-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
UDP and ICMP Flood Protection



Description
UDP and ICMP Flood attacks are a type of denial-of-service (DoS) attack. They are initiated by sending a large number of UDP or ICMP packets to a remote host. As a result, the victimized system's resources will be consumed with handling the attacking packets, which eventually causes the system to be unreachable by other clients.
SonicWall UDP and ICMP Flood Protection defend against these attacks by using a watch and block method. The appliance monitors UDP or ICMP traffic to a specified destination or to any destination. If the rate of UDP and ICMP packets per second exceeds the allowed threshold for a specified duration of time, the appliance drops subsequent UDP or ICMP packets to protect against a flood attack.
UDP packets that are DNS query or responses to or from a DNS server configured by the appliance are allowed to pass, regardless of the state of UDP Flood Protection.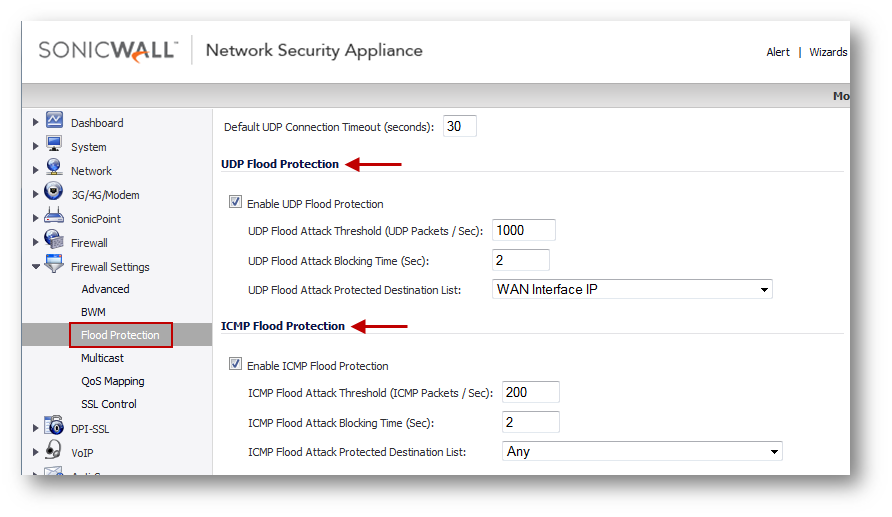
Resolution
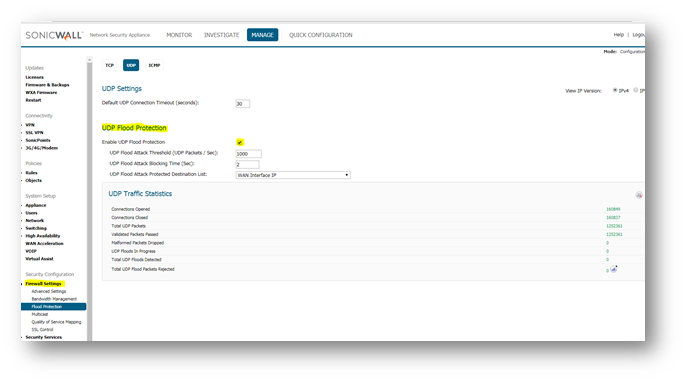
For UDP Flood Protection Option (GUI)
- Click MANAGE and then navigate to Firewall Settings | Flood Protection.
- On the Top bar , click UDP.
- Under UDP Flood Protection, enable checkbox Enable UDP Flood Protection.
- The following settings configure UDP Flood Protection.
- UDP Flood Attack Threshold (UDP Packets / Sec) The rate of UDP packets per second sent to a host, range or subnet that triggers UDP Flood Protection. The Threshold must be set carefully as too small a threshold may affect unintended traffic and too large a threshold may not effectively protect from an attack. The default value is 1000.
- UDP Flood Attack Blocking Time (Sec) After the appliance detects the rate of UDP packets exceeding the attack threshold for this duration of time, UDP Flood protection is activated, and the appliance will begin dropping subsequent UDP packets.
- UDP Flood Attack Protected Destination List The destination address object or address group that will be protected from UDP Flood Attack. If the destination target is random, set this field to Any.
- Click Accept.
The following log messages will be generated when SonicWall detects a UDP Flood Attack. The logs can be filtered by CategoryFirewall Settings andGroupFlood protection.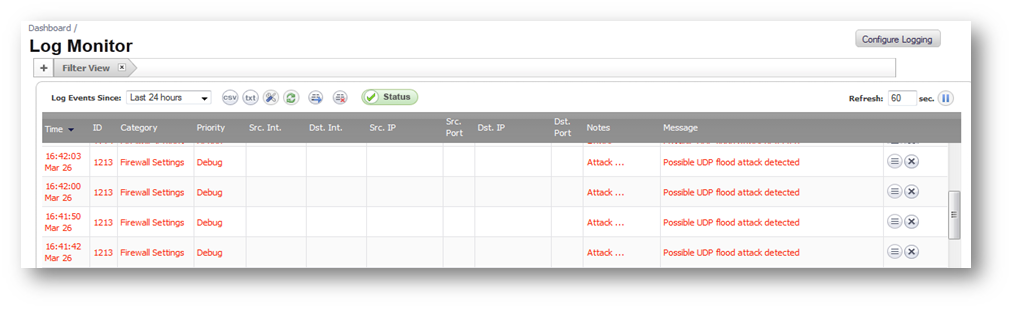
UDP Flood Protection can also be configured from the CLI.
- Login to the CLI.
- Enter Configuration mode.
- Enter the following commands to enable UDP Flood protection.
config(C0xxxxxxxx38)# udp To disable UDP Flood Protection
(config-udp)# flood-protection
(config-udp)# commit best-effort
(config-udp)# exit(config-udp)# no flood-protection
(config-udp)# commit best-effort
Additional options in the UDP prompt
- default-connection-timeout #Set default UDP connection timeout in minutes.
- flood-attack-threshold #Set UDP Flood Attack Threshold (UDP Packets / Sec).
- flood-block-timeout #Set UDP Flood Attack Blocking Time (Sec).
- flood-protected-dest-list #Set UDP flood attack protected destination list.
- flood-protection #Enable UDP flood protection.
For ICMP Flood Protection Option
- Click MANAGE and then navigate to Firewall Settings | Flood Protection.
- On the Top bar , click ICMP.
- Under ICMP Flood Protection, enable checkbox Enable ICMP Flood Protection.
- The following settings configure ICMP Flood protection.
- ICMP Flood Attack Threshold (ICMP Packets / Sec) The rate of ICMP packets per second sent to a host, range or subnet that triggers ICMP Flood protection. The Threshold must be set carefully as too small a threshold may affect unintented traffic and too large a threshold may not effectively protect from an attack. The default value is 200.
- ICMP Flood Attack Blocking Time (Sec) After the appliance detects the rate of ICMP packets exceeding the attack threshold for this duration of time, ICMP Flood protection is activated, and the appliance will begin dropping subsequent ICMP packets.
- ICMP Flood Attack Protected Destination List The destination address object or address group that will be protected from ICMP Flood attack.
- Click Accept.
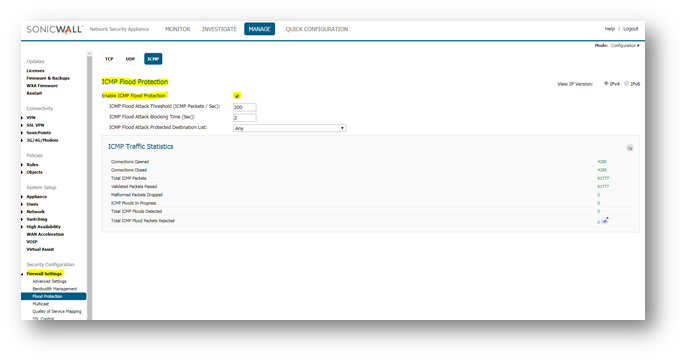
The following log messages will be generated when SonicWall detects a ICMP Flood Attack. The logs can be filtered by Category Firewall Settings and Group Flood protection.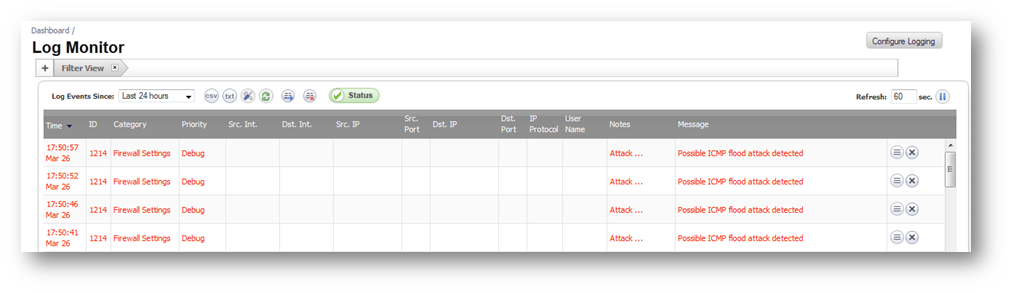
UDP Traffic Statistics
The UDP Traffic Statistics table provides statistics on the following.
- Connections Opened Incremented when a UDP connection initiator sends a SYN, or a UDP connection responder receives a SYN.
- Connections Closed Incremented when a UDP connection is closed when both the initiator and the responder have sent a FIN and received an ACK.
- Total UDP Packets Incremented with every processed UDP packet.
- Validated Packets Passed Incremented under the following conditions:
- When a UDP packet passes checksum validation (while UDP checksum validation is enabled).
- When a valid SYN packet is encountered (while SYN Flood protection is enabled).
- When a SYN Cookie is successfully validated on a packet with the ACK flag set (while SYN Flood protection is enabled).
- Malformed Packets Dropped - Incremented under the following conditions:
- When UDP checksum fails validation (while UDP checksum validation is enabled).
- When the UDP SACK Permitted (Selective Acknowledgment, see RFC1072) option is encountered, but the calculated option length is incorrect.
- When the UDP MSS (Maximum Segment Size) option is encountered, but the calculated option length is incorrect.
- When the UDP SACK option data is calculated to be either less than the minimum of 6 bytes, or modulo incongruent to the block size of 4 bytes.
- When the UDP option length is determined to be invalid.
- When the UDP header length is calculated to be less than the minimum of 20 bytes.
- When the UDP header length is calculated to be greater than the packet's data length.
- UDP Floods In Progress The number of individual forwarding devices that are currently exceeding the UDP Flood Attack Threshold.
- Total UDP Floods Detected The total number of events in which a forwarding device has exceeded the UDP Flood Attack Threshold
- Total UDP Flood Packets Rejected The total number of packets dropped because of UDP Flood Attack detection.
ICMP Traffic Statistics
- The ICMP traffic statistics table provides the same categories of information as the UDP traffic statistics above.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
Configuring UDP Flood Protection(GUI)
- Login to the SonicWall management GUI.
- Navigate to Firewall Settings | Flood Protection page.
- Under UDP Flood Protection, enable checkbox Enable UDP Flood Protection.
- The following settings configure UDP Flood Protection.
- UDP Flood Attack Threshold (UDP Packets / Sec): The rate of UDP packets per second sent to a host, range or subnet that triggers UDP Flood Protection. The Threshold must be set carefully as too small a threshold may affect unintended traffic and too large a threshold may not effectively protect from an attack. The default value is 1000.
- UDP Flood Attack Blocking Time (Sec) : After the appliance detects the rate of UDP packets exceeding the attack threshold for this duration of time, UDP Flood protection is activated, and the appliance will begin dropping subsequent UDP packets.
- UDP Flood Attack Protected Destination List : The destination address object or address group that will be protected from UDP Flood attack. If the destination target is random, set this field to Any.
- Click Accept.
The following log messages will be generated when SonicWall detects a UDP Flood attack. The logs can be filtered by Category Firewall Settings and Group Flood Protection.
Configuring UDP Flood Protection(CLI)
- Login to the CLI.
- Enter Configuration mode.
- Enter the following commands to enable UDP Flood protection.
config(C0xxxxxxxx38)# udp
(config-udp)# flood-protection
(config-udp)# commit best-effort
(config-udp)# exit
To disable UDP Flood Protection (config-udp)# no flood-protection
(config-udp)# commit best-effort
Additional options in the UDP prompt
- default-connection-timeout #Set default UDP connection timeout in minutes.
- flood-attack-threshold #Set UDP Flood Attack Threshold (UDP Packets / Sec).
- flood-block-timeout #Set UDP Flood Attack Blocking Time (Sec).
- flood-protected-dest-list #Set UDP flood attack protected destination list.
- flood-protection #Enable UDP flood protection.
Configuring ICMP Flood Protection
- Login to the SonicWall management GUI.
- Navigate to Firewall Settings | Flood Protection page.
- Under ICMP Flood Protection, enable checkbox Enable ICMP Flood Protection.
- The following settings configure ICMP Flood Protection.
- ICMP Flood Attack Threshold (ICMP Packets / Sec) The rate of ICMP packets per second sent to a host, range or subnet that triggers ICMP Flood protection. The Threshold must be set carefully as too small a threshold may affect unintented traffic and too large a threshold may not effectively protect from an attack. The default value is 200.
- ICMP Flood Attack Blocking Time (Sec) After the appliance detects the rate of ICMP packets exceeding the attack threshold for this duration of time, ICMP Flood protection is activated, and the appliance will begin dropping subsequent ICMP packets.
- ICMP Flood Attack Protected Destination List The destination address object or address group that will be protected from ICMP Flood attack.
- Click Accept at the top.
The following log messages will be generated when SonicWall detects a ICMP Flood Attack. The logs can be filtered by Category Firewall Settings and Group Flood protection.
UDP Traffic Statistics
The UDP Traffic Statistics table provides statistics on the following:
- Connections Opened Incremented when a UDP connection initiator sends a SYN, or a UDP connection responder receives a SYN.
- Connections Closed Incremented when a UDP connection is closed when both the initiator and the responder have sent a FIN and received an ACK.
- Total UDP Packets Incremented with every processed UDP packet.
- Validated Packets Passed Incremented under the following conditions.
- When a UDP packet passes checksum validation (while UDP checksum validation is enabled).
- When a valid SYN packet is encountered (while SYN Flood protection is enabled).
- When a SYN Cookie is successfully validated on a packet with the ACK flag set (while SYN Flood protection is enabled).
- Malformed Packets Dropped - Incremented under the following conditions:
- When UDP checksum fails validation (while UDP checksum validation is enabled).
- When the UDP SACK permitted (Selective Acknowledgment, see RFC1072) option is encountered, but the calculated option length is incorrect.
- When the UDP MSS (Maximum Segment Size) option is encountered, but the calculated option length is incorrect.
- When the UDP SACK option data is calculated to be either less than the minimum of 6 bytes, or modulo incongruent to the block size of 4 bytes.
- When the UDP option length is determined to be invalid.
- When the UDP header length is calculated to be less than the minimum of 20 bytes.
- When the UDP header length is calculated to be greater than the packet's data length.
- UDP Floods In Progress The number of individual forwarding devices that are currently exceeding the UDP Flood attack Threshold.
- Total UDP Floods Detected The total number of events in which a forwarding device has exceeded the UDP Flood attack Threshold
- Total UDP Flood Packets Rejected The total number of packets dropped because of UDP Flood attack detection.
ICMP Traffic Statistics
- The ICMP traffic statistics table provides the same categories of information as the UDP traffic statistics above.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > NSa Series > Networking
- Firewalls > NSv Series > Networking
- Firewalls > TZ Series > Networking






 YES
YES NO
NO