-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Unable to change expired password via NetExtender



Description
When connecting via NetExtender and your password has expired you receive the following error.
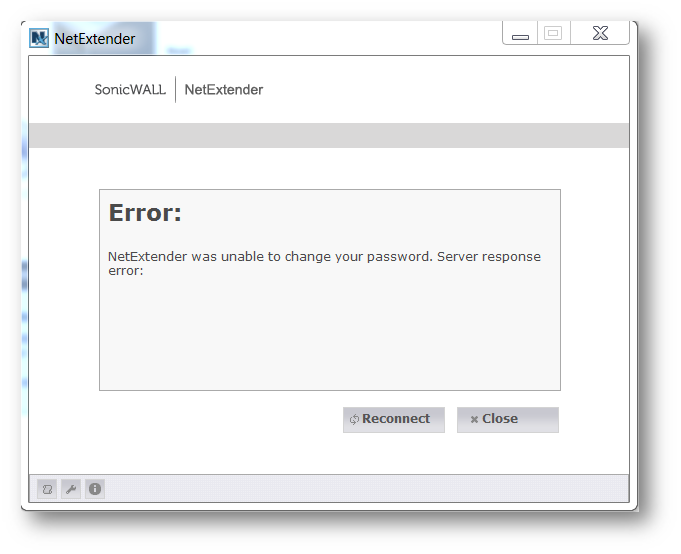
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
- Check that the time on the Server matches the local PC and SonicWall.
- Check the LDAP setting:
- If using bind distinguished name please confirm that the distinguished name is used. This can be found in AD by enabling Advanced Features and then going to the properties of the user account and selecting Attribute editor (you will find the distinguished name listed)
- Make sure the Use TLS(SSL) option is selected.
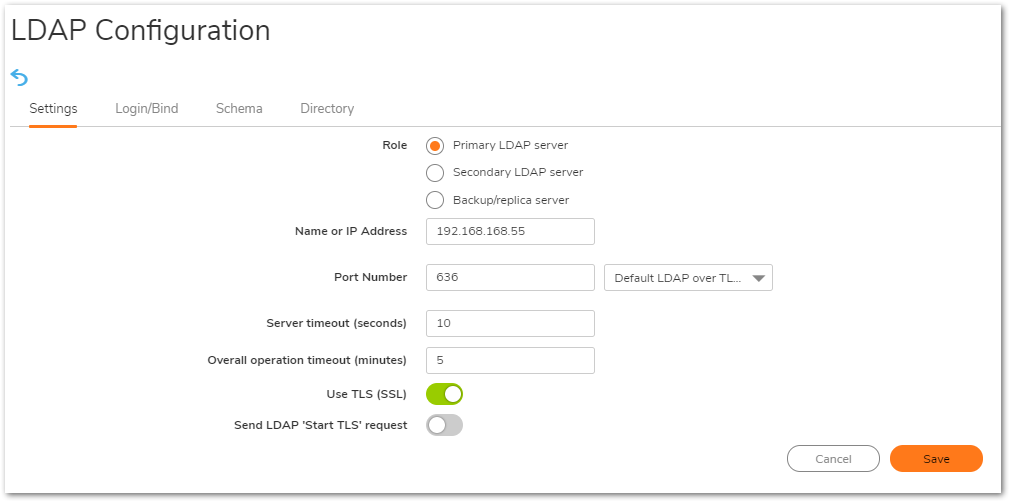
If the user account being used to bind to the LDAP server is not the builtin Administrator account, please make sure the following permissions are delegated:
- Create the user you'll bind with. Make it a member of Domain Users or Domain Admin.
 NOTE: The AD/LDAP bind account used can be a domain admin or a domain user with all required permission to read and modify users.
NOTE: The AD/LDAP bind account used can be a domain admin or a domain user with all required permission to read and modify users. - Create the group you'll delegate permissions to. Add the user you created to this group.
- Delegate control to the highest available OU where users are located. i.e. at the domain top level so that the user has control over your new group within the entire directory structure. You may need to enable the Advanced Features in Active Directory Users and Computers (ADUC) to see some of the security properties.
- In ADUC, click on the highest point in the directory.
- Right click on it, click Delegate Control.
- Follow the wizard... Add the newly created group to the list of users/groups to delegate control to. Click Next.
- Delegate the following common tasks: Reset user passwords and force password change at next logon.
- Click Next and close the wizard.
- Create the user you'll bind with. Make it a member of Domain Users or Domain Admin.
- At this point if you have the Advanced Features enabled in ADUC you should be able to right click the top level of the domain and click Properties | Security tab. In the Security tab you'll see the newly created group listed.
Select it, and click Advanced. In the Permission entries list you'll see at least two line items for the newly created group. One should say the access is Reset password, and the next should be blank. Both should be inherited from "None". Double-clicking the one with the blank access line will bring up the list of permissions. You should see that Read pwdLastSet and Write pwdLastSet are selected. Click Cancel. - Edit the Newly created group. Click the Security tab. Select the newly created group from the group list. Click Advanced. Note whether Inheritance has been enabled or not, and what permissions are in the list. Inheritance should be enabled, and you should see the two line items for the newly created group listed as well.
 NOTE: If the AD/LDAP bind account used is not part of the domain admin group, make sure to check the "Attribute Editor" tab for the user and change the "adminCount" parameter to "1". Once the above configurations have been checked / corrected, delete the LDAP configurations on the firewall and re-add them so the firewall can bind properly.
NOTE: If the AD/LDAP bind account used is not part of the domain admin group, make sure to check the "Attribute Editor" tab for the user and change the "adminCount" parameter to "1". Once the above configurations have been checked / corrected, delete the LDAP configurations on the firewall and re-add them so the firewall can bind properly.
How to Test:
- Set the test user account to change password at next login in Active directory.
- Launch NetExtender and connect to the SSLVPN.
- When prompted for the password change, enter the Old password and then the New password twice. Click OK.
- You will now be able to successfully change the password and not receive the server error.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
- Check that the time on the Server matches the local PC and SonicWall.
- Check the LDAP setting:
- If using bind distinguished name please confirm that the distinguished name is used. This can be found in AD by enabling Advanced Features and then going to the properties of the user account and selecting Attribute editor (you will find the distinguished name listed)
- Make sure the Use TLS(SSL) option is selected.
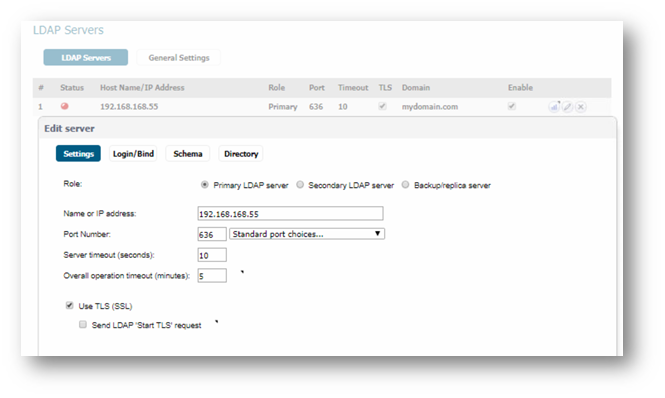
- If the user account being used to bind to the LDAP server is not the builtin Administrator account please make sure the following permissions are delegated:
- Create the user you'll bind with. Make it a member of Domain Users or Domain Admin.
 NOTE: The AD/LDAP bind account used can be a domain admin or a domain user with all required permission to read and modify users.
NOTE: The AD/LDAP bind account used can be a domain admin or a domain user with all required permission to read and modify users. - Create the group you'll delegate permissions to. Add the user you created to this group.
- Delegate control to the highest available OU where users are located. i.e. at the domain top level so that the user has control over your new group within the entire directory structure. You may need to enable the Advanced Features in Active Directory Users and Computers (ADUC) to see some of the security properties.
- In ADUC, click on the highest point in the directory.
- Right click on it, click Delegate Control.
- Follow the wizard... Add the newly created group to the list of users/groups to delegate control to. Click Next.
- Delegate the following common tasks: Reset user passwords and force password change at next logon.
- Click Next and close the wizard.
- Create the user you'll bind with. Make it a member of Domain Users or Domain Admin.
- At this point if you have the Advanced Features enabled in ADUC you should be able to right click the top level of the domain and click Properties | Security tab. In the Security tab you'll see the newly created group listed.
Select it, and click Advanced. In the Permission entries list you'll see at least two line items for the newly created group. One should say the access is Reset password, and the next should be blank. Both should be inherited from "None". Double-clicking the one with the blank access line will bring up the list of permissions. You should see that Read pwdLastSet and Write pwdLastSet are selected. Click Cancel. - Edit the Newly created group. Click the Security tab. Select the newly created group from the group list. Click Advanced. Note whether Inheritance has been enabled or not, and what permissions are in the list. Inheritance should be enabled, and you should see the two line items for the newly created group listed as well.
 NOTE: If the AD/LDAP bind account used is not part of the domain admin group, make sure to check the "Attribute Editor" tab for the user and change the "adminCount" parameter to "1". Once the above configurations have been checked / corrected, delete the LDAP configurations on the firewall and re-add them so the firewall can bind properly.
NOTE: If the AD/LDAP bind account used is not part of the domain admin group, make sure to check the "Attribute Editor" tab for the user and change the "adminCount" parameter to "1". Once the above configurations have been checked / corrected, delete the LDAP configurations on the firewall and re-add them so the firewall can bind properly.
How to Test:
- Set the test user account to change password at next login in Active directory.
- Launch NetExtender and connect to the SSLVPN.
- When prompted for the password change, enter the Old password and then the New password twice. Click OK.
- You will now be able to successfully change the password and not receive the server error.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
- Check that the time on the Server matches the local PC and SonicWall.
- Check the LDAP setting:
- If using bind distinguished name please confirm that the distinguished name is used. This can be found in AD by enabling Advanced Features and then going to the properties of the user account and selecting attribute editor (you will find the distinguished name listed).
- Make sure the Use TLS(SSL) option is selected.
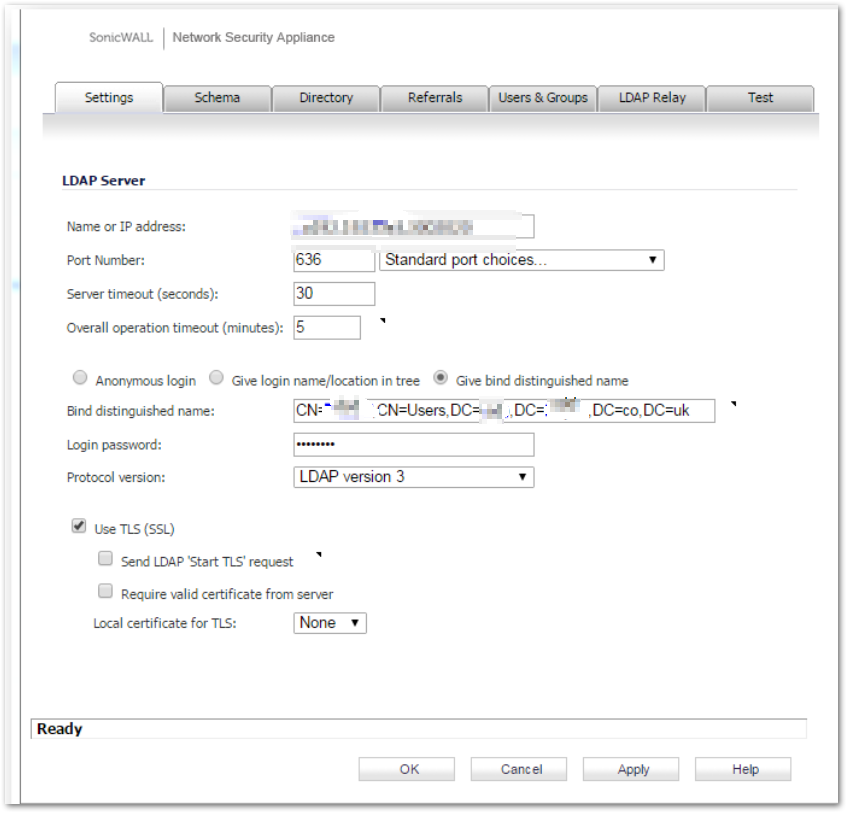
- If the user account being used to bind to the LDAP server is not the builtin Administrator account please make sure the following permissions are delegated:
- Create the user you'll bind with. Make it a member of Domain Users or Domain Admin.
 NOTE: The AD/LDAP bind account used can be a domain admin or a domain user with all required permission to read and modify users.
NOTE: The AD/LDAP bind account used can be a domain admin or a domain user with all required permission to read and modify users. - Create the group you'll delegate permissions to. Add the user you created to this group.
- Delegate control to the highest available OU where users are located. i.e. at the domain top level so that the user has control over your new group within the entire directory structure. You may need to enable the Advanced Features in Active Directory Users and Computers (ADUC) to see some of the security properties.
- In ADUC, click on the highest point in the directory.
- Right click on it, click Delegate Control.
- Follow the wizard... Add the newly created group to the list of users/groups to delegate control to. Click Next.
- Delegate the following common tasks: Reset user passwords and force password change at next logon.
- Click Next and close the wizard.
- Create the user you'll bind with. Make it a member of Domain Users or Domain Admin.
- At this point if you have the Advanced Features enabled in ADUC you should be able to right click the top level of the domain and click Properties | Security tab. In the Security tab you'll see the newly created group listed. Select it, and click Advanced. In the Permission entries list you'll see at least two line items for the newly created group. One should say the access is Reset password, and the next should be blank. Both should be inherited from "None". Double-clicking the one with the blank access line will bring up the list of permissions. You should see that Read pwdLastSet and Write pwdLastSet are selected. Click Cancel.
- Edit the Newly created group. Click the Security tab. Select the newly created group from the group list. Click Advanced. Note whether Inheritance has been enabled or not, and what permissions are in the list. Inheritance should be enabled, and you should see the two line items for the newly created group listed as well.
 NOTE: If the AD/LDAP bind account used is not part of the domain admin group, make sure to check the "Attribute Editor" tab for the user and change the "adminCount" parameter to "1". Once the above configurations have been checked / corrected, delete the LDAP configurations on the firewall and re-add them so the firewall can bind properly.
NOTE: If the AD/LDAP bind account used is not part of the domain admin group, make sure to check the "Attribute Editor" tab for the user and change the "adminCount" parameter to "1". Once the above configurations have been checked / corrected, delete the LDAP configurations on the firewall and re-add them so the firewall can bind properly.
How to Test:
- Set the test user account to change password at next login in Active directory.
- Launch NetExtender and connect to the SSLVPN.
- When prompted for the password change, enter the Old password and then the New password twice. Click OK.
- You will now be able to successfully change the password and not receive the server error.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSv Series > SSLVPN
- Firewalls > NSa Series > SSLVPN
- Firewalls > TZ Series > SSLVPN






 YES
YES NO
NO