-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Troubleshooting VPN packets drops with drop code message "Octeon Decryption Failed"



Description
This article explain the drop code Octeon Decryption Failed. Generally this drop comes up when vpn traffic is being dropped on the firewall. It means that the firewall was unable to decrypt the VPN packet and thus dropped it.
Now there can be multiple reasons why firewall was not able to decrypt it.
- Packet is corrupted due to network congestion on ISP end.
- Incoming SPI no. does not match to the SPI negotiated.
- It can be due to packet being tampered with prior to reaching SonicWall appliance and thus has changed its properties and thus is being dropped.
- If some ESP packets whose sequence is larger are reaching to firewall before the ESP packets whose sequence no. is smaller.
- It can be a valid behavior where the order in which packet are arriving to peer is not determined.
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
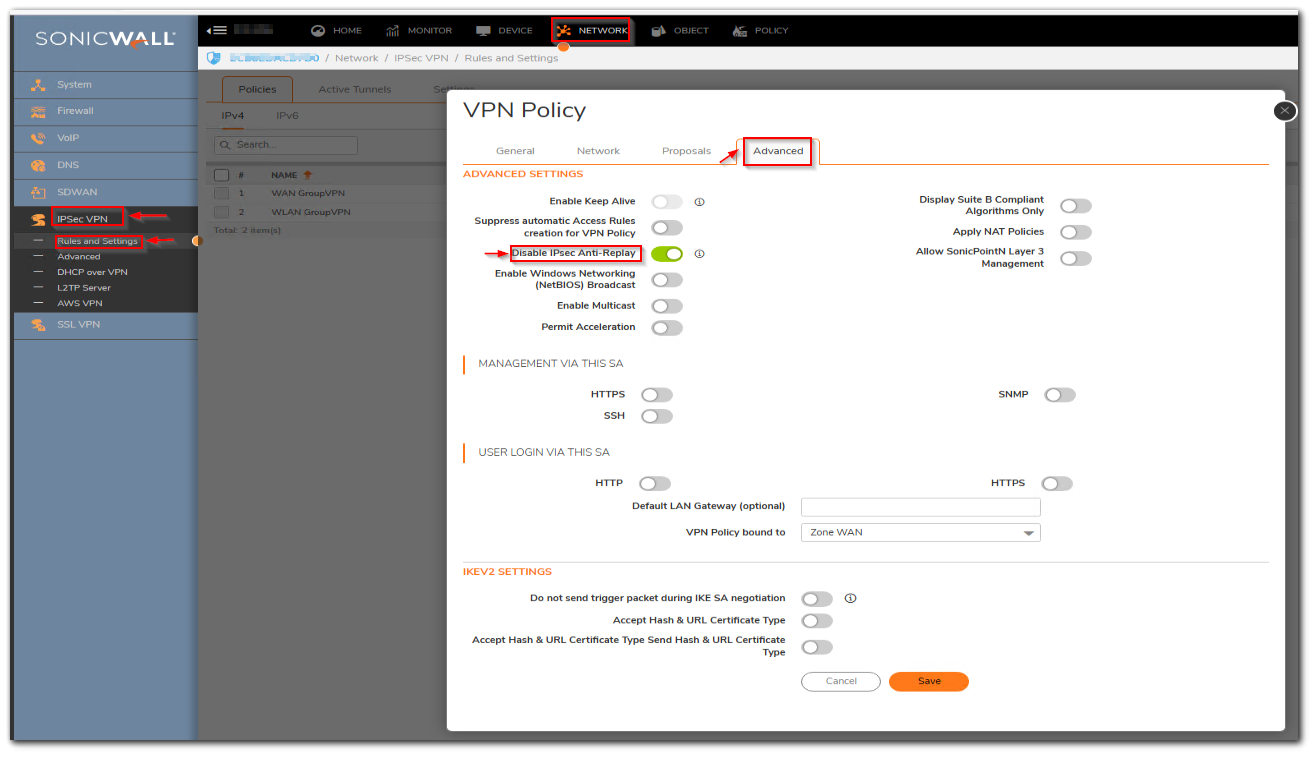
Check the box "Disable IPsec Anti-Replay"
The option would ensure that the SonicWall appliance would not drop the packets coming out of sequence and would accept it.It could be a valid reason as in a real-world network environment some packets might reach earlier compared to others.
The option is different for different platforms of firmware.
 NOTE: The VPN tunnel in question needs to be re-negotiated for the change to take effect.
NOTE: The VPN tunnel in question needs to be re-negotiated for the change to take effect.
- Navigate to Network Tab | IPsec VPN | Rules and Settings.
- Edit the VPN policy in question and click the Advanced tab.
- Check the box Disable IPsec Anti-Replay.
How to Test:
As mentioned earlier re-negotiate the VPN and perform the packet capture again. If the packet were being dropped due to incorrect sequence they would be allowed now.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
Check the box "Disable IPsec Anti-Replay"
The option would ensure that SonicWall appliance would not drop the packets coming out of sequence and would accept it.It could be a valid reason as in a real-world network environment some packets might reach earlier compared to others.
The option is different for different platforms of firmwares.
 NOTE: The VPN tunnel in question needs to be re-negotiated for the change to take effect.
NOTE: The VPN tunnel in question needs to be re-negotiated for the change to take effect.
- Navigate to Manage | VPN | Base settings.
- Edit the VPN policy in question and click Advanced tab.
- Check the box Disable IPSec Anti-Replay.

How to Test:
As mentioned earlier re-negotiate the VPN and perform the packet capture again.If the packet were being dropped due to incorrect sequence they would be allowed now.
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
In 6.1.1.8 and 5.9.1.x firmware and above
 NOTE:In current Gen5 (5.9.x) or Gen6 (6.x.x) firmware, this option is no longer on the diag page but is located on the Advanced tab of a VPN policy.
NOTE:In current Gen5 (5.9.x) or Gen6 (6.x.x) firmware, this option is no longer on the diag page but is located on the Advanced tab of a VPN policy.
- Navigate to VPN | settings.
- Edit the VPN policy in question and click Advanced tab.
- Check the box Disable IPSec Anti-Replay.

For older 5.9 firmware
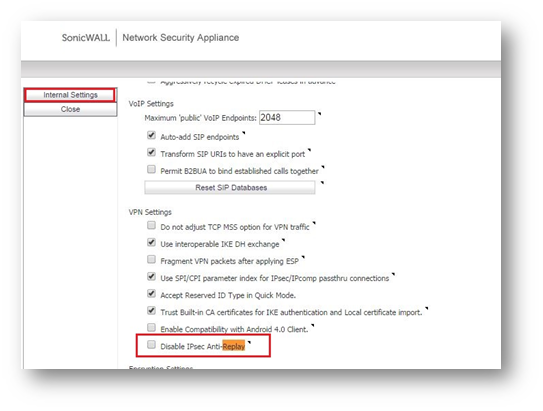
- Login to SonicWall appliance and change the url of the firewall from https://firewall ip/main.html to https://firewall ip/diag.html.
- Click Internal Settings.
- Find option Disable IPsec Anti-Replay and check the box , Once done scroll up the page and accept the change.
How to Test
As mentioned earlier re-negotiate the VPN and perform the packet capture again.If the packet were being dropped due to incorrect sequence they would be allowed now.
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > VPN
- Firewalls > NSv Series > VPN
- Firewalls > TZ Series > VPN






 YES
YES NO
NO