-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Sophos Protect Devices Update Failure



Description
Occasionally, when end stations are attempting to update Sophos End Point protection, the SonicWall Gateway Anti-Virus blocks the download as the updates contains strings that resemble malicious code. While the two companies are investigating, the following article will provide a way to avoid this issue.
Cause
Sophos updates contain strings that resemble malicious code, so when a SonicWall firewall scans them, they show up as indicators of malware and we block them. Our SonicWall Capture Labs Director is in contact with Sophos on the best way for us both to resolve this however, the fact that our GAV sees some of their Malware Definition/Signatures as potential Malware is not surprising given that they must contain data to detect Malware and that data looks like Malware.
Resolution
If you have troubles installing the Sophos client and not able to download the initial signature database it is most likely because SonicWall GAV security service is blocking the transfer. We will need to exclude a few Sophos FQDN addresses (i.e. *.sophos.com, *.sophosupd.com, etc.) in order to pass the traffic. To do this we will create a firewall access rule for the Sophos AV Group with the option to Disable DPI so traffic to the Sophos AV Group bypasses all of the SonicWall DPI engines. We will also modify the FQDN address objects to override the TTL given by the DNS server lookup as they are shorter than what it appears the Sophos client refreshes for, we will put them at the max of 86,400 seconds which is 24 hours. This is because if the client is trying to talk to d1.sophosupd.com for updates on IP 1.2.3.4 and uses that IP for the next 30 minutes but the TTL is only 60 seconds, the SonicWall could clear that IP out of the FQDN Address Object cache before the client does a new DNS query to repopulate the SonicWall firewall’s cache and it would therefore not match the bypass DPI Rule.
- Create custom Address Objects from Network | Address Objects for Sophos Domains and override the DNS TTL as below.
 NOTE: You will have to check with Sophos which domains you need to exclude and create as many customer Address Objects as needed. After the Address Objects are created, you can group them under an Address Group (i.e. Sophos AV Group) to be used into the Access Rules.
NOTE: You will have to check with Sophos which domains you need to exclude and create as many customer Address Objects as needed. After the Address Objects are created, you can group them under an Address Group (i.e. Sophos AV Group) to be used into the Access Rules.
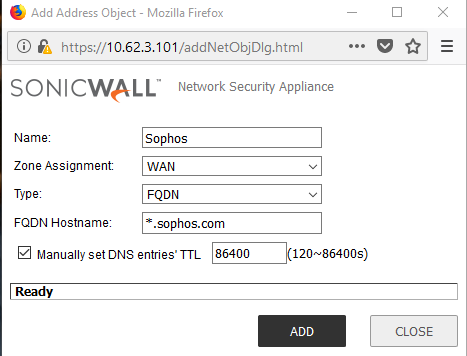
Sophos Endpoint - domains
*.sophos.com
*.sophosupd.com
*.sophosupd.net
*.sophosxl.net
ocsp2.globalsign.com
crl.globalsign.com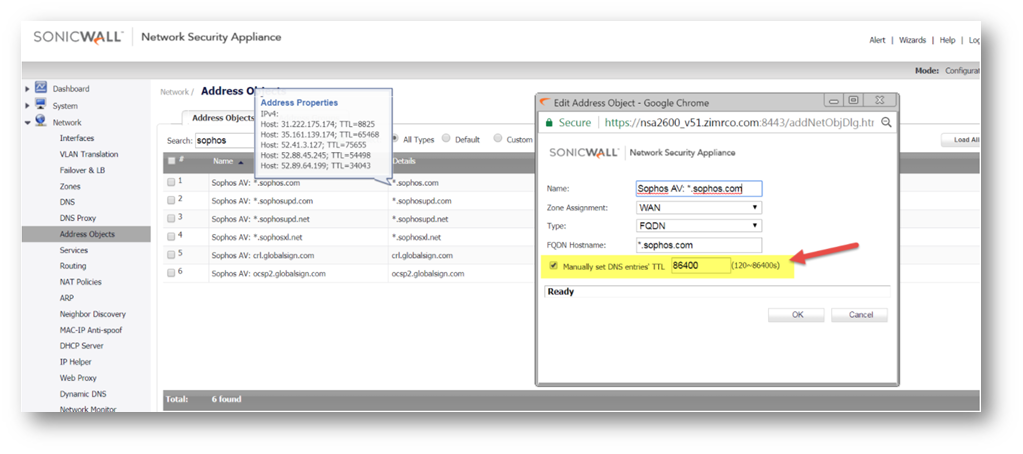
- Create the following access rule by navigating to Firewall | Access Rules.
Under the General tab select:- Action: Allow
- From: Any zone with Sophos clients
- To: WAN
- Source Port: Any
- Service: Any
- Source: Any
- Destination: The address objects that was created for Sophos
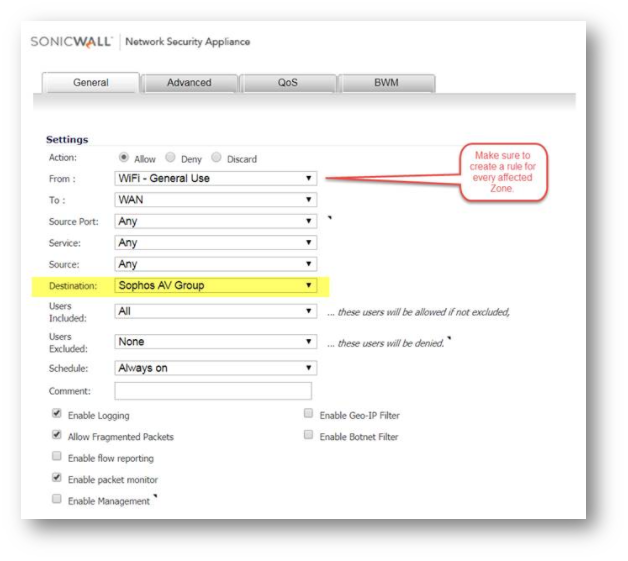
- Under the Advanced tab check Disable DPI.
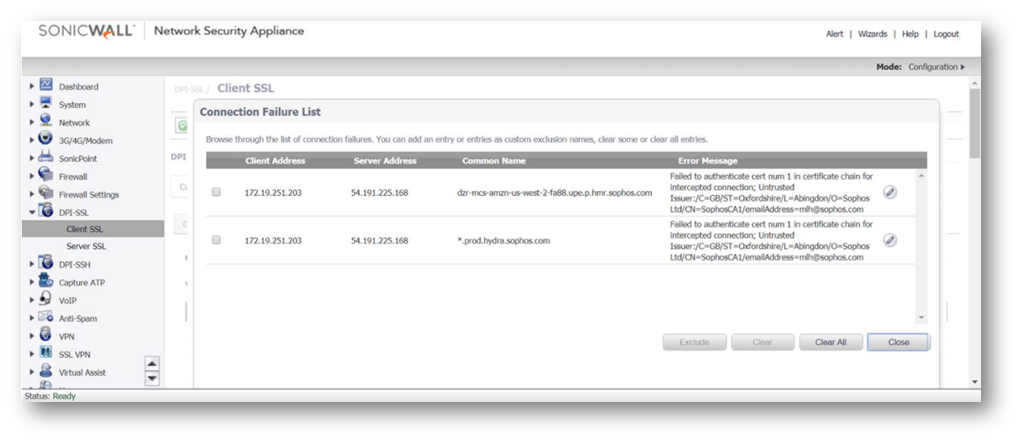
- Create DPI-SSL exclusions. Exclude the following:
- .prod.hydra.sophos.com
- dzr-mcs-amzn-us-west-2-fa88.upe.p.hmr.sophos.com
 NOTE: the exact FQDN for this will differ on a customer by customer basis. Thus, you could also simply exclude .upe.p.hmr.sophos.com per https://community.sophos.com/sophos-central/f/recommended-reads/122522/sophos-central-certificate-security-information which explains that the Sophos Client uses Certificate Pinning (thus, does not reference the OS’s Trusted CA database). For our example we added this and deleted the specific “dzr-mcs-amzn-us-west-2-fa88.upe.p.hmr.sophos.com”
NOTE: the exact FQDN for this will differ on a customer by customer basis. Thus, you could also simply exclude .upe.p.hmr.sophos.com per https://community.sophos.com/sophos-central/f/recommended-reads/122522/sophos-central-certificate-security-information which explains that the Sophos Client uses Certificate Pinning (thus, does not reference the OS’s Trusted CA database). For our example we added this and deleted the specific “dzr-mcs-amzn-us-west-2-fa88.upe.p.hmr.sophos.com”
DPI-SSL Connection Failure List when trying to install the client:
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > SonicWall NSA Series > IPS/GAV/Spyware
- Firewalls > SonicWall SuperMassive 9000 Series > IPS/GAV/Spyware
- Firewalls > TZ Series > IPS/GAV/Spyware






 YES
YES NO
NO