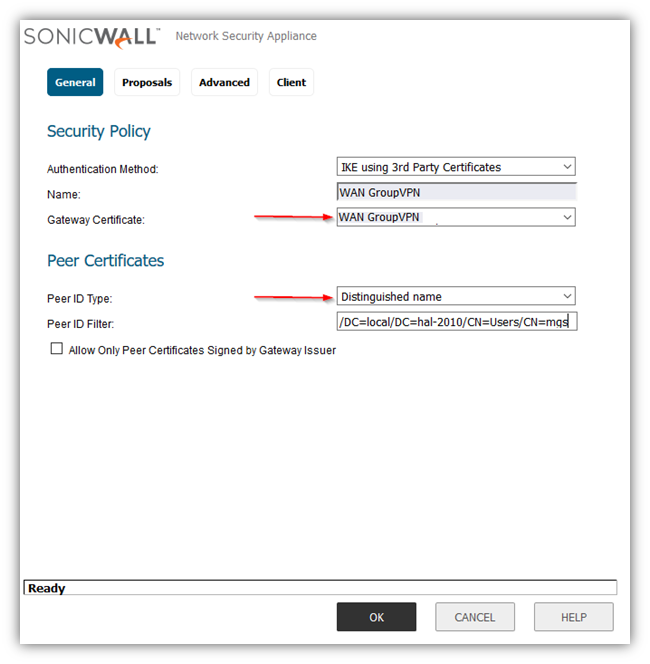
Peer Certificates
When setting Peer ID Type, the administrator may choose from Distinguished Name, Email Address or Domain Name. The IDs must be of the certificate to be used in the remote client (GVC). This is the certificate obtained from the Windows CA, installed in the browser and exported with private key earlier.
Peer ID Type: Domain Name - In this example, this is the attribute set at the time of obtaining the user certificate and found under the Subject Alternative Name field of the certificate - hal-2010.local
Peer ID Type: Email ID - This must be attribute of san:email=<email@address.com| set at the time of obtaining the user certificate and found under the Subject Alternative Name field of the certificate. For example, the string *@hal-2010.local would allow anyone with an email address ending in hal-2010.local to have access;
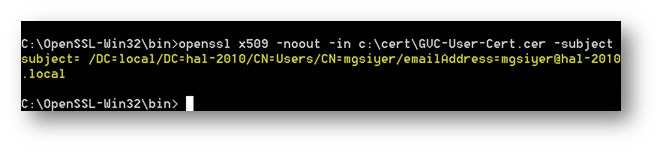
Peer ID Type: Distinguished Name - DN is a specific reference to a particulare certificate. To use DN for multiple users with certificates from the same domain, you must use a field common to all the user certificates. For example, for a Subject DN such as this:
/C=IN/ST=KA/O=SonicWall Inc./CN=gvc.kb-soniclab.local/emailAddress=admin@kb-soniclab.local.
Any of the following could be used:
O=SonicWall Inc. or
CN=gvc.kb-soniclab.local
The exact DN can be found using the following OpenSSL command:
Importing the user certificate into the GVC client and establishing a connection
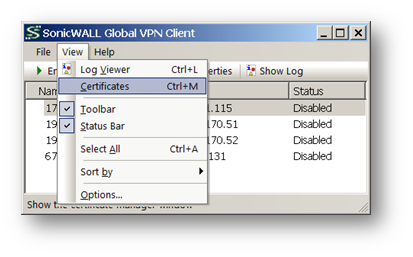
Open the GVC client
Click on View | Certificate to open the Certificate window.
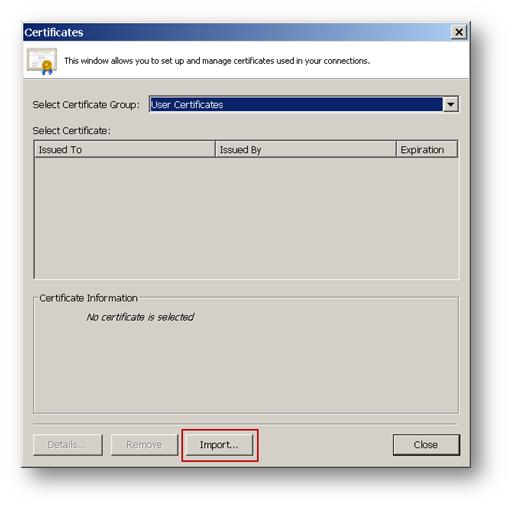
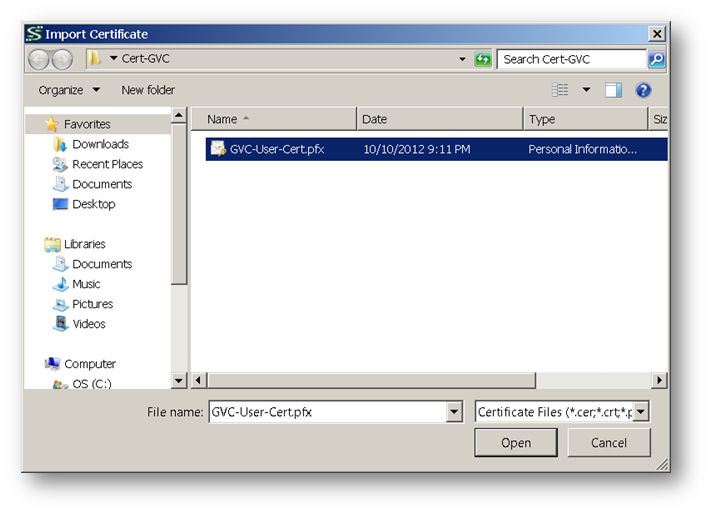
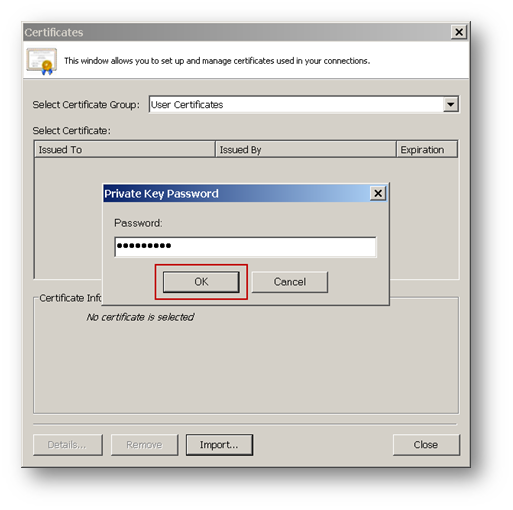
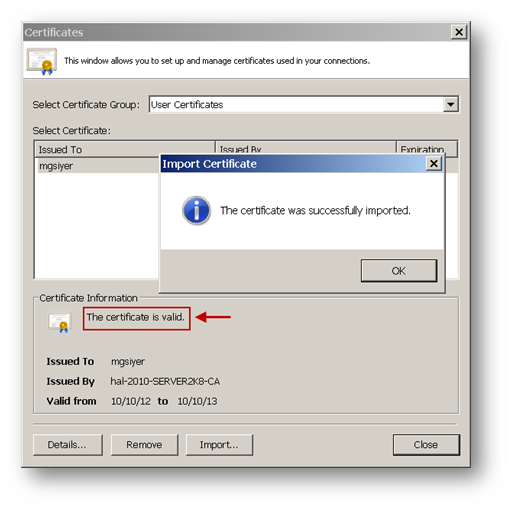
Click on Import to import the user certificate.
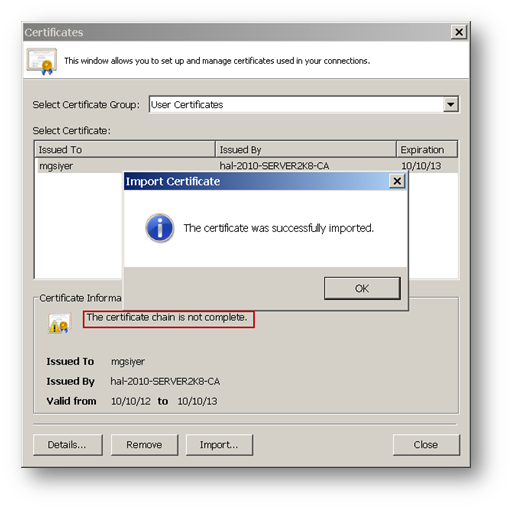
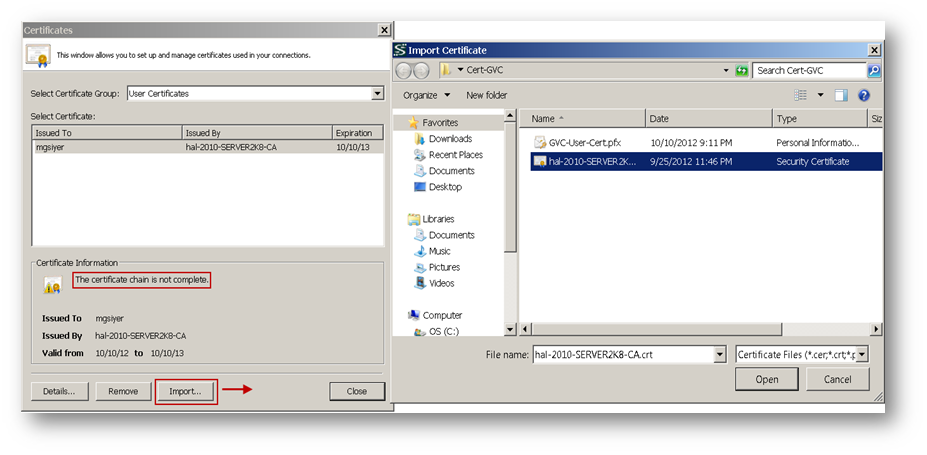
After the user certificate is imported, the CA certificate must be imported to establish trust. Until trust is established the Certificate window may show a message, The certificate chain is not complete.
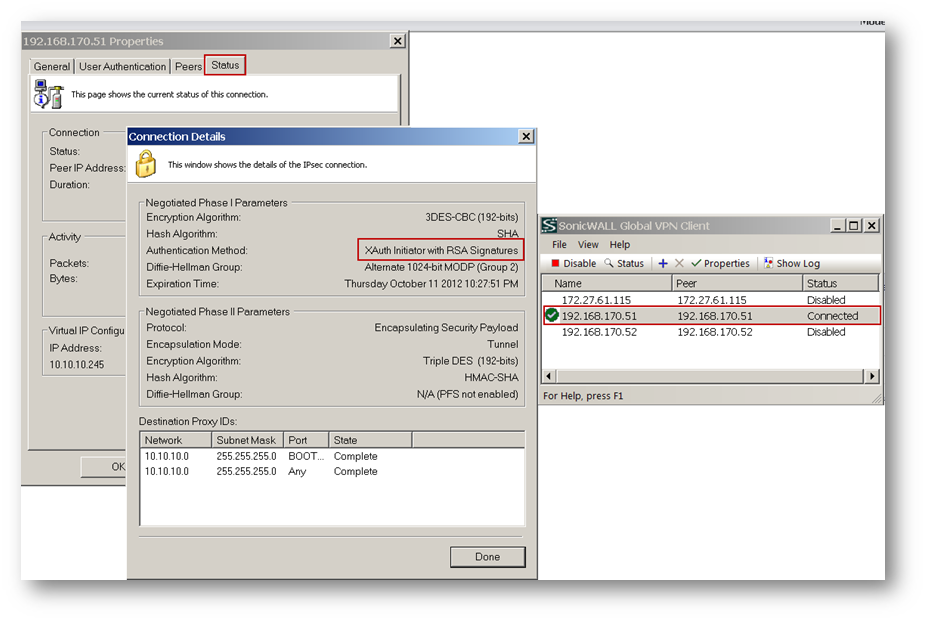
Once trust is established, the GVC client is ready to connect to the SonicWall. Create a connection and enable it.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series > VPN
- Firewalls > SonicWall NSA Series > VPN
- Firewalls > SonicWall SuperMassive 9000 Series > VPN
- Firewalls > SonicWall SuperMassive E10000 Series > VPN






 YES
YES NO
NO