-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
SSLVPN License Exhaustion on Gen7 Firewalls



Description
This article explains the symptoms, cause and fix for an Issue where remote SSLVPN users connecting to a GEN7 firewall operating on 7.1.1-7040, 7.1.1-7047, and 7.1.1-7051 firmware are unable to connect and receive a license exhaustion message. If the firewall admin logs into the firewall and views the SSLVPN|Status page, there are indications of unauthenticated users showing up with a login pending message with 0 mins of login time.
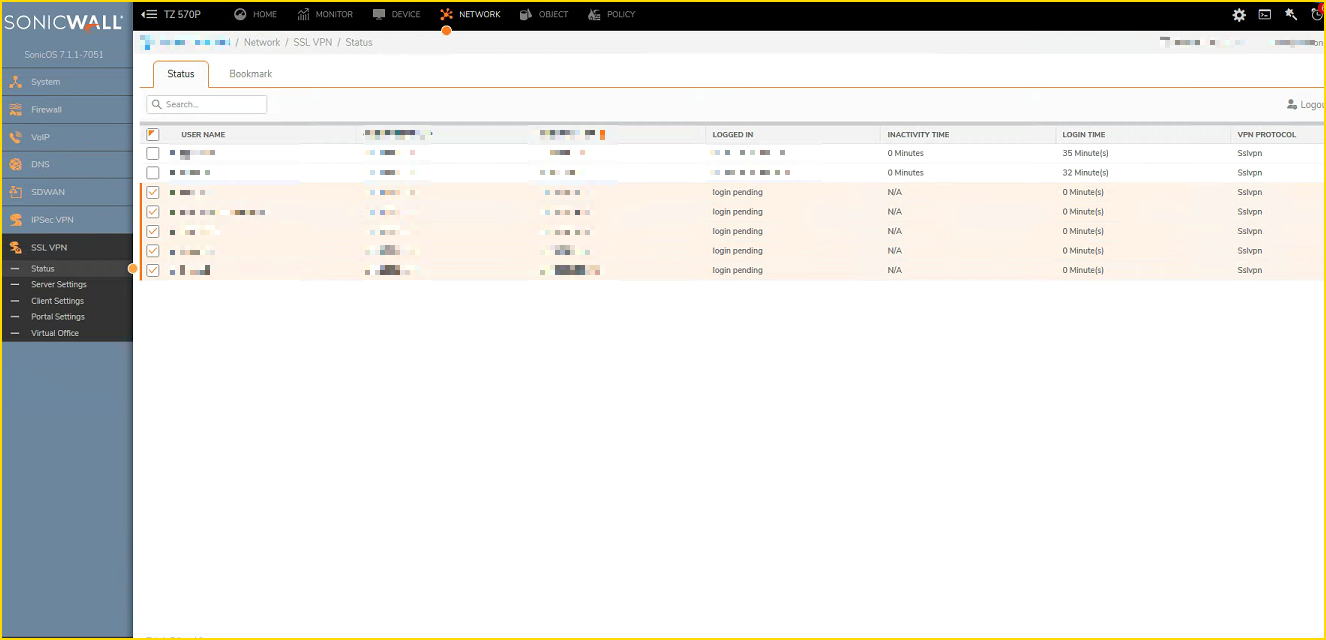
An example of the unathenticated users showing up on the UI:
NOTE: The users are showing N/A for the Inactivity Time and 0 mins for the Login Time.
Cause
The symptoms of remote users not being able to login is because the unauthenticated user is taking up the SSLVPN license.
This issue is only observed on GEN 7 firewalls currently operating with the 7.1.1 firmware.
Resolution
The issue was reported to Sonicwall Support. The fix comprises of two steps.
- Upgrading to the 7.1.1-7058 maintenance release firmware which has been published on mysonicwall.com on 19 June 2024. If you have been provided with a Hotfix Firmware ending with highlighted build 7.1.1-7051-R3290-HF46826 then you may also upgrade to the 7.1.1-7058 firmware as the appropriate fixes are included.
- Following the steps outlined below as additional counter measure steps on the firewall.
Additional required steps.
- Implement user account/IP lockout by Navigating to Device |Settings| Administration |Login/Multiple administrators.
-Local administrator account lockout – off means block the attempting IP instead of account
-Failed Login attempts – Set according to your situation, 10/min or so
-Lock out period – The maximum value is 60min (should be larger)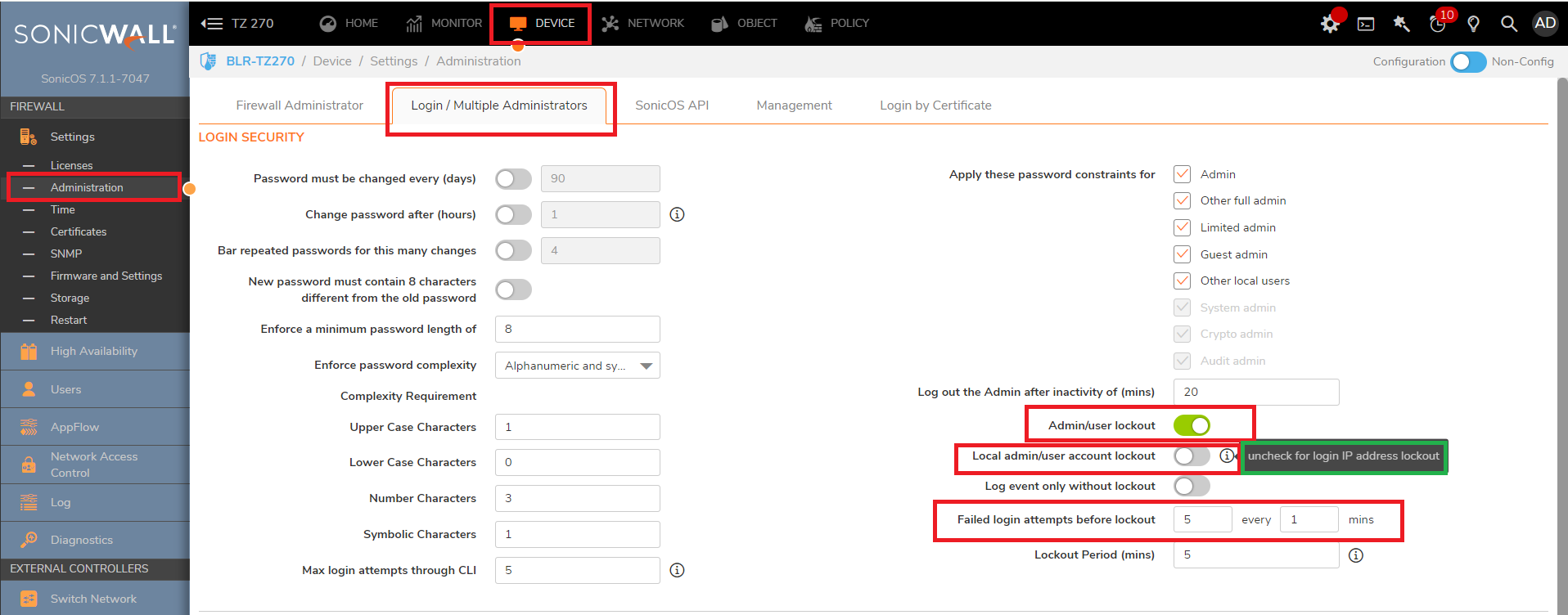
- Geo-IP can be implemented to allow only countries like US, Canada where your legitimate users are located. Other countries can be blocked.
-You can do this firewall rule based by enabling Geo-IP.
-Navigate to WAN to WAN Source-> Any, Destination: WAN interface IP or WAN IP, Services: SSLVPN services rule, edit the rule->Enable Geo-IP. Put a custom selection to allow and block country, and save it.
-This will apply Geo-IP only on SSLVPN rule and not on other rules.
-if you wish to enable on all rules, then select "all connections" in Geo-IP settings in Security services.
Geo-IP setting as below: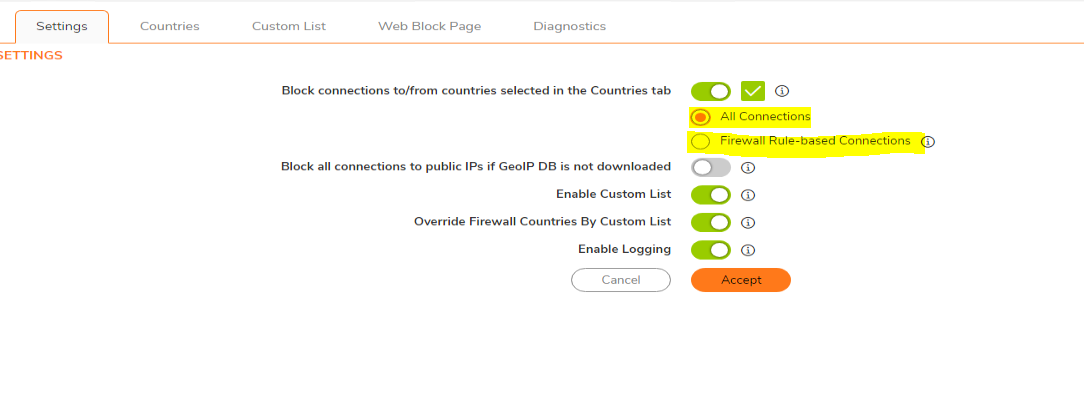
Access rule in question:
Editing rule to setup custom Geo-IP preferences: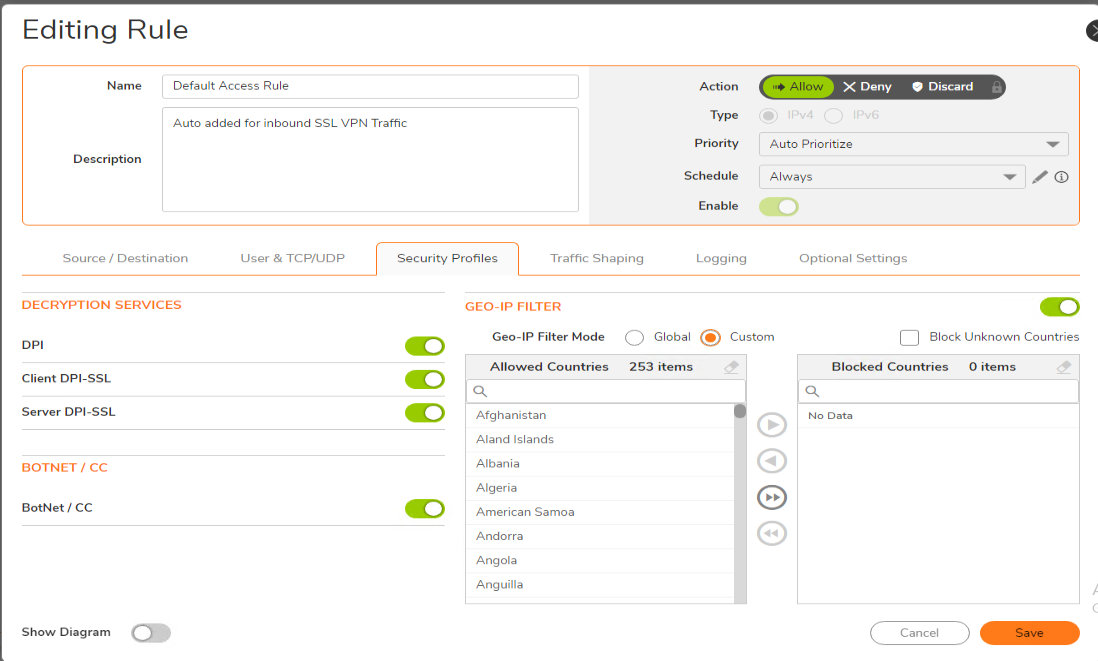
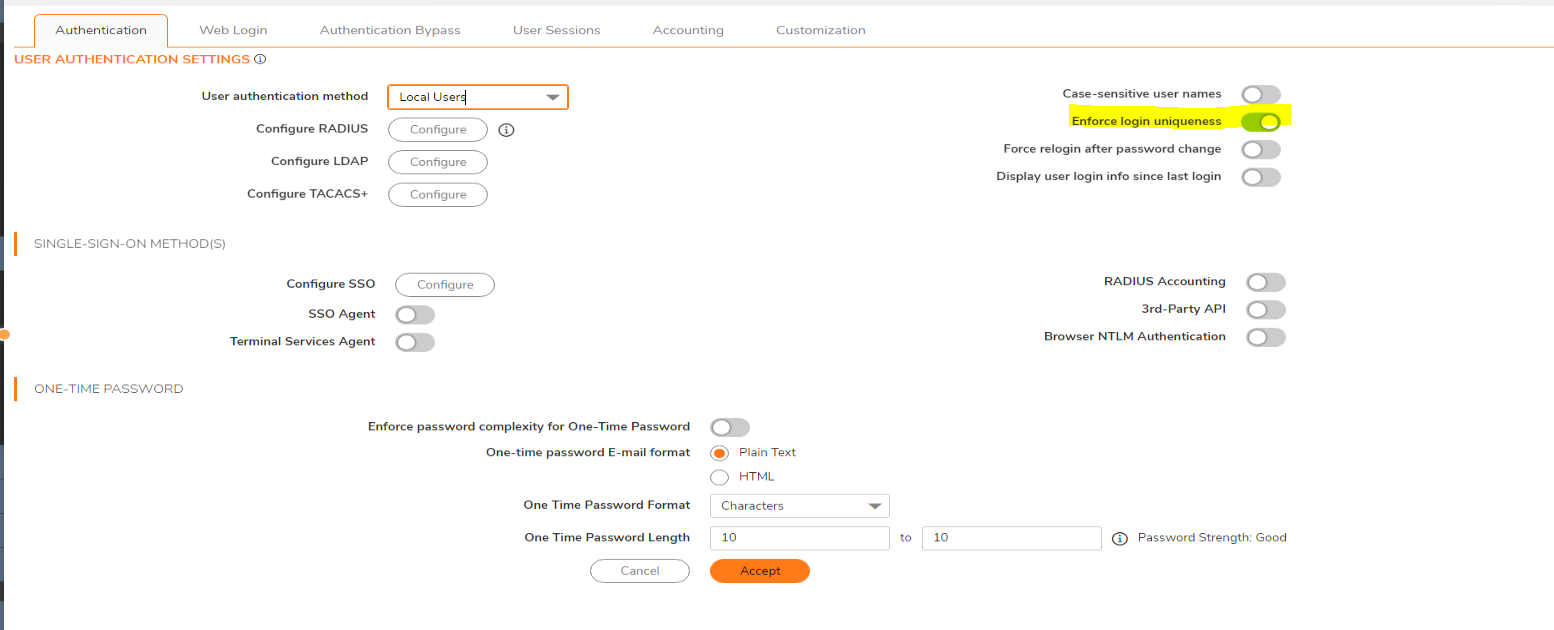
- Enable login uniqueness in Device -> Users -> Settings (highlighted in yellow).
- You can also utilize Botnet filter to block the unknown connections.
-This requires manual work where you can copy the IPs of unknown SSLVPN connections/auth attempts and create objects in WAN zone.
-Then group them together and create a botnet custom list.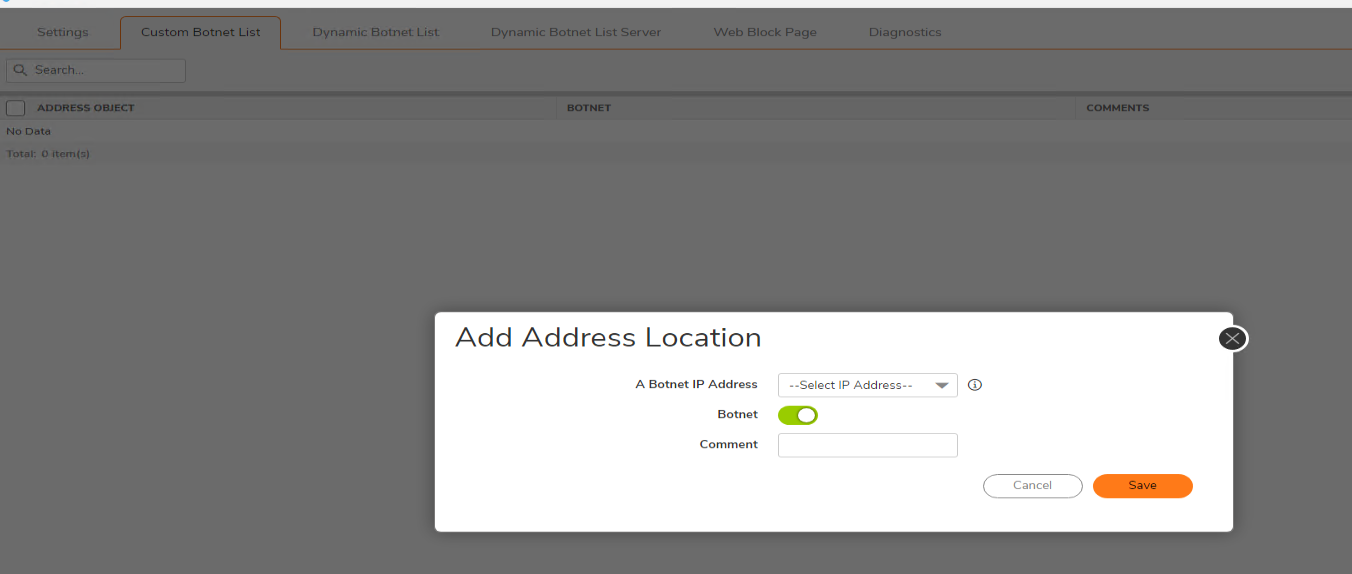
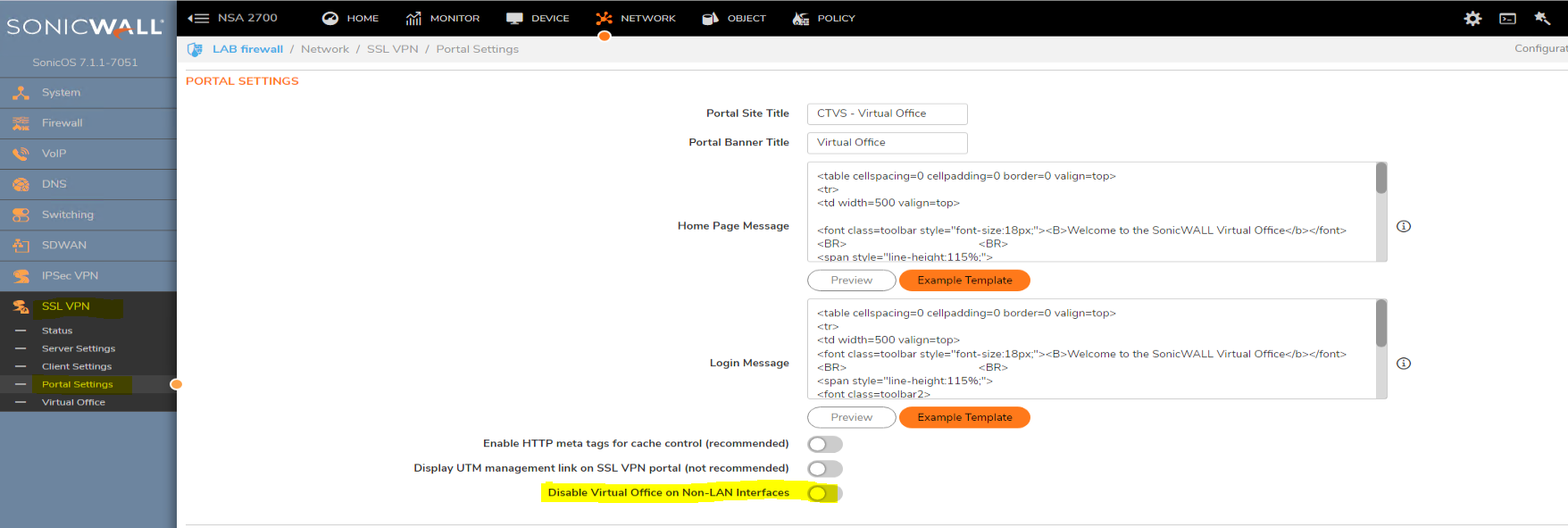
- Also as additional precaution, if you are not using virtual office then please navigate to Network -> SSL VPN -> Portal settings and Enable "Disable Virtual office on Non-LAN interfaces"
- Once the above step is done, you can secure the SSLVPN authentication more by changing SSLVPN port to something different than current SSLVPN. The default SSLVPN port is 4433.
Along with port, please consider to change User Domain name in SSLVPN server settings. This is just a pass phrase so you can keep something tough. NOTE: Users must have the correct port and domain name for authentication.
NOTE: Users must have the correct port and domain name for authentication.
Related Articles
- How to Block Google QUIC Protocol on SonicOSX 7.0?
- How to block certain Keywords on SonicOSX 7.0?
- How internal Interfaces can obtain Global IPv6 Addresses using DHCPv6 Prefix Delegation
Categories
- Firewalls > TZ Series
- Firewalls > NSa Series
- Firewalls > TZ Series > SSLVPN
- Firewalls > NSa Series > SSLVPN






 YES
YES NO
NO